Documente Academic
Documente Profesional
Documente Cultură
Creating Nat Policies: Panel - Addnatpoldlg
Încărcat de
Abhijeet KumarTitlu original
Drepturi de autor
Formate disponibile
Partajați acest document
Partajați sau inserați document
Vi se pare util acest document?
Este necorespunzător acest conținut?
Raportați acest documentDrepturi de autor:
Formate disponibile
Creating Nat Policies: Panel - Addnatpoldlg
Încărcat de
Abhijeet KumarDrepturi de autor:
Formate disponibile
14/06/2016
PANEL_addNatPolDlg
PANEL_addNatPolDlg
CreatingNATPolicies
ForgeneralinformationonNATPolicies,seeNetwork>NATPolicies.
NATpoliciesallowyoutheflexibilitytocontrolNetworkAddressTranslationbasedonmatchingcombinations
ofSourceIPaddress,DestinationIPaddress,andDestinationServices.PolicybasedNATallowsyouto
deploydifferenttypesofNATsimultaneously.Thissectioncontainsthefollowingsubsections:
CreatingaManytoOneNATPolicy
CreatingaManytoManyNATPolicy
CreatingaOnetoOneNATPolicyforOutboundTraffic
CreatingaOnetoOneNATPolicyforInboundTraffic(Reflective)
ConfiguringOnetoManyNATLoadBalancing
InboundPortAddressTranslationviaOnetoOneNATPolicy
InboundPortAddressTranslationviaWANIPAddress
UsingNATLoadBalancing
Forthischapter,theexamplesusethefollowingIPaddressesasexamplestodemonstratetheNATpolicy
creationandactivation.YoucanusetheseexamplestocreateNATpoliciesforyournetwork,substitutingyour
IPaddressesfortheexamplesshownhere:
192.168.10.0/24IPsubnetoninterfaceX0
67.115.118.64/27IPsubnetoninterfaceX1
192.168.30.0/24IPsubnetoninterfaceX2
X0IPaddressis192.168.10.1
X1IPaddressis67.115.118.68
X2SalesIPaddressis192.168.30.1
Webserversprivateaddressat192.168.30.200
Webserverspublicaddressat67.115.118.70
PublicIPrangeaddressesof67.115.118.7167.115.118.74
CreatingaManytoOneNATPolicy
ManytoOneisthemostcommonNATpolicyonaSonicWALLsecurityappliance,andallowsyoutotranslate
agroupofaddressesintoasingleaddress.Mostofthetime,thismeansthatyouretakinganinternalprivate
IPsubnetandtranslatingalloutgoingrequestsintotheIPaddressoftheWANinterfaceoftheSonicWALL
securityappliance(bydefault,theX1interface),suchthatthedestinationseestherequestascomingfromthe
IPaddressoftheSonicWALLsecurityapplianceWANinterface,andnotfromtheinternalprivateIPaddress.
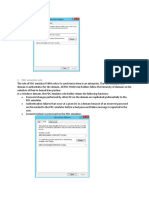
Thispolicyiseasytosetupandactivate.FromtheManagementInterface,gototheNetwork>NATPolicies
pageandclickontheAddbutton.TheAddNATPolicywindowisdisplayedforaddingthepolicy.Tocreatea
NATpolicytoallowallsystemsontheX2interfacetoinitiatetrafficusingtheSonicWALLsecurityappliances
WANIPaddress,choosethefollowingfromthedropdownboxes:
OriginalSource:X2Subnet
TranslatedSource:WANPrimaryIP
OriginalDestination:Any
TranslatedDestination:Original
OriginalService:Any
TranslatedService:Original
InboundInterface:X2
OutboundInterface:X1
Comment:Enterashortdescription
EnableNATPolicy:Checked
http://help.mysonicwall.com/sw/eng/6931/ui2/25201/PANEL_addNatPolDlg.html
1/9
14/06/2016
PANEL_addNatPolDlg
Createareflectivepolicy:Unchecked
Whendone,clickontheOKbuttontoaddandactivatetheNATPolicy.Thispolicycanbeduplicatedfor
subnetsbehindtheotherinterfacesoftheSonicWALLsecurityappliancejustreplacetheOriginalSource
withthesubnetbehindthatinterface,adjustthesourceinterface,andaddanotherNATpolicy.
CreatingaManytoManyNATPolicy
TheManytoManyNATpolicyallowsyoutotranslateagroupofaddressesintoagroupofdifferentaddresses.
ThisallowstheSonicWALLsecurityappliancetoutilizeseveraladdressestoperformthedynamictranslation.
ThusallowingamuchhighernumberofconcurrenttheSonicWALLsecurityappliancetoperformuptoahalf
millionconcurrentconnectionsacrosstheinterfaces.
Thispolicyiseasytosetupandactivate.YoufirstneedtogototheNetwork>AddressObjectsandclickon
theAddbuttonatthebottomofthescreen.WhentheAddAddressObjectwindowappears,enterina
descriptionfortherangeintheNamefield,chooseRangefromthedropdownmenu,entertherangeof
addresses(usuallypublicIPaddressessuppliedbyyourISP)intheStartingIPAddressandEndingIP
Addressfields,andselectWANasthezonefromtheZoneAssignmentmenu.Whendone,clickontheOK
buttontocreatetherangeobject.
SelectNetwork>NATPoliciesandclickontheAddbutton.TheAddNATPolicywindowisdisplayed.To
createaNATpolicytoallowthesystemsontheLANinterface(bydefault,theX0interface)toinitiatetraffic
usingthepublicrangeaddresses,choosethefollowingfromthedropdownmenus:
OriginalSource:LANPrimarySubnet
TranslatedSource:public_range
OriginalDestination:Any
TranslatedDestination:Original
OriginalService:Any
TranslatedService:Original
InboundInterface:X0
OutboundInterface:X1
Comment:Enterashortdescription
EnableNATPolicy:Checked
Createareflectivepolicy:Unchecked
Whendone,clickontheOKbuttontoaddandactivatetheNATPolicy.Withthispolicyinplace,the
SonicWALLsecurityappliancedynamicallymapsoutgoingtrafficusingthefouravailableIPaddressesinthe
rangewecreated.
YoucantestthedynamicmappingbyinstallingseveralsystemsontheLANinterface(bydefault,theX0
interface)ataspreadoutrangeofaddresses(forexample,192.168.10.10,192.168.10.100,and
192.168.10.200)andaccessingthepublicWebsitehttp://www.whatismyip.comfromeachsystem.Each
systemshoulddisplayadifferentIPaddressfromtherangewecreatedandattachedtotheNATpolicy.
CreatingaOnetoOneNATPolicyforOutboundTraffic
OnetoOneNATforoutboundtrafficisanothercommonNATpolicyonaSonicWALLsecurityappliancefor
translatinganinternalIPaddressintoauniqueIPaddress.Thisisusefulwhenyouneedspecificsystems,
suchasservers,touseaspecificIPaddresswhentheyinitiatetraffictootherdestinations.Mostofthetime,
aNATpolicysuchasthisOnetoOneNATpolicyforoutboundtrafficisusedtomapaserversprivateIP
addresstoapublicIPaddress,anditispairedwithareflective(mirror)policythatallowsanysystemfromthe
publicInternettoaccesstheserver,alongwithamatchingfirewallaccessrulethatpermitsthis.Reflective
NATpoliciesarecoveredinthenextsection.
Thispolicyiseasytosetupandactivate.SelectNetwork>AddressObjectsandclickontheAddbuttonat
thebottomofthescreen.IntheAddAddressObjectwindow,enteradescriptionforserversprivateIP
addressintheNamefield.ChooseHostfromtheTypemenu,entertheserversprivateIPaddressintheIP
Addressfield,andselectthezonethattheserverassignedfromtheZoneAssignmentmenu.ClickOK.
Then,createanotherobjectintheAddAddressObjectwindowfortheserverspublicIPaddressandwiththe
correctvalues,andselectWANfromZoneAssignmentmenu.Whendone,clickontheOKbuttontocreate
therangeobject.
Next,selectNetwork>NATPoliciesandclickontheAddbuttontodisplaytheAddNATPolicywindow.To
createaNATpolicytoallowtheWebservertoinitiatetraffictothepublicInternetusingitsmappedpublicIP
address,choosethefollowingfromthedropdownmenus:
http://help.mysonicwall.com/sw/eng/6931/ui2/25201/PANEL_addNatPolDlg.html
2/9
14/06/2016
PANEL_addNatPolDlg
OriginalSource:webserver_private_ip
TranslatedSource:webserver_public_ip
OriginalDestination:Any
TranslatedDestination:Original
OriginalService:Any
TranslatedService:Original
InboundInterface:X2
OutboundInterface:X1
Comment:Enterashortdescription
EnableNATPolicy:Checked
Createareflectivepolicy:Checked
Whendone,clickontheOKbuttontoaddandactivatetheNATPolicy.Withthispolicyinplace,the
SonicWALLsecurityappliancetranslatestheserversprivateIPaddresstothepublicIPaddresswhenit
initiatestrafficouttheWANinterface(bydefault,theX1interface).
YoucantesttheOnetoOnemappingbyopeningupaWebbrowserontheserverandaccessingthepublic
Websitehttp://www.whatismyip.com.TheWebsiteshoulddisplaythepublicIPaddressweattachedtothe
privateIPaddressintheNATpolicywejustcreated.
CreatingaOnetoOneNATPolicyforInboundTraffic(Reflective)
ThisisthemirrorpolicyfortheonecreatedintheprevioussectionwhenyoucheckCreateareflectivepolicy.
ItallowsyoutotranslateanexternalpublicIPaddressesintoaninternalprivateIPaddress.ThisNATpolicy,
whenpairedwithapermitaccesspolicy,allowsanysourcetoconnecttotheinternalserverusingthepublic
IPaddresstheSonicWALLsecurityappliancehandlesthetranslationbetweentheprivateandpublicaddress.
Withthispolicyinplace,theSonicWALLsecurityappliancetranslatestheserverspublicIPaddresstothe
privateIPaddresswhenconnectionrequestsarriveviatheWANinterface(bydefault,theX1interface).
Below,youcreatetheentryaswellastheruletoallowHTTPaccesstotheserver.Youneedtocreatethe
accesspolicythatallowsanyonetomakeHTTPconnectionstotheWebserverviatheWebserverspublicIP
address.
Note
Withpreviousversionsoffirmware,itwasnecessarytowriterulestotheprivateIP
address.ThishasbeenchangedasofSonicOSEnhanced.Ifyouwritearuletothe
privateIPaddress,theruledoesnotwork.
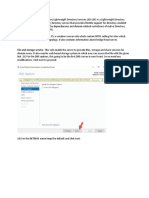
GototheFirewall>AccessRulespageandchoosethepolicyfortheWANtoSaleszoneintersection(or,
whateverzoneyouputyourserverin).ClickontheAddbuttontobringupthepopupaccesspolicyscreen.
Whenthepopupappears,enterinthefollowingvalues:
Action:Allow
Service:HTTP
Source:Any
Destination:Webserver_public_ip
UsersAllowed:All
Schedule:Alwayson
Logging:Checked
Comment:(Enterashortdescription)
Whenyouaredone,attempttoaccesstheWebserverspublicIPaddressusingasystemlocatedonthe
publicInternet.Youshouldbeabletosuccessfullyconnect.Ifnot,reviewthissection,andthesectionbefore,
andensurethatyouhaveenteredinallrequiredsettingscorrectly.
ConfiguringOnetoManyNATLoadBalancing
OnetoManyNATpoliciescanbeusedtopersistentlyloadbalancethetranslateddestinationusingtheoriginal
sourceIPaddressasthekeytopersistence.Forexample,SonicWALLsecurityappliancescanloadbalance
multipleSonicWALLSSLVPNappliances,whilestillmaintainingsessionpersistencebyalwaysbalancing
clientstothecorrectdestinationSSLVPN.Thefollowingfigureshowsasampletopologyandconfiguration.
http://help.mysonicwall.com/sw/eng/6931/ui2/25201/PANEL_addNatPolDlg.html
3/9
14/06/2016
PANEL_addNatPolDlg
ToconfigureOnetoManyNATloadbalancing,firstgototheFirewall>AccessRulespageandchoosethe
policyforWANtoLAN.ClickontheAddbuttontobringupthepopupaccesspolicyscreen.Whenthepop
upappears,enterinthefollowingvalues:
Action:Allow
Service:HTTPS
Source:Any
Destination:WANPrimaryIP
UsersAllowed:All
Schedule:Alwayson
Comment:Descriptivetext,suchasSSLVPNLB
Logging:Checked
AllowFragmentedPackets:Unchecked
Next,createthefollowingNATpolicybyselectingNetwork>NATPoliciesandclickingontheAdd...button:
OriginalSource:Any
TranslatedSource:Original
OriginalDestination:WANPrimaryIP
TranslatedDestination:SelectCreatenewaddressobject...tobringuptheAddAddressObject
screen.
Name:Adescriptivename,suchasmySSLVPN
Zoneassignment:LAN
Type:Host
IPAddress:TheIPaddressesforthedevicestobeloadbalanced(inthetopologyshownabove,
thisis192.168.200.10,192.168.200.20,and192.168.200.30.)
OriginalService:HTTPS
TranslatedService:HTTPS
InboundInterface:Any
OutboundInterface:Any
Comment:Descriptivetext,suchasSSLVPNLB
EnableNATPolicy:Checked
Createareflectivepolicy:Unchecked
InboundPortAddressTranslationviaOnetoOneNATPolicy
ThistypeofNATpolicyisusefulwhenyouwanttoconcealaninternalserversreallisteningport,butprovide
publicaccesstotheserveronadifferentport.Intheexamplebelow,youmodifytheNATpolicyandrule
createdintheprevioussectiontoallowpublicuserstoconnecttotheprivateWebserveronitspublicIP
address,butviaadifferentport(TCP9000),insteadofthestandardHTTPport(TCP80).
Step1 Createacustomserviceforthedifferentport.GototheFirewall>CustomServicespageandselect
http://help.mysonicwall.com/sw/eng/6931/ui2/25201/PANEL_addNatPolDlg.html
4/9
14/06/2016
PANEL_addNatPolDlg
theAddbutton.Whenthepopupscreenappears,giveyourcustomserviceanamesuchas
webserver_public_port,enterin9000asthestartingandendingport,andchooseTCP(6)asthe
protocol.Whendone,clickontheOKbuttontosavethecustomservice.
Step2 ModifytheNATpolicycreatedintheprevioussectionthatallowedanypublicusertoconnecttothe
WebserveronitspublicIPaddress.GototheNetwork>NATPoliciesmenuandclickontheEdit
buttonnexttothisNATpolicy.TheEditNATPolicywindowisdisplayedforeditingthepolicy.Editthe
NATpolicysothatitincludesthefollowingfromthedropdownmenus:
OriginalSource:Any
TranslatedSource:Original
OriginalDestination:webserver_public_ip
TranslatedDestination:webserver_private_ip
OriginalService:webserver_public_port(orwhateveryounameditabove)
TranslatedService:HTTP
InboundInterface:X1
OutboundInterface:Any
Comment:Enterashortdescription
EnableNATPolicy:Checked
Createareflectivepolicy:Unchecked
Note MakesureyouchoseAnyasthedestinationinterface,andnottheinterfacethatthe
serverison.Thismayseemcounterintuitive,butitisactuallythecorrectthingto
do(ifyoutrytospecifytheinterface,yougetanerror).
Step3 Whenfinished,clickontheOKbuttontoaddandactivatetheNATPolicy.Withthispolicyinplace,
theSonicWALLsecurityappliancetranslatestheserverspublicIPaddresstotheprivateIPaddress
whenconnectionrequestsarrivefromtheWANinterface(bydefault,theX1interface),andtranslates
therequestedprotocol(TCP9000)totheserversactuallisteningport(TCP80).
Finally,youregoingtomodifythefirewallaccessrulecreatedintheprevioussectiontoallowanypublicuser
toconnecttotheWebserveronthenewport(TCP9000)insteadoftheserversactuallisteningport(TCP80).
Note
WithpreviousversionsoftheSonicOSfirmware,itwasnecessarytowriterulesto
theprivateIPaddress.ThishasbeenchangedasofSonicOSEnhanced.Ifyouwrite
aruletotheprivateIPaddress,theruledoesnotwork.
GototheFirewall>AccessRulessectionandchoosethepolicyfortheWANtoSaleszoneintersection(or,
whateverzoneyouputyourserverin).ClickontheConfigurebuttontobringupthepreviouslycreatedpolicy.
Whenthepopupappears,editinthefollowingvalues:
Action:Allow
Service:server_public_port(orwhateveryounameditabove)
Source:Any
Destination:webserver_public_ip
UsersAllowed:All
Schedule:Alwayson
Logging:checked
Comment:(enterashortdescription)
Whenyouredone,attempttoaccesstheWebserverspublicIPaddressusingasystemlocatedonthepublic
Internetonthenewcustomport(example:http://67.115.118.70:9000).Youshouldbeabletosuccessfully
connect.Ifnot,reviewthissection,andthesectionbefore,andensurethatyouhaveenteredinallrequired
settingscorrectly.
InboundPortAddressTranslationviaWANIPAddress
ThisisoneofthemorecomplexNATpoliciesyoucancreateonaSonicWALLsecurityappliancerunning
SonicOSEnhanceditallowsyoutousetheWANIPaddressoftheSonicWALLsecurityappliancetoprovide
accesstomultipleinternalservers.ThisismostusefulinsituationswhereyourISPhasonlyprovidedasingle
publicIPaddress,andthatIPaddresshastobeusedbytheSonicWALLsecurityappliancesWANinterface
(bydefault,theX1interface).
Below,youcreatetheprogrammingtoprovidepublicaccesstotwointernalWebserversviatheSonicWALL
securityappliancesWANIPaddresseachistiedtoauniquecustomport.Inthefollowingexamples,youset
uptwo,butitispossibletocreatemorethantheseaslongastheportsareallunique.
Inthissection,wehavefivetaskstocomplete:
1.
Createtwocustomserviceobjectsfortheuniquepublicportstheserversrespondon.
http://help.mysonicwall.com/sw/eng/6931/ui2/25201/PANEL_addNatPolDlg.html
5/9
14/06/2016
PANEL_addNatPolDlg
2.
3.
4.
CreatetwoaddressobjectsfortheserversprivateIPaddresses.
CreatetwoNATentriestoallowthetwoserverstoinitiatetraffictothepublicInternet.
CreatetwoNATentriestomapthecustomportstotheactuallisteningports,andtomaptheprivateIP
addressestotheSonicWALLsWANIPaddress.
5. CreatetwoaccessruleentriestoallowanypublicusertoconnecttobothserversviatheSonicWALLs
WANIPaddressandtheserversrespectiveuniquecustomports.
Step1 Createacustomserviceforthedifferentport.GototheFirewall>CustomServicespageandclick
ontheAddbutton.Whenthepopupscreenappears,giveyourcustomservicesnamessuchas
servone_public_portandservtwo_public_port,enterin9100and9200asthestartingandending
port,andchooseTCP(6)astheprotocol.Whendone,clickontheOKbuttontosavethecustom
services.
Step2 GototheNetwork>AddressObjectsandclickontheAddbuttonatthebottomofthepage.Inthe
AddAddressObjectswindow,enterinadescriptionforserversprivateIPaddresses,chooseHost
fromthedropdownbox,entertheserversprivateIPaddresses,andselectthezonethattheservers
arein.Whendone,clickontheOKbuttontocreatetherangeobject.
Step3 GototheNetwork>NATPoliciesmenuandclickontheAddbutton.TheAddNATPolicywindow
isdisplayed.TocreateaNATpolicytoallowthetwoserverstoinitiatetraffictothepublicInternet
usingtheSonicWALLsecurityappliancesWANIPaddress,choosethefollowingfromthedropdown
boxes:
OriginalSource:servone_private_ip
TranslatedSource:WANPrimaryIP
OriginalDestination:Any
TranslatedDestination:Original
OriginalService:Any
TranslatedService:Original
InboundInterface:X2
OutboundInterface:X1
Comment:Enterashortdescription
EnableNATPolicy:Checked
Createareflectivepolicy:Unchecked
And:
OriginalSource:servtwo_private_ip
TranslatedSource:WANPrimaryIP
OriginalDestination:Any
TranslatedDestination:Original
OriginalService:Any
TranslatedService:Original
InboundInterface:X2
OutboundInterface:X1
Comment:Enterashortdescription
EnableNATPolicy:Checked
Createareflectivepolicy:Unchecked
Whenfinished,clickontheOKbuttontoaddandactivatetheNATpolicies.Withthesepoliciesinplace,the
SonicWALLsecurityappliancetranslatestheserversprivateIPaddressestothepublicIPaddresswhenit
initiatestrafficouttheWANinterface(bydefault,theX1interface).
Step4 GototheNetwork>NATPoliciesmenuandclickontheAddbutton.TheAddNATPolicywindow
isdisplayed.TocreatetheNATpoliciestomapthecustomportstotheserversreallisteningports
andtomaptheSonicWALLsWANIPaddresstotheserversprivateaddresses,choosethefollowing
fromthedropdownboxes:
OriginalSource:Any
TranslatedSource:Original
OriginalDestination:WANPrimaryIP
TranslatedDestination:servone_private_ip
OriginalService:servone_public_port
TranslatedService:HTTP
InboundInterface:X1
OutboundInterface:Any
Comment:Enterashortdescription
EnableNATPolicy:Checked
Createareflectivepolicy:Unchecked
http://help.mysonicwall.com/sw/eng/6931/ui2/25201/PANEL_addNatPolDlg.html
6/9
14/06/2016
PANEL_addNatPolDlg
And:
OriginalSource:Any
TranslatedSource:Original
OriginalDestination:WANPrimaryIP
TranslatedDestination:servtwo_private_ip
OriginalService:servtwo_public_port
TranslatedService:HTTP
SourceInterface:X1
DestinationInterface:Any
Comment:Enterashortdescription
EnableNATPolicy:Checked
Createareflectivepolicy:Unchecked
Note MakesureyouchooseAnyasthedestinationinterface,andnottheinterfacethatthe
serverison.Thismayseemcounterintuitive,butitisactuallythecorrectthingto
do(ifyoutrytospecifytheinterface,yougetanerror).
Whenfinished,clickontheOKbuttontoaddandactivatetheNATpolicies.Withthesepoliciesinplace,the
SonicWALLsecurityappliancetranslatestheserverspublicIPaddresstotheprivateIPaddresswhen
connectionrequestsarrivefromtheWANinterface(bydefault,theX1interface).
Step5 CreatetheaccessrulesthatallowsanyonefromthepublicInternettoaccessthetwoWebservers
usingthecustomportsandtheSonicWALLsecurityappliancesWANIPaddress.
Note Withpreviousversionsoffirmware,itwasnecessarytowriterulestotheprivateIP
address.ThishasbeenchangedasofSonicOS2.0Enhanced.Ifyouwritearuleto
theprivateIPaddress,theruledoesnotwork.
GototheFirewall>AccessRulespageandchoosethepolicyfortheWANtoSaleszoneintersection(or,
whateverzoneyouputyourservesin).ClickontheAddbuttontobringupthepopupwindowtocreatethe
policies.Whenthepopupappears,enterthefollowingvalues:
Action:Allow
Service:servone_public_port(orwhateveryounameditabove)
Source:Any
Destination:WANIPaddress
UsersAllowed:All
Schedule:Alwayson
Logging:checked
Comment:(enterashortdescription)
And:
Action:Allow
Service:servtwo_public_port(orwhateveryounameditabove)
Source:Any
Destination:WANIPaddress
UsersAllowed:All
Schedule:Alwayson
Logging:checked
Comment:(enterashortdescription)
Whenyourefinished,attempttoaccesstheWebserversviatheSonicWALLsWANIPaddressusinga
systemlocatedonthepublicInternetonthenewcustomport(example:
http://67.115.118.70:9100andhttp://67.115.118.70:9200).Youshouldbeabletosuccessfullyconnect.Ifnot,
reviewthissection,andthesectionbefore,andensurethatyouhaveenteredinallrequiredsettingscorrectly.
UsingNATLoadBalancing
Thissectioncontainsthefollowingsubsections:
NATLoadBalancingTopology
Prerequisites
ConfiguringNATLoadBalancing
http://help.mysonicwall.com/sw/eng/6931/ui2/25201/PANEL_addNatPolDlg.html
7/9
14/06/2016
PANEL_addNatPolDlg
TroubleshootingNATLoadBalancing
NATLoadBalancingTopology
ThefollowingfigureshowsthetopologyfortheNATloadbalancingnetwork.
Prerequisites
TheexamplesshownintheTasklistsectiononthenextfewpagesutilizeIPaddressinginformationfroma
demosetuppleasemakesureandreplaceanyIPaddressinginformationshownintheexampleswiththe
correctaddressinginformationforyoursetup.Alsonotethattheinterfacenamesmaybedifferent.
Note
Itisstronglyadvisedthatyouenableloggingforallcategories,andenablename
resolutionforlogging.
Toenableloggingandalerting,logintotheSonicWALLsManagementGUI,gotoLog>Categories,choose
DebugfromthedropdownnexttoLoggingLevel,choseAllCategoriesfromthedropdownnexttoView
Style,checktheboxesinthetitlebarnexttoLogandAlertstocaptureallcategories,andclickontheApply
buttonintheupperrighthandcornertosaveandactivatethechanges.Foranexample,seethescreenshot
below.Debuglogsshouldonlybeusedforinitialconfigurationandtroubleshooting,anditisadvisedthatonce
setupiscomplete,yousettheloggingleveltoamoreappropriatelevelforyournetworkenvironment.
Toenablelognameresolution,gotoLog>NameResolution,chooseDNSthenNetBIOSfromtheName
ResolutionMenudropdownlist,andclickontheApplybuttonintheupperrighthandcornertosaveand
activatethechanges.
ConfiguringNATLoadBalancing
ToconfigureNATloadbalancing,youmustcompletethefollowingtasks:
1.
2.
3.
4.
5.
6.
Createaddressobjects.
Createaddressgroup.
CreateinboundNATLBPolicy.
CreateoutboundNATLBPolicy.
CreateFirewallRule.
Verifyandtroubleshootthenetworkifnecessary.
Tocompletethisconfiguration,performthefollowingsteps:
Step1 CreateNetworkObjectsGototheNetwork>AddressObjectspageintheManagementGUIand
createthenetworkobjectsforbothoftheinternalWebservers,andtheVirtualIP(VIP)onwhich
externaluserswillaccesstheservers.
Step2 CreateAddressGroupNowcreateanaddressgroupnamedwww_groupandaddthetwointernal
serveraddressobjectsyoujustcreated.
Step3 CreateInboundNATRuleforGroupNowcreateaNATruletoallowanyoneattemptingtoaccess
http://help.mysonicwall.com/sw/eng/6931/ui2/25201/PANEL_addNatPolDlg.html
8/9
14/06/2016
PANEL_addNatPolDlg
Step4
Step5
Step6
Step7
theVIPtogettranslatedtotheaddressgroupyoujustcreated,usingStickyIPastheNATmethod.
Note DonotsavetheNATrulejustyet.
SetLBTypeandServerLivelinessMethodOntheAdvancedtaboftheNATpolicyconfiguration
control,youcanspecifythattheobject(orgroupofobjects,orgroupofgroups)bemonitoredvia
ICMPpingorbycheckingforTCPsocketsopened.Forthisexample,wearegoingtochecktoseeif
theserverisupandrespondingbymonitoringTCPport80(whichisgood,sincethatiswhatpeople
aretryingtoaccess).YoucannowclickontheOKbuttontosaveandactivatethechanges.
Note Beforeyougoanyfurther,checkthelogsandthestatuspagetoseeiftheresources
havebeendetectedandhavebeenloggedasonline.Twoalertswillappearas
FirewallEventswiththemessageNetworkMonitor:Host192.160.200.220isonline
(withyourIPaddresses).Ifyoudonotseethesetwomessagesbelow,checkthe
stepsabove.
CreateOutboundNATRuleforLBGroupWriteaNATruletoallowtheinternalserverstoget
translatedtotheVIPwhenaccessingresourcesouttheWANinterface(bydefault,theX1interface).
CreateFirewallRuleforVIPWriteafirewallruletoallowtrafficfromtheoutsidetoaccessthe
internalWebserversviatheVIP.
TestYourWorkFromalaptopoutsidetheWAN,connectviaHTTPtotheVIPusingaWeb
browser.
Note IfyouwishtoloadbalanceoneormoreSSLVPNAppliances,repeatsteps17,
usingHTTPSinsteadastheallowedservice.
TroubleshootingNATLoadBalancing
IftheWebserversdonotseemtobeaccessible,gototheFirewall>AccessRulespageandmouseoverthe
Statisticsicon.
IftheruleisconfiguredincorrectlyyouwillnotseeanyRxorTXBytesifitisworking,youwillseethese
incrementwitheachsuccessfulexternalaccessoftheloadbalancedresources.Youcanalsocheckthe
Firewall>NATPoliciespageandmouseovertheStatisticsicon.Ifthepolicyisconfiguredincorrectlyyou
willnotseeanyRxorTXBytesifitisworking,youwillseetheseincrementwitheachsuccessfulexternal
accessoftheloadbalancedresources.
Finally,checkthelogsandthestatuspagetoseeifthereareanyalerts(notedinyellow)abouttheNetwork
Monitornotinghoststhatareofflineitmaybethatallofyourloadbalancingresourcesarenotreachableby
theSonicWALLapplianceandthattheprobingmechanismhasmarkedthemofflineandoutofservice.Check
theloadbalancingresourcestoensurethattheyarefunctionalandcheckthenetworkingconnectionsbetween
themandtheSonicWALLappliance.
http://help.mysonicwall.com/sw/eng/6931/ui2/25201/PANEL_addNatPolDlg.html
9/9
S-ar putea să vă placă și
- SAP Variant Configuration: Your Successful Guide to ModelingDe la EverandSAP Variant Configuration: Your Successful Guide to ModelingEvaluare: 5 din 5 stele5/5 (2)
- Azure Application GatewayDocument574 paginiAzure Application GatewayJonnathan De La Barra100% (1)
- New English File Answers - Instructional MaterialsDocument4 paginiNew English File Answers - Instructional MaterialsSuhanto Kastaredja0% (2)
- Ssp654 WG enDocument108 paginiSsp654 WG enAndrei Baluse100% (1)
- Tutorial Fwbuilder PDFDocument26 paginiTutorial Fwbuilder PDFFrancisco Reyes F100% (1)
- Campus Network For High Availability Design Guide PDFDocument62 paginiCampus Network For High Availability Design Guide PDFguesieroÎncă nu există evaluări
- Overview: Bandwidth Control Management: Manual Chapter: Managing Traffic With Bandwidth ControllersDocument8 paginiOverview: Bandwidth Control Management: Manual Chapter: Managing Traffic With Bandwidth ControllersarthakristiwanÎncă nu există evaluări
- Chapter 5 - Security PolicyDocument32 paginiChapter 5 - Security PolicyJosé Miguel Melgar RojasÎncă nu există evaluări
- Black Manticore: ObjectsDocument3 paginiBlack Manticore: ObjectsAbhijeet KumarÎncă nu există evaluări
- Chapter 5 - NAT - 5.5R7Document20 paginiChapter 5 - NAT - 5.5R7Heshitha PushpawelaÎncă nu există evaluări
- Network Address TranslationDocument13 paginiNetwork Address TranslationRoberd LeeÎncă nu există evaluări
- Netgroups Clustered CDOTDocument4 paginiNetgroups Clustered CDOTDonald MillerÎncă nu există evaluări
- AppWall Implementation Plan V10 AppWall Verion 5 6Document7 paginiAppWall Implementation Plan V10 AppWall Verion 5 6Juan Pablo Guerrero CuevaÎncă nu există evaluări
- Fuel 8.0 InstallGuideDocument67 paginiFuel 8.0 InstallGuideR.s. Félix100% (1)
- Campus Network For High Availability Design Guide: AudienceDocument62 paginiCampus Network For High Availability Design Guide: AudienceKiKi MaÎncă nu există evaluări
- Campus Network For High Availability Design Guide: AudienceDocument62 paginiCampus Network For High Availability Design Guide: Audiencetwilly99Încă nu există evaluări
- Sophos - Considerations For Deploying Sophos Firewall in Common ScenariosDocument22 paginiSophos - Considerations For Deploying Sophos Firewall in Common ScenariosMiguel António ManuelÎncă nu există evaluări
- How To Use Multi-NAT Function On TP-LINK Modems (IP Address Mapping For Multiple IP Servers) - (Trendchip Solution) - Welcome To TP-LINKDocument5 paginiHow To Use Multi-NAT Function On TP-LINK Modems (IP Address Mapping For Multiple IP Servers) - (Trendchip Solution) - Welcome To TP-LINKvsalaiselvamÎncă nu există evaluări
- 001 52-Intrusion Policies TheoryDocument10 pagini001 52-Intrusion Policies TheoryPractical1Încă nu există evaluări
- FW4030 19.0v1 Sophos Firewall Web Protection Quotas and Traffic ShapingDocument13 paginiFW4030 19.0v1 Sophos Firewall Web Protection Quotas and Traffic ShapingAndré MouraÎncă nu există evaluări
- 4to6 Tunnels For Ipv6Document8 pagini4to6 Tunnels For Ipv6Volf MarkoÎncă nu există evaluări
- Configuring One To One NATDocument5 paginiConfiguring One To One NATSoledad Iris Llashag HuertasÎncă nu există evaluări
- Pfsense Bandwidth ManagementDocument9 paginiPfsense Bandwidth ManagementasimalampÎncă nu există evaluări
- Untitled 2Document13 paginiUntitled 2sheraz salimÎncă nu există evaluări
- DashInsight Installation and ConfigurationDocument36 paginiDashInsight Installation and ConfigurationIonut DeaconescuÎncă nu există evaluări
- How To Configure A 'Route All Traffic' WAN GroupVPN PolicyDocument10 paginiHow To Configure A 'Route All Traffic' WAN GroupVPN PolicyneuseeÎncă nu există evaluări
- Cluster and SVM Peering Express Guide: Ontap 9Document15 paginiCluster and SVM Peering Express Guide: Ontap 9amita1392Încă nu există evaluări
- IoT U-VDocument65 paginiIoT U-VVardhan TvkÎncă nu există evaluări
- PfSense Bandwidth Management - How To Configure The Traffic ShaperDocument6 paginiPfSense Bandwidth Management - How To Configure The Traffic ShaperJustin HayesÎncă nu există evaluări
- BlueCoat ISPDocument39 paginiBlueCoat ISPanh00Încă nu există evaluări
- Create DNAT and Firewall Rules For Internal ServersDocument9 paginiCreate DNAT and Firewall Rules For Internal Serversthats bistÎncă nu există evaluări
- NetScaler 10.5 RewriteDocument78 paginiNetScaler 10.5 RewritesudharaghavanÎncă nu există evaluări
- PfSense Bandwidth ManagementDocument9 paginiPfSense Bandwidth ManagementasimalampÎncă nu există evaluări
- Bandwidth Splitter RulesDocument28 paginiBandwidth Splitter RulesAtif ShahÎncă nu există evaluări
- Chapter7 Address TranslationDocument16 paginiChapter7 Address TranslationDacaen DanÎncă nu există evaluări
- SHOUTcast Audio and Video Streaming GuideDocument27 paginiSHOUTcast Audio and Video Streaming GuideDavid Childers100% (1)
- Azure WebappDocument28 paginiAzure WebappTech guru MaheshwariÎncă nu există evaluări
- Firewall SettingsDocument6 paginiFirewall Settingsgestradag-1Încă nu există evaluări
- Does The Internet "End" at 500K Routes?Document5 paginiDoes The Internet "End" at 500K Routes?BarryRaveendranGreeneÎncă nu există evaluări
- What Is Azure Application GatewayDocument548 paginiWhat Is Azure Application GatewayNagaraju LankaÎncă nu există evaluări
- Chapter 1-70-412 FINALDocument32 paginiChapter 1-70-412 FINALTariq GhareebaÎncă nu există evaluări
- Hybrid Deployment in Office 365 - Checklist and Pre Requirements - Part 3 of 3Document7 paginiHybrid Deployment in Office 365 - Checklist and Pre Requirements - Part 3 of 3Eyal DoronÎncă nu există evaluări
- Configure Untangle Using Virtual MachineDocument14 paginiConfigure Untangle Using Virtual MachineRehan KhanÎncă nu există evaluări
- Lab 2 - Creating A SOHO ConfigurationDocument13 paginiLab 2 - Creating A SOHO Configurationrashmi mÎncă nu există evaluări
- Global Policy SRX OverviewDocument10 paginiGlobal Policy SRX OverviewSon Tran Hong NamÎncă nu există evaluări
- Nat - Overview 8.3 and LaterDocument24 paginiNat - Overview 8.3 and LaterThomas SchmelingÎncă nu există evaluări
- Onapp Cloud Free Version Installation GuideDocument17 paginiOnapp Cloud Free Version Installation GuidetomaestaÎncă nu există evaluări
- Configure Anyconnect Virtual Private Network (VPN) Connectivity On The Rv34X Series RouterDocument13 paginiConfigure Anyconnect Virtual Private Network (VPN) Connectivity On The Rv34X Series RouterThe Maison MaidsÎncă nu există evaluări
- Ios Netflow OvDocument12 paginiIos Netflow OvMurtaxa KhanÎncă nu există evaluări
- Zone Design GuideDocument49 paginiZone Design Guidenirvana_0zÎncă nu există evaluări
- NetFlow Configuration GuideDocument424 paginiNetFlow Configuration GuideFher5_5Încă nu există evaluări
- NAT Gateway and NAT InstanceDocument17 paginiNAT Gateway and NAT InstanceBhanu VikasÎncă nu există evaluări
- 03 - Zone Security, Security and NAT PoliciesDocument23 pagini03 - Zone Security, Security and NAT Policiesiboy.foodyÎncă nu există evaluări
- Test Lab Guide: Demonstrate Ipv6Document23 paginiTest Lab Guide: Demonstrate Ipv6Mukesh TayadeÎncă nu există evaluări
- Autoscaling: When To Use AutoscalingDocument6 paginiAutoscaling: When To Use AutoscalingJo bookingÎncă nu există evaluări
- Basic Router Config CCP 00Document35 paginiBasic Router Config CCP 00Emil StojanovskiÎncă nu există evaluări
- Basic Firewall PolicyDocument6 paginiBasic Firewall PolicyhenriquecongoÎncă nu există evaluări
- Cisco CCP IntroductionDocument47 paginiCisco CCP IntroductionVishwa MohanÎncă nu există evaluări
- Fortigate Traffic Shaping 54Document56 paginiFortigate Traffic Shaping 54Martin GoyecheaÎncă nu există evaluări
- 11.1 Steps To Create A New Group Using Powershell: Groupscope Global - Groupcategory Security and Press EnterDocument2 pagini11.1 Steps To Create A New Group Using Powershell: Groupscope Global - Groupcategory Security and Press EnterAbhijeet KumarÎncă nu există evaluări
- How To Create AD ObjectsDocument2 paginiHow To Create AD ObjectsAbhijeet KumarÎncă nu există evaluări
- 11 NL AD InfrastructureDocument3 pagini11 NL AD InfrastructureAbhijeet KumarÎncă nu există evaluări
- How To Create AD Objects22Document2 paginiHow To Create AD Objects22Abhijeet KumarÎncă nu există evaluări
- 16.1 How To Take AD BackupDocument3 pagini16.1 How To Take AD BackupAbhijeet KumarÎncă nu există evaluări
- 11.1 Creating Organizational Unit (Ous) :: 12 Basic Ad Powershell ScriptsDocument2 pagini11.1 Creating Organizational Unit (Ous) :: 12 Basic Ad Powershell ScriptsAbhijeet KumarÎncă nu există evaluări
- Configure DHCP Relay AgentDocument28 paginiConfigure DHCP Relay AgentAbhijeet KumarÎncă nu există evaluări
- Current ScemaVersionDocument2 paginiCurrent ScemaVersionAbhijeet KumarÎncă nu există evaluări
- ADirectorystoryDocument2 paginiADirectorystoryAbhijeet KumarÎncă nu există evaluări
- ADDS Installation StepsDocument8 paginiADDS Installation StepsAbhijeet KumarÎncă nu există evaluări
- PDC Emulator RoleDocument3 paginiPDC Emulator RoleAbhijeet KumarÎncă nu există evaluări
- File and Storage Service-This Role Enable The Server To Provide Files, Storage and Share Services ForDocument4 paginiFile and Storage Service-This Role Enable The Server To Provide Files, Storage and Share Services ForAbhijeet KumarÎncă nu există evaluări
- 1 FSMO (Flexible Single Master Operation) RoleDocument2 pagini1 FSMO (Flexible Single Master Operation) RoleAbhijeet KumarÎncă nu există evaluări
- 3 Install & Configure ADDS: 8.1 PrerequisitesDocument2 pagini3 Install & Configure ADDS: 8.1 PrerequisitesAbhijeet KumarÎncă nu există evaluări
- 3.6 Organizational Unit:: Active Directory Database PartitionsDocument8 pagini3.6 Organizational Unit:: Active Directory Database PartitionsAbhijeet KumarÎncă nu există evaluări
- ADLDSDocument1 paginăADLDSAbhijeet KumarÎncă nu există evaluări
- 8 AD Logical & Physical StructureDocument2 pagini8 AD Logical & Physical StructureAbhijeet KumarÎncă nu există evaluări
- 1.1 How To Take Backup of Group Policy?Document4 pagini1.1 How To Take Backup of Group Policy?Abhijeet KumarÎncă nu există evaluări
- Wndows Server Shortcut CommandsDocument3 paginiWndows Server Shortcut CommandsAbhijeet Kumar100% (1)
- 5.1 Overview of Various AD Roles and ServicesDocument2 pagini5.1 Overview of Various AD Roles and ServicesAbhijeet KumarÎncă nu există evaluări
- Linking GPODocument6 paginiLinking GPOAbhijeet KumarÎncă nu există evaluări
- Abbreviations/Acronyms ExpansionDocument7 paginiAbbreviations/Acronyms ExpansionAbhijeet KumarÎncă nu există evaluări
- Group Policy: 6.1 How To Create GPO and GPT ?Document5 paginiGroup Policy: 6.1 How To Create GPO and GPT ?Abhijeet KumarÎncă nu există evaluări
- AD OU Labelling and Domain Migration-Draft - 18-Feb-2020Document28 paginiAD OU Labelling and Domain Migration-Draft - 18-Feb-2020Abhijeet KumarÎncă nu există evaluări
- TroubleshootingDocument2 paginiTroubleshootingAbhijeet KumarÎncă nu există evaluări
- Synchronization Service Manager - Azure ADDocument4 paginiSynchronization Service Manager - Azure ADAbhijeet KumarÎncă nu există evaluări
- Powershell ScriptDocument1 paginăPowershell ScriptAbhijeet KumarÎncă nu există evaluări
- DCDIAG-Before IP FLIPDocument5 paginiDCDIAG-Before IP FLIPAbhijeet KumarÎncă nu există evaluări
- Azure AD InstallationDocument33 paginiAzure AD InstallationAbhijeet KumarÎncă nu există evaluări
- Azure AD SynchronizationDocument6 paginiAzure AD SynchronizationAbhijeet KumarÎncă nu există evaluări
- Construction InspectionDocument1.153 paginiConstruction Inspectionjazmontz0% (1)
- MQX Rtos PDFDocument23 paginiMQX Rtos PDFcadornetti100% (1)
- Bender IR485 486 DB UpdatedDocument4 paginiBender IR485 486 DB UpdatedUrsula JohnsonÎncă nu există evaluări
- Baupunkt 32-133iDocument2 paginiBaupunkt 32-133itravel for photoÎncă nu există evaluări
- Subscriber Data Usage-2018!04!13Document10 paginiSubscriber Data Usage-2018!04!13Andrew NkhuwaÎncă nu există evaluări
- EE 2355-DEM 1-LibreDocument26 paginiEE 2355-DEM 1-LibreAmit GurungÎncă nu există evaluări
- SIB in LTEDocument19 paginiSIB in LTEsinafe0% (1)
- JW Player Quick Start GuideDocument7 paginiJW Player Quick Start Guidemaj1k123Încă nu există evaluări
- Hallett 15xs ManualDocument44 paginiHallett 15xs ManualLuis Martinez SanchezÎncă nu există evaluări
- AngloGold Ashanti Geologist PDFDocument1 paginăAngloGold Ashanti Geologist PDFashfa ulyaÎncă nu există evaluări
- Standard For Industrial Enclosed Gear Drives (Metric Edition)Document67 paginiStandard For Industrial Enclosed Gear Drives (Metric Edition)Nicole Suarez50% (2)
- Important Emissions Recall: UB4 Evaporative Emissions CanisterDocument2 paginiImportant Emissions Recall: UB4 Evaporative Emissions CanisterAyman RiyadhÎncă nu există evaluări
- CiscoDocument42 paginiCiscoSergio Julian Sivincha QuispeÎncă nu există evaluări
- Chapter 3 Lab 3-5, OSPF Challenge Lab: TopologyDocument3 paginiChapter 3 Lab 3-5, OSPF Challenge Lab: Topologysmil01Încă nu există evaluări
- Wifisky Wireless AdapterDocument9 paginiWifisky Wireless AdapterVan HusenÎncă nu există evaluări
- Calibration ProcedureDocument2 paginiCalibration ProcedureSairam Edupuganti100% (1)
- Eletrostatica Big BagsDocument3 paginiEletrostatica Big BagsNicolas150956Încă nu există evaluări
- D5983Document3 paginiD5983rimi7alÎncă nu există evaluări
- MarketingDocument12 paginiMarketingRoopasreeÎncă nu există evaluări
- 8155 Is An Integrated RamDocument22 pagini8155 Is An Integrated RamVipan SharmaÎncă nu există evaluări
- GS - EP - PVV - 158 - EN MaterialsDocument74 paginiGS - EP - PVV - 158 - EN MaterialswilÎncă nu există evaluări
- 6.1 Physical Non-Synchronized Random Access ProcedureDocument161 pagini6.1 Physical Non-Synchronized Random Access ProcedureLAVANYA MURALIÎncă nu există evaluări
- HIMax System ManualDocument122 paginiHIMax System ManualIsmail ShahidÎncă nu există evaluări
- Execution Procedure For Pipe Connection Tie in and Hot TapzDocument7 paginiExecution Procedure For Pipe Connection Tie in and Hot TapzyuwantoniÎncă nu există evaluări
- As 2419 1 2005 Fire Hydrant Installations System Design Installation and Commissioning PDFDocument9 paginiAs 2419 1 2005 Fire Hydrant Installations System Design Installation and Commissioning PDFtamago_fuji100% (1)
- B24 Power Meter RegistersDocument27 paginiB24 Power Meter RegistersRoy ChaiÎncă nu există evaluări
- Windows CFG Gen User GuideDocument5 paginiWindows CFG Gen User GuideOrlando Villabona BolañosÎncă nu există evaluări
- 158-Calculation of Short Circuit CurrentsDocument24 pagini158-Calculation of Short Circuit Currentsgeorgel1980100% (2)