Documente Academic
Documente Profesional
Documente Cultură
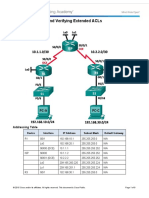
Cisco Instructor Fast Track Practical Test 2 Topology Diagram
Încărcat de
Sammy LinDescriere originală:
Titlu original
Drepturi de autor
Formate disponibile
Partajați acest document
Partajați sau inserați document
Vi se pare util acest document?
Este necorespunzător acest conținut?
Raportați acest documentDrepturi de autor:
Formate disponibile
Cisco Instructor Fast Track Practical Test 2 Topology Diagram
Încărcat de
Sammy LinDrepturi de autor:
Formate disponibile
Cisco Instructor Fast Track Practical Test 2 Topology Diagram
VLAN Table VLAN 10 20 30 Name Marketing Finance IT Network 10.1.1.0/24 10.1.2.0/24 10.1.3.0/24
DLCI Mappings Table From/To Core R3 R4 Core N/A 305 405 R3 503 N/A 403 R4 504 304 N/A
IP Addressing Table Device R1 Interface Fa0/0.10 Fa0/0.20 Fa0/0.30 S0/0/0 Fa0/0 R2 S0/0/0 Fa0/0 S0/0/0 Fa0/0 S0/0/0 S0/0/0 S0/0/1 S0/1/0 S0/1/1 ISP Server 1 Server 2 PC1 PC2 PC3 PC4 PC5 PC6 Fa0/0 S0/0/0 NIC NIC NIC NIC NIC NIC NIC NIC IP Address Subnet Mask Gateway 192.168.1.1 192.168.1.1
100.1.1.9 192.168.1.1 100.1.1.13 10.1.4.1 100.1.1.3 10.1.5.1 100.1.1.4
R3 R4
255.255.255.25 2 255.255.255.24 8 255.255.255.25 2 255.255.255.0 255.255.255.24 8 255.255.255.0 255.255.255.24 8 255.255.255.24 8 255.255.255.25 2 255.255.255.0 255.255.255.24 8 255.255.255.24 8 DHCP DHCP DHCP DHCP DHCP 255.255.255.0
Core
100.1.1.5 200.1.1.253 201.1.1.1 192.168.1.2 192.168.1.3
201.1.1.2
201.1.1.1
DHCP Pool Table Pool Name P1 P2 P3 P4 P5 Network 10.1.1.0 10.1.2.0 10.1.3.0 10.1.4.0 10.1.5.0
IP Address Assignment Assign the first host address of each VLAN to the sub-interface of router R1. Others Use 64000 as the clock rate. Use FSKTM for any password Task 1: Switch and Server Configurations Configure the hostname for S1. Create the VLANs on S1 based on the table and then configure the appropriate interfaces as access port or trunk port. Assign the static IP to the Server 1, Server 2 and PC6. Task 2: Routers Configurations Configure the hostname for R1 and assign the IP address to the appropriate interfaces. Configure Inter-VLAN routing on R1. Then, configure PPP PAP Authentication on the Serial link between R1 and Core. Configure the hostname for R2 and assign the IP address to the appropriate interfaces. Then, configure PPP CHAP Authentication on the serial link between R2 and Core. Configure the hostname for R3 and assign the IP address to the appropriate interfaces. Then, configure frame relay encapsulation using static mapping. Configure the hostname for R4 and assign the IP address to the appropriate interfaces. Then, configure frame relay encapsulation using static mapping. R4 is using the IETF encapsulation. Configure the hostname for Core and assign the IP address to the appropriate interfaces. Then, configure frame relay encapsulation for S0/1/0 using static mapping. The Frame Relay Cloud is using ANSI as the LMI Type. Configure the hostname for ISP and assign the IP address to the appropriate interfaces. Task 3: DHCP Configurations Configure the DHCP on Core router base on the DHCP Pool table. Exclude the first 5 IP addresses from each pool. Configure the default gateway for each pool. Task 4: NAT Configurations Configure the static NAT for Server 1 (200.1.1.249) and Server 2 (200.1.1.250).
Create a pool name NAT-POOL that translates other private IP addresses to an available IP address in the 200.1.1.225 200.1.1.238 range. Use access-list 5 for all the addresses that are eligible to be translated. Task 5: Routing Configure RIP version 2 on R1, R2, R3 and R4. Disable routing updates to the LANs. Configure RIP version 2 on Core router. Advertise all subnets except 200.1.1.252 network. Disable routing updates to ISP. Configure a default route on Core router using the exit-interface argument to send all default traffic to ISP. Propagate the default route to the neighbors. Configure two static routes on the ISP router to the global IP addresses of Core router using the exit-interface argument. The global IP addresses are used for Static NAT and Dynamic NAT. Task 6: ACL Configurations Configure an access-list 1 that prohibits traffic from 10.1.4.0 network from reaching 10.1.1.0 network. Apply the ACL on the appropriate router and interface. Configure an access-list 2 that prohibits traffic from 10.1.2.0 network from reaching 10.1.5.0 network. Apply the ACL on the appropriate router and interface. Configure an access-list 101 that block 10.1.3.0 network to access the FTP service on Server 1 but allow Web access to the Server 1. All other access from 10.1.3.0 network should be denied. Apply the ACL on the appropriate router and interface. Configure an access-list 102 that block 10.1.4.0 network to access to Server 2. All other access should be allowed. Apply the ACL on the appropriate router and interface. Configure an access-list 103 that allow Web access from PC6 to the Server 1. All other access should be denied. Apply the ACL on the appropriate router and interface.
S-ar putea să vă placă și
- CompTIA A+ Complete Review Guide: Core 1 Exam 220-1101 and Core 2 Exam 220-1102De la EverandCompTIA A+ Complete Review Guide: Core 1 Exam 220-1101 and Core 2 Exam 220-1102Evaluare: 5 din 5 stele5/5 (2)
- CompTIA Network+ CertMike: Prepare. Practice. Pass the Test! Get Certified!: Exam N10-008De la EverandCompTIA Network+ CertMike: Prepare. Practice. Pass the Test! Get Certified!: Exam N10-008Încă nu există evaluări
- Cisco CCNA Command Guide: An Introductory Guide for CCNA & Computer Networking Beginners: Computer Networking, #3De la EverandCisco CCNA Command Guide: An Introductory Guide for CCNA & Computer Networking Beginners: Computer Networking, #3Încă nu există evaluări
- H I ĐĂNG Assigment 3 1641Document17 paginiH I ĐĂNG Assigment 3 1641Huynh Ngoc Hai Dang (FGW DN)Încă nu există evaluări
- Modern Assembly Language Programming with the ARM ProcessorDe la EverandModern Assembly Language Programming with the ARM ProcessorÎncă nu există evaluări
- CBT For BDDDocument13 paginiCBT For BDDGregg Williams100% (5)
- Network with Practical Labs Configuration: Step by Step configuration of Router and Switch configurationDe la EverandNetwork with Practical Labs Configuration: Step by Step configuration of Router and Switch configurationÎncă nu există evaluări
- VoLTE and ViLTE: Voice and Conversational Video Services over the 4G Mobile NetworkDe la EverandVoLTE and ViLTE: Voice and Conversational Video Services over the 4G Mobile NetworkÎncă nu există evaluări
- Advanced Raspberry Pi: Raspbian Linux and GPIO IntegrationDe la EverandAdvanced Raspberry Pi: Raspbian Linux and GPIO IntegrationÎncă nu există evaluări
- CCST Cisco Certified Support Technician Study Guide: Networking ExamDe la EverandCCST Cisco Certified Support Technician Study Guide: Networking ExamÎncă nu există evaluări
- Extrajudicial Settlement of Estate Rule 74, Section 1 ChecklistDocument8 paginiExtrajudicial Settlement of Estate Rule 74, Section 1 ChecklistMsyang Ann Corbo DiazÎncă nu există evaluări
- Data Communication and Networking: For Under-graduate StudentsDe la EverandData Communication and Networking: For Under-graduate StudentsÎncă nu există evaluări
- CCNA Interview Questions You'll Most Likely Be AskedDe la EverandCCNA Interview Questions You'll Most Likely Be AskedÎncă nu există evaluări
- Analyze and Design Sewer and Stormwater Systems with SewerGEMSDocument18 paginiAnalyze and Design Sewer and Stormwater Systems with SewerGEMSBoni ClydeÎncă nu există evaluări
- Alcatel-Lucent Service Routing Architect (SRA) Self-Study Guide: Preparing for the BGP, VPRN and Multicast ExamsDe la EverandAlcatel-Lucent Service Routing Architect (SRA) Self-Study Guide: Preparing for the BGP, VPRN and Multicast ExamsÎncă nu există evaluări
- Mrs. Universe PH - Empowering Women, Inspiring ChildrenDocument2 paginiMrs. Universe PH - Empowering Women, Inspiring ChildrenKate PestanasÎncă nu există evaluări
- Uniform-Section Disk Spring AnalysisDocument10 paginiUniform-Section Disk Spring Analysischristos032Încă nu există evaluări
- Network Security All-in-one: ASA Firepower WSA Umbrella VPN ISE Layer 2 SecurityDe la EverandNetwork Security All-in-one: ASA Firepower WSA Umbrella VPN ISE Layer 2 SecurityÎncă nu există evaluări
- Exploring BeagleBone: Tools and Techniques for Building with Embedded LinuxDe la EverandExploring BeagleBone: Tools and Techniques for Building with Embedded LinuxEvaluare: 4 din 5 stele4/5 (2)
- Multicore DSP: From Algorithms to Real-time Implementation on the TMS320C66x SoCDe la EverandMulticore DSP: From Algorithms to Real-time Implementation on the TMS320C66x SoCÎncă nu există evaluări
- ARM Microcontrollers Programming for Embedded SystemsDe la EverandARM Microcontrollers Programming for Embedded SystemsEvaluare: 5 din 5 stele5/5 (1)
- WebRTC: APIs and RTCWEB Protocols of the HTML5 Real-Time Web, Third EditionDe la EverandWebRTC: APIs and RTCWEB Protocols of the HTML5 Real-Time Web, Third EditionEvaluare: 5 din 5 stele5/5 (1)
- IP Routing Protocols All-in-one: OSPF EIGRP IS-IS BGP Hands-on LabsDe la EverandIP Routing Protocols All-in-one: OSPF EIGRP IS-IS BGP Hands-on LabsÎncă nu există evaluări
- Practical Guide to LTE-A, VoLTE and IoT: Paving the way towards 5GDe la EverandPractical Guide to LTE-A, VoLTE and IoT: Paving the way towards 5GÎncă nu există evaluări
- EWAN NAT/ACL PT Practice SBA ConfigurationDocument9 paginiEWAN NAT/ACL PT Practice SBA Configurationandreajr100% (1)
- Lab 4Document8 paginiLab 4pzydf6wjxvÎncă nu există evaluări
- Routing and Switching Lab - 2019: Anycast TopologyDocument7 paginiRouting and Switching Lab - 2019: Anycast TopologyChinen momoÎncă nu există evaluări
- Lab 7 - Configuring and Verifying Extended ACLsDocument6 paginiLab 7 - Configuring and Verifying Extended ACLsmeerasÎncă nu există evaluări
- 4.2.2.13 Lab - Configuring and Verifying Extended ACLs - ILMDocument16 pagini4.2.2.13 Lab - Configuring and Verifying Extended ACLs - ILMCte eduÎncă nu există evaluări
- Lab 4 Basic PPP Configuration Lab: Topology DiagramDocument6 paginiLab 4 Basic PPP Configuration Lab: Topology DiagramDat LCÎncă nu există evaluări
- Ospf ChallangeDocument7 paginiOspf ChallangeDave RojasÎncă nu există evaluări
- 4.2.2.13 Lab - Configuring and Verifying Extended ACLs - ILMDocument9 pagini4.2.2.13 Lab - Configuring and Verifying Extended ACLs - ILMGuri DhillonÎncă nu există evaluări
- CISCO PACKET TRACER LABS: Best practice of configuring or troubleshooting NetworkDe la EverandCISCO PACKET TRACER LABS: Best practice of configuring or troubleshooting NetworkÎncă nu există evaluări
- WAN TECHNOLOGY FRAME-RELAY: An Expert's Handbook of Navigating Frame Relay NetworksDe la EverandWAN TECHNOLOGY FRAME-RELAY: An Expert's Handbook of Navigating Frame Relay NetworksÎncă nu există evaluări
- ROUTING INFORMATION PROTOCOL: RIP DYNAMIC ROUTING LAB CONFIGURATIONDe la EverandROUTING INFORMATION PROTOCOL: RIP DYNAMIC ROUTING LAB CONFIGURATIONÎncă nu există evaluări
- LEARN MPLS FROM SCRATCH PART-B: A Beginners guide to next level of networkingDe la EverandLEARN MPLS FROM SCRATCH PART-B: A Beginners guide to next level of networkingÎncă nu există evaluări
- Bluetooth Application Programming with the Java APIsDe la EverandBluetooth Application Programming with the Java APIsÎncă nu există evaluări
- First Hop Redundancy Protocol: Network Redundancy ProtocolDe la EverandFirst Hop Redundancy Protocol: Network Redundancy ProtocolÎncă nu există evaluări
- Cisco Packet Tracer Implementation: Building and Configuring Networks: 1, #1De la EverandCisco Packet Tracer Implementation: Building and Configuring Networks: 1, #1Încă nu există evaluări
- Internet of Things: Architectures, Protocols and StandardsDe la EverandInternet of Things: Architectures, Protocols and StandardsÎncă nu există evaluări
- TCP/IP: Network+ Protocols And Campus LAN Switching FundamentalsDe la EverandTCP/IP: Network+ Protocols And Campus LAN Switching FundamentalsÎncă nu există evaluări
- IP MULTICAST ROUTING Part -3: Use of multicast routing.De la EverandIP MULTICAST ROUTING Part -3: Use of multicast routing.Încă nu există evaluări
- IPTV Delivery Networks: Next Generation Architectures for Live and Video-on-Demand ServicesDe la EverandIPTV Delivery Networks: Next Generation Architectures for Live and Video-on-Demand ServicesSuliman Mohamed FatiÎncă nu există evaluări
- Empanelment of Architect-Consultant - Work Costing More Than 200 Lacs. (Category-B)Document6 paginiEmpanelment of Architect-Consultant - Work Costing More Than 200 Lacs. (Category-B)HARSHITRAJ KOTIYAÎncă nu există evaluări
- Cover Letter PDFDocument1 paginăCover Letter PDFAli EjazÎncă nu există evaluări
- Letter From Attorneys General To 3MDocument5 paginiLetter From Attorneys General To 3MHonolulu Star-AdvertiserÎncă nu există evaluări
- Statistical Quality Control, 7th Edition by Douglas C. Montgomery. 1Document76 paginiStatistical Quality Control, 7th Edition by Douglas C. Montgomery. 1omerfaruk200141Încă nu există evaluări
- EIRA v0.8.1 Beta OverviewDocument33 paginiEIRA v0.8.1 Beta OverviewAlexQuiñonesNietoÎncă nu există evaluări
- CENG 5503 Intro to Steel & Timber StructuresDocument37 paginiCENG 5503 Intro to Steel & Timber StructuresBern Moses DuachÎncă nu există evaluări
- Dance Appreciation and CompositionDocument1 paginăDance Appreciation and CompositionFretz Ael100% (1)
- White Box Testing Techniques: Ratna SanyalDocument23 paginiWhite Box Testing Techniques: Ratna SanyalYogesh MundhraÎncă nu există evaluări
- A Princess of Mars Part 3Document4 paginiA Princess of Mars Part 3Sheila Inca100% (1)
- Mpu 2312Document15 paginiMpu 2312Sherly TanÎncă nu există evaluări
- AVR Instruction Set Addressing ModesDocument4 paginiAVR Instruction Set Addressing ModesSundari Devi BodasinghÎncă nu există evaluări
- Ielts Practice Tests: ListeningDocument19 paginiIelts Practice Tests: ListeningKadek Santiari DewiÎncă nu există evaluări
- Technical Specification of Heat Pumps ElectroluxDocument9 paginiTechnical Specification of Heat Pumps ElectroluxAnonymous LDJnXeÎncă nu există evaluări
- Maxx 1657181198Document4 paginiMaxx 1657181198Super UserÎncă nu există evaluări
- Objective Mech II - IES 2009 Question PaperDocument28 paginiObjective Mech II - IES 2009 Question Paperaditya_kumar_meÎncă nu există evaluări
- EC GATE 2017 Set I Key SolutionDocument21 paginiEC GATE 2017 Set I Key SolutionJeevan Sai MaddiÎncă nu există evaluări
- C4 ISRchapterDocument16 paginiC4 ISRchapterSerkan KalaycıÎncă nu există evaluări
- Baobab MenuDocument4 paginiBaobab Menuperseverence mahlamvanaÎncă nu există evaluări
- Endangered EcosystemDocument11 paginiEndangered EcosystemNur SyahirahÎncă nu există evaluări
- Draft SemestralWorK Aircraft2Document7 paginiDraft SemestralWorK Aircraft2Filip SkultetyÎncă nu există evaluări
- 1st SemDocument3 pagini1st SemARUPARNA MAITYÎncă nu există evaluări
- Methods to estimate stakeholder views of sustainabilityDocument7 paginiMethods to estimate stakeholder views of sustainabilityAlireza FatemiÎncă nu există evaluări
- Busbar sizing recommendations for Masterpact circuit breakersDocument1 paginăBusbar sizing recommendations for Masterpact circuit breakersVikram SinghÎncă nu există evaluări
- Critical Methodology Analysis: 360' Degree Feedback: Its Role in Employee DevelopmentDocument3 paginiCritical Methodology Analysis: 360' Degree Feedback: Its Role in Employee DevelopmentJatin KaushikÎncă nu există evaluări