Documente Academic
Documente Profesional
Documente Cultură
A Comparison of The Performance and Scalability of Xen and KVM Hypervisors PDF
Încărcat de
Raywon Teja KDescriere originală:
Titlu original
Drepturi de autor
Formate disponibile
Partajați acest document
Partajați sau inserați document
Vi se pare util acest document?
Este necorespunzător acest conținut?
Raportați acest documentDrepturi de autor:
Formate disponibile
A Comparison of The Performance and Scalability of Xen and KVM Hypervisors PDF
Încărcat de
Raywon Teja KDrepturi de autor:
Formate disponibile
A comparison of the performance and scalability of
Xen and KVM hypervisors
Stefan Gabriel Soriga
Mihai Barbulescu
Information and Communication Technology Dept.
University POLITEHNICA of Bucharest
Bucharest, Romania
stefan.soriga@upb.ro
Information and Communication Technology Dept.
University POLITEHNICA of Bucharest
Bucharest, Romania
mihai@roedu.net
Abstract Virtualization is the fundamental technology for
corporate data center consolidation and cloud computing.
Companies and academic institutions consolidate their servers
through virtualization in search for efficient hardware resource
usage, lower energy consumption, improved fault tolerance, and
increased security. In this paper, we investigate the performance
and scalability of two open source virtualization platforms: Xen
and Kernel-based Virtual Machine (KVM). We analyze the
influence of the number of virtual machines on the performance
of several benchmarks that measure compute power, network,
and I/O throughput. Virtual machines are running on top of a
single physical host. The results show that these two
virtualization solutions have similar behavior. An important
degradation in the performance is noticed when the number of
virtual machines equals or exceeds the number of physical core
available. Hyper-threading boots the performance by a small
margin. The effect of virtualization on I/O throughput is even
more noticeable, although virtual machines were using LVM
logical volumes as disk images in our tests.
Keywordsserver virtualization; hypervizor; Xen; KVM;
benchmark
I.
INTRODUCTION
In recent years server virtualization has become very
important because it consolidates workloads for more efficient
resource utilization. The traditional server-per-workload
paradigm is typically underutilized. Because many of these
workloads dont play well with others and each needs its own
dedicated machine, most servers use only a small fraction of
their overall processing capabilities (10% to 20% of their
possible capacity) [1]. Virtualization has the capability of
isolating the running environments, so workloads of different
type can share the same hardware. Server virtualization
addresses this very issue. We say that a computer server is
virtualized when a single physical machine is made to appear
as multiple isolated virtual machines (VM). The server is called
host and the virtual machines running on it are called guests.
Each guest has its own virtual processor, memory and
peripheral interfaces, and is capable of running its own
operating system, called guest OS.
The virtual imitation of the hardware layer that allows the
guest OS to run without modifications, unaware that it is
running on emulated hardware, is called full virtualization. In
full virtualization, the guest OS is running unmodified, but the
virtual machine suffer serious performance penalties due to the
extra layers of abstraction provided by an additional software
that simulates the hardware behavior, called hypervisor. The
hypervisor runs on top of the physical hardware and creates the
virtual environment on which the virtual machines operate. Its
functions include scheduling, memory management, and
resource control for various virtual machines.
More performance oriented, the para-virtualized machine
approach (PVM) requires a modified guest OS capable of
making system calls to the hypervisor, rather than executing
machine I/O instructions that the hypervisor simulates.
Whenever an instruction is to be executed, a call is made to the
hypervisor and the hypervisor performs the necessary task on
behalf of the guest. Para-virtualization provides near-native
performance and the appearance of complete and secure
isolation at the hardware level. The disadvantage consists in the
required modified operating system.
In this respect, the Hardware Virtual Machine (HVM)
represents a more flexible solution. HVM is a platform
virtualization approach that enables efficient full virtualization
using help from hardware capabilities, primarily virtualization
extensions in processors. Hardware-assisted virtualization was
added to x86 processor (Intel VT-x or AMD-V) in 2006. HVM
does not need a modified kernel and the guest OS has direct
access to processor, so the performance in HVM will be better
than that in full virtualization.
In the following sections we will evaluate Xen and KVM,
two open source hypervisors that can run natively on Linux.
The rest of this paper is organized as follows. Section II
describes briefly the architecture of Xen and KVM. Section III
evaluates the performance and scalability of the hypervisors
using a series of benchmarks. Section IV discusses some
related works, and Section V summarizes our findings.
II.
HYPERVISORS DESCRIPTION
A. Xen hypervisor
Xen is an open source hypervisor originally developed at
the University of Cambridge and now distributed by Citrix
Systems, Inc. The first public release of Xen occurred in 2003
[6]. It is designed for various hardware platforms, especially
x86, and supports a wide range of guest operating systems,
including Windows, Linux, Solaris and versions of the BSD
family.
Xen architecture consists of a hypervisor, a host OS and a
number of guests. In Xen terminology, the host OS is referred
to as the Domain 0 (dom0) and the guest OS is referred to as
Domain U (domU). Dom0 is created automatically when the
system boots. Although it runs on top of the hypervisor itself,
and has virtual CPUs (vCPUs) and virtual memory, as any
other guest, Dom0 is privileged. It provides device drivers for
the I/O devices, it runs user space services and management
tools, and is permitted to use the privileged control interface to
hypervisor. It also performs all other OS related functions. Like
a DomU, Dom0 can be any operating system in the Linux,
Solaris, and BSD family. As we see, Xen separates the
hypervisor execution from Dom0. In this way, the series of
tasks that are not related to processing the virtualized guests
performed by Dom0 do not influence the hypervisor, ensuring
maximum performance.
Xen employs para-virtualization from the very beginning.
Through para-virtualization, Xen can achieve very high
performance, but it has the disadvantage of supporting Linux
only; and that Linux has to have a modified kernel and
bootloader, and a fixed layout with two partitions, one for hard
disk and one for swap.
Xen also implements support for hardware-assisted
virtualization. In this configuration, it does not require
modifying the guest OS, which make it possible to host
Windows guests.
B. KVM hypervisor
KVM is a hardware-assisted virtualization developed by
Qumranet, Inc and was merged with upstream mainline Linux
kernel in 2007, giving the Linux kernel native virtualization
capabilities. KVM make use of the virtualization extensions
Intel VT-x and AMD-V. In 2008, Red Hat, Inc acquired
Qumranet.
KVM is a kernel module to the Linux kernel, which
provides the core virtualization infrastructure and turns a Linux
host into a hypervisor. Scheduling of processes and memory is
handled through the kernel itself. Device emulation is handle
by a modified version of QEMU [7]. The guest is actually
executed in the user space of the host and it looks like a regular
process to the underlying host kernel.
A normal Linux process has two modes of execution:
kernel mode and user mode. KVM adds a third one: guest
mode. When a guest process is executing non-I/O guest code, it
will run in guest mode. All the guests running under KVM are
just regular linux processes on the host. Each and every virtual
CPU of your KVM guests is implemented using a Linux
thread. The Linux scheduler is responsible for scheduling a
virtual CPU, as it is a normal thread. This brings the advantage
that you can set priorities and affinity for these processes using
normal adjusting commands, and use all the common linux
utilities related to processes. Also, control groups can be
created and used to limit resources that each guest can consume
on a host. In KVM, guest physical memory is just a chunk of
host virtual memory. So it can be swapped, shared, backed by
large pages, backed by a disk file, and is also NUMA aware.
KVM supports I/O para-virtualization using virtio
subsystem. Virtio is a virtualization standard for device
(network, disk, etc.) drivers where the guests device driver is
aware of running in a virtual environment, and communicates
directly with the hypervisor. This enables the guests to get high
performance network and disk operations. Virtio is different,
but architecturally similar to Xen para-virtualized device
drivers.
C. Linux support for Xen and KVM hypervisors
After the acquisition of XenSource by Citrix Systems, Inc,
in 2007, and the acquisition of Qumranet by Red Hat, Inc, the
Linux community started to migrate from Xen to KVM. In
2009, Red Hat decided to move forward with KVM instead of
Xen and integrated KVM into Red Hat Enterprise Linux
(RHEL) distribution. As a result, Xen was present in RHEL 5.x
distributions, but no longer supported in the next iteration,
RHEL 6.x. Having vendor-supplied kernels increases the
likelihood that sites would deploy a type of hypervisor or
another, and this was a big step forward for KVM. Xen is an
open source project but not so tightly integrated with the Linux
community and Linux kernel as KVM. KVM is part of the
Linux kernel, and inherits from it everything from device
management, CPU scheduling, sophisticated memory
management (NUMA, huge pages) or scalable I/O stack,
isolation, security and hardware enablement. Instead, Xen
hypervisor is a separate project and a completely separate code
base. This means that Xen kernel does not support all the
hardware and features that are available on Linux kernel.
Without being part of upstream kernel, development of Xen is
entirely a separate process and you need to install the Xen
kernel on bare metal and build a special guest Dom0 to manage
it and to provide device drivers. But today this is not anymore
the complicated process of compiling the source code of a
modified kernel. Linux mainline kernel tree from version 3.0
onwards includes every component needed for Linux to run
both as a Dom0 and a guest. This means that Linux 3.0 or
higher can be used unmodified as a Dom0 and that paravirt
drivers for Xen in a DomU used for accelerated disk and NIC
are available in any Linux 3.x+ guest, just like KVM virtio
drivers. As a result of the inclusion of Xen in mainline kernel
currently it is available in CentOS 6.x through Xen4Centos
project. The Xen4Centos project is the result of collaboration
between the Xen Project, the Citrix Xen open source teams, the
CentOS developers, GoDaddy Cloud Operations team, and
Rackspace Hosting. Xen4CentOS delivers the Xen stack, a
Linux kernel based on the 3.4 mainline tree, libvirt and QEMU
with associated tools that target Xen support in the distribution.
Although CentOS is a clone of RHEL, Red Hat will obviously
continue to focus on KVM as their primary method of
virtualization. Overall, KVM does have a slight advantage in
the Linux camp of being the default mainline hypervisor. If
you're getting a recent Linux kernel, you've already got KVM
built in.
III.
PERFORMANCE AND SCALABILITY EVALUATION
When evaluating a virtualization platform, the first thing
we would like to find out is how many virtual machines can
run on the host. This number largely depends on the nature of
the virtual machines, whether they are compute-intensive, diskintensive, or network-intensive. In this section we show the
results obtained from the different benchmarks targeted to
stress exactly these parts. Initially, we describe the hardware
and software used in the host and in the guests.
A. Hardware and software configuration
The hardware we used as host for our evaluation is a HP
ProLiant DL180 G6 with the following characteristics:
2 Intel Xeon X5670 six-core @ 2.93 GHz CPUs, with
support for Intel-VT hardware extension;
192 GB DDR3 ECC Registered RAM @ 1066 MHz;
8 HP Compaq x 450 GB SAS, 15K RPM disks
connected to a Smart Array P212 RAID controller
equipped with 256 MB RAM cache memory (disks
configured with RAID 1+0 option, for a total size of 1.6
TB);
1 Broadcom NetXtreme II BCM5709 1Gbps LAN
adapter;
1 Intel 82576 1Gbps LAN adapter. This is used as
bridge for the virtual machines.
The host is connected to a Cisco 2960G gigabit switch with
two network cables, one for each LAN adapter.
In terms of software, the hypervisors were running on a
Centos 6.4 Linux distribution. The guests are using the same
distribution. The hypervisors and the guests have been installed
together on the same hard disk within separate disk partitions,
respectively. In order to obtain the highest possible
performance and scalability of the disk space for the guest
environments we used Logical Volume Manager (LVM) for
partitioning. The disk layout comprised a volume group
dedicated to hypervisors (named hosts), split in two logical
volumes, one for each root partition of the hypervisors, and
another separate volume group (named vms) dedicated to
virtual machines. A separate logical volume represents each
virtual machines hard disk. The main benefit of using LVM in
a system virtualization environment is that it allows for
dynamically enlarging, reducing, adding and deleting disk
space in the form of logical volumes during runtime, taking
snapshots, and cloning virtual machines. In addition to
flexibility, LVM based virtual machine images have less
overhead, because they are not accessed through a filesystem.
The drawback is that you cannot overcommit storage, but in
our evaluation we try to find the right line in respect to
performance, so were not overcommitting anything: CPU,
memory, or storage.
Version of the hypervisors used:
qemu-kvm-0.12.1
xen-hypervisor-4.2.2
Regardless of the type of hypervisor or virtualization
method, all virtual machines were 1 vCPU, 2 GB RAM, and 20
GB hard disk partitioned in a 4 GB swap and 16 GB root
partition. According to conducted tests, VMs were
communicating with the outside world through a bridge
interface configured on the host (one or two interfaces of the
Intel NIC).
B. Benchmarks
We conduct experiments to compare these two
virtualization platforms in respect to one another and evaluate
the overhead introduced by them in comparison to a nonvirtualized environment. We run three sets of benchmarks
targeted to measure the most critical performance parameters
of a machine (CPU, memory, network, and disk access), with
the following tools:
CPU: Hep-Spec06 v1.1
Network: iperf 2.0.5
Disk I/O: iozone 3.408
Each of the benchmarks was executed concurrently on an
increasing number of VMs from 1 to 23 to determine how the
performance degrades as the hosts load increases.
C. CPU performance and scalability
The focus of these CPU tests is to assess the performance
of the hypervisors measuring the number of vCPUs supported.
We tested the same parameters for KVM and Xen, and
compared them with a non-virtualized machine. We intent to
drive the CPU usage in VMs to 100%, and measure the
performance of the guests in order to quantify the differences
for these two virtualization solutions. To accomplish this task,
Hep-Spec06 benchmark is used. Hep-Spec06 is the standard
processor performance benchmarking method in High Energy
Physics (HEP) community. It is based on a subset of the SPEC
CPU2006 benchmark and intended to stress the computer
processor, the memory architecture, the compilers, and the
chipset. Hep-Spec06 does very little I/O, either through NICs
or disk controllers, and doesnt stress the operating system.
This gives us the opportunity to saturate the servers processor
while eliminating other system bottlenecks. Also, the
benchmark has a memory footprint around 2 GB, the same
capacity available to each virtual machine. Since we used an
x86_64 platform, all the experiments were conducted in 64-bit
mode. All the new hardware is 64-bit capable nowadays and
theres little interest in running 32-bit OS or applications.
The maximum number of guests that the hardware can host
depends on the number of physical core. In our testing we have
followed various best practices. It is a well-known fact that
over allocating the number of vCPUs affects not only the
performance of the VM, but the physical server and all the
other VMs on the server. With the objective to analyze the
influence of the hyper-threading (HT), we have run several
tests turning hyper-threading on and off. When HT was on, we
included the logical core of hyper-threading in the number of
physical core [1,8,9]. So to evaluate the impact of the number
of virtual machines deployed per host on the performance, we
considered 11 and 23 VMs, when HT was disabled and
enabled, respectively.
Another well-known guideline is to dedicate one physical
core exclusively to hypervisor and only the rest to the virtual
machines [10,11]. In Xen, the disk and network drivers are
running on Dom0. Dedicating a core only for Dom0 makes
sure Dom0 always has free CPU time to process the I/O
requests for the guests, giving better performance. Moreover,
we have dedicated a fixed amount of 2 GB of memory, and
disabled memory ballooning for Dom0. This optimization is
beneficial especially when running I/O intensive tasks, but
does not hurt for compute intensive tasks either.
Fig. 1 shows the performance comparison of the
hypervisors with and without hyper-threading. Initially, a
single VM was run to determine a base level of performance.
As expected there is a penalty in performance when the number
of VMs per host is increased. The performance of Hep-Spec06
while using hyper-threaded cores is higher than that with HT
off, when the number of VMs exceeds the number of core.
When the number of VMs is 23, tests with hyper-threading on
results in almost 16% better performance for both hypervisors.
Keep in mind that hyper-threading increased the performance
of the bare metal with 30%, from a score of 193.82 to almost
230.8. Interestingly, with 11 VMs deployed, Xen without HT
performs better than KVM with HT on. Nonetheless, there is a
45% to 50% degradation in performance between 11, 12 VMs
case and 23 VMs running in the same time.
Fig. 2 shows a comparison between the Hep-Spec06
benchmark running concurrently on 11 and 12 VMs and the
same benchmark run on physical machine, with HT off. The
performance loss is acceptable. The benefits obtained by
virtualization overcome the minimal performance loss. Xen
performs better again. The average score for 11 VMs running
concurrently was 14.67 for KVM and 16.23 for Xen. When we
increased the number of VMs to 12, the score average
performance level at 14.09 for KVM, and 15.69 for Xen, but
the physical machine was better used.
Fig. 1. Performance comparison of the hypervisors versus the number of VMs
deployed when there is no I/O generated
We run the next tests on 11 VMs, without hyper-threading
because it is easier to do performance comparisons.
D. Network throughput performance
The goal of this experiment is to measure the network
performance of the virtual machines with respect to
throughput. The same hardware and software configuration is
used, with the addition of an external ProLiant DL370 G7
machine, which runs CentOS 6.4 too. No changes were made
in the network parameters of the external machine, hosts, and
guests. The external machine is connected via a Gigabit link to
the same switch as the host. Iperf has been used to measure the
throughput between the VMs and the external machine both in
inbound and outbound directions. VMs are iperf servers in
inbound tests, and iperf clients in outbound tests. A time
parameter of 60 seconds is used. All other default settings
remain the same single TCP stream, 23.2 KB TCP window
size. Each test is repeated 5 times in a row, to make a more
accurate measure.
We started with an initial baseline test. Iperf is run
between the host and the external machine along the 1 Gbps
line to determine the actual line performance. The best line
speed achieved in this test is around 957 Mbps. Then a single
virtual machine is started on the host. Running iperf results in
the usage close to 98% of the network bandwidth. Then the
number of virtual machines running concurrently is increased.
When two VMs are started, the total throughput stays in the
95% to 98% range. However, the bandwidth of VM is reduced
evenly per VM, 475 Mbps each. Fig. 3 shows the results when
are started 2, 4, 8, and 11 VMs.
Fig. 2. Bare metal vs. 11 and 12 VMs aggregate without hyper-threading
Fig. 3. Network throughput vs. number of concurrent VMs
As the number of VMs increases, the bandwidth per VM
decreases. Even the standard deviation is in the same range.
Next tables show the low, high, and average bandwidth for the
VMs and the total bandwidth in Mbps, for KVM and Xen.
They show only inbound throughput as outbound is perfectly
symmetric.
TABLE I. Low, high, and average bandwidth for KVM VMs for Inbound
traffic
No. VMs
2
4
8
11
Low
475
159
70
46
High
475
316
136
136
Average
475
237.5
119.5
86.76
Total
950
950
956.2
954.8
TABLE II. . Low, high, and average bandwidth for KVM VMs for Inbound
traffic
No. VMs
2
4
8
11
Low
474
159
53.9
54
High
476
316
158
158
Average
475
237.5
118.9
86.84
Total
950
950
952.7
954.5
Fig. 4. I/O throughput on bare metal vs. 1 VM
E. Disk I/O throughput
We decided to use a LVM logical volume as disk for virtual
machines. This solution does not limit the I/O performance and
is flexible enough when having to deal with backup, recovery,
and migration. We used virtio disk controller and the default
caching mode (writethrough). The virtio devices are the
paravirtual interfaces for disk I/O. Both hypervisors have this
feature.
The benchmark consists in running iozone ten times in a
row, with the following parameters:
Record size of 64 KB;
File to test size set to 4 GB, double the amount of
memory found in VMs.
Include flush (fsync, fflush) and close() in the timing
calculations.
Use direct I/O for all file operations; tells the filesystem
that all operations are to bypass the buffer cache and go
directly to disk. Direct I/O operations means that the
guest cache is bypassed.
Enable O_RSYNC and O_SYNC.
Fig. 5. I/O throughput comparison for 11 VMs running kvm and xen
The operations mean the following:
Write indicates the performance of writing a new file to
the filesystem.
Rewrite indicates the performance of writing to an
existing file.
This test measured the maximum throughput for six core
operations related to disk performance: write, rewrite, read, reread, random write, and random read. The values given in the
figures represent the average throughput of each operation
(from 10 iterations).
Read indicates the performance of reading a file that
already exists in the filesystem.
Fig. 4 shows the read/write speed performance for bare metal
machine compared to a virtual one, either Xen or KVM. Both
solutions perform badly, especially in disk writing. Fig. 5
shows disk performances when 11 VMs concurrently access
the disk. In this circumstances both solutions performs very
badly compared to the real machine, for all operations.
Random write indicates the performance of writing to a
file in various random locations.
Re-read indicates the performance of reading a file
again.
Random read indicates the performance of reading a file
by reading random information from the file.
IV.
RELATED WORK
There are many papers related to the comparison and
performance evaluation of Xen and KVM, using different
benchmarks. More recent articles are those of Deshane et al.
[2], Xianghua Xu et al. [3], and Andrea Chierici et al. [4, 5].
They all performed quantitative comparisons of Xen and KVM
focusing on overall performance and scalability of the virtual
machines, performance isolation, network and I/O
performance, using tools like hep-spec06, iperf, netperf,
iozone, SysBench, and bonnie++. They tested the hypervisors
in configurations suited primarily on flexibility, like disk on a
file approach or non-virtio drivers for KVM virtual machines.
On the other hand, this technology is evolving very fast. Every
new version of the hypervisors offers optimizations and
features that can influence the decision regarding the
implementation of one over the other. In this paper, we
compared the performance and scalability of virtual machines
in an environment configured particularly for performance,
using the latest versions of hypervisors.
V.
CONCLUSIONS
Our benchmarks showed that on the basis of scalability
both hypervisors perform very well. In terms of CPU
performance provided, KVM and Xen are comparable, with a
small advantage for Xen. The performance drops with the
number of VMs that exceeds the number of physical core.
Hyper-threading has a positive impact, although on a small
margin of 16%.
Network performance is practically the same for both
hypervisors. The guests accessed the network through a bridge
interface configured a on the host. As shown with the
networking testing, the default it is to distribute the bandwidth
as evenly as possible between all VMs. Both hypervisors do
this very well, with practically the same output.
Compared to bare metal, virtual disk I/O is the most
problematic aspect for virtualization. Particularly when
multiple machines concurrently access the disk. Even for a
single VM, the I/O throughput is around 30% to 50% lower
than that of the real hardware. On the other hand, the
performance of this version of KVM is very good compared
with previous versions. The optimizations added to this version
of KVM are obvious.
VI.
FUTURE WORK
These tests gave us some input on future investigations
using the Windows operating system in the near future. But in
the long term, besides server consolidation, we are moving to a
storage area network environment with NetApp storage and
fibre channel (FC). In this case, we intent to compare two open
source solutions for enterprise class consolidation: oVirt and
XenServer. One is based on KVM, the other on Xen.
XenServer is available as a free open source virtualization
platform since version 6.2.
REFERENCES
[1]
SGI technical white paper, Virtualization Best Practices on SGI Altix
UV 1000 using Red Hat Enterprise Linux 6.0 KVM, april 2011.
[2] T. Deshane, Z. Shepherd, J. Matthews, M. Ben-Yehuda, A. Shah and B.
Rao,Quantitative Comparison of Xen and KVM, Xen Summit., June
23-24, 2008.
[3] Xianghua Xu, Feng Zhou, Jian Wan Yucheng Jiang, Quantifying
Performance Properties of Virtual Machine,International Symposium
on Information Science and Engieering, 2008.
[4] A. Chierici and R. Veraldi, A quantitative comparison between xen and
kvm, 17th International Conference on Computing in High Energy and
Nuclear Physics (CHEP09), J. Phys.: Conf. Ser. 219 042005, Part 4,
2010.
[5] A. Chierici and D. Salomoni, Increasing performance in KVM
virtualization within a Tier-1 environment, International Conference on
Computing in High Energy and Nuclear Physics (CHEP2012), J. Phys.:
Conf. Ser. 396 032024, Part 3, 2012.
[6] Paul Barham, Boris Dragovic, Keir Fraser, Steven Hand, Tim Harris,
Alex Ho, Rolf Neugebauer, Ian Pratt and Andrew Warfield, Xen and
the Art of Virtualization,vezi Proceedings of the ACM Symposium on
Operating Systems Principles, 2003.
[7] A. Singh, An Introduction to Virtualization, kernelthread.com,
January 2004
[8] HP Technical white paper, Performance characterization of Citrix
XenServer on HP BladeSystem, , feb. 2010.
[9] HP Technical white paper, Scalability of bare-metal and virtualized HP
ProLiant servers in 32- and 64-bit HP Server Based Computing
environments, 2012.
[10] IBM technical white paper, Best practices for KVM, 2nd Ed, april
2012.
[11] IBM technical white paper, Tunning KVM for performance, 2nd Ed,
april 2012.
S-ar putea să vă placă și
- Huawei: Exam H12-721Document112 paginiHuawei: Exam H12-721Arif MohdÎncă nu există evaluări
- Background Verification ServicesDocument14 paginiBackground Verification Servicesmohitgarg08Încă nu există evaluări
- ThesisDocument148 paginiThesisabdiÎncă nu există evaluări
- Amada Operators ManualDocument110 paginiAmada Operators ManualJeff Dunn86% (7)
- DHomesb Chapter 1 - CCNA DiscoveryDocument6 paginiDHomesb Chapter 1 - CCNA DiscoveryAbdullah Al HawajÎncă nu există evaluări
- HCIA - Storage CourseDocument16 paginiHCIA - Storage CourseAndrea MurgiaÎncă nu există evaluări
- 7 Maintaning PayshieldDocument16 pagini7 Maintaning PayshieldBruno NunesÎncă nu există evaluări
- Abm Principles of Marketing Module 6 9Document10 paginiAbm Principles of Marketing Module 6 9Trixie GallanoÎncă nu există evaluări
- CCNA Discovery Working at A Small-To-Medium Business or ISP (Version 4.1) Final ExamDocument17 paginiCCNA Discovery Working at A Small-To-Medium Business or ISP (Version 4.1) Final ExamJesusforgivemeÎncă nu există evaluări
- HCIA-AI - HCDA Test PreparationsDocument22 paginiHCIA-AI - HCDA Test PreparationsAkram AlkouzÎncă nu există evaluări
- HCIA-Datacom V1.0 Training MaterialDocument987 paginiHCIA-Datacom V1.0 Training Materialjunaid ahmedÎncă nu există evaluări
- Modernize Your Data Center Network With An Ethernet VPN VirtualDocument45 paginiModernize Your Data Center Network With An Ethernet VPN VirtualThuan Nguyen100% (1)
- FortiAnalyzer 6.2 CookbookDocument62 paginiFortiAnalyzer 6.2 CookbookEDGAÎncă nu există evaluări
- DEA-41T1 - Associate - PowerEdge Version 2.0 (DCA)Document2 paginiDEA-41T1 - Associate - PowerEdge Version 2.0 (DCA)Arnaldo Jonathan Alvarado RuizÎncă nu există evaluări
- ВопросыDocument12 paginiВопросыRoman Travin33% (3)
- Performance Analysis of Selected Hypervisors (Virtual Machine Monitors - VMMS)Document6 paginiPerformance Analysis of Selected Hypervisors (Virtual Machine Monitors - VMMS)Ricardo LuizÎncă nu există evaluări
- Huawei Premium H12-211 by VCEplus 325q PDFDocument160 paginiHuawei Premium H12-211 by VCEplus 325q PDFyaya konateÎncă nu există evaluări
- Huawei Prep4sure H12-211 v2021-04-28 by Jude 227qDocument111 paginiHuawei Prep4sure H12-211 v2021-04-28 by Jude 227qGebg BuglezÎncă nu există evaluări
- Correct Answer: ADocument76 paginiCorrect Answer: Amark jayÎncă nu există evaluări
- Huawei Certkey H12-211 v2018-11-19 by - Julian 127qDocument59 paginiHuawei Certkey H12-211 v2018-11-19 by - Julian 127qABDULLAÎncă nu există evaluări
- h12-261 v3.0 (451) - (Translated From Chinese To English)Document94 paginih12-261 v3.0 (451) - (Translated From Chinese To English)Ali TopalanÎncă nu există evaluări
- Aziz PDFDocument2 paginiAziz PDFAziz Ur RehmanÎncă nu există evaluări
- Ipsec On Huawei Ar Router PDFDocument5 paginiIpsec On Huawei Ar Router PDFHussein DhafanÎncă nu există evaluări
- HCIP Datacom Advanced RS H12 831 - V1.0 ENUDocument123 paginiHCIP Datacom Advanced RS H12 831 - V1.0 ENUguido.martini100% (2)
- ASR1002-HX Datasheet: Quick SpecDocument4 paginiASR1002-HX Datasheet: Quick SpecC KÎncă nu există evaluări
- Exam H12-222 - V2.5-ENU: The Safer, Easier Way To Help You Pass Any IT ExamsDocument91 paginiExam H12-222 - V2.5-ENU: The Safer, Easier Way To Help You Pass Any IT ExamsfishÎncă nu există evaluări
- H12-221 Exam QuestionsDocument66 paginiH12-221 Exam QuestionsmohammadÎncă nu există evaluări
- ENSDWI Training New ENSDWI QuestionsDocument17 paginiENSDWI Training New ENSDWI QuestionsCesar Campos LimaÎncă nu există evaluări
- CCNA 3 v7 Modules 13 - 14: Emerging Network Technologies Exam AnswersDocument11 paginiCCNA 3 v7 Modules 13 - 14: Emerging Network Technologies Exam AnswersLeandro J. HinestrozaÎncă nu există evaluări
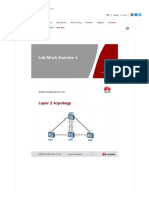
- H12-261 HCIE-R - S Lab Mock Exercise 1 - Huawei Training - CertificationDocument8 paginiH12-261 HCIE-R - S Lab Mock Exercise 1 - Huawei Training - CertificationGustavo BacaláÎncă nu există evaluări
- FortiOS-6.4-VMware ESXi Cookbook PDFDocument56 paginiFortiOS-6.4-VMware ESXi Cookbook PDFHari KumavatÎncă nu există evaluări
- H12-224-Enu V10.02 Hcip-R&s 31 - 12 - 2019Document70 paginiH12-224-Enu V10.02 Hcip-R&s 31 - 12 - 2019Khalat OmerÎncă nu există evaluări
- ITN Practice Skills Assessment - Packet TracerDocument3 paginiITN Practice Skills Assessment - Packet TracerArnaldo CosÎncă nu există evaluări
- 100 REAL TIME COMPUTER NETWORKING Multiple Choice Questions and Answers PDFDocument14 pagini100 REAL TIME COMPUTER NETWORKING Multiple Choice Questions and Answers PDFSufian IqbalÎncă nu există evaluări
- H12-711.exam.30q: Website: VCE To PDF Converter: Facebook: TwitterDocument17 paginiH12-711.exam.30q: Website: VCE To PDF Converter: Facebook: Twitterdeltakio@gmail.comÎncă nu există evaluări
- Hcip VCDocument73 paginiHcip VC1q2w3e4tÎncă nu există evaluări
- IP Static Routes - Attempt ReviewDocument2 paginiIP Static Routes - Attempt ReviewBilz Elly100% (1)
- Port Security On Huawei Switches PDFDocument2 paginiPort Security On Huawei Switches PDFHussein DhafanÎncă nu există evaluări
- Southbound API communication between SDN controller and network switchesDocument6 paginiSouthbound API communication between SDN controller and network switchesHoai Duc HoangÎncă nu există evaluări
- HCNP NewDocument26 paginiHCNP NewAnonymous cs4BLczEÎncă nu există evaluări
- ENetwork Final Exam CCNA 1 4Document22 paginiENetwork Final Exam CCNA 1 4Jay LeeÎncă nu există evaluări
- DTMF Using FPGADocument16 paginiDTMF Using FPGATejas DharaniÎncă nu există evaluări
- H12-711 Exam A QuestionsDocument18 paginiH12-711 Exam A QuestionsIct labÎncă nu există evaluări
- H13-629.prepaway - Premium.exam.364q: Number: H13-629 Passing Score: 800 Time Limit: 120 Min File Version: 2.0Document111 paginiH13-629.prepaway - Premium.exam.364q: Number: H13-629 Passing Score: 800 Time Limit: 120 Min File Version: 2.0Talel ZidiÎncă nu există evaluări
- Smartzone Admin GuideDocument5 paginiSmartzone Admin GuideDilshan ChandimaÎncă nu există evaluări
- CCNA QuestionsDocument29 paginiCCNA QuestionsfelipemunozmoraÎncă nu există evaluări
- HCIP-Routing & Switching-IENP V2.5 Exam Outline PDFDocument3 paginiHCIP-Routing & Switching-IENP V2.5 Exam Outline PDFصلاح الدينÎncă nu există evaluări
- Proxmox VE HA Cluster SetupDocument4 paginiProxmox VE HA Cluster SetupDhani MultisolutionÎncă nu există evaluări
- CCNA (200-301) Certification Practice Exam Answers (ENSA v7.0)Document54 paginiCCNA (200-301) Certification Practice Exam Answers (ENSA v7.0)samiÎncă nu există evaluări
- Final Discovery 3 100%Document20 paginiFinal Discovery 3 100%Trần Ngọc Ngàn100% (2)
- H12-311 - Exam A Questions and AnswersDocument24 paginiH12-311 - Exam A Questions and Answersandreu cerdan50% (2)
- Network Virtualization Techniques and Technologies ExplainedDocument47 paginiNetwork Virtualization Techniques and Technologies ExplainedamarmudirajÎncă nu există evaluări
- VRRP On Huawei Router PDFDocument7 paginiVRRP On Huawei Router PDFHussein DhafanÎncă nu există evaluări
- Fos 801 PwrecoverynotesDocument23 paginiFos 801 PwrecoverynotesHam Za0% (1)
- Nse7 - Efw-6.4 (KP) V8.02Document56 paginiNse7 - Efw-6.4 (KP) V8.02Geraud TchadaÎncă nu există evaluări
- Huawei H12-224 Exam QuestionsDocument56 paginiHuawei H12-224 Exam QuestionsАвто СледÎncă nu există evaluări
- CCNA v4 Accessing The Wan CH 1 100%Document3 paginiCCNA v4 Accessing The Wan CH 1 100%richmone73Încă nu există evaluări
- WIRELESS+AND+MOBILE+NETWORKING Seme2 2006Document2 paginiWIRELESS+AND+MOBILE+NETWORKING Seme2 2006api-26171521Încă nu există evaluări
- C.1 Test BankDocument24 paginiC.1 Test Bankmikewang001Încă nu există evaluări
- CAMEL: Intelligent Networks for the GSM, GPRS and UMTS NetworkDe la EverandCAMEL: Intelligent Networks for the GSM, GPRS and UMTS NetworkEvaluare: 2 din 5 stele2/5 (1)
- About SiWIMDocument29 paginiAbout SiWIMFrancesco GinesiÎncă nu există evaluări
- Verification of AMBA Bus Model Using SystemVerilogDocument5 paginiVerification of AMBA Bus Model Using SystemVerilogdoomachaleyÎncă nu există evaluări
- Mba-Pgdba Referee FormDocument2 paginiMba-Pgdba Referee FormHanung PurbakusumaÎncă nu există evaluări
- Yash Port Folio-MinDocument21 paginiYash Port Folio-Minyash petamberÎncă nu există evaluări
- User Guide: Echolife Hg520C Home GatewayDocument25 paginiUser Guide: Echolife Hg520C Home Gatewayluis PavilaÎncă nu există evaluări
- Chapter 4Document38 paginiChapter 4WANÎncă nu există evaluări
- Father of Indonesian EducationDocument9 paginiFather of Indonesian EducationFarah Fatimatuz ZahraÎncă nu există evaluări
- MULTEMP PS No. 2 - TDSDocument1 paginăMULTEMP PS No. 2 - TDSVishal AmleÎncă nu există evaluări
- E WasteDocument8 paginiE Wasteanon-815109100% (1)
- Geii2 Internship Report ManglaDocument22 paginiGeii2 Internship Report ManglaNeel ChayetunÎncă nu există evaluări
- A Study On Customer Preferences of The Products and Services Offered by Media Industry With Special Reference To Magnik IndiaDocument8 paginiA Study On Customer Preferences of The Products and Services Offered by Media Industry With Special Reference To Magnik IndiaResearch ParkÎncă nu există evaluări
- Fatigue Test of Alsi10mgDocument26 paginiFatigue Test of Alsi10mg180320119134.me.rayush.hariÎncă nu există evaluări
- MP 60 and MP 80 Miniature Usb 20 Power Meters Fiberchek Pro Integration Data Sheets enDocument2 paginiMP 60 and MP 80 Miniature Usb 20 Power Meters Fiberchek Pro Integration Data Sheets enRocky LeeÎncă nu există evaluări
- IISc Postdoc Application FormDocument3 paginiIISc Postdoc Application FormBineshÎncă nu există evaluări
- Activation Functions in Neural Networks - GeeksforGeeksDocument12 paginiActivation Functions in Neural Networks - GeeksforGeekswendu felekeÎncă nu există evaluări
- Laboratory Exercise No. 2-C Sieve Analysis and Abrasion Test of AggregatesDocument4 paginiLaboratory Exercise No. 2-C Sieve Analysis and Abrasion Test of AggregatesHaziel DizonÎncă nu există evaluări
- Iso 20000-1Document4 paginiIso 20000-1Dr-MohamedLashinÎncă nu există evaluări
- BloodspireDocument37 paginiBloodspirediegoff77Încă nu există evaluări
- Talos: Technical SpecificationsDocument2 paginiTalos: Technical SpecificationsAkinbuja 'SolaÎncă nu există evaluări
- POLYCAB - MV Power Cable IEC 60502 2Document32 paginiPOLYCAB - MV Power Cable IEC 60502 2AmitabhaÎncă nu există evaluări
- How To Render A WallDocument2 paginiHow To Render A WallMoe Zaw OoÎncă nu există evaluări
- Chapter 2 Research - Shiela MaeDocument6 paginiChapter 2 Research - Shiela MaeKate Alyzza TubatoÎncă nu există evaluări
- Gauranshi Jain MBA A Dr. Smita RamakrishnaDocument27 paginiGauranshi Jain MBA A Dr. Smita RamakrishnaPRAKHAR GUPTAÎncă nu există evaluări
- Test preparation document with listening comprehension questionsDocument11 paginiTest preparation document with listening comprehension questionsLove YouÎncă nu există evaluări
- NACA ACR L4L07 - Tests of A Curtiss Propeller On P47CDocument36 paginiNACA ACR L4L07 - Tests of A Curtiss Propeller On P47CAnonymous xD8wUeMyÎncă nu există evaluări
- Assignment HPGD3103 Instructional Technologies September 2022 Semester - Specific InstructionDocument21 paginiAssignment HPGD3103 Instructional Technologies September 2022 Semester - Specific Instructionhafiz zikriÎncă nu există evaluări