Documente Academic
Documente Profesional
Documente Cultură
A Quick Guide To CISSP Certification
Încărcat de
zoophagousimmunohistochemistryTitlu original
Drepturi de autor
Formate disponibile
Partajați acest document
Partajați sau inserați document
Vi se pare util acest document?
Este necorespunzător acest conținut?
Raportați acest documentDrepturi de autor:
Formate disponibile
A Quick Guide To CISSP Certification
Încărcat de
zoophagousimmunohistochemistryDrepturi de autor:
Formate disponibile
A quick guide to CISSP certification
CISSP
CISSP Exam Notes will help you pass CISSP exam It is concise, to-the-point, and quick way to determine if you are ready for the CISSP exam
Draft Version 43 Date of Publish: 19 September 2009
RAFEEQ UR REHMAN, CISSP
Chapter One: Information Security and Risk Management
Copyright Notice This book is copyright 2009 of Rafeeq Ur Rehman and Conformix Technologies Inc. No part of this book can be distributed or reproduced in any form or shape without written permission of the Author and the Publisher.
Disclaimer The book is made available without any direct, indirect, or implied warranty of any kind, including the correctness of material presented here. The author and the publisher of this book are not responsible for any direct or indirect loss as a result of use of this book.
Trademarks and Service Marks All references to trademarks and service marks used in this book are the property of respective owners. Published By Rafeeq Rehman ISBN13: 978-0-9724031-1-5 ISBN: 0-9724031-1-6 Web: http://www.cisspbook.com Latest Edition of this book is always available on this web site. Email: rafeeq.rehman@gmail.com
Copyright 2009 Rafeeq Rehman
Page: 2 of 93
Chapter One: Information Security and Risk Management
Table of Contents
1 Information Security and Risk Management .......................................................................... 10 1.1 Definitions......................................................................................................................... 10 1.2 Introduction ....................................................................................................................... 11 1.3 Basic Principles ................................................................................................................. 12 1.4 Availability ........................................................................................................................ 14 1.4.1 Avoiding Single Points of Failure ............................................................................. 14 1.5 Data Classification ............................................................................................................ 14 1.6 Personnel Security ............................................................................................................ 15 1.7 Risk Management and Risk Lifecycle .............................................................................. 16 1.8 Security Policies and Standards security policy and standards .......................................17 1.9 Education and Awareness education and awareness ...................................................... 18 1.10 Roles and Responsibilities................................................................................................ 18 1.11 Attacks and Vulnerabilities .............................................................................................. 18 1.12 Miscellaneous.................................................................................................................... 19 2 Access Control .......................................................................................................................... 21 2.1 Definitions......................................................................................................................... 21 2.2 Access Control ................................................................................................................... 22 2.2.1 Access Control Types................................................................................................. 25 2.3 Remote Authentication..................................................................................................... 25 2.4 Biometrics ......................................................................................................................... 26 2.5 Passwords Security ........................................................................................................... 26 2.6 Identity Management and Directory Services ................................................................. 27 2.6.1 Kerberos..................................................................................................................... 28 2.6.2 Light Weight Directory Access Protocol or LDAP .................................................... 29 2.6.3 OpenID ...................................................................................................................... 29 2.6.4 NTLM ......................................................................................................................... 30 2.6.5 Microsoft Active Directory Active Directory ............................................................ 30 2.7 Controlling Access in Networks ....................................................................................... 30 2.8 Types of Access Controls .................................................................................................. 31 2.9 Access Control Monitoring ............................................................................................... 31 2.10 Attacks and Vulnerabilities .............................................................................................. 31 3 Cryptography ............................................................................................................................ 33 3.1 Terminology ...................................................................................................................... 33 3.2 Introduction ...................................................................................................................... 34 3.3 Alogrithms......................................................................................................................... 35 3.3.1 Digital Encryption Standard (DES) .......................................................................... 35 3.3.2 Triple Digital Encryption Standard (3DES) ............................................................. 35 3.3.3 Advanced Encryption Standard or AES AES ........................................................... 36 3.4 Public Key Cryptography .................................................................................................. 36 3.4.1 RSA Algorithm........................................................................................................... 37 3.5 PGP .................................................................................................................................... 37 3.6 Hashing ............................................................................................................................. 37 3.7 Encrypting Data-At-Rest .................................................................................................. 38 3.8 Public Key Infrastructure (PKI) ....................................................................................... 38 3.8.1 Digital Certificates ..................................................................................................... 39 3.8.2 Certificate and Key Management Key Management ................................................ 41 3.9 Attacks and Vulnerabilities .............................................................................................. 42
Copyright 2009 Rafeeq Rehman
Page: 3 of 93
Chapter One: Information Security and Risk Management 3.10 Miscellaneous.................................................................................................................... 42 Physical Security ...................................................................................................................... 44 4.1 Definitions......................................................................................................................... 44 4.2 Introduction ...................................................................................................................... 44 4.3 Physical Access Controls .................................................................................................. 45 4.4 Environmental Controls and HVAC ................................................................................. 46 4.5 Fire Control ....................................................................................................................... 47 4.6 Facility Design and Planning............................................................................................ 48 4.7 Monitoring and Surveillance ............................................................................................ 49 4.8 Attacks and Vulnerabilities .............................................................................................. 49 4.9 Miscellaneous.................................................................................................................... 50 5 Security Architecture and Design ............................................................................................ 51 5.1 Definitions......................................................................................................................... 51 5.2 Computer and System Architecture ................................................................................. 51 5.2.1 The Central Processing Unit - CPUCPU ................................................................... 51 5.3 Security Architecture ........................................................................................................ 53 5.4 Models for Access Control ................................................................................................ 53 5.5 Security Certification and Accreditation .......................................................................... 53 5.6 System Evaluation ............................................................................................................ 53 5.7 Attacks and Vulnerabilities .............................................................................................. 53 5.8 Miscellaneous.................................................................................................................... 53 6 Business Continuity and Disaster Recovery............................................................................ 54 6.1 Definitions......................................................................................................................... 54 6.2 Introduction ...................................................................................................................... 55 6.3 Business Impact Analysis (BIA) ....................................................................................... 55 6.4 Parts of Business Continuity Plan (BCP) ......................................................................... 56 6.5 Disaster Recovery Plan (DRP).......................................................................................... 57 6.6 Data Center Recovery ....................................................................................................... 58 6.7 Attacks and Vulnerabilities .............................................................................................. 58 6.8 Miscellaneous.................................................................................................................... 59 7 Telecommunication and Network Security .............................................................................60 7.1 Definitions.........................................................................................................................60 7.2 ISO-OSI Network Model ..................................................................................................60 7.3 TCP/IP Network Layers.................................................................................................... 62 7.3.1 Physical Layer ............................................................................................................ 62 7.3.2 Data Link Layer ......................................................................................................... 62 7.3.3 IP Layer ...................................................................................................................... 63 7.3.4 Transport Layer and TCP/UDP ................................................................................ 63 7.3.5 Application Layer ...................................................................................................... 64 7.4 Network Tiers and Defense-in-Depth defense in depth .................................................. 65 7.5 Network Services Security ................................................................................................ 65 7.5.1 Domain Name System or DNS.................................................................................. 65 7.5.2 Email .......................................................................................................................... 66 7.5.3 Web Servers ............................................................................................................... 66 7.5.4 Telnet ......................................................................................................................... 67 7.5.5 Secure Shell or SSH ................................................................................................... 67 7.5.6 FTP and SFTP ............................................................................................................ 67 7.5.7 TCP Wrappers ........................................................................................................... 67 7.5.8 Network Time Protocol or NTP ................................................................................ 67 7.6 Network Transport Level Security ................................................................................... 68 7.6.1 SSL/TLS SSL TLS ...................................................................................................... 68 4
Copyright 2009 Rafeeq Rehman
Page: 4 of 93
Chapter One: Information Security and Risk Management 7.6.2 IPSec and GRE Tunnels ............................................................................................ 68 7.6.3 Secure Shell (SSH) SSH ............................................................................................ 68 7.7 Firewalls ............................................................................................................................ 68 7.7.1 Application Layer Firewalls and Application Proxies .............................................. 68 7.7.2 Load Balancers .......................................................................................................... 68 7.8 Network Address Translation or NAT ............................................................................. 68 7.9 Remote Access and Virtual Private Networks VPN ......................................................... 68 7.10 Intrusion Detection Systems IDS ..................................................................................... 69 7.11 Commonly Used Ports and Protocols .............................................................................. 70 7.12 Cellular Networks ............................................................................................................. 70 7.12.1 CDMA ........................................................................................................................ 70 7.12.2 GPRS .......................................................................................................................... 70 7.12.3 GSM ........................................................................................................................... 70 7.12.4 3G Wireless ................................................................................................................ 70 7.12.5 EDGE ......................................................................................................................... 70 7.12.6 EVDO ......................................................................................................................... 70 7.13 Voice Over IP or VoIP ....................................................................................................... 70 7.14 Attacks and Vulnerabilities .............................................................................................. 70 7.15 Miscellaneous.................................................................................................................... 70 8 Application Security ..................................................................................................................71 8.1 Definitions..........................................................................................................................71 8.2 Security of Web Based Applications ................................................................................ 72 8.2.1 Three-Tier Architecture ............................................................................................ 72 8.2.2 User Registration and CAPTCHA ............................................................................. 72 8.2.3 Use of SSL .................................................................................................................. 72 8.3 Securing Client/Server Applications ................................................................................ 72 8.4 Single Sign On (SSO) ........................................................................................................ 72 8.5 Cross Company Authentication (CCA)............................................................................. 72 8.6 Common Attacks on Web-Based Applications ................................................................ 72 8.7 Attacks and Vulnerabilities .............................................................................................. 72 8.8 Miscellaneous.................................................................................................................... 72 8.9 Introduction ...................................................................................................................... 72 8.10 Software Development Life Cycle (SDLC) ....................................................................... 73 8.11 Application Security Testing ............................................................................................ 74 8.12 Security of Web Based Applications ................................................................................ 74 8.12.1 Three-Tier Architecture ............................................................................................ 75 8.12.2 User Registration and CAPTCHA ............................................................................. 75 8.12.3 Web Server Security .................................................................................................. 75 8.12.4 Use of SSL .................................................................................................................. 75 8.13 Security Web Services ....................................................................................................... 75 8.14 AJAX and Web 2 Technologies ........................................................................................ 75 8.15 Securing Client/Server Applications ................................................................................ 75 8.16 Single Sign On (SSO SSO) ................................................................................................ 75 8.17 Cross Company Authentication (CCA CCA) .................................................................... 75 8.18 Common Application Attacks and Flaws ......................................................................... 75 8.19 Attacks and Vulnerabilities .............................................................................................. 76 8.20 Miscellaneous.................................................................................................................... 76 9 Operations Security .................................................................................................................. 77 9.1 Definitions......................................................................................................................... 77 9.2 Introduction ...................................................................................................................... 77 9.3 Securing Server ................................................................................................................. 78
Copyright 2009 Rafeeq Rehman
Page: 5 of 93
Chapter One: Information Security and Risk Management 9.3.1 Securing Windows Servers........................................................................................ 78 9.3.2 Securing UNIX/Linux Servers .................................................................................. 78 9.3.3 Securing Mail Servers ............................................................................................... 78 9.3.4 Securing Web Servers ............................................................................................... 78 9.3.5 Creating Server Check Lists and Security Templates .............................................. 78 9.4 Securing Desktop .............................................................................................................. 78 9.5 Patch Management ........................................................................................................... 78 9.6 Vulnerability Testing ........................................................................................................ 78 9.7 Password Cracking............................................................................................................ 78 9.8 Data Destruction ............................................................................................................... 78 9.9 Attacks and Vulnerabilities .............................................................................................. 78 9.10 Miscellaneous.................................................................................................................... 78 10 Legal, Regulations, Compliance and Investigation ............................................................. 80 10.1 Definitions........................................................................................................................ 80 10.2 Computer Crimes .............................................................................................................. 82 10.3 Ethics ................................................................................................................................. 82 10.4 Laws................................................................................................................................... 82 10.5 Incident Management ...................................................................................................... 83 10.6 Investigation and Forensics ............................................................................................. 83 10.7 Attacks and Vulnerabilities .............................................................................................. 83 10.8 Miscellaneous.................................................................................................................... 83 11 Commonly Used TCP and UDP Ports ..................................................................................... 84 12 Glossary .................................................................................................................................... 87 13 Index ......................................................................................................................................... 89 14 Sample Questions ..................................................................................................................... 91 14.1 Introduction ...................................................................................................................... 91 14.2 Questions .......................................................................................................................... 91
Copyright 2009 Rafeeq Rehman
Page: 6 of 93
Chapter One: Information Security and Risk Management
Preface, Acknowledgements and Introduction
CISSP certification needs a lot of preparation and breadth of knowledge. This book will help you assess your knowledge quickly to help you know if you are really prepared for the CISSP exam. If you are an experienced information security professional, it also helps you refresh your knowledge quickly.
Acknowledgements
I am thankful to all of my friends who shared their thoughts and gave feedback to prepare manuscript for this book.
How to Read This Book
By this time, you may have noticed that this book is very short compared to other CISSP exam preparation books. The objective is to save your time (and money) while preparing for the CISSP exam. The book also gives you a chance to see how prepared you are for the CISSP examination by going through the bulleted points. This book provides a quick overview of each topic in CISSP certification exam. You should read it when you start preparing for the examination. At this stage, it will give you an idea about your current level of knowledge. At the end of each chapter, you will see a number of links where you can find more detailed information about the CISSP exam. While reading information from those resources, if you find something new that is not in this book, just keep on adding your notes with the empty pages. This way you will keep on creating your own notes as well. By the time you have reached the end of this book, you will have a decent amount of knowledge that you can quickly browse through.
Questions, Comments, Criticism, Appreciations
Please contact the Author, Rafeeq Ur Rehman, at rafeeq.rehman@gmail.com for any questions or comments or provide any feedback that can be helpful in the next version of this book. All types of critique is welcomed.
Copyright 2009 Rafeeq Rehman
Page: 7 of 93
Chapter One: Information Security and Risk Management
Support This Free Book Project By Your Advertisement
You can support this book by placing your advertisement in this book. For more information, contact info@conformix.com. If you are a vendor of information security products, you will reach the right audience and it will be the best use of your marketing dollars.
Copyright 2009 Rafeeq Rehman
Page: 8 of 93
Chapter One: Information Security and Risk Management
ADVERTISEMENT
Copyright 2009 Rafeeq Rehman
Page: 9 of 93
Chapter One: Information Security and Risk Management
Chapter One
1Information Security and Risk Management
1.1
Definitions
Confidentiality of information prevents disclosure, unauthorized use of information. Information should be made available who have a need-to-know. Integrity ensures that data is not modified in an un-authorized manner and it is consistent Availability means that the data is available when it is needed by authorized persons or processes. Single Point of Failure is something that, if broken, can cause the whole system or process to stop working. Defense-In-Depth or DID means that there are multiple lines of defense to secure data
Copyright 2009 Rafeeq Rehman
Page: 10 of 93
Chapter One: Information Security and Risk Management SLA or Service Level Agreement defines the minimum standard of a service provided to customers. Certification is the formal process of risk assessment for a system and documenting the risk with due-diligence Accreditation is a process where business owners formally accept risk associated with a project or system. Accreditation happens after certification Risk is likelihood of loss. Safeguard or a control or a counter measure is measure to reduce risk. Threat is an event that can cause harm to assets (natural or man-made) Threat Agent is an entity that can cause harm to an asset, e.g. an Internet attacker. Vulnerability is a weakness in a system or process that can be exploited by a threat agent to get access to an asset. Exposure Factor or EF is the percentage loss (in dollar) from a single incident. Single Loss Expectancy or SLE is loss in term of dollar from a single successful incident. SLE= EF x Asset Value Annual Rate of Occurrence or ARO is an estimate of how many time an incident will occur within a year that will cause loss. Annual Loss Expectancy or ALE is the total estimated loss within a year. This estimate is based upon SLE and ARO. ALE=SLE x ARO
1.2
Introduction
1. Organizations need to have a program to manage information security risk 2. An organization need to have policies, standards, guidelines, and procedures to ensure information security. 3. Policies are generic whereas standards are specific. So a policy may state that data must be protected whereas a standard may have specific language about protecting data by encryption with AES encryption. 4. Policies and Standards are mandatory, whereas guidelines are not. 5. Procedures are detailed processes to do certain tasks
Copyright 2009 Rafeeq Rehman
Page: 11 of 93
Chapter One: Information Security and Risk Management 6. Policies include controls framework and are very high level. Sample controls frameworks are ISO 17799/ISO 27002. 7. ISO 17799 security controls framework is divided into 10 domains1. These ten domains are: i. ii. iii. iv. v. vi. vii. viii. ix. x. xi. Organization of information security management Asset control Human resources Physical and environmental security Telecommunications and operations Access control IT systems development and maintenance Incident management Business continuity and disaster recovery Compliance An organization must also have a mission statement that shows the fundamental principle of the organization.
8. An organization must also have a mission statement that shows the fundamental principle of the organization. 9. SLA or Service Level Agreement defines the minimum standard of a service provided to customers.
1.3
Basic Principles
1. Risk management includes two major parts: risk assessment and risk mitigation. 2. Risk assessment is performed on different risk/attack scenarios keeping in view vulnerabilities and controls. 3. Risk management consists of:
This book follows those ten domains, starting from this chapter
Copyright 2009 Rafeeq Rehman
Page: 12 of 93
Chapter One: Information Security and Risk Management 4. Mitigating the risk by using some safeguards and counter measures. 5. Transferring the risk to other entities, like buying insurance 6. Assuming the risk, if expenditure on mitigation or transfer is more than the risk itself. 7. Three basic principles of information security are Confidentiality, Integrity, and Availability or C-I-A. It is also called information security triad. 8. Opposite to CIA is DAD which is Disclosure-Alteration-Destruction. 9. To achieve defense-in-depth, you need to do many things including: a. Have multiple layers of network separated by firewalls. b. Implement solutions from different vendors at different layers to ensure a problem with one vendor does not impact all layers. c. Incorporate security principles, policies, best practices, education, and awareness programs d. Implement monitoring systems including log monitoring, intrusion detection and prevention, event correlation, and log retention. e. Implement the principle of separation of duties such that one person is not able to perform end-to-end tasks f. Avoid single points of failure
g. Implement network segmentation to create choke points so that parts of network can be quarantined if needed. 10. Data classification means that data should be categorized based upon level of sensitivity and level of protection required for a particular of data. Sample classifications may include confidential, protected, public etc. 11. A person must be in-charge of overall management of information security 12. Roles are responsibilities must be defined based upon the principle of separation of duties 13. Organizations must implement a program for security certification and accreditation (SC&A) to identify, document, and manage risk related to projects. 14. A network architecture should be created for defense-in-depth that implements multiple lines of defense, also called network tiers
Copyright 2009 Rafeeq Rehman
Page: 13 of 93
Chapter One: Information Security and Risk Management 15. Information security practices should be integrated in human resources hiring and firing processes 16. Senior management is responsible for creating information security program 17. You should use multiple controls to protect data. These controls include: a. Administrative controls such as security policies. b. Technical controls such as encryption. c. Physical controls such as key card access, security guards.
1.4
Availability
1. Single points of failure affect availability and reliability of a system. 2. Highly Available (HA) systems dont have single points of failure
1.4.1
Avoiding Single Points of Failure
1. Hardware: Dual power supplies, RAID including disk mirroring, fail-over clustering, parity, multiple network adapters, hot swappable components 2. Software and Systems: failover clustering, multiple data centers 3. Network: multiple network paths, dynamic routing algorithms, dial backup, multiple telecom providers, firewall clusters 4. Processes: Multiple vendors and service providers, multiple employees trained for each job.
1.5
Data Classification
1. Data classification is important to put appropriate security controls around data depending upon its importance 2. Data classification is based upon different criteria like: value of data, regulatory requirements, retention period. 3. Data value will be high if the data is related to company secrets, customer and employee information, credit card and bank/financial information, health information, etc. 4. Different types of security controls are applied depending upon data classification.
Copyright 2009 Rafeeq Rehman
Page: 14 of 93
Chapter One: Information Security and Risk Management 5. Ideally, all data should be marked with its classification irrespective of how it is stored (electronic, paper) 6. US government data classifications include (in order of sensitivity): Unclassified, Sensitive but Unclassified, Confidential, Secret, and Top Secret. 7. Private organizations may define their own classification depending upon their own requirements. Examples: restricted, confidential, internal user only, public, etc. 8. Data owner data owner is a an executive or senior management person who is officially responsible and personally liable for the security of data. 9. A data custodian data custodian has the day to day responsibility of managing data. Data custodians may network administrator, DBA, system administrator or other people in similar role. The owner has the ultimate responsibility whereas the custodian has the day-to-day responsibility to ensure security. 10. The owner performs data classification, create policy to protect data, and assign custodians. Custodians on the other hand backup and restore data, perform encryption, manage privileged user accounts, and so on. 11. Regular users who have access to data are responsible for following policies defined by data owners. 12. Data classification must be reviewed at some defined intervals because it may change over time depending upon changed risk posture to a company 13. During data classification process, factors like value of data, age of data, competitive advantage, etc should be considered.
1.6
Personnel Security
1. Where needed, hiring process should include drug testing, background checks, credit history, and security clearance. 2. Minimum notice should be given to a candidate for drug test, preferably one to two days only to get good results. 3. The new employee orientation process should include introduction to security policy 4. The HR policies should include accepted guidelines for computers and other company resources. 5. Employee references and application data must be verified for new employees
Copyright 2009 Rafeeq Rehman
Page: 15 of 93
Chapter One: Information Security and Risk Management 6. If an employee is fired from company, the HR process must include notification to IT staff to immediately disable user accounts and access to network. In other words, the HR process must be tied to the identity management process. 7. Security badges and key card access must be used for employees with access to sensitive locations, including data centers. 8. If an employee has knowledge of shared account/generic accounts, passwords for those accounts must be changed when an employee leaves the company or moves to another position in the company 9. Upon termination of employment, notice should be sent to other employees, vendors, service providers, and so on. 10. It is accepted industry practice that company email is the property of a company. There should be a policy to keep email of terminated employees for a certain period of time. Incoming email for a terminated employee may be redirected to the manager for a specified period of time to avoid missing email from vendors. 11. There should be a specific job description for each employee to ensure roles and responsibilities understood by all. 12. Job rotation is a way to minimize risk related to collusion. In collusion, two or more people work together to commit fraud. 13. The principle of separation of duties should be implemented to ensure a single person is not able to control any process completely.
1.7
Risk Management and Risk Lifecycle
1. Risk is a measure of a corporations tolerance to security events. It depends upon threat vectors, vulnerabilities, and estimation of loss in number of dollars. In many places in the text, the formula is: risk = threat x vulnerability. The author believes that this formula does not show the complete picture because it does not take into account expected loss2. 2. Risk goes through different stages in its life. Some stages are: identified, documented, assessed, transferred, mitigated, closed
SMART (http://smart.conformix.com) is a system to manage information risk
Copyright 2009 Rafeeq Rehman
Page: 16 of 93
Chapter One: Information Security and Risk Management 3. Risk associated with a security issue may change over time. For example, new laws and regulations, change in business practices, and new threats may change risk level. 4. After identification, risk can be controlled in three ways: it can be mitigated, assumed, or transferred to other entities. 5. Risk controlling should be cost effective. This means that if a risk is worth $100, you should spend less than $100 to control it. 6. An example of transferring risk is buying an insurance to an asset. 7. Risk can never be zero. However it can be mitigated to an acceptable level. 8. Quantitative risk analysis includes estimating risk in terms on number of dollars or numbers. 9. Qualitative risk analysis is usually in terms of ``High'', ``Medium'', and ``Low''. It does not deal with numbers and is more subjective than quantitative risk analysis. 10. Quantitative risk analysis may include complex formulas, needs data, and may take more time to perform. On the other hand, qualitative risk analysis is more subjective, does not include many calculations, and does not need that much data as the quantitative risk analysis. 11. Compensation controls compensation controls are measures that you take to reduce risk. 12. Risk is never zero. There is always a residual risk even if good controls are implemented 13. OCTAVE is a risk assessment methodology.
1.8
Security Policies and Standards security policy and standards
1. Policies3 are high level statements from senior management. 2. Standards define how the policies will be implemented. 3. Guidelines are not mandatory. These are used to help implement the information security policy. 4. Procedures are detailed, step-by-step processes to do certain tasks.
PolicyDOC (http://www.policydoc.com) is a policy and procedure management software.
Copyright 2009 Rafeeq Rehman
Page: 17 of 93
Chapter One: Information Security and Risk Management 5. If a security policy can't be implemented for any reason, there must be an exception process to the security policy 6. Since technologies keep on changing, security policies must be updated on regular basis
1.9
Education and Awareness education and awareness
1. Security awareness program is important for overall information security management. 2. Awareness programs help in avoiding attacks related to social engineering, data leakage by accident. 3. The programs need to be continuous in nature (not a one-time item). 4. Items like security policies, data destruction, importance of paper shredding, roles, responsibilities, data classification, physical security, importance of key card access, appropriate use of email and the Internet, should be covered in these programs. 5. Security newsletters, seminars, etc may be part of awareness programs.
1.10
Roles and Responsibilities
1. Owner is an executive level person who is the ultimate responsible person to protect information. 2. Custodian is appointed by the owner and has responsibility of securing information from a day to day routine perspective. 3. Information Users are the end users of the information who are given access by the custodian on the basis of need-to-know.
1.11
Attacks and Vulnerabilities
In the absence of a well established information security and risk management program, the organization may become vulnerable to a number of attacks as listed below. 1. Lack of education and awareness may result in successful social engineering attacks. Social engineering is a type of attack where an attacker will try to get information by social interaction like pretending to be a fellow company employee, using phone calls to get information, etc. 2. If employees are not trained in data destruction \footnoteData destruction means destroying data when no longer needed, e.g. shredding papers, degaussing disks, Copyright 2009 Rafeeq Rehman Page: 18 of 93
Chapter One: Information Security and Risk Management shredding tapes, etc.data destruction, attacks like dumpster diving \footnoteIn dumpster diving, attackers look into company dumpsters to find papers and other useful data dumpster diving may result in data disclosure 3. Absence of data classification may confuse employees about which information is sensitive and how it should be protected. As a result, employee may divulge sensitive information. 4. Denial of Service (DoS) Denial of Serviceattacks cause availability issues. DoS attacks try to make a system (web site, databases) unavailable to users causing in loss. 5. Distributed Denial of Service (DDoS) Distributed Denial of Service is a special type of attack that Internet attackers launch against web sites. Typically, a large number of hacked computers are used to launch attack against a web site. These attacks include creating a large Internet traffic volume to the web site to bring it down or to make it very difficult for the real users to access it. 6. Attackers, social engineering, unprotected files, insecure communication protocols, are some examples of major threats to confidentiality of data 7. Natural disasters, power outages, system failures, denial of service attacks are major threats to availability of data. 8. Usually software patches are used to fix vulnerabilities in software. Vulnerabilities related to poor network design are difficult to fix until new network design is implemented.
1.12
Miscellaneous
1. Separation of duties help in safeguarding data from internal threats. Job rotation is another way to combat internal threats. 2. People should also be considered as single point of failure if there is only one person to do a certain business function. 3. Education and awareness may include publication of security newsletters, security training, employee orientation, etc. 4. Baselines are minimum security processes implemented in an organization.
Copyright 2009 Rafeeq Rehman
Page: 19 of 93
Chapter One: Information Security and Risk Management
Copyright 2009 Rafeeq Rehman
Page: 20 of 93
Chapter Two: Access Control
Chapter Two
2 Access Control
Access controls domain scope is related to all of the following: 1. Authentication and authorization 2. User account provisioning, management, deletion 3. Password controls 4. Network access controls
2.1
Definitions
Accounting is mechanism to calculate for how long a resource is used or for how long a user has been logged in to a web site. Identification is a process to ensure that an entity (person, program, computer) is what it claims to be. In a typical scenario, an account is created after identification. Authentication happens after identification. Typically it is a login process using username/password. Other mechanisms like X.509 certificates, PINs, token, cards, etc can also be used. Authorization is used after authentication to grant a certain level of access based upon authentication. For example, all authenticated users may not be allowed to alter information. Only users in administrator group may alter/add/delete information. Copyright 2009 Rafeeq Rehman Page: 21 of 93
Chapter Two: Access Control SSO (Single Sign On) is a mechanism of getting access to multiple resources (systems, applications, etc) by entering username/password only once. Graded Authorization systems implement multiple levels of authorization. For example, a person may be granted read-only access to a web account, read-only access plus view bills, and all of the above plus make payments Risk-based Authorization is used to grant access resources based upon risk level associated with an account, account creation, or authentication method. Cognitive Passwords are based upon some facts or something you remember, e.g. mother's maiden name, color of your first car, etc. Passphrase is a string that is longer than password and is used in place of password. The actual password is generated by the application based upon passphrase. PGP is an example of the application that uses passphrase.
2.2
Access Control
1. Access controls are put in place to control and monitor flow or retrieval of information in networks, databases, and other systems. 2. Username/password, certificates, group memberships, access lists are some mechanisms for access control. 3. Access Controls are put in place to protect Availability, Confidentiality, and Integrity of information. 4. Availability means that information must be available to users in timely manner. 5. Confidentiality means that information will be made available to only those entities (people, systems, applications) who have a need to get that information. 6. Integrity means that information should be protected from unauthorized alteration. 7. Access can be controlled using many factors like physical access, logical access, access based upon time of day, etc. 8. Access should always be granted on the basis of need-to-know. 9. When granting access, principle of least-privileges should be implemented. By thin principle, a person should have no more privileges than needed to do his/her job.
Copyright 2009 Rafeeq Rehman
Page: 22 of 93
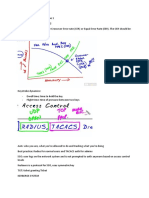
Chapter Two: Access Control 10. Role-based access helps in granting access to a person based upon his/her role. If role of a person changes, the access level also changes. 11. Role-based access helps in controlling access creep which results from employees moving from one department to another and previous access is not fully revoked. In rolebased access, when a role changes, access for the previous role is automatically revoked. 12. A good practice of granting access is to always start with ``no access'' to a resource. Example: while creating access list on a firewall, first deny everything and then open ports on as-needed basis. 13. Authentication is based upon three items: Something you know, something you have, or something you are. 14. Strong authentication happens when a system uses multiple mechanisms (know, have, is). 15. Two factor authentication means you are using two out of three mechanisms (know, have, is). 16. Pass phrases are longer strings than passwords. Typically a system will convert a passphrase into a password for actual authentication. 17. Memory cards store information which is used for authentication. Smart cards are capable of storing and processing information. Smart cards usually have integrated chips on them. Some smart cards work on contact while others are contact-less. 18. RADIUS (Remote Authentication Dial-in User Service) and TACACS (Terminal Access Controller Access Control System) are used for centralized access control. 19. Microsoft RAS is another centralized access control mechanism for remote users. 20. PAP (Password Authentication Protocol) and CHAP (Challenge Handshake Authentication Protocol) are also used for remote as well as client-server access controls. 21. EAP (Extensible Authentication Protocol) is also used for access control for remote users. 22. AAA (Authentication, Authorization, Accounting) is a name for process that does all these three items. 23. Accounting is mechanism to calculate for how long a resource is used or for how long a user has been logged in to a web site.
Copyright 2009 Rafeeq Rehman
Page: 23 of 93
Chapter Two: Access Control 24. Always start with no access to a resource. Example: while creating access list on a firewall, first deny everything and then open ports on as-needed basis. 25. Identification is a process to ensure that an entity (person, program, computer) is what it claims to be. In a typical scenario, an account is created after identification. 26. Identity Management is a process of creating/modifying/deleting identities. It also includes services for authentication and authorization. 27. LDAP (Lightweight Directory Access Protocol) is used to store and retrieve authentication and authorization information. OpenLDAP is open source implementation of LDAP. 28. There are other directory services as well, like Novell NDS, Oracle OID, etc. 29. Kerberos is an authentication and authorization mechanism used in many systems including Microsoft Windows. In Greek mythology, Kerberos is name of a three headed dog. 30. SSO (Single Sign On) is a mechanism of getting access to multiple resources (systems, applications, etc) by entering username/password only once. 31. Kerberos can be used for single sign on (SSO). 32. In Kerberos, KDC (Key Distribution Center which is a component of Kerberos) generates tickets for principals. 33. Principals use tickets to get access to different resources in a Kerberos system. 34. Certificates with public/private encryption keys are used in Kerberos. 35. Authentication happens after identification. Typically it is a login process using username/password. Other mechanisms like X.509 certificates, PINs, token, cards, etc can also be used. 36. Authorization is used after authentication to grant a certain level of access based upon authentication. For example, all authenticated users may not be allowed to alter information. Only users in administrator group may alter/add/delete information. 37. Authentication is based upon three items: Something you know, something you have, or something you are. 38. Strong authentication happens when a system uses multiple mechanisms (know, have, is).
Copyright 2009 Rafeeq Rehman
Page: 24 of 93
Chapter Two: Access Control 39. Two factor authentication means you are using two out of three mechanisms (know, have, is). 40. Graded authorization means you give a lower level of access initially and if the person needs more access, you ask for additional proof to grant more access. 41. Risk-based authorization means you provide access to entities based upon risk level associated with the object and the security clearance of the person needing access. 42. Pass phrases are longer strings than passwords. Typically a system will convert a passphrase into a password for actual authentication. 43. Memory cards store information which is used for authentication. Smart cards are capable of storing and processing information. Smart cards usually have integrated chips on them. Some smart cards work on contact while others are contact-less. 44. Memory and smart cards are vulnerable to attacks where an attacker can steel information by placing rogue card readers.
2.2.1
Access Control Types
1. Discretionary access control (DAC) access based systems allow the owner of a resource to decide who can access the resource. 2. Mandatory access control (MAC) based systems ensure that the operating system makes a determination about who can access a resource. 3. Mandatory access controls systems assign sensitivity levels to different resources. If a user has permission equal to or higher of the sensitivity level, the user is allowed to access the resource. 4. Role-based access control (RBAC) systems work on the basis of roles assigned to users. Permissions to access a resource are granted to different roles instead of particular users. The access to a resource is controlled by the system.
2.3
Remote Authentication
1. RADIUS (Remote Authentication Dial-in User Service) RADIUS and TACACS (Terminal Access Controller Access Control System) TACACS are two protocols used for centralized access control. 2. Microsoft RAS is another centralized access control mechanism for remote users.
Copyright 2009 Rafeeq Rehman
Page: 25 of 93
Chapter Two: Access Control 3. PAP (Password Authentication Protocol) PAP and CHAP (Challenge Handshake Authentication Protocol) CHAP are also used for remote as well as client-server access controls. 4. EAP (Extensible Authentication Protocol) EAP is also used for access control for remote users. 5. AAA (Authentication, Authorization, Accounting) AAA is a name for process that does all these three items.
2.4
Biometrics
1. Biometrics (finger prints, retina and iris scans, facial recognition, hand geometry and topography, voice print, signatures characteristics, etc) are also used for authentication. Biometrics are used to authentication based upon what you are. 2. Biometric systems are not 100% accurate and can reject authorized individuals (Type I errors) or allow unauthorized users (Type II errors). 3. Things to consider in biometric: processing speed, Crossover Error Rate (CER), cost, sensitivity. 4. CER shows the point where Type I and Type II errors become equal. The lower CER, the better the device is. To get CER, Type I and Type II errors are plotted against sensitivity. The point where both curves cross shows CER. 5. Each authenticated entity must have unique credentials (e.g. unique username) for accountability and logging.
2.5
Passwords Security
1. Passwords are usually stored in directory services (like LDAP), database tables, or in flat files. Passwords must be encrypted. 2. Many systems use passwords in one-way hash (e.g. MD5, SHA1, etc) forms. Hashed passwords are better than encrypted because if someone finds encryption key, that person can decrypt passwords. However, there is no reverse process for hashed passwords. 3. Passwords are vulnerable to attacks like brute force, dictionary attacks, social engineering, password crackers, network traffic sniffing.
Copyright 2009 Rafeeq Rehman
Page: 26 of 93
Chapter Two: Access Control 4. Password controls should be put in place. Password controls include password aging, password expiration, disallowing dictionary words as passwords, enforcing a combination of letter and numbers, password history so that old passwords cant be reused, and so on. 5. Password aging forces user to change passwords within a certain period of time. 6. When a password is reset by a customer service representative, the user must be enforced to change it at the first login. 7. If more than one person knows passwords, it is a bad sign for security. 8. One time use passwords (OTP) are created dynamically with the help of a token device. The token device generates these based upon sequence number of time stamp. 9. Token devices are vulnerable if stolen and user ID (username) is not kept confidential. 10. Self-service password reset can be achieved in a number of ways, including: a. b. Sending email to a pre-registered email address Asking the user to answer to one or more questions that the user has already stored on the web site Sending a text message to a pre-registered cell phone
c.
2.6
Identity Management and Directory Services
1. Identity Management is a process of creating/modifying/deleting identities. It also includes services for authentication and authorization. 2. LDAP (Lightweight Directory Access Protocol) is used to store and retrieve authentication and authorization information. 3. OpenLDAP is open source implementation of LDAP. 4. There are other directory services as well, like Novell NDS, Oracle OID, etc.
Copyright 2009 Rafeeq Rehman
Page: 27 of 93
Chapter Two: Access Control
2.6.1
Kerberos
1. Kerberos4 is an authentication and authorization mechanism used in many systems including Microsoft Windows. In Greek mythology, Kerberos is name of a three-headed dog. 2. Kerberos was developed in MIT as part of project Athena. 3. Many systems including Windows 2000 and Windows 2003 use Kerberos. 4. Passwords are never sent over network during authentication process used in Kerberos. 5. Kerberos can be used for single sign on (SSO). 6. In Kerberos, KDC (Key Distribution Center which is a component of Kerberos) generates tickets for principals'. 7. Principals use tickets to get access to different resources in a Kerberos system. 8. KDC provides authentication and key distribution. KDC is the center of trust in Kerberos. Any compromise to KDC has the potential of compromise of the whole system. 9. Principals can be considered as clients' and they may be regular users, computers, printers, and so on. 10. Kerberos is essentially a 3-party system where two principles authenticate to each other using KDC. 11. Remember the following about the Kerberos system: a. KDC runs Authentication Service (AS) and Ticket Granting Service (TGS) b. When a user first time authenticates to Kerberos, KDC issues a Ticket Granting Ticket (TGT). c. A principal will keep TGT and will use to get a ticket from KDC when needed d. The authenticator is part of ticket that contains identification information of a user. e. A Service Center (SS) is usually a principal that provides a service to a client. 12. A session key is used between two principals to secure data.
http://web.mit.edu/kerberos
Copyright 2009 Rafeeq Rehman
Page: 28 of 93
Chapter Two: Access Control 13. KDC is a single point of failure in Kerberos. 14. Kerberos keys are vulnerable to memory attacks because these are stored in RAM by principals. 15. A secret key is established between a principal and the KDC. KDC and the principals trust each other based upon that secret key. 16. KDC acts as a trusted party among different principals who don't trust each other directly. 17. All tickets have time limit and protected from replay attacks and someone captures network traffic. 18. Kerberos uses symmetric encryption (DES). Some extensions allow use of PKI and certificates as well. 19. Kerberos is mutual authentication protocol where both parties taking part in a conversation verify each other. 20. Recent updates to Kerberos has implemented stronger encryption to Kerberos, including AES. 21. Kerberos time synchronization among principals and KDC to verify validity of tickets. 22. Use of protocols like NTP is needed to run Kerberos smoothly.
2.6.2
Light Weight Directory Access Protocol or LDAP
1. One of more LDAP servers are used to store information about objects. Most of the servers can synchronize their databases. 2. LDAP clients connect to directory servers for authentication and authorization purposes. 3. Authorization is performed based upon different attributes associated with an object.
2.6.3
OpenID
1. OpenID5 is used mostly for authentication with web-based applications. 2. OpenID is a 3-party system: Identity Provider, Relying Party, and the User Agent (or web browser)
http://www.openidbook.com for my other book on OpenID
Copyright 2009 Rafeeq Rehman
Page: 29 of 93
Chapter Two: Access Control
2.6.4
NTLM
1. NTLM or NT LAN Manager is a Microsoft protocol. 2. NTLM is a challenge-response protocol. It is an evolution of an older Microsoft protocol known as LAN Manager. 3. NTLM has two versions: NTLMv1 and NTLMv2. 4. NTLM is an older protocol and is replaced by Kerberos in Windows 2000 onwards. 5. NTLM is still being used when a computer is not part of a Windows domain or where no Windows domain exists. Examples: peer-to-peer networks like Windows workgroups in small offices. 6. It can be used for authentication based upon IP addresses.
2.6.5
Microsoft Active Directory Active Directory
1. Active Directory or AD is the directory service that comes with Microsoft Windows servers and it is the main directory repository from Microsoft. 2. Active Directory implements the concept of forest in which there may be multiple domains. 3. Each domain can contain multiple Organizational Units or OU. OU is used to group objects and implements controls on the group. 4. Different types of trusts can be established among Active Directory domains.
2.7
Controlling Access in Networks
1. To control access on network, it is advisable to segment network in different domains. Example: administration domain should be separate from Internet. 2. Each domain should be separated by firewalls with only limited traffic to pass through. 3. Network should also have layers of security. Three layers between Internet and core database computers are recommended. 4. Layers should be separated by firewalls. 5. While opening firewall ports, use individual IP addresses for source and destination computers instead of network addresses.
Copyright 2009 Rafeeq Rehman
Page: 30 of 93
Chapter Two: Access Control
2.8
Types of Access Controls
1. One way to classify access controls is based upon how they are utilized. In this regard, access controls may be preventive or detective in nature. 2. Access controls may also be classified as physical, technical, and administrative. 3. Preventive access controls are used to stop an attacker from getting access to data or system, such as passwords. Detective access controls are used to detect any violation after the fact, such as log files. 4. Examples of physical access controls are security guards, locks, key card access, and so on. 5. Example of technical access controls are passwords, firewalls, etc. 6. Examples of administrative access controls are policies, security templates, background checks, etc.
2.9
Access Control Monitoring
1. Access controls violations need to be monitored at multiple places. The controls should be monitored at least at Network level, Operating Systems level, and applications level. 2. Access control monitoring is performed in many ways using logs, IDS/IPS, etc. 3. In Microsoft Windows, event viewer shows failed logins. 4. In UNIX/Linux systems, Syslog can be used to monitor failed and successful logins. 5. The logs data must be stored on log servers instead of locally at each machine. The reason is that if a system is compromised and log data is stored on the same system, the attacker will remove that data to delete any footprints.
2.10 Attacks and Vulnerabilities
1. Keyboard loggers are commonly used by attackers to steel username and password information. Key loggers are software or other mechanisms that log keyboard information without a user knowledge and send this information to an attacker. 2. Phishing attacks are also commonly used against popular attacks to get username and password information. This is done by sending fake emails that look like official and luring innocent users to click on links in the email to go to a rouge web site that looks like an official company web site. Copyright 2009 Rafeeq Rehman Page: 31 of 93
Chapter Two: Access Control 3. Password crackers are software that are used to crack password. These programs work on common password vulnerabilities and dictionaries to crack passwords. For example, a password cracker may get a UNIX password file and start password cracking by using the same password as the username, first name, last name, and so on. 4. Memory and smart cards are vulnerable to attacks where an attacker can steel information by placing rogue card readers.
Copyright 2009 Rafeeq Rehman
Page: 32 of 93
Chapter Three: Cryptography
Chapter Three
3 Cryptography
3.1
Terminology
Cryptography is field of science that deals with encryption. Plaintext is converted to ciphertext as a result of encryption. Plaintext is intelligible data. Plaintext is also called cleartext. A key is used to convert plaintext to ciphertext. Key is a string of characters and depending upon type of encryption, it may have different lengths. The opposite of encryption is decryption. Cryptanalysis is the field of study to break encryption. It is used to decrypt data without the keys. If two parties were engaged in a communication and one of them denies of having the communication, it is called repudiation. Encryption is also used to overcome this problem by ensuring non-repudiation. The work factor is the amount of time required to break encryption or other protective measures. In block-mode ciphers, data is broken into blocks for encryption.
Copyright 2009 Rafeeq Rehman
Page: 33 of 93
Chapter Three: Cryptography In block-chaining ciphers, data is broken into block for encryption but parts of blocks overlap. In stream-ciphers, data is passed through the encryption mechanism as a stream of bits or characters instead of breaking it into blocks. Cryptographic Algorithms are used to convert plain text to cipher text and vice versa. Link Encryption enables encrypting data on a communication link, like a computer network. End-to-End Encryption encrypts date from source to the destination. Substitution Cipher replaces character in the plain text with other characters or numbers. It may also be done by shifting character right or left in the sequence. Transposition Cipher uses permutation to convert plain text to cipher text. Digital Signature is a mechanism to detect any unauthorized modification to text and nonrepudiation. It is not encryption.
3.2
Introduction
1. Encryption is used for the many purposes, including: a. Protection of confidentiality of data b. Ensuring data integrity c. Non repudiation 2. Typical key lengths are 64 bit, 128 bit, 256 bits, and so on. 3. Longer keys usually provide stronger encryption. 4. Encryption is performed using open or public algorithms as well as proprietary algorithms 5. Open algorithms are considered as more standard and more secure. 6. For encryption to be reliable, the security of encrypted data should depend only on secrecy of the encryption key and not on the process of encryption (encryption algorithm).
Copyright 2009 Rafeeq Rehman
Page: 34 of 93
Chapter Three: Cryptography
3.3
Alogrithms
1. There are two main types of algorithms: symmetric and asymmetric. 2. Symmetric encryption algorithms are also called private key algorithms. or shared key
3. Symmetric algorithms use that same key for encryption and decryption. This key is also called a shared key. DES, 3DES, AES, etc are examples of symmetric algorithms. 4. Asymmetric algorithms use two keys: public and private. Data encrypted by one key can be decrypted only by the other key. RSA is an example of asymmetric algorithm. 5. Symmetric algorithms are usually faster than asymmetric algorithms as for as execution time is concerned. 6. In many cases, asymmetric algorithms are used to transfer shared key in the initial phase of communication between two parties. After that shared key is used for encryption. This is done to make the encryption faster.
3.3.1
Digital Encryption Standard (DES)
1. Developed by IBM 2. Provides block mode symmetric encryption. A single key is used for both encryption and decryption. 3. Uses 56 bit key length with 8 parity bits making the key a total of 64 bit long. 4. It uses 16 rounds of substitutions and transpositions. 5. The detailed information is available at http://www.itl.nist.gov/fipspubs/fip46-2.htm 6. Can be implemented in hardware and software and provides efficient encryption.
3.3.2
Triple Digital Encryption Standard (3DES6)
1. More secure than simple DES algorithm. Written as 3DES or TDES. 2. It is symmetric encryption algorithm. 3. Uses three steps to encrypt data with effective key length of 192 bits (64x3). If parity bits are taken off, the key length is 168 bits (56x3).
Standard document available at http://csrc.nist.gov/publications/nistpubs/800-67/SP800-67.pdf
Copyright 2009 Rafeeq Rehman
Page: 35 of 93
Chapter Three: Cryptography 4. Another algorithm, Advanced Encryption Standard (AES) is preferred now over 3DES.
3.3.3
Advanced Encryption Standard or AES AES
1. AES is a US government standard for information encryption. 2. AES used Rijndael block cipher algorithm. 3. AES can have key length as 128, 192, or 256 bits. 4. It is fast and can be easily implemented in hardware. 5. Another characteristic of AES is that it is resistant against currently known attacks.
3.4
Public Key Cryptography
1. Public key cryptography is a mechanism where two keys are used for encryption and decryption: A public key and a private key. 2. A person with the key pair (public and private) makes his/her public key available to everyone while keeps the private key secret. 3. Data encrypted with public key can be decrypted by private key only and vice versa. 4. If a person Bob wants to send a secure data to another person Alice, Bob will use Alices public key to encrypt the data. Now only Alice can decrypt it because only Alice has the private key. 5. To ensure that the data is coming from Bob, Bob will use his private key to encrypt it. When Alice receives it, she will use Bobs public key to decrypt it. If the decryption is successful, it is guaranteed that Bob sent it because Bob is the only person who has the private key. If someone else pretended to be Bob and sent a message to Alice, Alice will not be able to decrypt the data using Bobs public key. Sometimes this is also called signing the data and is used for non-repudiation. 6. Digital Signature may be added to a digital message (like email) to ensure the source of message. Digital signature is usually hash code of the message which is encrypted using senders private key. The recipient can decrypt the signature (get hash code), create a new hash code and compare the two. If both match, it ensure that the message was not altered on its way and it was sent by the real sender. 7. In many cases both encryption and digital signature are used to: a. Ensure confidentiality of data
Copyright 2009 Rafeeq Rehman
Page: 36 of 93
Chapter Three: Cryptography b. Integrity of data (the data was not altered) c. Non-repudiation (the data was sent by the real sender) 8. Many systems are developed using public key cryptography. The most commonly known system is PGP (Pretty Good Privacy) 9. Key Rings are electronic storage of digital keys. In many cases, key rings are simple files.
3.4.1
RSA Algorithm
1. RSA is the most commonly used asymmetric algorithm in PKC Public Key Cryptography. 2. The name of the algorithm is composed of first characters of last names of its inventors (Rivest, Shamir, Addleman). 3. The algorithm is based upon large prime numbers that are used to generate public and private key pair. 4. The larger the prime numbers, the difficult it is to factor their product.
3.5
PGP
PGP is now a standard encryption mechanism defined by Internet Engineering Task Force (IETF) RFC 48807 and used a public/private key pair for data encryption. 1. Free version of PGP is available from http://www.gnupg.org 2. PGP can be used for multiple purposes including file and disk encryption, secure email, digital signatures and so on.
3.6
Hashing
1. Hashing is a used to ensure integrity of data. It is not used for encryption. 2. There are many popular hashing algorithms including MD5 (Message Digest 5), SHA-1 (Secure Hash Algorithm), etc. 3. MD5 produces 128 hash code and was developed by Ron Rivest. MD5 is IETF standard defined by RFC 13218.
http://www.ietf.org/rfc/rfc4880.txt
Copyright 2009 Rafeeq Rehman
Page: 37 of 93
Chapter Three: Cryptography 4. MD4 is older than MD5 and is not used much. 5. SHA-1 produces 160 bit hash code and was developed by NIST. 6. Output of a hash function is the same, no matter how long the input data is. 7. CRC or Cyclic Redundancy Check is a type of hash. 8. Message Authentication Code or MAC is a checksum calculated for a message before sending it out. MAC is then calculated at the recipient side to ensure that the message is not changes on its way. Hashed Message Authentication Code or HMAC uses a key to generate MAC.
9.
3.7
Encrypting Data-At-Rest
1. Data needs to be encrypted when it is in transit (on the network) and when it is at rest or stored on disk. 2. Data is stored on disk usually in two broad categories: flat files or databases.
3.8
Public Key Infrastructure (PKI)
1. PKI is a framework with many components including but not limited to X.509 standard, cryptography, trusted parties, certificate authority, key management, etc. 2. Both symmetric and asymmetric encryption algorithms are used in PKI. Note that public key cryptography uses only asymmetric algorithms like RSA. 3. PKI is a framework and not a particular technology or product. 4. Each entity (persons, servers) participating in PKI has an X.509 certificate. 5. A certificate authority (CA) issues and signs certificates to entities (or subjects) in PKI. 6. CA is a trusted third party. By signing a certificate, it ensures that the certificate is valid. Signed certificates can't be modified. 7. When an entity needs to verify a certificate authenticity, it will decrypt signature hash of a certificate using public key from CA and match it with the actual hash of the public key in the certificate.
http://www.faqs.org/rfcs/rfc1321.html
Copyright 2009 Rafeeq Rehman
Page: 38 of 93
Chapter Three: Cryptography 8. Certificates can also be validates using On-line Certificate Status Protocol (OSCP) OSCP which checks the validity of a certificate using CRLs 9. Two or more CA can trust each other by the process of certification cross certification cross
10. PKI is used for many purposes including authentication, non-repudiation, access control, two factor authentication, etc. 11. A certificate authority is an integral and central part for PKI. 12. Major functions of PKI are confidentiality, integrity, and authentication. 13. PKI is useful when two parties don't know (or trust) each other but trust a Trusted Third Party.
3.8.1
Digital Certificates
1. Digital certificate, also called X.509 certificates are used to package public key associated with an entity (person, server, device) 2. Digital certificates are used for multiple purposes. A sample certificate is shown in Figure below.
Figure: X.509 Certificate general information
3. Figure show the same certificate. The General' TAB in Figure shows the general information about the certificate. The Detail TAB in Figure shows detail about the same certificate in Firefox web browser. When you are looking at a real certificate, you can scroll down to see more information as well.
Figure : X.509 Certificate detail 4. Digital certificate is a file that follows the X.509 standard. A certificate is usually signed by a certificate authority (CA) 5. A certificate may contain many fields, including, but not limited to: a. Certificate issuer information b. Version number Copyright 2009 Rafeeq Rehman Page: 39 of 93
Chapter Three: Cryptography c. Serial number d. Signature algorithm e. Issuer name f. Issue date and Expiration date
g. Public key h. Name of owner/entity 6. The certificate shown in Figures are self-signed certificates. Anybody can create selfsigned certificates. However, they don't provide the trusted third party (certificate authority) assuring. 7. The certificate shown in Figures are examples of certificates signed by a certificate authority. In Figure, you can see the certificate is signed by Verisign (certificate authority) and is issued to google.com X.509 Certificate general information, issued by a certificate authority 8. Figures xxx xxx show ``General'' and ``Detail'' parts of the same certificate as viewed in Firefox web browser. X.509 Certificate detail, issued by a certificate authority 9. Certificates are most commonly used by web sites to ensure authenticity of a web site. In the browser, you can click on the security lock button to view certificate detail. 10. Certificates are also used for secure email transfer from sender to recipient. 11. Certificate Revocation List or CRL is published by certificate authority to publish list of certificates that are revoked. 12. Certificates may be revoked before expiration date for a number of reasons, including compromise of private keys. CRL is a means for informing the certificate consumers that a certificate is not valid. CRL contains serial number of revoked certificates. 13. The URL for the location of CRL is included in the certificate itself. 14. Registration Authority or RA registration authority is a broker between the certificate owner and the certificate authority. RA gets user information, verifies it, and then sends it to CA to issue certificate. In most cases RA and CA roles are combined in a single entity. A certificate has public key of the owner. The owner keeps the private key
Copyright 2009 Rafeeq Rehman
Page: 40 of 93
Chapter Three: Cryptography 15. Certificates are used for many purposes including authentication, mutual authorization, secure web traffic, secure email, and so on. 16. Digital certificates can be stored in multiple file formats including: a. Base-64 or DER encoded files ending with .CER b. PKCS-7 files ending with .P7B c. PKCS-12 files ending with .PFX 17. When exporting certificates to a file, the file can be password protected.
3.8.2
Certificate and Key Management Key Management
1. Security of keys used for encryption/decryption is essential for modern cryptography because encryption algorithms are open and well-known. 2. Key management includes many tasks, including: a. Key generation b. Delivery and distribution of key to key owner in a secure way c. Storing keys in a secure way d. Using keys in a secure way e. Destroying keys when no longer needed f. Recovering keys from backup store or archive
3. Keys can be delivered by courier, secure servers, or some other mechanism that ensures that only the owner of a key receives it. 4. There are many automated key delivery systems. for example, Kerberos uses key distribution center or KDC to distribute keys. 5. In many modern communication protocols, keys are changed automatically and very frequently 6. An organization should always maintain backup copy of keys, also called a key escrow, in case a key is lost. If a key is needed for data decryption and becomes unavailable, there is no way to recover the data.
Copyright 2009 Rafeeq Rehman
Page: 41 of 93
Chapter Three: Cryptography 7. NIST (National Institute of Standards and Technology\footnote\urlhttp://www.nist.gov) has published a standard for key escrow known as Escrowed Encryption Standard or ESS. 8. In ESS, a key is split into two (or more parts) that are kept by different parties. 9. Keys length should be determined depending upon the sensitivity of the data encrypted by the key, the frequency of key usage. 10. Hardware Security Module or HSM is a hardware module used to generate and store keys. HSM provides a very high level of security in key management. 11. In many cases a backend directory like LDAP or Active Directory is used for storing keys and certificates. 12. Key Encryption Key or KEK is a key used to encrypt other keys.
3.9
Attacks and Vulnerabilities
1. Man in the middle attacks may happen if a trusted third party, like CA, is not used in encryption. 2. Brute force attacks are also used against encryption by trying all possible combinations of encryption keys. DES is vulnerable to this attack
3.10 Miscellaneous
1. SSLSSL uses asymmetric solution to exchange a symmetric (shared) key initially. The shared key is then used for subsequent encryption between web browser and web server. This primary reason to use shared key in subsequent communication is to lower computational overhead because symmetric algorithms are faster. 2. Enigma machine machines were used by Germany in World War II for encryption. 3. In some cases text from a book is also used as a key to convert plain text to cipher text. This is called Book Cipher as well. 4. Diffie-Hellman is a mechanism of exchanging a secret over a non-secure medium. 5. SSH or Secure Shell SSH is another application that uses public-private keys or PKC to encrypt data. SSH is used for secure remote access, secure file transfer, creating secure tunnels and many other purposes.
Copyright 2009 Rafeeq Rehman
Page: 42 of 93
Chapter Three: Cryptography 6. Digital Signature Standard or DSS is US Government standard for signatures and is defined by FIPS-181-1.
Copyright 2009 Rafeeq Rehman
Page: 43 of 93
Chapter Four: Physical Security
Chapter Four
4 Physical Security
4.1
Definitions
1. Fire Triangle fire triangle consists of three factors that help in burning process. These are Fuel, Oxygen, and Heat. 2. Blackout is a total loss of power. 3. Brownout is a drop in normal voltage for a longer period of time. Brownout may be caused by overloading of electrical distribution system. 4. Electric Fault is temporary power outage. 5. Electric Spike is a short (momentary) increase of voltage. 6. Electrical Surge is a prolonged increase in voltage which can be very harmful for computer equipment. 7. Sag is a short drop in voltage.
4.2
Introduction
1. The objective of physical security is to safeguard against a number of threats, both natural (floods, natural disasters, storms, lightning strikes) and man-made (theft, fire, intrusion, etc).
Copyright 2009 Rafeeq Rehman
Page: 44 of 93
Chapter Four: Physical Security 2. Physical security is an integral part of overall risk management and protecting information. 3. In case of any physical security related incident, saving human life is always the first priority. 4. Physical security is responsibility of all employees. Any violations should be reported to security department. 5. Organizations must have a physical security policy, emergency phone numbers, and a mechanism of reporting physical security violations.
4.3
Physical Access Controls
1. To control physical access to a facility, many types of controls are employed. These include, but not limited to: 2. Security guards which are good where human judgment is needed or where employees have to show a badge to get into a building. 3. Locks, doors, and fences 4. Card key access 5. ID badges with photos and magnetic stripes 6. Biometric scans such as finger scans, retina scans, iris scans, hand scans, voice recognition, etc. 7. Security cameras such as CCTV (Closed Circuit TV)CCTV 8. Mantraps where two doors are used. 9. Turnstile 10. Fences with gates. Fences with 8 feet of height stop intruders from climbing. 11. Dogs 12. In biometric devices for access control: a. False Accept Rate or FAR is also called Type II errors and it shows the rate at which unauthorized users are granted access b. False Reject Rate or FRR is also called Type I errors and it shows the rate at which real users are denied access Copyright 2009 Rafeeq Rehman Page: 45 of 93
Chapter Four: Physical Security c. Crossover Error Rate or CER shows a point on graph where FAR and FRR are equal. The lower the CER, the better the device. 13. Locks are of many different types such as locks with keys (preset), programmable, electronic, or hybrid. 14. Security guards can perform multiple functions as visible deterrence, security escorts, reception, and making immediate decisions in case of unforeseen emergencies. 15. Cost of employing security guards may be high. 16. Proximity Cards proximity cards are small cards that don't need to be inserted into a card reader. 17. Proximity cards may be: 18. Passive cards have no battery and rely of card reader's electromagnetic field. 19. Field-Powered cards contains electronics and battery and RF transmitter. 20. Transponders type cards use two way communication between card reader and the card itself. This is the most sophisticated ones. 21. RFID cards are being used these days. These cards have RFID chip that a card reader can read. The card itself has no power. 22. In case of emergencies like power failure, the door should become open by default to avoid people being trapped inside a building. 23. Visitors must always be escorted inside a building. 24. Different levels of physical access controls should be implemented in different areas of a building. 25. An audit trail must be kept for physical access to investigate incidents. An example of audit trail is a visitor log register 26. Employees with different level of access should be assigned badges of different colors so that security guards can easily distinguish them.
4.4
Environmental Controls and HVAC
1. HVAC stands for Heating, Ventilation, and Air Conditioning. This is a major consideration for any secure facility.
Copyright 2009 Rafeeq Rehman
Page: 46 of 93
Chapter Four: Physical Security 2. Air pressure inside a building should be more than atmospheric pressure so that air goes out when doors are open. This is to avoid smoke accumulation inside a building in case of fire. 3. Buildings should be installed with emergency lights and backup power sources. 4. All electrical wiring must be grounded properly. 5. Uninterrupted Power Supply (UPS) UPS is used for a temporary power supply. 6. To protect computing equipment, surge protectors should always be used. 7. A good temperature for data centers is 10-26 degrees centigrade or 50-80 Fahrenheit. 8. The humidity should be between 40% and 60%. 9. British Thermal Unit or BTU is a commonly used to calculate energy requirements. 10. Electrical spikes and surges can be taken care of using surge protectors. 11. HVAC system should be monitored and should have an alarm system attached to it.
4.5
Fire Control
1. Fire depends upon three factors: Oxygen, Fuel, and Heat. 2. Class A fire is caused by common items like paper, wood, etc and it can be extinguished by water or soda acid. 3. Class B fire is caused by burning of fuel such as gasoline and can be extinguished by carbon dioxide (CO2), soda acid, and Halon. 4. Class C fire is caused by electrical wiring of electronic equipment and can be extinguished by CO2 and Halon. 5. CO2 is colorless and odorless gas; It extinguishes fire by cutting Oxygen supply. 6. CO2 is used in portable fire extinguishers and is effective for class B and C fires. 7. Class D fire is caused by chemicals and needs special techniques to extinguish. 8. Computer equipment and data may be lost as a result of fire extinguishing process, such as water. 9. Data may also be compromised during the salvage process after fire if proper controls are not kept in place (e.g. half burnt papers dumped into trash).
Copyright 2009 Rafeeq Rehman
Page: 47 of 93
Chapter Four: Physical Security 10. Fire detection systems use different technologies like smoke detection, heat sensing, flame sensing, and so on. 11. Smoke detectors can detect smoke using variation in light intensity, detecting interruption in light beams, sampling air and ionization. 12. Water sprinklers extinguish fire by reducing heat. 13. Wet pipe water sprinklers have a head which melts by heat and sprinkler starts throwing water on fire. The water pipe is always filled by water. 14. Wet pipes can cause damage in case of malfunction or failure of nozzle because pipe is always filled by water. 15. Dry pipe water sprinklers have dry pipe and water is opened in case of fire only. This may cause delay in activation of sprinklers. 16. Preaction systems have dry pipes which are filled only by heat sensors or some other mechanisms. Otherwise they work as wet pipe systems. 17. Deluge systems are dry pipe and have a mechanism to pump water quickly. 18. Soda Acid is used for class A and B fires. It cuts off fuel supply to the fire but is corrosive. 19. Halon is an inert gas and is not used anymore because of its impact on Ozone layer. 20. FM-200 is another gas that is being used in place of Halon. 21. Fire extinguishers that use a gas to extinguish gas are called gas discharge systems.
4.6
Facility Design and Planning
1. Computing facilities should be able to withstand earthquakes, severe weather. 2. Electric and magnetic fields can cause data damage, especially data stored on magnetic devices. While designing facilities, this should be taken care of. 3. Lower humidity causes Electro Static Discharge (ESD) ESD is phenomenon when two objects at different voltage levels are brought together. This can damage circuits. Electrostatic discharge can be felt by humans as well when there is lower humidity. 4. Electro Magnetic Interference (EMI) and Radio Frequency Interference (RFI) are examples of noise. Facility should be built with considerations of these and other types of noise.
Copyright 2009 Rafeeq Rehman
Page: 48 of 93
Chapter Four: Physical Security 5. While choosing a location for data centers or facility, the following things should be considered: a. Study for natural disasters, earthquake faults, distance from rivers or other flood hazards, hurricanes, tornadoes. b. Distance from high visibility locations like railroads, airports, government buildings, military installations, electrical grids, etc. c. Crime areas are not good for building facilities. d. Convenience to communication locations such as roads, distance from local telephone centers. e. Distance to emergency facilities like police station, hospitals, fire stations and ambulance services. 6. External walls of a facility should be high enough for people to jump. Ideal height of external walls is 8 feet minimum. 7. Floors should be able to bear a load of minimum of 150 pounds per square foot. 8. Buildings must have secure shelter areas where employees can go in case of disasters like tornadoes.
4.7
Monitoring and Surveillance
1. Physical intrusion can be detected using photoelectric sensors, motion detectors, alarms and so on. 2. Motion detectors work on different technologies like wave patters changes related to motion, changes in electric field, sounds, heat waves, and infra-red light among others. 3. Alarms are used when an intrusion is detected. There are many types of alarms, including local, remote, centrally managed by other companies and police.
4.8
Attacks and Vulnerabilities
1. Programmable locks are vulnerable to shoulder surfing attacks. 2. Security guards are humans and can make mistakes. For example, they can't verify validity of all security badges.
Copyright 2009 Rafeeq Rehman
Page: 49 of 93
Chapter Four: Physical Security 3. Tail-gating is when an authorized person follows an authorized person to pass through doors and other security controls. 4. Social engineering attacks are used against physical security controls. 5. Dumpster diving dumpster diving is still one of the major attacks to steal company information. In dumpster diving, people look for things thrown in trash dumpsters to find information. Paper shredding should be used to take care of this issue. 6. Physical security helps in stopping theft of computers which is used not only for hardware but to get data from disks.
4.9
Miscellaneous
1. Physical security is neglected many times but is very important for safety of data.
Copyright 2009 Rafeeq Rehman
Page: 50 of 93
Chapter Five: Security Architecture and Design
Chapter Five
5 Security Architecture and Design
5.1 5.2
5.2.1
Definitions Computer and System Architecture
The Central Processing Unit - CPUCPU
1. Computer hardware consists of many building blocks like CPU, Memory, different types of buses, etc. 2. Memory is divided into two major parts: physical memory and virtual memory. Physical memory is the actual amount of RAM installed in a computer. Virtual memory is the disk space that computer can use as memory if physical memory is not enough for some process.
Copyright 2009 Rafeeq Rehman
Page: 51 of 93
Chapter Five: Security Architecture and Design 3. The Central Processing Unit or CPU has many components that include: a. Arithmetic and Logic Unit or ALU performs arithmetic and logic functions. b. The control unit controls the sequence in which different operations are performed. c. Memory Management Unix or MMU controls memory addressing and mapping memory addresses from virtual memory to physical memory. d. Registers are located inside the CPU and these are locations where CPU temporarily stored data and commands for processing. e. Floating Point Unit or FPU is used to perform floating point arithmetic efficiently. In older computers, FPU and CPU are two separate units. 4. CPU brings data and commands from memory and performs operations on data based upon these commands. Typical commands are ADD, MUL (multiply), JUMP, and so on. 5. CPUs can perform a fixed set of commands, called an instruction set instruction set. Different CPUs may have different instruction sets. 6. A CPU that can perform operation on 32 bit long numbers in one step is called a 32-bit CPU. Similarly there are 64-bit CPUs are well. 7. A CPU step is triggered by a clock chip. The speed of clock chip determines speed of CPU and how fast it can execute instructions. 8. Another way of measuring CPU speed CPU!CPU speed is in MIPS or millions of instructions per second 9. A Complex Instruction Set Computer or CISC and has usually single set of internal registers. 10. A Reduced Instruction Set Computer or RISC has simpler instructions but has multiple sets of internal registers. 11. CPUs usually have two major cycles: The fetch cycle is used to bring data and instructions from memory into CPU internal registers. The execute cycle is used to execute instructions. In some cases if data needs to be stored into the memory after execution, a third cycle store is also used to put data back to memory from CPU registers.
Copyright 2009 Rafeeq Rehman
Page: 52 of 93
Chapter Five: Security Architecture and Design
5.3 5.4 5.5
Security Architecture Models for Access Control Security Certification and Accreditation
1. Security Certification and Accreditation or SC&A is a process of project based work 2. The purpose of SC&A is to identity, document, assess, and convey risk to business owners so that they can make informed decisions. 3. Certifiers certifier are IT people who certify that due diligence has been done in assessing risk 4. Accreditors are the people who own the business process and they decide to assume a risk or mitigate it.
5.6 5.7 5.8
System Evaluation Attacks and Vulnerabilities Miscellaneous
Copyright 2009 Rafeeq Rehman
Page: 53 of 93
Chapter Six: Business Continuity and Disaster Recovery
Chapter Six
6 Business Continuity and Disaster Recovery
6.1
Definitions
Business Impact Analysis (BIA): Exploring any vulnerabilities in an organization and creating strategy to minimize impact. Disaster Recovery Plan (DRP): A document that shows processes to be followed in case a disaster happens. The plan includes steps to recover from the disaster. Its focus is on restoring normal business operations. Business Continuity Plan (BCP): A document that shows processes to be followed to ensure that business continues to function normally when a disaster happens. Its focus in on ensuring no (or minimal) interruption to business functions. Incident Response (IR): A documented process for handling different incidents.
Copyright 2009 Rafeeq Rehman
Page: 54 of 93
Chapter Six: Business Continuity and Disaster Recovery Maximum Tolerable Downtime (MTD): It is the maximum time a business can afford to be out of normal functionality. This is a parameter used in BCP. Recovery Time Objective (RTO): is the desired time to recover from any disruptions. Recovery Point Objective (RPO): is the affordable amount of data loss in terms of time. For example, if an organization can afford to lose data for 3 hours, the RPO will be 3 hours. Mutual or Reciprocal Agreement: Mutual agreements are made among multiple organizations to use each others facility in case a disaster strikes one company. Hot Site: is a location that has all infrastructure, HVC, computer systems and applications, networks ready and operational for use in case of a disaster. This is the most costly solution for BCP and DRP. Warm Site: This type of site has physical location and HVAC ready installed. Computer systems and network are available. You have to restore data to start business functions. Cold Site: This site is vacant and has only electric and may be network cabling. There is no equipment in this location. This is least expensive but takes more time to recover. Service Bureaus: are third parties that can provide data processing services.
6.2
Introduction
BCP and DRP are usually revised on an annual basis (at least). Disaster are either natural (e.g. earthquake, flood, etc) or man-made (e.g. fire, explosions, strikes, toxic material spill) People are always the first concern of BCP or DRP.
6.3
Business Impact Analysis (BIA)
1. BIA is performed to make an assessment for loss in case of a catastrophe or disaster. 2. The losses may be in many shapes and forms, including direct financial losses, additional expenses, violation of contracts, etc. 3. The loss estimation in BIA may be qualitative or quantitative
Copyright 2009 Rafeeq Rehman
Page: 55 of 93
Chapter Six: Business Continuity and Disaster Recovery 4. BIA included finding critical assets that are needed to keep performing business functions. 5. Typical critical assets are related to one of the following: a. Physical location and infrastructure (building, furniture, generators, etc) b. Personnel c. Network and telecom links d. Customer related systems e. Employee related critical systems (payroll, accounting, etc) 6. Financial impact may be in many categories, including but not limited to: a. Loss in revenue because of less or no sale b. Penalties for breach of service level agreements (SLA) c. Additional operational cost to operate at a different location in case of emergencies d. Loss of company reputation and customer confidence.
6.4
Parts of Business Continuity Plan (BCP)
1. BCP has four essential components including the following: a. Defining scope b. Perform BIA c. Develop a plan d. Get management approval and implement 2. A BCP includes many items including the following: a. Networks and servers b. Application software c. Workstations, desktops, telephone d. Telecommunication links
Copyright 2009 Rafeeq Rehman
Page: 56 of 93
Chapter Six: Business Continuity and Disaster Recovery e. Data f. Office space, office equipment like fax machines
g. HVAC h. Work around plans 3. When creating a BCP, criticality of assets must be identified. The BCP plan depends upon this assessment. 4. You also need to assess resource requirements for BCP
6.5
Disaster Recovery Plan (DRP)
1. DRP should include actions taken before, during, and after a disaster. 2. For testing plans, scheduling and scope of testing must be defined. Results of a test must be documented and used for updating plans. 3. The duration of testing must also be defined. 4. DRP can be testing using multiple ways. Five types of DRP tests are more common including: a. Check lists b. Walk through is done as a table top exercise where all stake holders get together and they walk through the plan based upon certain scenarios. c. Simulation is used for different disaster scenarios d. Parallel testing is done where normal business function continue and testing is performed in parallel e. Full interruption where all business functions are interrupted and a full disaster recovery process is tested. 5. Call tree exercises are used to ensure all phone numbers are accurate and people can communicate in a timely manner. 6. There are four more common types of groups defined in a DRP.
Copyright 2009 Rafeeq Rehman
Page: 57 of 93
Chapter Six: Business Continuity and Disaster Recovery a. The normal operations group is tasked with ensuring the normal operation of business continues in case of a disaster. b. The recovery group is tasked with recovering from a disaster. c. The salvage group is tasked with salvage and cleanup activities. d. Media, public, and employee relations group is responsible for communications to different communities about the situation and progress of the disaster recovery work. 7. Transaction redundancy is used to copy all transaction data to a remote location a. Electronic Vault b. Remote Journaling c. Database shadowing 8. DRP also includes resource external to organization (Fire department, vendors, FEMA, etc. 9. Plans must be accessible and placed where everyone can get in case of disaster. Multiple locations for plans are necessary in case one of the location is part of disaster.
6.6
Data Center Recovery
1. Data center recovery strategies include: a. Hot sites b. Cold sites c. Warm sites d. Mobile sites e. Reciprocal agreements
6.7
Attacks and Vulnerabilities
1. Any plan that is not tested does not improve recoverability posture.
Copyright 2009 Rafeeq Rehman
Page: 58 of 93
Chapter Six: Business Continuity and Disaster Recovery 2. BCP and DRP, if not updated on regular basis, get out of date because of changes and updates in systems and personnel. To keep the plans relevant, they must be reviewed at least on a yearly basis.
6.8
Miscellaneous
1. BCP is needed to avoid loss of revenue due to non-functioning of business. 2. Software escrow is a way to keep installation media of all software in a secure location so that in case of disaster, you have the software install media available. 3. Offsite backup for data are kept to ensure you have the data in case you lose a facility. Typical strategies for keeping offsite backup are to send backup tapes to a remote location on a regular basis.
Copyright 2009 Rafeeq Rehman
Page: 59 of 93
Chapter Seven: Telecommunication and Network Security
Chapter Seven
7 Telecommunication and Network Security
7.1
Definitions
1. Layered Network Model is a network approach where different functions of network are divided into different layers.
7.2
ISO-OSI Network Model
1. ISO is International Standards Organization ISO responsible for creating many 2. standards for different industries. 3. OSI or Open Systems Interface is a network model consisting of seven layers as listed below: i. Physical Layer Copyright 2009 Rafeeq Rehman Page: 60 of 93
Chapter Seven: Telecommunication and Network Security ii. iii. iv. v. vi. vii. Data Link Layer Network Layer Transport Layer Session Layer Presentation Layer Application Layer
4. Physical layer is the hardware, cabling, and other physical network components. Data on physical layer flows in terms of electrical signals or light signals. 5. Wireless medium may be a physical layer medium for wireless networks. 6. Data Link Layer or DLL data link layer is on top of physical layer. 7. DLL is divided into two sub-layers known as Logical Access Control or LLC and Medium Access Control or MAC. 8. MAC addresses are defined at DLL level. Typically a MAC address is 48-bit number written as six groups of hexadecimal number. 9. An example of MAC address is 34:32:F4:C3:00:14 10. Data packets at DLL layer are known as frames 11. Network layer is responsible for addressing, routing and point-to-point data delivery. 12. The Transport layer is responsible for end-to-end data delivery, error detection and recovery, packet sequencing and so on. 13. The Session layer creates sessions for communication between two hosts. It creates, manages, and tears down sessions. 14. The presentation layer takes care of converting different data formats in case hosts understand different data formats. 15. The application layer provides user interface and this is where a user interacts with a computer. As an example, a web browser is an application. 16. Each layer may contain different protocols. 17. When two hosts communicate, each layer from the sending side attaches its header to data and sends it to its lower layer until it reaches the physical layer. On the receiving
Copyright 2009 Rafeeq Rehman
Page: 61 of 93
Chapter Seven: Telecommunication and Network Security side, data flows from physical layer towards the application layer and each layer takes out its header information. 18. Layer headers are used to convey information between peer layers on the sending and receiving hosts. 19. ISO-OSI is a network model and is not a protocol itself. 20. Different layers on a host talk to each other using interfaces Data flow in layers of OSI model
7.3
TCP/IP Network Layers
1. TCP/IP is a five layer protocol i. ii. iii. iv. v. Physical Layer Data Link Layer IP Layer TCP/UDP Layer Application Layer
2. Routing happens at the IP layer 3. Sockets and ports work at the TCP/UDP layer 4. A socket is a combination of port number and IP address
7.3.1
Physical Layer
1. Physical layer in TCP/IP model is similar to physical layer in the OSI model. 2. Data transfer at the physical layer is in the form of 0s and 1s. 3. Different devices are used at the physical layer to test signal strength. 4. Security of physical layer is important to take care of different types of sniffing and snooping.
7.3.2
Data Link Layer
1. There are two main protocols used at the DLL layer level: Address Resolution Protocol (ARP) and Reverse Address Resolution Protocol (RARP).
Copyright 2009 Rafeeq Rehman
Page: 62 of 93
Chapter Seven: Telecommunication and Network Security 2. ARP is used to find MAC address of a host when IP address is known. 3. RARP is used to find IP address of a host when MAC address is known. 4. ARP and RARP are broadcast protocols. 5. A special MAC address FF:FF:FF:FF:FF:FF is used for broadcast packets. 6. BootP is another protocol used at the MAC layer. BootP or bootstrap protocol BootP is used in diskless workstations.
7.3.3
IP Layer
1. IP addresses are assigned to each host in this layer. 2. There are two main version of TCP/IP protocol being used today: IPv4 and IPv6 3. In IPv4, an IP address consists of four parts separated by a dot character. 4. Each part of an IP address is called an Octet and its value ranges from 0 to 255. 5. A typical IP address look like 192.168.32.77 6. Each IP address consists of a host part and a network part. The network part is common between all hosts on a network. The host part is unique for each host. 7. IP addresses are unique in a network. No two hosts can have the same IP address in a network.
7.3.4
Transport Layer and TCP/UDP
1. Transport Control Protocol or TCP is connection oriented protocol and guarantees data delivery. 2. User Datagram Protocol or UDP is connection-less protocol and does not guarantee data delivery. 3. TCP establishes connection between two hosts using 3-way handshake process. 4. In 3-way handshake, the initiator sends a SYN packet to recipient. The recipient sends a SYN-ACK packet. Then the sender sends an ACK packet to complete the handshake. 5. To close a communication, one party sends a FIN packet. Connection can also be closed by a reset (RST) packet. Note that RST is abnormal termination of a connection. 6. UDP may be faster than TCP because it does not have any connection management overhead.
Copyright 2009 Rafeeq Rehman
Page: 63 of 93
Chapter Seven: Telecommunication and Network Security 7. Both TCP and UDP protocols work on the basis of ports. The server side opens a port and listens for incoming connection requests on that port. port 8. Each port has a number between 1 and 65535. 9. Some ports are standardized for certain type of protocols. These are called well-known ports. 10. List of commonly used well-known ports is available at the end of the book. 11. Internet Message Control Protocol (ICMP) is used for sending different types of messages over TCP/IP network for flow control and information exchange. 12. The most common use of ICMP is ping command that is used to verify if a host is alive or dead. 13. UDP is commonly used for VoIP because loss of some packets can be tolerated in voice communication. 14. A socket is a combination of IP address and port number. An open port is associated with a socket.
7.3.5
Application Layer
1. Application layer has a number of protocols. Usually one protocol for each type of service.
Table: Application layer protocols
Protocol Purpose FTP SSH File Transfer Protocol, used for copying files from one host to another host. Secure Shell is a protocol used for remote login, secure file transfer, creating secure tunnels, etc. It is a protocol used for remote login. It is an old protocol and is not secure. It transmits data in clear text. Simple Mail Transfer Protocol which is used to transmit email from one host to another host. Domain Name System which is used to resolve host names to IP addresses and vice
Telnet
SMTP
DNS
Copyright 2009 Rafeeq Rehman
Page: 64 of 93
Chapter Seven: Telecommunication and Network Security versa. HTTP Hyper Text Transfer Protocol which is the main protocol for web traffic between web browsers and web servers. Secure HTTP Light Weight Directory Access Protocol used for directory access over a network. Post Office Protocol 3 which is used to retrieve email from a mail server. Internet Message Access Protocol is another protocol to get email messages from a server. Network Information Services is a protocol that is used in UNIX systems to login to any of the available machines on a local area network. Network Time Protocol is used to synchronize time among hosts on a network using a standard time source. Server Message Block is a protocol that is used to access resources, like files, from a remote host on a network
HTTPS LDAP POP3 IMAP
NIS
NTP
SMB
7.4
Network Tiers and Defense-in-Depth defense in depth
Defense in depth is a mechanism where an attacker has to cross multiple layers of network to get to data.
7.5
7.5.1
Network Services Security
Domain Name System or DNS
1. DNS uses port TCP 53 and UDP 53 to resolve host names to IP addresses and vice versa. 2. DNS server has records of data that are called Resource Records or RR. 3. Start Of Authority or SOA is a resource record that is used to enter information about the domains that a DNS server owns.
Copyright 2009 Rafeeq Rehman
Page: 65 of 93
Chapter Seven: Telecommunication and Network Security 4. NS or Name Server record is used to define IP addresses of DNS servers associated with a domain. 5. A records are used to assign IP address to a fully qualified domain name. 6. CNAME or Canonical Name record is used for creating aliases for domain names. 7. Multiple IP addresses can be assigned to the same host name to distribute traffic among many servers in a round-robin fashion. 8. Root servers are the servers on the Internet that are the ultimate source of finding information about a domain and the name servers that host that domain.
7.5.2
1. SMTP is usually used to send email from one machine to another whereas POP3 is used to retrieve email from a mail server. 2. SPAM is unwanted mass email that people send for things like marketing, selling stuff. 3. Phishing is a common attack to get information from others using email and fake web sites. 4. Spoofed emails are those emails that appear to be coming from a known source but they are not. 5. Email servers should not relay email from unknown sources. Unprotected email relays are used by spammers to send mass emails.
7.5.3
Web Servers
1. Apache, Microsoft IIS, Websphere, Weblogic are example of web servers. 2. Web servers maintain session variables session variable with a browser. Session variables are used to keep information related to a connection when a user is browsing a web site. 3. HTTP is a connection-less protocol. However, with the help of session variables, it can maintain a session active with web browser. 4. Buffer overflow is a common attack on web servers and web-based applications. 5. Regular web traffic uses TCP port 80 whereas secure web sites use TCP 443 port. However, a web server can use any port it likes and there is no restriction on using a specific port.
Copyright 2009 Rafeeq Rehman
Page: 66 of 93
Chapter Seven: Telecommunication and Network Security
7.5.4
Telnet
1. Telnet uses port 23 for remote login to a computer. It is a client-server protocol. 2. Telnet can also be used to check if a port is open or closed (e.g. mail server or web server). 3. Telnet is replaced by SSH which is a secure protocol for remote login.
7.5.5
Secure Shell or SSH
1. SSH is commonly used for remote login in a secure fashion. 2. SSH is also used for tunneling other protocols. 3. SSH uses TCP port 22.
7.5.6
FTP and SFTP
1. FTP or File Transfer Protocol is used for transferring files from one host to another in a network. 2. Regular FTP is not secure because data and username/password are sent in clear text. 3. Secure FTP uses SSH to transfer files. Both data and username/password are transmitted securely in SFTP.
7.5.7
TCP Wrappers
1. TCP wrappers are used to start network services on-demand e.g. when a connection request is received 2. Another use of TCP wrapper is to create another layer of security to protect these services. 3. TCP wrapper is an additional level of security and they can filter access to a network service.
7.5.8
Network Time Protocol or NTP
1. Network time protocol is used synchronize system time of a host with a standard time source. 2. Standard time sources may be dedicated devices, radio signals, or a server on local network or the Internet.
Copyright 2009 Rafeeq Rehman
Page: 67 of 93
Chapter Seven: Telecommunication and Network Security 3. Time synchronization is needed for systems like Kerberos where decision of validity of a ticket is made based upon the current time. 4. NTP used UDP port 23 for communication. 5. SNTP stands for Simple Network Time Protocol.
7.6
Network Transport Level Security
Security of data can be maintained at different levels. Transport level security means securing data when it is being sent from one place to another.
7.6.1 7.6.2 7.6.3
SSL/TLS SSL TLS IPSec and GRE Tunnels Secure Shell (SSH) SSH
7.7
Firewalls
Firewalls will
7.7.1 7.7.2
Application Layer Firewalls and Application Proxies Load Balancers
7.8 7.9
Network Address Translation or NAT Remote Access and Virtual Private Networks VPN
1. There are multiple types of VPNs, including: a. Site-to-Site VPN b. Hub-spoke VPN c. SSL VPN 2. VPN connections may use one or more of the following protocols: a. IPSec b. Point to Point Tunneling Protocol or PPTP Copyright 2009 Rafeeq Rehman Page: 68 of 93
Chapter Seven: Telecommunication and Network Security c. SSL VPN 3. Authentication in VPN connections may be performed using different techniques, including the following: a. X.509 Certificates b. Password Authentication Protocol or PAP c. Extensible Authentication Protocol or EAP d. Challenge Handshake Authentication Protocol or CHAP e. Microsoft CHAP or MS-CHAP
7.10
Intrusion Detection Systems IDS
1. Intrusion detection systems are categorized into two major categories: Anomaly based intrusion detection system and signature (or rule) based intrusion detection systems. 2. Anomaly based IDS listens to network traffic and generates alerts when it detects an anomaly in a packet 3. Signature based IDS works from a set of signatures and alert is generated when a signature (rule) is triggered.
Copyright 2009 Rafeeq Rehman
Page: 69 of 93
Chapter Seven: Telecommunication and Network Security
7.11 7.12
7.12.1
Commonly Used Ports and Protocols Cellular Networks
CDMA
7.12.2 GPRS 7.12.3 GSM 7.12.4 3G Wireless 7.12.5 EDGE 7.12.6 EVDO
7.13 7.14
Voice Over IP or VoIP Attacks and Vulnerabilities
1. DNS cache poisoning is a know attack which is used to redirect network clients to a malicious host instead of real host. 2. Cookie poisoning a common attack where an attacker changes contents of a cookie.
7.15
Miscellaneous
1. Network is the first line of defense against Internet attacks 2. Cookie is a small file that is saved by a server on the user computer. This file is used to keep information needed by web server. 3. Session cookies are used only during the duration of a communication session between web browser and web server. 4. Persistent cookies stay on disk on the user computer. Persistent cookies can be manually deleted by the user or by the web server.
Copyright 2009 Rafeeq Rehman
Page: 70 of 93
Chapter Eight: Application Security
Chapter Eight
8 Application Security
8.1
Definitions
1. Security By Obscurity is when people try to hide internal working of a system or application hoping an attacker will not be able to figure it out (very bad idea!) 2. Salted Hash functions are used if passwords are stored in a database to ensure dictionary attacks and rainbow attacks can be avoided
Copyright 2009 Rafeeq Rehman
Page: 71 of 93
Chapter Eight: Application Security
8.2
8.2.1 8.2.2 8.2.3
Security of Web Based Applications
Three-Tier Architecture User Registration and CAPTCHA Use of SSL
8.3 8.4 8.5 8.6
Securing Client/Server Applications Single Sign On (SSO) Cross Company Authentication (CCA) Common Attacks on Web-Based Applications
1. SQL injection 2. Command injection 3. Buffer overflow 4. Parameter validation 5. Phishing 6. Denial of service
8.7 8.8 8.9
Attacks and Vulnerabilities Miscellaneous Introduction
1. Software Development Life Cycle (SDLC)SDLC is helpful in building better software with less vulnerabilities and protections in place
Copyright 2009 Rafeeq Rehman
Page: 72 of 93
Chapter Eight: Application Security 2. Applications must provide authentication and authorization to allow only authorized users to access data 3. Sensitive data, e.g. passwords, must be encrypted while storing on file systems or databases 4. Application security depends on security of underlying infrastructure, including: a. Physical security of datacenter where application is hosted b. Security of hardware c. Operating system security d. Application platform including web server, middleware, etc e. Database security 5. Using secure coding techniques are important in creating secure application. 6. Good random number generators should be used to avoid different attacks related to brute force and statistical techniques
8.10 Software Development Life Cycle (SDLC)
1. Security Requirements gathering that include: a. Authentication and authorization requirements b. Physical security requirements c. Disaster recovery and business continuity requirements d. Data storage, backup, retrieval, and data destruction requirements e. Encryption requirements f. Regulatory and compliance requirements (GLBA, HIPAA, SOX, PCI, etc)
g. Interfaces to any existing systems for data exchanges h. Network connectivity to vendors or other third party service providers i. j. Audit and logging requirements Monitoring requirements
Copyright 2009 Rafeeq Rehman
Page: 73 of 93
Chapter Eight: Application Security k. Supporting processes, including helpdesk process 2. Including security features in the architecture and design of an application based upon security requirements 3. Testing application to ensure security requirements are properly met. Testing may include infrastructure testing using tools such as nmap, Nessus, Qualys as well as testing for web based applications using tools like Appscan, Web Inspect etc 4. Documenting all identified risk items with the application and mitigating the associated risk by putting in place compensating controls
8.11
Application Security Testing
1. Application security is tested at multiple levels using manual tests as well as security testing tools. a. Network testing using sniffers b. Testing for privilege escalation using different user IDs c. Code review that reveals different vulnerabilities in an application d. Testing for vulnerabilities in web-based applications using different security testing tools e. User of production data in test environment is another major issue f. Test for any hard-coded passwords or other hard-coded information
8.12 Security of Web Based Applications
1. Security of web-based application is very crucial because other perimeter defense measures (like firewalls) can't stop attacks against web applications. The reason is that system administrators have already opened firewall ports to web servers.
Copyright 2009 Rafeeq Rehman
Page: 74 of 93
Chapter Eight: Application Security
8.12.1 Three-Tier Architecture 8.12.2 User Registration and CAPTCHA 8.12.3 Web Server Security 8.12.4 Use of SSL
8.13 Security Web Services 8.14 AJAX and Web 2 Technologies
8.15 Securing Client/Server Applications
8.16 Single Sign On (SSO SSO)
1. SSO is important security measure to ensure users don't have to remember different passwords for each application. Multiple passwords force users to write them down on a paper, sticky notes, etc increasing the probability of password leakage.
8.17
Cross Company Authentication (CCA CCA)
8.18 Common Application Attacks and Flaws
1. SQL injection 2. Command injection 3. Buffer overflow Copyright 2009 Rafeeq Rehman Page: 75 of 93
Chapter Eight: Application Security 4. Parameter validation 5. Phishing 6. Denial of service 7. Many times a major problem with web-based applications is not handling error messages properly. As a result of this issue, many times error messages from databases and backend applications are displayed to users. These error messages may have contain information about internal working of databases or applications. It is important to display a standard error message instead of displaying application/database errors directly to users.
8.19 Attacks and Vulnerabilities 8.20 Miscellaneous
1. Developers should not have access to production systems 2. CMM or Capability Maturity Model is a framework for gauging maturity of the software development processes
Copyright 2009 Rafeeq Rehman
Page: 76 of 93
Chapter Nine: Operations Security
Chapter Nine
9 Operations Security
9.1
Definitions
1. Configuration Management is a process to control modification to hardware, software, documentation, firmware, configuration, and so on. This is done through change management process 2. Contingency Management is planning for ensuring availability of resources in emergency situations. This planning includes steps and actions to be taken before, during, and after an emergency situation or incident. This is done to ensure availability of critical resources. The contingency planning includes many items including but not limited to backup, storage, and testing of critical systems.
9.2
Introduction
1. Resources that need to be protected for secure operation include: a. Servers: Mail, Web, Directory, Authentication b. Backup and Files: Password files, backup media, configuration files, libraries c. Application Software: Customer applications, source code, design documents d. Network and Communication standardized configurations equipment: Routers, switches, wireless,
Copyright 2009 Rafeeq Rehman
Page: 77 of 93
Chapter Nine: Operations Security e. Logs: Audit logs for systems and applications f. Printers: Multi-function machines, paper printouts
9.3
9.3.1 9.3.2 9.3.3 9.3.4 9.3.5
Securing Server
Securing Windows Servers Securing UNIX/Linux Servers Securing Mail Servers Securing Web Servers Creating Server Check Lists and Security Templates
9.4 9.5 9.6 9.7 9.8 9.9
Securing Desktop Patch Management Vulnerability Testing Password Cracking Data Destruction Attacks and Vulnerabilities
9.10 Miscellaneous
1. To recover from a failure, there can be three types of restarts: Reboot, emergency restart, and cold restart 2. Reboot and emergency restart are done in a controlled manner whereas cold restart results in some information loss.
Copyright 2009 Rafeeq Rehman
Page: 78 of 93
Chapter Nine: Operations Security
Copyright 2009 Rafeeq Rehman
Page: 79 of 93
Chapter Ten: Legal, Regulations, Compliance and Investigation
Chapter Ten
10 Legal, Regulations, Compliance and Investigation
10.1
Definitions
Denial of Service (DoS): The attacker tries to overload computer resources such that the computer is not able to do its regular function.
Copyright 2009 Rafeeq Rehman
Page: 80 of 93
Chapter Ten: Legal, Regulations, Compliance and Investigation Distributed Denial of Service (DDoS): An attack where the attacker uses a large number of computers on the Internet to attack a company infrastructure. This type of attack is common for famous web sites. Data Diddling: It is a way to alter data during or before it is entered into a database. Logic Bomb: is a program or a process that runs at a specific time. This is done usually by disgruntled employees. They plan this kind of software that is executed after they have left the company. Trojan Horse: is usually a computer program that is disguised as something else. It may be a an altered program as well. Its name is derived from Greek history of city of Troy. Typically it is used for malicious purposes like stealing data. 414 Gang: was a group of teenagers in Wisconsin telephone area code 414 who attacked medical records of hospital. Intellectual property: is non-tangible property (e.g. an invention, idea, book, etc) that other people cant use without permission from the owner of the property. Copyright: is to protect work of authors. Trade Secret: are not patents or copyrighted materials. These are company secrets that are held very tightly by a small group of people inside the company (e.g. Coca Cola recipe) Phreakers are hackers who break into PBX and telephone systems. Major known hacker groups are 2600 group and 414 Club. 2600 is a tone pattern to get long distance access and 414 club consisted of people in this area code. Blue Box is the name for a box that created 2600 Hz tone to trick telephone systems for long distance calls. Red Box simulates tones for coins dropping in pay phones. Black Boxes manipulate voltage levels to get toll free calling. Information warfare: This is relatively a modern term used for governmental level actions against other countries.
Copyright 2009 Rafeeq Rehman
Page: 81 of 93
Chapter Ten: Legal, Regulations, Compliance and Investigation
10.2 Computer Crimes
1. Common computer crimes: a. Password theft b. DoS or DDoS c. Eavesdropping d. Spreading malware e. Internet fraud 2. DoS may result as overloading of resources or crashing a system using some vulnerability.
10.3 Ethics
10.4 Laws
1. Title 18: Title 18 of US Code (U.S.C) is crime and criminal procedures. Most of computer crimes come under this law. 2. Common Law: Common Law is practiced in US and many other countries. It has three branches of government: executive, judicial, and legislative. 3. Common law has three categories: Criminal, civil, and administrative. 4. In United States, patents are granted by US Patent and Trademark office (http://uspto.gov/) 5. Patents can fall into multiple categories such as design, utility, process, etc. 6. Patents expire after a certain period of time which is different for types of patents and the countries where they are obtained. 7. It is possible to get international patents.
Copyright 2009 Rafeeq Rehman
Page: 82 of 93
Chapter Ten: Legal, Regulations, Compliance and Investigation
10.5 Incident Management
10.6 Investigation and Forensics 10.7 Attacks and Vulnerabilities
10.8 Miscellaneous
Copyright 2009 Rafeeq Rehman
Page: 83 of 93
Appendix A: Commonly Used TCP and UDP Ports
Appendix A
11 Commonly Used TCP and UDP Ports
This chapter lists most commonly used port numbers that may be asked in CISSP exam.
Port Number & Port Description
Port Number TCP/20 TCP/21 TCP/22
Port Description FTP data transfer FTP control channel Secure shell of SSH used for secure remote login, secure file transfer, and many other purposes Telnet program used for remote login
TCP/23
Copyright 2009 Rafeeq Rehman
Page: 84 of 93
Appendix A: Commonly Used TCP and UDP Ports
TCP/25 TCP/53 UDP/53 TCP/80 TCP/110 TCP/443
SMTP or Simple Mail Transfer Protocol. This is used for email transfer DNS zone transfer DNS Queries HTTP port used for web traffic POP3 port used by email clients to retrieve email from mail servers Secure HTTP web traffic used for secure Internet web browsing, especially for ecommerce solutions, banks, and other confidential data transfer NTP or network time protocol used for time synchronization among servers and workstations and LDAP server
UDP/123
TCP/389 UDP/389 TCP/636 UDP/636 TCP/135 UDP/137 UDP/138 UDP/139 UDP/67 UDP/445 TCP/143 TCP/993
and Secure LDAP or LDAP over SSL
RPC RPS or remote procedure calls NetBIOS name resolution NetBIOS datagram service NetBIOS session service DHCP server SMB service IMAP IMAP over SSL
Copyright 2009 Rafeeq Rehman
Page: 85 of 93
Appendix A: Commonly Used TCP and UDP Ports
TCP/995 TCP/88 UDP/88 TCP/1723 UDP/161 UDP/162 TCP/515 TCP/3389 UDP/69
POP3 over SSL and Kerberos
PPTP, Point to point tunneling protocol used for VPN. SNMP SNMP Traps LPD or Line Printer Daemon protocol mostly used on network printing. Terminal services in Microsoft Windows. TFTP or Trivial File Transfer Protocol TFTP
Copyright 2009 Rafeeq Rehman
Page: 86 of 93
Appendix B: Glossary
Appendix B
12 Glossary
Item OTP SSH
Description One Time Passwords which are randomly generated and used only once. Secure Shell is a mechanism to log on to remote servers in a secure way. The protocol establishes a secure communication tunnel between two end points for data transport. Digital Certificate or X.509 Certificate is the electronic information that identifies an entity. The entity may be a person, a server, or any other device to name a few. The certificate may also be used for applications and in many scenarios authentication and authorization is done using certificates. Certificates are also used to encrypt internet traffic, like SSL or sending secure email. Interactive Voice Response is a system used with traditional telephony to get information over telephone. Single Sign On
Digital Certificate
IVR
SSO
Copyright 2009 Rafeeq Rehman
Page: 87 of 93
Appendix B: Glossary
CCA SSL Consumer
Cross Company Authentication Secure Socket Layer Consumer is web-enables application that uses the OpenID system for authentication purposes. See Consumer
Relying Party RAID
Redundant Array of Inexpensive Disks. This is a technology used in computers to achieve high availability, fault tolerance, and better performance. In many RAID systems, failure of a single disk does not result in loss of data.
Copyright 2009 Rafeeq Rehman
Page: 88 of 93
Appendix C: Index
Appendix C
13 Index
Availability, 10, 22 Business Continuity Plan (BCP), 54 Business Impact Analysis (BIA), 54 CCA, 68, 82 CER, 26 CIA, 13 ciphertext, 33 cleartext, 33 Confidentiality, 10, 22 Crossover Error Rate. See CER Cryptanalysis, 33 Cryptography, 33 DAD, 13 Defense-In-Depth, 10 DES, 35 Digital Certificate, 81 Digital Encryption Standard. See DES Disaster Recovery Plan (DRP), 54
Disclosure-Alteration-Destruction, 13 Incident Response (IR), 54 Integrity, 10, 22 IVR, 81 Kerberos, 24 LDAP, 24 least-privileges, 22 OpenLDAP, 24 OTP, 81 Phreakers, 77 Plaintext, 33 RAID, 14, 82 Service Level Agreement, 11, 12 Single Point of Failure, 10 SLA, 12, See Service Level Agreement SSH, 81 SSL, 68, 81, 82 SSO, 24, 68, 81 Page: 89 of 93
Copyright 2009 Rafeeq Rehman
Appendix C: Index work factor, 33
Copyright 2009 Rafeeq Rehman
Page: 90 of 93
Appendix D: Sample Questions
Appendix D
14 Sample Questions
14.1
Introduction
There are many questions in this section. The author has tried to make these questions as close to the actual CISSP exam questions as possible. However, please note that the questions are listed here only as a reference and actual exam questions may be quite different. The key to passing the exam to be ready at a conceptual level and not try to memorize any content. The field of information security is very dynamic and you have to keep yourself updated on a continuous basis.
14.2 Questions
1. Which of the following is not an encryption algorithm9? a. 3DES b. AES c. RSA
The answer to this question is MD5 which is a hash algorithm and not an encryption algorithm. All others are encryption algorithms.
9
Copyright 2009 Rafeeq Rehman
Page: 91 of 93
Appendix D: Sample Questions d. MD5
Copyright 2009 Rafeeq Rehman
Page: 92 of 93
Appendix D: Sample Questions
Policy and Exception Management (PolicyDOC)
Policy and Policy Exception Management Software Features
1. Web-based software with no client requirements 2. Centralized policy management for all corporate policies, information security policies and procedures 3. Policy exception management and PDF exception file generation 4. The system comes as VmWare appliance with all software prebuilt and configured. However, you can choose to install it on your server as well 5. Drag and drop functionality to re-arrange policy sections 6. Printing policies in PDF format 7. Online submission and processing of policy exception requests 8. Role-based access to the application with policy approval process 9. Embedded HTML editor with commonly used editor functionality 10. Spell checking 11. Policy exception signatures 12. Search capability to look for policy sections related to a particular scenario 13. Policy exception reports and alerts (the graphs above show a screenshot) 14. Option to subscribe to notifications for any policy changes. You will be notified whenever a policy change happens with old and new text 15. PDF file generation for policy exceptions
Major Benefits
All policies are up-to-date all the time and accessible for users Exceptions to policies can be requested online Get notification for expired exceptions Provides web-based interface You can tweak policy in case number of exceptions on a particular policy section exceeds a certain limit No need for distribution of updated policies to all audience thus avoiding out-of-sync problem related to policy documents
Get PCI compliance for PCI DSS Section 12
http://www.policydoc.com
Copyright 2009 Rafeeq Rehman Page: 93 of 93
S-ar putea să vă placă și
- Cissp Step by Step GuideDocument1 paginăCissp Step by Step GuideKady YadavÎncă nu există evaluări
- 7 Types Hard CISSP Exam QuestionsDocument6 pagini7 Types Hard CISSP Exam QuestionsIndarko WiyogoÎncă nu există evaluări
- CISSP NotesDocument2 paginiCISSP Notesfrédéric Masiala0% (1)
- CISSP preparation guide and resourcesDocument2 paginiCISSP preparation guide and resourcesDavid WilliamsÎncă nu există evaluări
- EC-Council Certified Security Analyst Standard RequirementsDe la EverandEC-Council Certified Security Analyst Standard RequirementsÎncă nu există evaluări
- 0-CISSP Flash Cards Draft 6-6-2010Document126 pagini0-CISSP Flash Cards Draft 6-6-2010Maurício SilvaÎncă nu există evaluări
- CISSP Study Guide NotesDocument5 paginiCISSP Study Guide NotesElle Rose0% (1)
- CISSP Exam Study PlanDocument7 paginiCISSP Exam Study Planravi kantÎncă nu există evaluări
- CISSP Study PlanDocument1 paginăCISSP Study PlanAnonymous RA353CÎncă nu există evaluări
- Domain 1 CisaDocument93 paginiDomain 1 CisaRehanaÎncă nu există evaluări
- CISSP Aide Memoire20v4Document11 paginiCISSP Aide Memoire20v4momoTNÎncă nu există evaluări
- New CISSP Certification 2015Document29 paginiNew CISSP Certification 2015ramsramboÎncă nu există evaluări
- Cgeit PDFDocument5 paginiCgeit PDFdaleel enta0% (1)
- Emerging Technology Analysis - SOARDocument11 paginiEmerging Technology Analysis - SOARsharmasunil6325Încă nu există evaluări
- Knet Cissp 10Document847 paginiKnet Cissp 10Ali KayacanÎncă nu există evaluări
- CISSP Session 04Document93 paginiCISSP Session 04wfelicescÎncă nu există evaluări
- CISSP Exam Outline English April 2021 PDFDocument16 paginiCISSP Exam Outline English April 2021 PDFKevin MonkamÎncă nu există evaluări
- CISSP Test TemplateDocument37 paginiCISSP Test TemplateRichard WilliamsÎncă nu există evaluări
- YZA.A2 CISSP Practice Exam Security & Management AnswersDocument15 paginiYZA.A2 CISSP Practice Exam Security & Management AnswersChaz FranklinÎncă nu există evaluări
- Test 2015 CSSLPDocument158 paginiTest 2015 CSSLPAnonymous prxufEbSÎncă nu există evaluări
- 390 - Certified Cloud Security Professional CCSP - 1572385660 PDFDocument231 pagini390 - Certified Cloud Security Professional CCSP - 1572385660 PDFBalan WvÎncă nu există evaluări
- CISSP Exam Notes Physical Security v1.1Document18 paginiCISSP Exam Notes Physical Security v1.1Franck WurtzÎncă nu există evaluări
- C-CISO-Eligibility-Form UpdatedDocument14 paginiC-CISO-Eligibility-Form UpdatedAni SonÎncă nu există evaluări
- Security 701 Exam Objectives Comparison Flyer OnlineDocument4 paginiSecurity 701 Exam Objectives Comparison Flyer OnlineWayne WayneÎncă nu există evaluări
- CISSP Mind Maps by Matheus PDF 1638358395Document10 paginiCISSP Mind Maps by Matheus PDF 1638358395Rodrigo Juan100% (1)
- Exam Cissp: Physical Security Principles & ControlsDocument34 paginiExam Cissp: Physical Security Principles & ControlsN Chandra SekharÎncă nu există evaluări
- Cissp CramDocument36 paginiCissp CramAniket Bhosle100% (1)
- Top 100+ Cyber Security Interview Questions and AnswersDocument27 paginiTop 100+ Cyber Security Interview Questions and AnswersDwayne PereiraÎncă nu există evaluări
- Cybersecurity Risk Management A Complete Guide - 2021 EditionDe la EverandCybersecurity Risk Management A Complete Guide - 2021 EditionÎncă nu există evaluări
- CISSP - Cryptography Drill-Down HandoutDocument43 paginiCISSP - Cryptography Drill-Down HandoutPremdeepakHulagbaliÎncă nu există evaluări
- Owasp MobileDocument50 paginiOwasp MobileNarasimha Rao AkundiÎncă nu există evaluări
- SSCP Questions Study GuideDocument27 paginiSSCP Questions Study Guidervnkrish24100% (1)
- 1119416876-CompTIA Security+ Study Guide by Emmett DulaneyDocument5 pagini1119416876-CompTIA Security+ Study Guide by Emmett DulaneygoxosipiÎncă nu există evaluări
- Qualified Security Assessor Complete Self-Assessment GuideDe la EverandQualified Security Assessor Complete Self-Assessment GuideÎncă nu există evaluări
- Network Security A Complete Guide - 2021 EditionDe la EverandNetwork Security A Complete Guide - 2021 EditionÎncă nu există evaluări
- Key Mnemonics To Know - CisspDocument4 paginiKey Mnemonics To Know - CisspSairam R KonalaÎncă nu există evaluări
- The SSCP Prep Guide: Mastering the Seven Key Areas of System SecurityDe la EverandThe SSCP Prep Guide: Mastering the Seven Key Areas of System SecurityÎncă nu există evaluări
- Thor Teaches Study Guide CISSP Domain 8Document30 paginiThor Teaches Study Guide CISSP Domain 8baby100% (1)
- CISSP Referenced The Reddit Forum WeeklyDocument2 paginiCISSP Referenced The Reddit Forum WeeklySakil MahmudÎncă nu există evaluări
- How To Prepare For The CISSP Exam: Outline, Study Tips & StrategyDocument37 paginiHow To Prepare For The CISSP Exam: Outline, Study Tips & StrategyDodo winyÎncă nu există evaluări
- The Ultimate Guide To The: Jumpstart Your IT Security CareerDocument13 paginiThe Ultimate Guide To The: Jumpstart Your IT Security CareereppoxroÎncă nu există evaluări
- CCSK Prep Guide V3Document4 paginiCCSK Prep Guide V3satish_networkerÎncă nu există evaluări
- CISSP ExqsDocument20 paginiCISSP Exqssentoubudo1647Încă nu există evaluări
- Cybersecurity Regulations A Complete Guide - 2021 EditionDe la EverandCybersecurity Regulations A Complete Guide - 2021 EditionÎncă nu există evaluări
- CCISO BattleCardDocument1 paginăCCISO BattleCardDeveney Roberts0% (1)
- Cloud Security Compliance A Complete Guide - 2021 EditionDe la EverandCloud Security Compliance A Complete Guide - 2021 EditionÎncă nu există evaluări
- Ins Important QuestionsDocument3 paginiIns Important QuestionsSanjanaÎncă nu există evaluări
- CISSP Domain 2 v2 CompleteDocument29 paginiCISSP Domain 2 v2 CompleteJeff EdstromÎncă nu există evaluări
- Certified Information Security Manager Second EditionDe la EverandCertified Information Security Manager Second EditionÎncă nu există evaluări
- CAS-003 VCE DumpsDocument10 paginiCAS-003 VCE Dumpsnancy williamÎncă nu există evaluări
- CNDDocument4 paginiCNDDandy GonzálezÎncă nu există evaluări
- MYcolour TrendsDocument13 paginiMYcolour TrendsShiferawBekeleÎncă nu există evaluări
- CRACK TOUGH CISSP EXAMDocument6 paginiCRACK TOUGH CISSP EXAMrahuls256Încă nu există evaluări
- Certified in CCISODocument22 paginiCertified in CCISOmostoles0% (1)
- ET 115 ch1-ch6 QuizDocument18 paginiET 115 ch1-ch6 QuizhyperphackÎncă nu există evaluări
- UltimateGuideCCSP 2018Document13 paginiUltimateGuideCCSP 2018Manish JoshiÎncă nu există evaluări
- Internet Gateway Best Practice Security PolicyDocument52 paginiInternet Gateway Best Practice Security Policyalways_redÎncă nu există evaluări
- Cyber Security: Importance and ThreatsDocument73 paginiCyber Security: Importance and ThreatsShreya KiniÎncă nu există evaluări
- Error Code - List Konica MinoltaDocument13 paginiError Code - List Konica MinoltaEdgarÎncă nu există evaluări
- Function CategoryDocument15 paginiFunction CategoryFrancesco F.Încă nu există evaluări
- RSA Algorithm in CryptographyDocument3 paginiRSA Algorithm in CryptographyKanwal PreetÎncă nu există evaluări
- Data Security by AES Advanced Encryption StandardDocument5 paginiData Security by AES Advanced Encryption StandardEditor IJTSRDÎncă nu există evaluări
- SplunkDocument12 paginiSplunkSantosh KumarÎncă nu există evaluări
- CF 5Document42 paginiCF 5b meherbabaÎncă nu există evaluări
- Name: Josie C. Cesista Bsit 3N Student No.: Warm Up ActivityDocument13 paginiName: Josie C. Cesista Bsit 3N Student No.: Warm Up ActivityRodjean SimballaÎncă nu există evaluări
- CSCU Module 04 Data Encryption PDFDocument23 paginiCSCU Module 04 Data Encryption PDFSandeep Roy100% (1)
- Web Security Vulnerabilities ExplainedDocument10 paginiWeb Security Vulnerabilities ExplainedNadeem MalikÎncă nu există evaluări
- Security Misconfiguration v2Document6 paginiSecurity Misconfiguration v2erickÎncă nu există evaluări
- Vulnerability Management Guideline v1.0.0 PUBLISHEDDocument11 paginiVulnerability Management Guideline v1.0.0 PUBLISHEDJean Dumas MauriceÎncă nu există evaluări
- Firewall Security Review: Audit ReportDocument20 paginiFirewall Security Review: Audit ReportAbhishek BahiratÎncă nu există evaluări
- Implement Least Privilege with a Guide to Accounts, Groups, and RestrictionsDocument9 paginiImplement Least Privilege with a Guide to Accounts, Groups, and RestrictionsAhmed M. SOUISSIÎncă nu există evaluări
- Private key encryption and recovery in blockchainDocument23 paginiPrivate key encryption and recovery in blockchainJackÎncă nu există evaluări
- Cryptosoft: Divya G.R. Gigi P.S. Sethuparvathi CDocument35 paginiCryptosoft: Divya G.R. Gigi P.S. Sethuparvathi Chunt4djÎncă nu există evaluări
- Exam 1 SampleDocument4 paginiExam 1 SampleAhmer MehmoodÎncă nu există evaluări
- Career Path to Chief Information Security OfficerDocument1 paginăCareer Path to Chief Information Security OfficeradyanganefiÎncă nu există evaluări
- If You Have To Both Encrypt and Compress Data During TransmissionDocument12 paginiIf You Have To Both Encrypt and Compress Data During TransmissionPallavi BhartiÎncă nu există evaluări
- BSBXCS402 Assessment Task 2 V4 Digital Marketing PDFDocument61 paginiBSBXCS402 Assessment Task 2 V4 Digital Marketing PDFHafizshoaib381Încă nu există evaluări
- question paperDocument2 paginiquestion paperDr. Jayanthi V.S.Încă nu există evaluări
- SSL Certificates Provide Simple Website SecurityDocument8 paginiSSL Certificates Provide Simple Website SecurityPIVLLCÎncă nu există evaluări
- Past Question ICSDocument2 paginiPast Question ICSAnanya SwaminathanÎncă nu există evaluări
- Cyber Handbook Enterprise Latest Pages DeletedDocument37 paginiCyber Handbook Enterprise Latest Pages DeletedRaghuram CoorgÎncă nu există evaluări
- Sneha Chideti New England College Database SecurityDocument3 paginiSneha Chideti New England College Database Securitycofoje9006Încă nu există evaluări
- Bio-Metrics Data Correction Form PDFDocument1.011 paginiBio-Metrics Data Correction Form PDFNehal TohaniÎncă nu există evaluări
- A Personal Privacy Data Protection Scheme For Encryption and Revocation of High-Dimensional Attri-1Document4 paginiA Personal Privacy Data Protection Scheme For Encryption and Revocation of High-Dimensional Attri-1DhineshÎncă nu există evaluări
- IT Access Control Policy SummaryDocument10 paginiIT Access Control Policy SummarySanthosh Krishnan100% (2)