Documente Academic
Documente Profesional
Documente Cultură
MFE Encryption Android WP
Încărcat de
ValeRodasDescriere originală:
Drepturi de autor
Formate disponibile
Partajați acest document
Partajați sau inserați document
Vi se pare util acest document?
Este necorespunzător acest conținut?
Raportați acest documentDrepturi de autor:
Formate disponibile
MFE Encryption Android WP
Încărcat de
ValeRodasDrepturi de autor:
Formate disponibile
best practices for
encryption in android
developer.motorola.com/enterprise
introduction
Android has featured commercial and government-grade encryption
libraries from its earliest releases. The Android encryption libraries
make it possible for organizations to protect data on a mobile device
with the highest level of security. The best data security practice is
to keep all corporate data on servers behind the frewall and use the
mobile device to access it there. But sometimes storing corporate data
locally on a mobile device cannot be avoided (for example, if an app
needs to keep working even when there is no data connection).
There are numerous examples within the world of encryption where
mistakes have compromised security goals. Some of the security librar-
ies in the javax.crypto package have non-obvious APIs, and reference
material can be thin and hard to fnd. This white paper draws together
a number of best practices to use when designing Android apps that
depend on encryption. This is not an exhaustive list. It is a starting point
to raise awareness about the kinds of issues you need to consider
when working with working with symmetric key encryption software.
WHITE PAPER BEST PRACTICES FOR ENCRYPTION IN ANDROID 2
Figure 1
Overview of
Encryption
SECRET
MEETING
SECRET
MEETING
Sender gives receiver
a copy of the key they
will use.
Sender encrypts the
plaintext to produce a
ciphertext which she
sends to her contact.
Receiver gets the ciphertext
and uses his copy of the key
to decrypt it, revealing a copy
of the plaintext.
CIPHERTEXT
To review sample source code which implements this complete process, please refer to
Using the Advanced Encryption Standard in Android Technical Article.
http://developer.motorola.com/docs/using_the_advanced_encryption_standard_in_android/
WHITE PAPER BEST PRACTICES FOR ENCRYPTION IN ANDROID 3
best practices
Encryption best practices fall into two categories - practices that relate to good security discipline
generally, and practices that relate to software design and development.
GOOD SECURITY DISCIPLINE:
1. Assume that anything stored on the device can be read by someone who has physical
possession of the device.
In particular, never store the plaintext secret key on the device. One way to avoid storing the secret
key on the device is to generate the secret key whenever you need it, by deriving it from a human-
friendly password supplied by prompting the user. This technique is described with sample code in
the technical article at reference 4 at the end of this paper.
Although encryption doesnt prevent an attacker from reading the encrypted bits from a fle, it pre-
vents him from seeing the decrypted data. Mobile Device Management consoles have the remote
wipe feature because of the assumption that anything stored on the device can be
read by someone who has the device (regardless of fle permissions, user IDs, etc).
2. Use standard security algorithms to solve standard security problems.
An example of failure to use standard algorithms is the Content Scramble System
used to assert Digital Rights Management (DRM) on DVD movies. A proprietary
algorithm was created for this application. Its faws were revealed by reverse engi-
neering, and it was broken within a couple of years. Shortly after that, it was sepa-
rately discovered that errors in the design of the algorithm reduced the effective
size of the key to only 16 bits. The reduced key made brute force attacks (trying
every key in the key space) not just feasible, but trivial. A major factor behind the
movie industrys promotion of Blu-ray video players is to greatly strengthen DRM
controls (in addition to support for larger fles and high defnition formats).
3. The admonition to use standard security algorithms extends to using
standard implementations of those algorithms.
An example where this best practice was not followed concerned an early imple-
mentation of Unix. A replacement terminal login manager was written. This compo-
nent is part of the security framework, and prompts for a username/password pair
to check for authorized access. Unlike more secure versions of the component, this
implementation checked that the username existed, before checking the password.
If the username did not exist, there was no password to check against, and it
immediately returned a failure. If the username did exist, the login manager would
go on to check the password, which took a fractionally longer time. The slight dif-
ference in timing between password comparison and no password comparison
was enough to leak information about whether a username was valid or not.
If you need to create an
encrypted session between a
client and a server, your frst
thought should be to design
it as a web service using an
HTTPS session, rather than
designing a new protocol.
HTTPS is a well-tested and
standard way to create and
maintain a special-purpose
VPN connection between a
browser and a web server.
Use the libraries provided
with the device. If you need
an algorithm that does not
come with the device, source
it from an established
security organization.
WHITE PAPER BEST PRACTICES FOR ENCRYPTION IN ANDROID 4
4. Consider requesting a design review by a security professional.
Be very careful when designing systems that use encryption. It is easy to make small mistakes
which degrade or even eliminate the security measures.
SOFTWARE DESIGN AND DEVELOPMENT:
5. Avoid the use of Javas String class.
Everything relating to holding plaintexts, encrypting, decrypting, salts, initialization vectors, seeds,
passwords and keys should be done with char arrays or byte arrays. Oracles Java documentation
explains why:
Objects of type String are immutable, i.e., there are no methods defned that allow you to change
(overwrite) or zero out the contents of a String after usage. This feature makes String objects unsuit-
able for storing security sensitive information such as user passwords. You should always collect and
store security sensitive information in a char array instead.
As a practical matter, Androids EditText feld has Strings assigned into it at various points in the
implementation. So you cannot follow this best practice and use an Android EditText component to
collect a password or plaintext. The string you get back from EditText may remain visible to a process
that can dump your memory including interned Strings at some later point. Java solves the problem
in its Swing GUI library by having a JPasswordField method that returns a char array, not a String.
One Android solution is to create a new View based on android.graphics.Canvas,
with a key listener for accepting individual characters and assembling them into a
char[ ].
6. Be certain to use high quality key generation algorithms when you use
password-based encryption.
The UTF-8 character encoding specifed for Android restricts the valid values of
bytes. The encoding allows up to 4 bytes for a character, in theory supporting 4.2
billion different values, but UTF-8 only has 1.1 million different characters. So the effective keyspace
is a lot smaller than the theoretical keyspace. PKCS#5 is the current gold standard for password-
based encryption.
Androids character encoding can be problematic in other ways, too. The character encoding used
when converting a String into individual bytes is always UTF-8 in Android, but varies among J2SE
implementations. Therefore whenever you construct a String, or you get the individual bytes repre-
senting a string with String.getBytes(), you should specify the character set to use in translation. If
Android Input Method Editors
also make extensive use of
Strings, and are thus open to
the same vulnerability (post-
execution memory dump
harvesting of involuntarily-
retained interned Strings).
char [ ] getPassword();
WHITE PAPER BEST PRACTICES FOR ENCRYPTION IN ANDROID 5
you forget to do this, your code will compile, but fail to work correctly when ported to a J2SE imple-
mentation that uses a non-UTF-8 character set.
7. Use unpredictable Initialization Vectors.
Some block cipher modes require an Initialization Vector (IV). The IV is picked at
random at the beginning of the encryption process, and it is there to introduce addi-
tional randomness into the ciphertext. The IV is typically transmitted to the recipi-
ent in a plaintext header prepended to the ciphertext. A different IV must be used
for each message. Its acceptable for an attacker to know what IV was used for a
particular message, but the attacker must not be able to predict the IV that will be
used in a future message.
The requirement for an unpredictable IV was also overlooked in SSL/TLS prior to
version 1.1. In those widespread early versions, the last block of the ciphertext for
message n was used as the IV for message n+1. The IV was thus completely pre-
dictable to an eavesdropper. In summer 2011, this was the basis of a chosen plaintext man-in-the-
middle attack on SSL (a theoretical attack by a couple of security researchers, not an actual
onslaught by career criminals). The penetration was styled the BEAST attack, for Browser Exploit
Against SSL/TLS. You can read more about it in reference 5 at the end of this paper.
A common novice mistake is
to use low order digits from
the system clock to provide
a random number. If the
attacker is on the same
machine (generally assumed),
he has perfect foreknowl-
edge of the values coming
from the system clock.
Figure 2
Man in the Middle Attack
wea ancwsen nttncken wea senven
Web browser: for example, a user accesses her banking records online and transfers funds between accounts.
Attacker: intercepts the packets, and rewrites the account number to divert funds to an account he controls.
He then passes the changed packet to the server.
Web server: receives packets from the attacker, does what is requested, and returns an acknowledgement.
Attacker: intercepts the reply from the server, and modifes it to hide evidence of the change from the user.
WHITE PAPER BEST PRACTICES FOR ENCRYPTION IN ANDROID 6
8. Do not use any message key indefnitely.
Keep a count of messages sent using this key and replace each key when it
approaches the limit. After sending 2
^
48 AES blocks with CBC, the probability of
decryption shifts too much in favor of an attacker. You must change the key at this
point. DES and 3DES require a key change after just 2
^
16 blocks. This is one of the
reasons why AES has a larger block size than older algorithms like DES or 3DES.
AES allows you to encrypt signifcantly more data before you have to change the key.
AES has another mode, known as counter mode, that lets you use the same key
up to 2
^
64 times. Developers are gradually transitioning to this slightly more involved
counter mode (it requires an additional parameter, known as a number used once,
usually abbreviated to nonce).
9. The setSeed() method of SecureRandom should only be used to generate
predictable runs for testing.
Class java.security.SecureRandom is used to generate cryptographically secure pseudo-random numbers.
The class has a method setSeed() that causes the instance to return a predictable sequence of numbers.
Many programmers assume from the name that calling setSeed() always resets the internal state of the
random number generator. In reality, once you have started to receive random numbers by calling next-
Bytes(), setSeed() does not cause a reset. It uses the new seed to augment the randomness produced.
The method would be more accurately named something like addMoreEntropy().
This incorrect assumption makes it easy for careless programmers to pass the same arguments to
setSeed(), but later get an unexpectedly different key back from generateKey(). The use of setSeed()
outside of testing is generally an indication of faulty design or coding.
To reliably generate a copy of a key starting from a password, you should use a PBE
(password-based encryption) algorithm. Never use the user password itself as the
seed to SecureRandom, as that makes brute force attacks too easy. Use the class
java.security.SecureRandom to generate a seed number or an initialization vector.
These seed values dont have to be kept secret, but you must remember them for
future use with this message.
conclusion
As most software developers readily appreciate, the proper use of encryption in mobile software is both sub-
tle and complex. We have reviewed a number of real world examples of faws that transform a seemingly-
secure system into a system which is not resistant to attack, or - even worse - which actively leaks data.
The best practices advocated here do not comprise an exhaustive list, but are intended to convey the
subtleties of the subject. For acceptable security, software developers are well advised to take college level
encryption courses, and use an understanding of the material in their work.
DES uses a block size of 8
bytes and requires a key
change after 2
^
16 blocks.
So you can only send
65K * 8 bytes (0.5 MB)
before a keychange.
AES supports 2
^
48 * 16
bytes (4.5 billion MB) when
using CBC mode, before a
key change is needed.
For acceptable security,
software developers are well
advised to take college level
encryption courses, and use
an understanding of the
material in their work. Visit an
online cryptography class to
learn more.
developer.motorola.com/enterprise
Screen images simulated, enhanced to show detail. MOTOROLA and the Stylized M Logo are registered trademarks of
Motorola Trademark Holdings, LLC. Android is a trademark of Google Inc. The Android robot is reproduced or modifed from
work created and shared by Google and used according to terms described in the Creative Commons 3.0 Attribution License.
All other product and service names are the property of their respective owners. 2012 Motorola Mobility, Inc. All rights reserved.
REFERENCES
1. Handbook of Applied Cryptography: the public-spirited authors have made their work available as a
free download from http://cacr.uwaterloo.ca/hac/, with a hardcover version available for purchase.
Computer security professionals frequently refer to this book, though it does not cover techniques
developed in the last decade (like AES).
2. A websearch for online cryptography class will provide many hits, including some free classes that
are offered by top US universities: http://www.google.com/#q=online+cryptography+class
3. See http://docs.oracle.com/javase/1.5.0/docs/guide/security/jce/JCERefGuide.html#PBEEx
to review the admonition about use of Java Strings in cryptographic applications.
4. http://developer.motorola.com/docs/using_the_advanced_encryption_standard_in_android
- a MOTODEV technical article walking through a coding example using encryption.
5. More details on the 2011 BEAST attack on SSL/TLS can be found at:
http://blogs.cisco.com/security/beat-the-beast-with-tls/
about motodev for enterprise
MOTODEV for Enterprise offers a wealth of information on developing secure enterprise apps, covering
topics such as secure connectivity, the Android permissions model, signing Android applications, certif-
cates and VPNs, and developing secure HTML5 apps. Youll fnd technical articles, best practice guides,
webinars, podcasts, tech support and more to support you throughout the development lifecycle.
For more information. visit: http://moto.ly/enterprisesecurity
S-ar putea să vă placă și
- Shoe Dog: A Memoir by the Creator of NikeDe la EverandShoe Dog: A Memoir by the Creator of NikeEvaluare: 4.5 din 5 stele4.5/5 (537)
- Grit: The Power of Passion and PerseveranceDe la EverandGrit: The Power of Passion and PerseveranceEvaluare: 4 din 5 stele4/5 (587)
- Hidden Figures: The American Dream and the Untold Story of the Black Women Mathematicians Who Helped Win the Space RaceDe la EverandHidden Figures: The American Dream and the Untold Story of the Black Women Mathematicians Who Helped Win the Space RaceEvaluare: 4 din 5 stele4/5 (894)
- The Yellow House: A Memoir (2019 National Book Award Winner)De la EverandThe Yellow House: A Memoir (2019 National Book Award Winner)Evaluare: 4 din 5 stele4/5 (98)
- The Little Book of Hygge: Danish Secrets to Happy LivingDe la EverandThe Little Book of Hygge: Danish Secrets to Happy LivingEvaluare: 3.5 din 5 stele3.5/5 (399)
- On Fire: The (Burning) Case for a Green New DealDe la EverandOn Fire: The (Burning) Case for a Green New DealEvaluare: 4 din 5 stele4/5 (73)
- The Subtle Art of Not Giving a F*ck: A Counterintuitive Approach to Living a Good LifeDe la EverandThe Subtle Art of Not Giving a F*ck: A Counterintuitive Approach to Living a Good LifeEvaluare: 4 din 5 stele4/5 (5794)
- Never Split the Difference: Negotiating As If Your Life Depended On ItDe la EverandNever Split the Difference: Negotiating As If Your Life Depended On ItEvaluare: 4.5 din 5 stele4.5/5 (838)
- Elon Musk: Tesla, SpaceX, and the Quest for a Fantastic FutureDe la EverandElon Musk: Tesla, SpaceX, and the Quest for a Fantastic FutureEvaluare: 4.5 din 5 stele4.5/5 (474)
- A Heartbreaking Work Of Staggering Genius: A Memoir Based on a True StoryDe la EverandA Heartbreaking Work Of Staggering Genius: A Memoir Based on a True StoryEvaluare: 3.5 din 5 stele3.5/5 (231)
- The Emperor of All Maladies: A Biography of CancerDe la EverandThe Emperor of All Maladies: A Biography of CancerEvaluare: 4.5 din 5 stele4.5/5 (271)
- The Gifts of Imperfection: Let Go of Who You Think You're Supposed to Be and Embrace Who You AreDe la EverandThe Gifts of Imperfection: Let Go of Who You Think You're Supposed to Be and Embrace Who You AreEvaluare: 4 din 5 stele4/5 (1090)
- The World Is Flat 3.0: A Brief History of the Twenty-first CenturyDe la EverandThe World Is Flat 3.0: A Brief History of the Twenty-first CenturyEvaluare: 3.5 din 5 stele3.5/5 (2219)
- Team of Rivals: The Political Genius of Abraham LincolnDe la EverandTeam of Rivals: The Political Genius of Abraham LincolnEvaluare: 4.5 din 5 stele4.5/5 (234)
- The Hard Thing About Hard Things: Building a Business When There Are No Easy AnswersDe la EverandThe Hard Thing About Hard Things: Building a Business When There Are No Easy AnswersEvaluare: 4.5 din 5 stele4.5/5 (344)
- Devil in the Grove: Thurgood Marshall, the Groveland Boys, and the Dawn of a New AmericaDe la EverandDevil in the Grove: Thurgood Marshall, the Groveland Boys, and the Dawn of a New AmericaEvaluare: 4.5 din 5 stele4.5/5 (265)
- The Unwinding: An Inner History of the New AmericaDe la EverandThe Unwinding: An Inner History of the New AmericaEvaluare: 4 din 5 stele4/5 (45)
- The Sympathizer: A Novel (Pulitzer Prize for Fiction)De la EverandThe Sympathizer: A Novel (Pulitzer Prize for Fiction)Evaluare: 4.5 din 5 stele4.5/5 (119)
- Her Body and Other Parties: StoriesDe la EverandHer Body and Other Parties: StoriesEvaluare: 4 din 5 stele4/5 (821)
- Ol8 HardeningDocument38 paginiOl8 HardeningdominusceoÎncă nu există evaluări
- 10.1007 978 3 319 58808 7Document369 pagini10.1007 978 3 319 58808 7AJÎncă nu există evaluări
- Oracle Adapter R3 Implementation GuideDocument80 paginiOracle Adapter R3 Implementation GuideFJAutosysuserÎncă nu există evaluări
- Codeks V10 EN Instructions For USERSDocument11 paginiCodeks V10 EN Instructions For USERSamel hrvicÎncă nu există evaluări
- Checklist How To Test A Mobile App r1Document1 paginăChecklist How To Test A Mobile App r1Sike ThedeviantÎncă nu există evaluări
- Infographics About Digital Footprint & Digital CitizenshipDocument2 paginiInfographics About Digital Footprint & Digital CitizenshipAifah HernandezÎncă nu există evaluări
- Server For NIS Step-By-Step GuideDocument27 paginiServer For NIS Step-By-Step GuidedrajbhatnagarÎncă nu există evaluări
- Health Card Registration User GuideDocument42 paginiHealth Card Registration User GuidesundarkspÎncă nu există evaluări
- contents-auction-QFPIRA000HBW-QFPIRA00T4ST-!QFPIRA00T526DMU Technical Assistance Manual PDFDocument72 paginicontents-auction-QFPIRA000HBW-QFPIRA00T4ST-!QFPIRA00T526DMU Technical Assistance Manual PDFtsdcnÎncă nu există evaluări
- Reka Sap HR Pa NotesDocument24 paginiReka Sap HR Pa Notestekkie4Încă nu există evaluări
- Opmanager User GuideDocument185 paginiOpmanager User Guidetiki2003Încă nu există evaluări
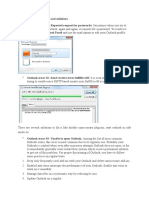
- Common Outlook Issues and SolutionsDocument3 paginiCommon Outlook Issues and SolutionsJennie KimÎncă nu există evaluări
- Instructions On Azure MFA Enrollment and Reset: User InstructionDocument10 paginiInstructions On Azure MFA Enrollment and Reset: User InstructionEDWIN MUTAIÎncă nu există evaluări
- Esi Online GuidlinesDocument53 paginiEsi Online GuidlinesBharat AhujaÎncă nu există evaluări
- Packetstorm Google Dorks ListDocument476 paginiPacketstorm Google Dorks ListSteven Mason80% (5)
- 5127 902 E.3 Omnikey 5x27ck Keyboard Wedge User GuideDocument94 pagini5127 902 E.3 Omnikey 5x27ck Keyboard Wedge User GuidedmitriyfurÎncă nu există evaluări
- LoginDocument2 paginiLoginAnonymous s9rPRqLÎncă nu există evaluări
- Verify login functionality and create account validation of TT projectDocument12 paginiVerify login functionality and create account validation of TT projecthemantrulzÎncă nu există evaluări
- Fac ViewDocument152 paginiFac ViewannilneilzÎncă nu există evaluări
- Common Problems and SolutionsDocument6 paginiCommon Problems and SolutionsArshad HussainÎncă nu există evaluări
- Sediv ManualDocument66 paginiSediv ManualHoàng Quân100% (4)
- A Research Paper For Data Privacy PAHUNANG FINALDocument9 paginiA Research Paper For Data Privacy PAHUNANG FINALBomer RangÎncă nu există evaluări
- Reverse Password Synchronization With IBM Tivoli Identity Manager Redp4299Document22 paginiReverse Password Synchronization With IBM Tivoli Identity Manager Redp4299bupbechanhÎncă nu există evaluări
- All in 1 PDFDocument625 paginiAll in 1 PDFAbdur Rahman Sarker (Abid)Încă nu există evaluări
- Callisto Terminal Commands GuideDocument8 paginiCallisto Terminal Commands Guidenicolás_lorréÎncă nu există evaluări
- Chapter 1 3Document25 paginiChapter 1 3Haciel BautistaÎncă nu există evaluări
- TradeCast Tutorial - FullDocument91 paginiTradeCast Tutorial - Fulljamilhaider100% (1)
- How To Integrate ISONAS Pure Access and Entrust Datacard TruCredentialDocument9 paginiHow To Integrate ISONAS Pure Access and Entrust Datacard TruCredentialGamaliel AranedaÎncă nu există evaluări
- Tense Limited ECommerce Website ProposalDocument15 paginiTense Limited ECommerce Website ProposalJVTC CorporationÎncă nu există evaluări
- Software Requirements Specification Template - Skype-Software-Requirement-Specification-SrsDocument37 paginiSoftware Requirements Specification Template - Skype-Software-Requirement-Specification-SrsSuryansh raiÎncă nu există evaluări