Documente Academic
Documente Profesional
Documente Cultură
CISO Perspectives On Compliance
Încărcat de
MSFTSIRTitlu original
Drepturi de autor
Formate disponibile
Partajați acest document
Partajați sau inserați document
Vi se pare util acest document?
Este necorespunzător acest conținut?
Raportați acest documentDrepturi de autor:
Formate disponibile
CISO Perspectives On Compliance
Încărcat de
MSFTSIRDrepturi de autor:
Formate disponibile
Trustworthy Computing
CISO Perspectives: Compliance in the cloud August 2013
CISO Perspectives
CISO Perspectives provides insight into some of the key questions facing information security professionals today. These articles are based on interviews and discussions with chief information security officers (CISOs) and information security and risk specialists from Microsoft and the industry. This article will discuss some of the key challenges, success factors, and potential solutions regarding compliance in the cloud.
Compliance in the cloud
The shift to cloud computing provides an organization with the ability to focus on its core value proposition and allows for far greater flexibility and capital cost reductions. This shift often changes the way that organizations operate, and presents unique challenges to information security professionals. New operating paradigms demand consideration of different risk factors and additional compliance concerns. For this article we interviewed several information security and risk specialists and surveyed approaches that work for them with regard to the shift to cloud computing. Location The inherent flexibility in cloud computing allows an organization to move data, applications, and certain operations to a cloud provider. The fact that such an organization no longer houses data and related functions in its own physical structure leads to the
CISO Perspectives Compliance in the Cloud | 1
concern that many current legal frameworks, contractual requirements, and regulatory demands are trailing technological developments in several areas. One such area focuses on national geographical boundaries, such as the EU Data Protection Directive 95/46/EC.1 Simply put, many laws demand that data shall not cross borders or be shared with other environments in a different national area. (Some laws allow data to cross borders or reside in different locations if followed by a strict pre-approval process.) The biggest impediment is clear visibility of where the data is and how it is separated from other data. Thomas Doughty, Vice President and Chief Security Officer of Prudential Financial. Telus Communications had to insist that [certain] data must remain within Canada. Kenneth Haertling, Vice President and Chief Security Officer of Telus Communication. When geographic location of data is a question, a best practice is to have an open dialogue with the cloud service provider to understand the type of data being stored, where the service provider will process and store the data, and who will have access to it. Risk assessment Another challenge is the general requirement for audit, assessment, and verification, such as the one inherent in the Payment Card Industry Data Security Standard (PCI DSS).2 This requirement generally means that much of the work around audit, assessment, and verification must be performed by each individual data-owning organization, to satisfy their own unique risk acceptance criteria and the unique regulatory environment that applies to the organization. One approach is to apply the process described in the International Organization for Standardization / International Electrotechnical Commission 27001:2005 (ISO/IEC 27001:2005) standard.3 This provides an industry accepted method to managing information security risk. As a way to help organizations recognize and mitigate cloud-specific risks, the Cloud Security Alliance (CSA) developed a controls framework called the Cloud Controls Matrix (CCM). The CCM provides organizations with a standards-based framework that incorporates cloud services. The goal of the CCM is to reduce the risk of an organization failing to consider important factors when selecting a cloud provider. It provides visibility into how participating cloud providers operate, particularly in the areas of security and compliance controls. The CSAs
EU Data Protection Directive 95/46/EC http://eurlex.europa.eu/LexUriServ/LexUriServ.do?uri=CELEX:31995L0046:EN:HTML 2 Payment Card Industry (PCI) Data Security Standard (DSS)https://www.pcisecuritystandards.org/ 3 the International Organization for Standardization / International Electrotechnical Commission 27001:2005 (ISO/IEC 27001:2005) standard http://www.iso.org/iso/catalogue_detail?csnumber=42103
2 | CISO Perspectives: Compliance in the cloud
Security, Trust & Assurance Registry (STAR)4 contains detailed responses to more than a hundred self-assessment questions that were posed to cloud service providers about cloud security controls. The purpose of STAR is to reduce much of the effort, ambiguity, and cost associated with getting the most relevant questions and information about cloud providers compliance, security, and privacy practices. Access to the registry is free, and it helps cloud customers compare services from different participating cloud providers. If you are considering using a cloud service provider, check to see whether they have submitted answers to the CSA STAR so you can learn more about their security and privacy practices and compliance-supporting controls. If the cloud provider has not submitted a self-assessment to the CSA STAR, you can use the free framework provided by the CSA to ask the cloud provider the questions that are relevant to your organization. Understanding how your cloud provider manages security and privacy to support your compliance efforts can help to minimize potential future problems. By referencing the CSAs cloud controls matrix through STAR, organizations can reduce or eliminate the cost of engaging outside expertise to select an appropriate cloud provider and rely instead on combined efforts that represent years of expertise in the field. Due diligence A key consideration for CISOs is what data to move to the cloud and what data to keep onpremises. In our conversations with CISOs we identified two key approaches for identifying and reducing risk and ensuring compliance in the cloud. The first approach is to use existing due-diligence processes, including the identification of the process owner, the data owner, and the risk elements, when deciding what to put in the cloud. Thomas Doughty adds Due diligence is a central requirement, while impetus [to move to the cloud] is decentralized. This view leads to an increased focus on monitoring and documenting the due diligence process. This increased focus is a challenge for CISOs, because the pace and frequency of due diligence processes continues to increase as organizations discover the many benefits of shifting additional workloads to the cloud. These benefits include faster provisioning, increased capacity, increased flexibility and cost savings, to name a few. In addition, many
CSAs Security, Trust & Assurance Registry (STAR) https://cloudsecurityalliance.org/star/
CSO Perspectives: Compliance in the cloud | 3
cloud consumers say that they believe the level of security they get from their cloud provider is better than that of their on-premises operations. A greater challenge exists for CISOs in industries that are highly regulated: Companies subject to tighter regulations have more to consider when they move to the cloud, says Mark Estberg, Senior Director, Global Foundation Services at Microsoft. The STAR framework, which Microsoft participates in, allows an organization to follow a well-documented process, including a check list that helps them more thoroughly document their due-diligence process. A different approach thats used by other CISOs we spoke with stems from an organizational demand for rapid provisioning times: How do you come up with the right security controls and still keep provisioning time to less than 24 hours? asks Kenneth Haertling. He suggests that there might be a need, at times, to build new, virtualized security frameworks that use new and potentially virtualized controls. After all, as John Meakin, Chief Information Security Officer, Royal Bank of Scotland, says, Security implications vary wildly across different implementation schemes. Contracts and agreements are important vehicles for clarifying security responsibility and risk assignments between organizations that use cloud services and cloud providers. The STAR registry allows cloud service providers to provide customers with visibility into their security, privacy, and compliance commitments and capabilities. Whatever the approach, all the experts we spoke with agreed that offering risk-based weighting and consideration is a better approach than treating compliance with a regulatory approach. As Kenneth Haertling succinctly put it: Is this [the risk profile] really a risk profile you can accept? For more CISO Perspectives, visit http://aka.ms/cisoperspectives
Trustworthy Computing Next 2013 Microsoft Corp. All rights reserved. This document is provided "as-is." Information and views expressed in this document, including URL and other Internet Web site references, may change without notice. You bear the risk of using it. This document does not provide you with any legal rights to any intellectual property in any Microsoft product. You may copy and use this document for your internal, reference purposes. Licensed under Creative Commons Attribution-Non Commercial-Share Alike 3.0 Unported
4 | CISO Perspectives: Compliance in the cloud
S-ar putea să vă placă și
- The Subtle Art of Not Giving a F*ck: A Counterintuitive Approach to Living a Good LifeDe la EverandThe Subtle Art of Not Giving a F*ck: A Counterintuitive Approach to Living a Good LifeEvaluare: 4 din 5 stele4/5 (5794)
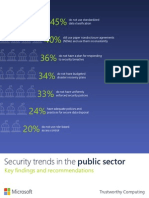
- Security Trends in The Public SectorDocument8 paginiSecurity Trends in The Public SectorMSFTSIRÎncă nu există evaluări
- The Little Book of Hygge: Danish Secrets to Happy LivingDe la EverandThe Little Book of Hygge: Danish Secrets to Happy LivingEvaluare: 3.5 din 5 stele3.5/5 (400)
- An Introduction To Designing Reliable Cloud Services January 2014Document14 paginiAn Introduction To Designing Reliable Cloud Services January 2014MSFTSIRÎncă nu există evaluări
- Shoe Dog: A Memoir by the Creator of NikeDe la EverandShoe Dog: A Memoir by the Creator of NikeEvaluare: 4.5 din 5 stele4.5/5 (537)
- Security Trends in Retail OrganizationsDocument8 paginiSecurity Trends in Retail OrganizationsMSFTSIRÎncă nu există evaluări
- Hidden Figures: The American Dream and the Untold Story of the Black Women Mathematicians Who Helped Win the Space RaceDe la EverandHidden Figures: The American Dream and the Untold Story of the Black Women Mathematicians Who Helped Win the Space RaceEvaluare: 4 din 5 stele4/5 (895)
- Microsoft Security Intelligence Report Volume 16Document152 paginiMicrosoft Security Intelligence Report Volume 16MSFTSIRÎncă nu există evaluări
- The Yellow House: A Memoir (2019 National Book Award Winner)De la EverandThe Yellow House: A Memoir (2019 National Book Award Winner)Evaluare: 4 din 5 stele4/5 (98)
- The Microsoft Approach To Compliance in The CloudDocument12 paginiThe Microsoft Approach To Compliance in The CloudMSFTSIRÎncă nu există evaluări
- The Emperor of All Maladies: A Biography of CancerDe la EverandThe Emperor of All Maladies: A Biography of CancerEvaluare: 4.5 din 5 stele4.5/5 (271)
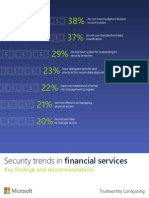
- Security Trends in Financial ServicesDocument8 paginiSecurity Trends in Financial ServicesMSFTSIRÎncă nu există evaluări
- A Heartbreaking Work Of Staggering Genius: A Memoir Based on a True StoryDe la EverandA Heartbreaking Work Of Staggering Genius: A Memoir Based on a True StoryEvaluare: 3.5 din 5 stele3.5/5 (231)
- Security Trends in HealthcareDocument8 paginiSecurity Trends in HealthcareMSFTSIRÎncă nu există evaluări
- Never Split the Difference: Negotiating As If Your Life Depended On ItDe la EverandNever Split the Difference: Negotiating As If Your Life Depended On ItEvaluare: 4.5 din 5 stele4.5/5 (838)
- Data Classification For Cloud ReadinessDocument22 paginiData Classification For Cloud ReadinessHarkirat Singh50% (2)
- Grit: The Power of Passion and PerseveranceDe la EverandGrit: The Power of Passion and PerseveranceEvaluare: 4 din 5 stele4/5 (588)
- Microsoft Security Intelligence Report Volume 15Document160 paginiMicrosoft Security Intelligence Report Volume 15MSFTSIRÎncă nu există evaluări
- On Fire: The (Burning) Case for a Green New DealDe la EverandOn Fire: The (Burning) Case for a Green New DealEvaluare: 4 din 5 stele4/5 (73)
- Microsoft Security Intelligence Report Volume 15 Key Findings SummaryDocument24 paginiMicrosoft Security Intelligence Report Volume 15 Key Findings SummaryMSFTSIRÎncă nu există evaluări
- Cybersecurity Risk ParadoxDocument12 paginiCybersecurity Risk ParadoxMSFTSIRÎncă nu există evaluări
- Elon Musk: Tesla, SpaceX, and the Quest for a Fantastic FutureDe la EverandElon Musk: Tesla, SpaceX, and the Quest for a Fantastic FutureEvaluare: 4.5 din 5 stele4.5/5 (474)
- CISO Perspectives Data ClassificationDocument5 paginiCISO Perspectives Data ClassificationMSFTSIRÎncă nu există evaluări
- Devil in the Grove: Thurgood Marshall, the Groveland Boys, and the Dawn of a New AmericaDe la EverandDevil in the Grove: Thurgood Marshall, the Groveland Boys, and the Dawn of a New AmericaEvaluare: 4.5 din 5 stele4.5/5 (266)
- AppLocker Design GuideDocument82 paginiAppLocker Design GuideMSFTSIR100% (1)
- The Unwinding: An Inner History of the New AmericaDe la EverandThe Unwinding: An Inner History of the New AmericaEvaluare: 4 din 5 stele4/5 (45)
- Five Principles For Shaping Cybersecurity NormsDocument12 paginiFive Principles For Shaping Cybersecurity NormsMSFTSIRÎncă nu există evaluări
- Trends in Cloud Computing Cloud Security Readiness ToolDocument40 paginiTrends in Cloud Computing Cloud Security Readiness ToolChristian Paul Manalo TaburadaÎncă nu există evaluări
- Team of Rivals: The Political Genius of Abraham LincolnDe la EverandTeam of Rivals: The Political Genius of Abraham LincolnEvaluare: 4.5 din 5 stele4.5/5 (234)
- Problem Management For Reliable Online Services PDFDocument16 paginiProblem Management For Reliable Online Services PDFsaad14014Încă nu există evaluări
- Microsoft Security Response Center (MSRC) Progress Report 2013Document27 paginiMicrosoft Security Response Center (MSRC) Progress Report 2013MSFTSIRÎncă nu există evaluări
- Developing A National Strategy For CybersecurityDocument24 paginiDeveloping A National Strategy For CybersecurityMSFTSIRÎncă nu există evaluări
- The World Is Flat 3.0: A Brief History of the Twenty-first CenturyDe la EverandThe World Is Flat 3.0: A Brief History of the Twenty-first CenturyEvaluare: 3.5 din 5 stele3.5/5 (2259)
- CISO Perspectives Today's RiskDocument4 paginiCISO Perspectives Today's RiskMSFTSIRÎncă nu există evaluări
- The Gifts of Imperfection: Let Go of Who You Think You're Supposed to Be and Embrace Who You AreDe la EverandThe Gifts of Imperfection: Let Go of Who You Think You're Supposed to Be and Embrace Who You AreEvaluare: 4 din 5 stele4/5 (1090)
- Resilience by Design For Cloud ServicesDocument19 paginiResilience by Design For Cloud ServicesMSFTSIRÎncă nu există evaluări
- Learn How Socio-Economic Factors Affect Regional Malware RatesDocument27 paginiLearn How Socio-Economic Factors Affect Regional Malware RatesMSFTSIRÎncă nu există evaluări
- The Hard Thing About Hard Things: Building a Business When There Are No Easy AnswersDe la EverandThe Hard Thing About Hard Things: Building a Business When There Are No Easy AnswersEvaluare: 4.5 din 5 stele4.5/5 (344)
- Whitepaper: Evaluating Microsoft's Protection Performance and Capabilities Protection Performance and CapabilitiesDocument13 paginiWhitepaper: Evaluating Microsoft's Protection Performance and Capabilities Protection Performance and CapabilitiesMSFTSIRÎncă nu există evaluări
- Microsoft Security Intelligence Report Volume 14 EnglishDocument120 paginiMicrosoft Security Intelligence Report Volume 14 EnglishMSFTSIRÎncă nu există evaluări
- Mitigating Pass-The-Hash (PTH) Attacks and Other Credential Theft Techniques - EnglishDocument82 paginiMitigating Pass-The-Hash (PTH) Attacks and Other Credential Theft Techniques - EnglishMSFTSIRÎncă nu există evaluări
- Determined Adversaries and Targeted AttacksDocument22 paginiDetermined Adversaries and Targeted AttacksMSFTSIRÎncă nu există evaluări
- Deploying Highly Available and Secure Cloud SolutionsDocument26 paginiDeploying Highly Available and Secure Cloud SolutionsMSFTSIRÎncă nu există evaluări
- Microsoft Malware Protection Center Threat Report: RootkitsDocument16 paginiMicrosoft Malware Protection Center Threat Report: RootkitsMSFTSIRÎncă nu există evaluări
- Microsoft Security Intelligence Report Volume 13 EnglishDocument146 paginiMicrosoft Security Intelligence Report Volume 13 EnglishNeagu JellyÎncă nu există evaluări
- The Sympathizer: A Novel (Pulitzer Prize for Fiction)De la EverandThe Sympathizer: A Novel (Pulitzer Prize for Fiction)Evaluare: 4.5 din 5 stele4.5/5 (121)
- MSRC Progress Report 2012Document33 paginiMSRC Progress Report 2012MSFTSIRÎncă nu există evaluări
- RA 9344 As Amended by RA 10630 - HandoutsDocument9 paginiRA 9344 As Amended by RA 10630 - HandoutsJan Re Espina CadeleñaÎncă nu există evaluări
- Amor Vs FlorentinoDocument17 paginiAmor Vs FlorentinoJessica BernardoÎncă nu există evaluări
- Southeast Asian Fabrics and AttireDocument5 paginiSoutheast Asian Fabrics and AttireShmaira Ghulam RejanoÎncă nu există evaluări
- Ministry of Truth Big Brother Watch 290123Document106 paginiMinistry of Truth Big Brother Watch 290123Valentin ChirilaÎncă nu există evaluări
- Confidential Recommendation Letter SampleDocument1 paginăConfidential Recommendation Letter SamplearcanerkÎncă nu există evaluări
- Radiopharmaceutical Production: History of Cyclotrons The Early Years at BerkeleyDocument31 paginiRadiopharmaceutical Production: History of Cyclotrons The Early Years at BerkeleyNguyễnKhươngDuyÎncă nu există evaluări
- ACT December 2018 Form B05 PDFDocument54 paginiACT December 2018 Form B05 PDFPranav ChatiÎncă nu există evaluări
- Design of Experiments: I. Overview of Design of Experiments: R. A. BaileyDocument18 paginiDesign of Experiments: I. Overview of Design of Experiments: R. A. BaileySergio Andrés Cabrera MirandaÎncă nu există evaluări
- Entrepreneur: Job/Career InvolvementDocument5 paginiEntrepreneur: Job/Career InvolvementYlaissa GeronimoÎncă nu există evaluări
- Jesus Christ Was A HinduDocument168 paginiJesus Christ Was A Hinduhbk22198783% (12)
- Her Body and Other Parties: StoriesDe la EverandHer Body and Other Parties: StoriesEvaluare: 4 din 5 stele4/5 (821)
- Donna Claire B. Cañeza: Central Bicol State University of AgricultureDocument8 paginiDonna Claire B. Cañeza: Central Bicol State University of AgricultureDanavie AbergosÎncă nu există evaluări
- 7 - LESSON PLAN CULTURAL HERITAGE AND CULTURAL DIVERSITY - Lesson PlanDocument4 pagini7 - LESSON PLAN CULTURAL HERITAGE AND CULTURAL DIVERSITY - Lesson PlanRute SobralÎncă nu există evaluări
- The Bible Does Not Condemn Premarital SexDocument16 paginiThe Bible Does Not Condemn Premarital SexKeith502100% (3)
- Middle Grades ReportDocument138 paginiMiddle Grades ReportcraignewmanÎncă nu există evaluări
- Moon and SaturnDocument4 paginiMoon and SaturnRamanasarmaÎncă nu există evaluări
- Filipino HousesDocument4 paginiFilipino HousesjackÎncă nu există evaluări
- LakmeDocument34 paginiLakmeSuraj Pratap Sawhney79% (14)
- Sale Deed Document Rajyalakshmi, 2222222Document3 paginiSale Deed Document Rajyalakshmi, 2222222Madhav Reddy100% (2)
- Grade 5 Forces Acting On Structures and Mechanisms CirriculumDocument3 paginiGrade 5 Forces Acting On Structures and Mechanisms Cirriculumapi-2072021750% (1)
- The ReformationDocument20 paginiThe ReformationIlyes FerenczÎncă nu există evaluări
- The Role of Financial System in DevelopmentDocument5 paginiThe Role of Financial System in DevelopmentCritical ThinkerÎncă nu există evaluări
- Debus Medical RenaissanceDocument3 paginiDebus Medical RenaissanceMarijaÎncă nu există evaluări
- Units 6-10 Review TestDocument20 paginiUnits 6-10 Review TestCristian Patricio Torres Rojas86% (14)
- 1999, 2003 - Purple Triangles - BrochureDocument32 pagini1999, 2003 - Purple Triangles - BrochureMaria Patinha100% (2)
- Darkness Points Reminder 2Document2 paginiDarkness Points Reminder 2Tata YoyoÎncă nu există evaluări
- Caltech RefDocument308 paginiCaltech RefSukrit ChatterjeeÎncă nu există evaluări
- Vrushalirhatwal (14 0)Document5 paginiVrushalirhatwal (14 0)GuruRakshithÎncă nu există evaluări
- Introduction To E-Business SystemsDocument19 paginiIntroduction To E-Business SystemsArtur97% (79)
- Danculos - M1 - L3 - Activity TasksDocument2 paginiDanculos - M1 - L3 - Activity TasksAUDREY DANCULOSÎncă nu există evaluări
- A Tool For The Assessment of Project Com PDFDocument9 paginiA Tool For The Assessment of Project Com PDFgskodikara2000Încă nu există evaluări