Documente Academic
Documente Profesional
Documente Cultură
Configure Windows XP/Vista L2TP Client & Zeroshell VPN Basics
Încărcat de
Loly MarreroDescriere originală:
Titlu original
Drepturi de autor
Formate disponibile
Partajați acest document
Partajați sau inserați document
Vi se pare util acest document?
Este necorespunzător acest conținut?
Raportați acest documentDrepturi de autor:
Formate disponibile
Configure Windows XP/Vista L2TP Client & Zeroshell VPN Basics
Încărcat de
Loly MarreroDrepturi de autor:
Formate disponibile
Configuring Windows XP/Vista L2TP client & Zeroshell Basics:
Boot from zeroshell CD then log into your zeroshell box. With the default image/configs it is ready to accept L2TP connections by simply enabling the check box in the /NETWORK/VPN/Host-toLAN (L2TP/IPSEC) GUI menu and USERS/RADIUS enable. Watch for the radius warning.
Zeroshell is ready now its time to setup the clients. The admin account on zeroshell is created by default well just use that one for demonstration purpose. Now you want to create a host file certificate for each computer that will be accessing your L2TP vpn server (i.e. zeroshell box). Click on NETWORK/Hosts/Add
Now select your user admin account USERS/Users/View and make sure L2TP is checked so that this user is allowed to connect.
Thats all with zeroshell. Now move on to your clients PC. In your windows XP computer Create a new connection from Control Panel/Network Connections. In windows Vista Set up a connection or network from Control Panel/Network and Internet/Connect to a network.
Screenshots of windows XP below
Thats the end of the basics.
Screenshots of Vista are essentially the same so Im not going to put them here.
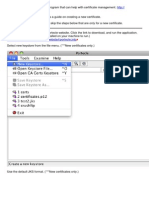
Preparation Download all your certificates from the machine you will be connecting the L2TP session or place them on a thumbnail/jump drive. You will need the host certificate that you created earlier on zeroshell for your computer and also the zeroshell CA or root Certificate of Authority. Go to your zeroshell log in screen to get the certificates you need. You can click on CA to download the root certificate and then Hosts to get your certificate for your computer. You dont need to be logged on to the zeroshell box, in fact its better that youre not logged on.
For the root CA it is important (on windows machines) to export the certificate with the *.DER file extension and NOT THE *.PEM file. Now under Hosts choose your host certificate and export the PKCS#12 (PFX) file.
Advanced:
To complete the following you should be logged on an Administrator account on your client PC. I will assume you did everything correct with the zeroshell CA and exported your host certificate (pkcs #12, der or pem file to your remote computer, example hostname.pfx) and now you want to configure windows XP or Vista computer. Note: For the certificate store windows will either default to use option "Automatically select the certificate store based on the type of certifcate" or "Place all certificates in the following store". We're talking about windows here so if that options doesn't import the certificate well use the other option. The object is to get the certificate imported into the correct store.
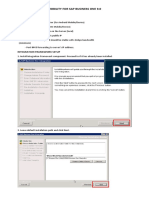
_______Part 1 of 4_______ Log on an Administrator Account and use the Run. Type "MMC" and when the console opens click, FileAdd/Remove Snap-in.
Click Add-Certificates-Add-"Computer Account" Click Next-Local Computer-Finish
Once again, Click Add-Certificates-Add-"Service Account" Click Next-Local Computer-Next-IPSEC Services-Finish
Now Click OK, Expand "Certificates(Local Computer)"
Right Click Personal-All Tasks-Import...-"hostname.pfx"-Next-Next-Automatically Select Certificate Store-Next-Finish
Expand "Certificates(Local Computer)"-Personal-Certificates Now you should see your "hostname"
_______Part 2 of 4_______ Now Click OK, Expand "Certificates - Service (IPSEC Services) on Local Computer" Right Click PolicyAgent\Personal-All Tasks-Import...-"hostname.pfx"-Next-Next-Automatically Select Certificate Store-Next-Finish
Expand "Certificates - Service (IPSEC Services) on Local Computer"-PolicyAgent\Personal-Certificates Now you should see your "hostname"
_______Part 3 of 4_______ Last detail you need to import is the Trusted Root Certification Authorities or your "Zeroshell CA". Easy method is to: Export the der or pem file from your Zeroshell CA to your computer (Zeroshell_CA.der) Expand "Certificates(Local Computer)" Right Click Trusted Root Certification Authorities-Certificates-All Tasks-Import...-"Zeroshell_CA.der"Next-Next-Place all certificates in the following store-Trusted Root Certification Authorities-Next-Finish
Now Expand "Certificates(Local Computer)"-Trusted Root Certification Authorities-Certificates Now you should see your "Zeroshell_CA"
_______Part 4 of 4_______ Review: You should see the hostname of your computer in 2 places, Certificates(Local Computer)-Personal-Certificates & Certificates - Service (IPSEC Services) on Local Computer-PolicyAgent\Personal-Certificates You should see the Zeroshell_CA in 2 places Certificates (Local Computer)-Trusted Root Certification Authorities-Certificates & Certificates - Service (IPSEC Services) on Local Computer-PolicyAgent\Trusted Root Certification Authorities-Certificates
Note: When you add the Zeroshell_CA to the Certificates(Local Computer) it gets added by default to Certificates - Service (IPSEC Services) but if it doesn't you need to manually add it like we did with the other ones. When I say manually I mean instead of letting the certificate store automatically get selected instead import it directly to the correct certificate store and use Place all certificates in the following storeoption or the default windows selects. Note: After completing these steps you can Create a vpn connectoid for Windows Vista & Windows XP with the default settings. In the Networking tab you should select L2TP IPSec VPN. Under Security use Typical(recommended settings) with checkbox Require data encryption (disconnect if none). Note: Hosts should have same domain as the zeroshell box unless you know what youre doing with Kerberos 5 domain/realm trust relationships.
Click the vpn shortcut we created earlier.
The End
Created by vpn_rollercoaster
S-ar putea să vă placă și
- Hiding Web Traffic with SSH: How to Protect Your Internet Privacy against Corporate Firewall or Insecure WirelessDe la EverandHiding Web Traffic with SSH: How to Protect Your Internet Privacy against Corporate Firewall or Insecure WirelessÎncă nu există evaluări
- Configure ZeroShell WPA Enterprise Step-by-Step GuideDocument16 paginiConfigure ZeroShell WPA Enterprise Step-by-Step GuidezachwormsÎncă nu există evaluări
- Manual OpenCADocument6 paginiManual OpenCAsolovinooneÎncă nu există evaluări
- Setup OpenVPN on Pfsense 2.0 with Local User AuthDocument15 paginiSetup OpenVPN on Pfsense 2.0 with Local User AuthKarla TechiÎncă nu există evaluări
- How to Setup a Windows PC: A Step-by-Step Guide to Setting Up and Configuring a New Computer: Location Independent Series, #4De la EverandHow to Setup a Windows PC: A Step-by-Step Guide to Setting Up and Configuring a New Computer: Location Independent Series, #4Încă nu există evaluări
- Windows Server 2016 Installation and ConfigurationDocument47 paginiWindows Server 2016 Installation and ConfigurationAziz LbaibiÎncă nu există evaluări
- Setup of a Graphical User Interface Desktop for Linux Virtual Machine on Cloud PlatformsDe la EverandSetup of a Graphical User Interface Desktop for Linux Virtual Machine on Cloud PlatformsÎncă nu există evaluări
- XcaDocument16 paginiXcaLuis Arturo Ovando DominguezÎncă nu există evaluări
- WWW - tcs-CA - Tcs.co - in Index - JSP LeftHtml HTML Faqsleft - HTDocument9 paginiWWW - tcs-CA - Tcs.co - in Index - JSP LeftHtml HTML Faqsleft - HTsumitsemwalÎncă nu există evaluări
- Mobility For Sap Business One 9.0: Integration Framework SetupDocument13 paginiMobility For Sap Business One 9.0: Integration Framework SetupRobeth John BacalanÎncă nu există evaluări
- Complete Pangya Setup Guide v1.2Document24 paginiComplete Pangya Setup Guide v1.2BananaspiltÎncă nu există evaluări
- Network Licensing Installation GuideDocument11 paginiNetwork Licensing Installation GuideKishore SakhileÎncă nu există evaluări
- Pxe Wds Server Setup SopDocument45 paginiPxe Wds Server Setup SopAlexandru CureaÎncă nu există evaluări
- INetsim SetupDocument13 paginiINetsim SetupNguyen HoangÎncă nu există evaluări
- How To Configure PfSenseDocument15 paginiHow To Configure PfSenseAung Kyaw Thu100% (1)
- Steps_to_activate_LAN_Windows__1_Document4 paginiSteps_to_activate_LAN_Windows__1_maxev92106Încă nu există evaluări
- Step 1: Familiarize Yourself With Your Current Setup: 8 Steps TotalDocument9 paginiStep 1: Familiarize Yourself With Your Current Setup: 8 Steps TotalThe Fern Residency PuneÎncă nu există evaluări
- DDWRT OpenVPN Setup GuideDocument33 paginiDDWRT OpenVPN Setup Guidepedrama2002Încă nu există evaluări
- PitDocument3 paginiPitdibiyaÎncă nu există evaluări
- CSEC630 Lab2 - IDS Revised 20110614Document18 paginiCSEC630 Lab2 - IDS Revised 20110614acg49100% (1)
- WFH DocumentDocument18 paginiWFH DocumentBach TruongÎncă nu există evaluări
- Installing A Secure Pcanywhere 10.5 Remote On WindowsDocument13 paginiInstalling A Secure Pcanywhere 10.5 Remote On WindowsDaniel BPÎncă nu există evaluări
- VoipNow Professional 2 Amazon EC2 Deployment GuideDocument4 paginiVoipNow Professional 2 Amazon EC2 Deployment GuideAndres Felipe Collazos RamosÎncă nu există evaluări
- How to Set Up an OpenVPN Server on MikroTik Router for Secure VPN ConnectionsDocument12 paginiHow to Set Up an OpenVPN Server on MikroTik Router for Secure VPN Connectionshhhhh123450% (1)
- Cacti Plugin ConfigurationDocument7 paginiCacti Plugin ConfigurationnarsingthakurÎncă nu există evaluări
- PF Sense Setup Open VPN: Certificate InstallationDocument7 paginiPF Sense Setup Open VPN: Certificate InstallationYosvany Ramos SánchezÎncă nu există evaluări
- Preface: Howto Set Up Certificate Based Vpns With Check Point Appliances - R80.X EditionDocument35 paginiPreface: Howto Set Up Certificate Based Vpns With Check Point Appliances - R80.X Edition000-924680Încă nu există evaluări
- Petrel 2018 & Eclipse 2015 Installation TutorialDocument24 paginiPetrel 2018 & Eclipse 2015 Installation TutorialEdinson Romero100% (1)
- Advanced FuzzingDocument73 paginiAdvanced FuzzingzoopiÎncă nu există evaluări
- SSL Connection in Managed MQ .NET (MQ v8)Document3 paginiSSL Connection in Managed MQ .NET (MQ v8)Марфутин АнтонÎncă nu există evaluări
- Wikiportecle PDFDocument11 paginiWikiportecle PDFAlvarus_XÎncă nu există evaluări
- Davidmc-Easydis Read This FirstDocument6 paginiDavidmc-Easydis Read This FirstsanistoroaeÎncă nu există evaluări
- Connect SSL Guide PDFDocument17 paginiConnect SSL Guide PDFshaahin13631363Încă nu există evaluări
- Aspen 7.1 InstallationDocument2 paginiAspen 7.1 InstallationJèfrì PìnémÎncă nu există evaluări
- Enable LDAPS On Windows IISDocument5 paginiEnable LDAPS On Windows IISFahad ShaikhÎncă nu există evaluări
- Enable Hyper ReplicationDocument41 paginiEnable Hyper Replicationsimoo2010Încă nu există evaluări
- Howto Dedicated Icecast ServerDocument20 paginiHowto Dedicated Icecast ServerAwad YunusÎncă nu există evaluări
- Install SSL certificates for Qlik NPrintingDocument2 paginiInstall SSL certificates for Qlik NPrintingManuel Gomez FredesÎncă nu există evaluări
- SOP For WFH ConfigurationDocument16 paginiSOP For WFH ConfigurationASHISH OJHAÎncă nu există evaluări
- User Guide - Fujitsu Juniper SSL Vpnv14Document11 paginiUser Guide - Fujitsu Juniper SSL Vpnv14Sergio ArtinanoÎncă nu există evaluări
- DDWRT OpenVPN Server Setup Guide v2.01Document35 paginiDDWRT OpenVPN Server Setup Guide v2.01kickflip900Încă nu există evaluări
- How To Install The Microsoft Loopback Adapter in Windows XP: Manual InstallationDocument5 paginiHow To Install The Microsoft Loopback Adapter in Windows XP: Manual InstallationramkahaniÎncă nu există evaluări
- Repackage UWP AppsDocument3 paginiRepackage UWP AppsJavadÎncă nu există evaluări
- Installation SSL Certificates and Coturn For OpenMeetings 5.0.0-M3Document10 paginiInstallation SSL Certificates and Coturn For OpenMeetings 5.0.0-M3FooÎncă nu există evaluări
- Tech Note - PAN Vwire Eval InstallDocument16 paginiTech Note - PAN Vwire Eval InstallJhonnySinatraÎncă nu există evaluări
- Creating A Thin ClientDocument8 paginiCreating A Thin ClientArthur EspanolaÎncă nu există evaluări
- Nortel 10.04.016 VPN Client User GuideDocument9 paginiNortel 10.04.016 VPN Client User GuideSreeram RobinHoodÎncă nu există evaluări
- Brad'S It Jumpbag: Wednesday, August 20, 2014Document6 paginiBrad'S It Jumpbag: Wednesday, August 20, 2014jean bonÎncă nu există evaluări
- Fortios Certificate ManagementDocument40 paginiFortios Certificate ManagementSuppat RungraungsilpÎncă nu există evaluări
- SSL Decryption Certificates TN RevCDocument7 paginiSSL Decryption Certificates TN RevCChau NguyenÎncă nu există evaluări
- How To Enable and Secure Remote Desktop On WindowsDocument13 paginiHow To Enable and Secure Remote Desktop On Windowsanak1n888Încă nu există evaluări
- Configuring CISCO ACS Server As Radius For Intel AMT 802.1x Clients With Windows DB Rev 3Document30 paginiConfiguring CISCO ACS Server As Radius For Intel AMT 802.1x Clients With Windows DB Rev 3Angel AlarasÎncă nu există evaluări
- Vpro Labs GuideDocument27 paginiVpro Labs GuiderodderixÎncă nu există evaluări
- IPredator - Setting Up OpenVPN On Windows 8 PDFDocument22 paginiIPredator - Setting Up OpenVPN On Windows 8 PDFCora BlakeÎncă nu există evaluări
- VPN & Server: User GuideDocument18 paginiVPN & Server: User GuideReshma SeeraÎncă nu există evaluări
- DeltaV Problems and Solutions - PCEDCSDocument10 paginiDeltaV Problems and Solutions - PCEDCShashempour100% (1)
- Virtual Carding Handbook 2.0 1Document16 paginiVirtual Carding Handbook 2.0 1עומר הקבבÎncă nu există evaluări
- Check Point-VPN-Installation-Guide: P.N: Installation of Checkpoint VPN Client Is One-Time Requirement OnlyDocument7 paginiCheck Point-VPN-Installation-Guide: P.N: Installation of Checkpoint VPN Client Is One-Time Requirement OnlyAyushi JaiswalÎncă nu există evaluări
- Openerp MobileDocument17 paginiOpenerp MobileLoly MarreroÎncă nu există evaluări
- OpenERP for Schools & Universities: The Education ProgramDocument9 paginiOpenERP for Schools & Universities: The Education ProgramnsgadminÎncă nu există evaluări
- Boot CDDocument16 paginiBoot CDLoly MarreroÎncă nu există evaluări
- Ejemplo Examen Ingles Oral Nivel B2Document1 paginăEjemplo Examen Ingles Oral Nivel B2igmarbarÎncă nu există evaluări
- Mobile VPN Using OPEN VPN e ZeroshellENDocument10 paginiMobile VPN Using OPEN VPN e ZeroshellENLoly MarreroÎncă nu există evaluări
- Ingles NA Examen Junio 2009Document15 paginiIngles NA Examen Junio 2009Loly MarreroÎncă nu există evaluări
- Talk Briefly (3-4 Minutes) About The Above Subject Using The Photos As A CueDocument3 paginiTalk Briefly (3-4 Minutes) About The Above Subject Using The Photos As A CueLoly MarreroÎncă nu există evaluări
- 1 1 NAT in ZeroShellDocument6 pagini1 1 NAT in ZeroShellLoly MarreroÎncă nu există evaluări
- Avanzado Ingles Comprension OralDocument3 paginiAvanzado Ingles Comprension OralsanpedropinatarÎncă nu există evaluări
- Ingles NA EOI Food SafetyDocument2 paginiIngles NA EOI Food SafetyJorge SanzÎncă nu există evaluări
- Past Paper December 07Document1 paginăPast Paper December 07Loly MarreroÎncă nu există evaluări
- WANScaler Client System Guide 070907Document54 paginiWANScaler Client System Guide 070907Elena CojocaruÎncă nu există evaluări
- Past Paper December 07Document1 paginăPast Paper December 07Loly MarreroÎncă nu există evaluări
- Ingles NA CLAVES Junio 2009Document5 paginiIngles NA CLAVES Junio 2009Loly MarreroÎncă nu există evaluări
- Changes in NAV 5 0 SP1Document84 paginiChanges in NAV 5 0 SP1psicho113Încă nu există evaluări
- EulaDocument3 paginiEulaBrandon YorkÎncă nu există evaluări
- EulaDocument3 paginiEulaBrandon YorkÎncă nu există evaluări
- Cleft SentencesDocument3 paginiCleft Sentencesradgull83% (6)
- ChangeDocument2 paginiChangeBen-x TonÎncă nu există evaluări
- Mutoh Drafstation & Drafstation Pro Service ManualDocument348 paginiMutoh Drafstation & Drafstation Pro Service Manualdynamicdesigns100% (8)
- A ZDocument12 paginiA Zjoseph_guitarista12Încă nu există evaluări
- WLAS - CSS 12 - w3Document11 paginiWLAS - CSS 12 - w3Rusty Ugay LumbresÎncă nu există evaluări
- KMS Server UpdateDocument9 paginiKMS Server UpdateAbhijeet KumarÎncă nu există evaluări
- Pro-Watch 5.0 SP1 Data Sheet Nov 5 2020Document8 paginiPro-Watch 5.0 SP1 Data Sheet Nov 5 2020carlos0217Încă nu există evaluări
- Catalog Andover ContinuumDocument80 paginiCatalog Andover ContinuumbabakcrewÎncă nu există evaluări
- Specificaton PanelDocument3 paginiSpecificaton PanelMartin HupkaÎncă nu există evaluări
- 0 0 Filtertrie IntermediateDocument33 pagini0 0 Filtertrie IntermediatealtaminÎncă nu există evaluări
- EBI System Architecture 77-2148 PDFDocument1 paginăEBI System Architecture 77-2148 PDFEric DunnÎncă nu există evaluări
- LepraDocument30 paginiLepraJuan AurichÎncă nu există evaluări
- CS5 Expire Fix - Readme - Amtlib - DLLDocument1 paginăCS5 Expire Fix - Readme - Amtlib - DLLNazeeruddin S0% (1)
- Using APIS With CHC Base and RoversDocument15 paginiUsing APIS With CHC Base and RoversbradleyÎncă nu există evaluări
- Proface GP2300-2301 PDFDocument137 paginiProface GP2300-2301 PDFAlex RaduÎncă nu există evaluări
- Fast Picture Viewer Cheat SheetDocument1 paginăFast Picture Viewer Cheat SheetmodisuryaharshaÎncă nu există evaluări
- Minibus 71 - Stup - RjecicaDocument1 paginăMinibus 71 - Stup - RjecicaededovicÎncă nu există evaluări
- What Are The F1 Through F12 KeysDocument5 paginiWhat Are The F1 Through F12 KeysAppalarajuÎncă nu există evaluări
- Chordio For LPX Installation & Quickstart Instructions: Treaybur@topmail - IeDocument2 paginiChordio For LPX Installation & Quickstart Instructions: Treaybur@topmail - IeFrank CampbellÎncă nu există evaluări
- Opos Apg110Document330 paginiOpos Apg110Daniel BojorgeÎncă nu există evaluări
- v13.0 Release NotesDocument31 paginiv13.0 Release NotespedirstuffÎncă nu există evaluări
- Diane WinDocument15 paginiDiane Winimranbseee100% (2)
- AMOS Maintenance Keeps Ships RunningDocument2 paginiAMOS Maintenance Keeps Ships Runningswapneel_kulkarniÎncă nu există evaluări
- 82-SW - CMU - Rev 1 - EN - 14 - 03 - 2014Document104 pagini82-SW - CMU - Rev 1 - EN - 14 - 03 - 2014lab copriÎncă nu există evaluări
- SINAMICS G120 PN at S7-1200 DOCU V1d4 enDocument62 paginiSINAMICS G120 PN at S7-1200 DOCU V1d4 enGiang BùiÎncă nu există evaluări
- Missing Texture Pack FilesDocument1.952 paginiMissing Texture Pack FilesDemian CorralesÎncă nu există evaluări
- OfficeServ DM User Guide - Ed - 00Document424 paginiOfficeServ DM User Guide - Ed - 00ayuntamientoigualaÎncă nu există evaluări
- 4100 Technical PresentationDocument96 pagini4100 Technical PresentationRodrigo LimaÎncă nu există evaluări
- SP55 Printer Guide C Sep 2004Document30 paginiSP55 Printer Guide C Sep 2004sausenalexÎncă nu există evaluări
- Kryon Console v5.19 User GuideDocument89 paginiKryon Console v5.19 User Guidenskprasad89Încă nu există evaluări
- Installation ConfigDocument844 paginiInstallation ConfigRosenAnastasovÎncă nu există evaluări
- Upgrading The MICREX-SX Series Programming Support Tool: To Our CustomersDocument12 paginiUpgrading The MICREX-SX Series Programming Support Tool: To Our CustomersMisael PorrasÎncă nu există evaluări