Documente Academic
Documente Profesional
Documente Cultură
Computer Network Notes
Încărcat de
Heta DesaiDescriere originală:
Drepturi de autor
Formate disponibile
Partajați acest document
Partajați sau inserați document
Vi se pare util acest document?
Este necorespunzător acest conținut?
Raportați acest documentDrepturi de autor:
Formate disponibile
Computer Network Notes
Încărcat de
Heta DesaiDrepturi de autor:
Formate disponibile
Computer Network According to Tanenbaum, computer network is a collection of autonomous computers interconnected by a single technology.
It is a collection of computers and other devices interconnected by communication channels that allow sharing of resources and information. The connection can be done as peer-to-peer or client/server. Basic Elements of a Network: Data a collection of known facts and figures that can be represented and transferred in an electronic format, e.g. text, numbers, pictures, audio, video Sender a collection of User and Hardware, e.g. a computer Receiver a collection of User and Hardware, e.g. a computer Medium the channel or path through which the data transfers, e.g. cable Protocol system of digital message formats and rules for exchanging those messages Applications of Computer Networks: Business Applications (Electronic Inventory, Information Systems, Email, Accounting/Payroll, OLTP, MIS/Reporting, Online Database, etc) Home Applications (Communication, Gaming, Ecommerce, Remote Sharing) Mobile Users (24x7 Online, GPS / Location tracking, Instant communication) Advantages and Disadvantages of Computer Networks: Advantage: Communication Sharing of files, data, and other types of information Sharing of network and computing resources Increased Storage Capacity Increased Performance Increased Cost Efficiency Increased Fault Tolerance / High Availability Disadvantage: Security Issues Threat of Computer Viruses Dependency Interference with other technologies Expensive and difficult Setup Legal and Social Issues Networks may be classified according to a wide variety of characteristics such as: Scale / Span of the network Topology the network follows, Medium used to transport the data, communications Protocol used,
organizational Scope
Types of Network according to Physical Span: Local Area Network (LAN) A LAN connects network devices over a relatively short distance. A networked office building, school, or home usually contains a single LAN, though sometimes one building will contain a few small LANs (perhaps one per room), and occasionally a LAN will span a group of nearby buildings. In TCP/IP networking, a LAN is often but not always implemented as a single IP subnet. In addition to operating in a limited space, LANs are also typically owned, controlled, and managed by a single person or organization. They also tend to use certain connectivity technologies, primarily Ethernet and Token Ring. Most local area networks are built with relatively inexpensive hardware such as Ethernet cables, network adapters, and hubs. Some of the major technologies that the LANs use are Ethernet, Token Ring, FDDI, WiFi, etc. Metropolitan Area Network (MAN) A metropolitan area network (MAN) is a computer network that usually spans a city or a large campus. A MAN usually interconnects a number of local area networks (LANs) using a high-capacity backbone technology, such as fiber-optical links, and provides up-link services to wide area networks (or WAN) and the Internet. An example of MAN can be the Cable Television broadcasting. Some technologies used for this purpose are Asynchronous Transfer Mode (ATM), FDDI, and SMDS, however, they are in the verse of being replaced by the Ethernet based MAN, also known as Metro-Ethernet. MAN can also use wireless technologies like microwave, radio, or infra-red laser links Wide Area Networks (WAN) WAN spans a large physical distance. It is a geographically-dispersed collection of LANs. A network device called a router connects LANs to a WAN. In IP networking, the router maintains both a LAN address and a WAN address. The Internet is the largest WAN, spanning the Earth. A WAN differs from a LAN in several important ways. Most WANs (like the Internet) are not owned by any one organization but rather exist under collective or distributed ownership and management. WANs tend to use technology like ATM, Frame Relay and X.25 for connectivity over the longer distances. Types of Network according to the Topology:
Physical Topology means the physical design of a network including the devices, location and cable installation. Logical Topology refers to the fact that how data actually transfers in a network as opposed to its design.
Network topology is the layout pattern of interconnections of the various elements (links, nodes, etc.) of a computer network. Network topologies may be physical or logical. Physical topology means the physical design of a network including the devices, location and cable installation. Logical topology refers to how data is actually transferred in a network as opposed to its physical design. In general, physical topology relates to a core network whereas logical topology relates to basic network. A local area network (LAN) is one example of a network that exhibits both a physical topology and a logical topology. Any given node in the LAN has one or more links to one or more nodes in the network and the mapping of these links and nodes in a graph results in a geometric shape that may be used to describe the physical topology of the network. Likewise, the mapping of the data flow between the nodes in the network
determines the logical topology of the network. The physical and logical topologies may or may not be identical in any particular network. Basic topology types: The study of network topology recognizes seven basic topologies: Point-to-point topology Bus (point-to-multipoint) topology Star topology Ring topology Tree topology Mesh topology Hybrid topology This classification is based on the interconnection between computers be it physical or logical. The physical topology of a network is determined by the capabilities of the network access devices and media, the level of control or fault tolerance desired, and the cost associated with cabling or telecommunications circuits. 1. Point-to-point The simplest topology is a permanent link between two endpoints. Switched point-to-point topologies are the basic model of conventional telephony. The value of a permanent point-to-point network is the value of guaranteed, or nearly so, communications between the two endpoints. The value of an on-demand point-topoint connection is proportional to the number of potential pairs of subscribers, and has been expressed as Metcalfe's Law. Types of Point-to-Point topology: 1.a Permanent (Dedicated) Easiest to understand, of the variations of point-to-point topology, is a point-to-point communications channel that appears, to the user, to be permanently associated with the two endpoints. A children's "tin-can telephone" is one example, with a microphone to a single public address speaker is another. These are examples of physical dedicated channels. Within many switched telecommunications systems, it is possible to establish a permanent circuit. One example might be a telephone in the lobby of a public building, which is programmed to ring only the number of a telephone dispatcher. "Nailing down" a switched connection saves the cost of running a physical circuit between the two points. The resources in such a connection can be released when no longer needed, for example, a television circuit from a parade route back to the studio. 1.b Switched Using circuit-switching or packet-switching technologies, a point-to-point circuit can be set up dynamically, and dropped when no longer needed. This is the basic mode of conventional telephony. 2. Bus topology
In local area networks where bus topology is used, each node is connected to a single cable. Each computer or server is connected to the single bus cable through some kind of connector. A terminator is required at each end of the bus cable to prevent the signal from bouncing back and forth on the bus cable. A signal from the source travels in both directions to all machines connected on the bus cable until it finds the MAC address or IP address on the network that is the intended recipient. If the machine address does not match the intended address for the data, the machine ignores the data. Alternatively, if the data does match the machine address, the data is accepted. Since the bus topology consists of only one wire, it is rather inexpensive to implement when compared to other topologies. However, the low cost of implementing the technology is offset by the high cost of managing the network. Additionally, since only one cable is utilized, it can be the single point of failure. If the network cable breaks, the entire network will be down. Types of Bus network topology: 2.a Linear bus The type of network topology in which all of the nodes of the network are connected to a common transmission medium which has exactly two endpoints (this is the 'bus', which is also commonly referred to as the backbone, or trunk) all data that is transmitted between nodes in the network is transmitted over this common transmission medium and is able to be received by all nodes in the network virtually simultaneously (disregarding propagation delays). The two endpoints of the common transmission medium are normally terminated with a device called a terminator that exhibits the characteristic impedance of the transmission medium and which dissipates or absorbs the energy that remains in the signal to prevent the signal from being reflected or propagated back onto the transmission medium in the opposite direction, which would cause interference with and degradation of the signals on the transmission medium. 2.b Distributed bus The type of network topology in which all of the nodes of the network are connected to a common transmission medium which has more than two endpoints that are created by adding branches to the main section of the transmission medium the physical distributed bus topology functions in exactly the same fashion as the physical linear bus topology (i.e., all nodes share a common transmission medium). 1.) All of the endpoints of the common transmission medium are normally terminated with a device called a 'terminator'. 2.) The physical linear bus topology is sometimes considered to be a special case of the physical distributed bus topology i.e., a distributed bus with no branching segments. 3.) The physical distributed bus topology is sometimes incorrectly referred to as a physical tree topology however, although the physical distributed bus topology resembles the physical tree topology, it differs from the physical tree topology in that there is no central node to which any other nodes are connected, since this hierarchical functionality is replaced by the common bus.
3. Star topology
In local area networks with a star topology, each network host is connected to a central hub. In contrast to the bus topology, the star topology connects each node to the hub with a point-to-point connection. All traffic that traverses the network passes through the central hub. The hub acts as a signal booster or repeater. The star topology is considered the easiest topology to design and implement. An advantage of the star topology is the simplicity of adding additional nodes. The primary disadvantage of the star topology is that the hub represents a single point of failure. A point-to-point link is sometimes categorized as a special instance of the physical star topology therefore, the simplest type of network that is based upon the physical star topology would consist of one node with a single point-to-point link to a second node, the choice of which node is the 'hub' and which node is the 'spoke' being arbitrary. After the special case of the point-to-point link, the next simplest type of network that is based upon the physical star topology would consist of one central node the 'hub' with two separate point-to-point links to two peripheral nodes the 'spokes'. Although most networks that are based upon the physical star topology are commonly implemented using a special device such as a hub or switch as the central node (i.e., the 'hub' of the star), it is also possible to implement a network that is based upon the physical star topology using a computer or even a simple common connection point as the 'hub' or central node. Star networks may also be described as either broadcast multi-access (BMA) or non-broadcast multi-access (NBMA), depending on whether the technology of the network either automatically propagates a signal at the hub to all spokes, or only addresses individual spokes with each communication. 3.a Extended star A type of network topology in which a network that is based upon the physical star topology has one or more repeaters between the central node (the 'hub' of the star) and the peripheral or 'spoke' nodes, the repeaters being used to extend the maximum transmission distance of the point-to-point links between the central node and the peripheral nodes beyond that which is supported by the transmitter power of the central node or beyond that which is supported by the standard upon which the physical layer of the physical star network is based. If the repeaters in a network that is based upon the physical extended star topology are replaced with hubs or switches, then a hybrid network topology is created that is referred to as a physical hierarchical star topology, although some texts make no distinction between the two topologies. 3.b Distributed Star A type of network topology that is composed of individual networks that are based upon the physical star topology connected together in a linear fashion i.e.; 'daisy-chained' with no central or top level connection point (e.g., two or more 'stacked' hubs, along with their associated star connected nodes or 'spokes'). 4. Ring topology
A network topology that is set up in a circular fashion in which data travels around the ring in one direction and each device on the right acts as a repeater to keep the signal strong as it travels. Each device incorporates a receiver for the incoming signal and a transmitter to send the data on to the next device in the ring. The network is dependent on the ability of the signal to travel around the ring. Types of Ring network topology: 4.a Token Ring Token ring local area network (LAN) technology is a local area network protocol which resides at the data link layer (DLL) of the OSI model. It uses a special three-byte frame called a token that travels around the ring. Token-possession grants the possessor permission to transmit on the medium. Token ring frames travel completely around the loop. 4.2 Dual Ring (failover) This structure consists of dual rings the primary for data transfer; and the secondary is for reliability and robustness. 5. Mesh topology The value of fully meshed networks is proportional to the exponent of the number of subscribers, assuming that communicating groups of any two endpoints, up to and including all the endpoints, is approximated by Reed's Law.
The number of connections in a full mesh = n(n - 1) / 2
5.a Fully connected mesh The physical fully connected mesh topology is generally too costly and complex for practical networks, although the topology is used when there are only a small number of nodes to be interconnected. 5.b Partially connected mesh The type of network topology in which some of the nodes of the network are connected to more than one other node in the network with a point-to-point link this makes it possible to take advantage of some of the redundancy that is provided by a physical fully connected mesh topology without the expense and complexity required for a connection between every node in the network.
In most practical networks that are based upon the physical partially connected mesh topology, all of the data that is transmitted between nodes in the network takes the shortest path (or an approximation of the shortest path) between nodes, except in the case of a failure or break in one of the links, in which case the data takes an alternative path to the destination. This requires that the nodes of the network possess some type of logical 'routing' algorithm to determine the correct path to use at any particular time. 6. Tree topology
Tree topology is also known as a hierarchy network.
The type of network topology in which a central 'root' node (the top level of the hierarchy) is connected to one or more other nodes that are one level lower in the hierarchy (i.e.; the second level) with a point-to-point link between each of the second level nodes and the top level central 'root' node, while each of the second level nodes that are connected to the top level central 'root' node will also have one or more other nodes that are one level lower in the hierarchy (i.e.; the third level) connected to it; also with a point-to-point link, the top level central 'root' node being the only node that has no other node above it in the hierarchy. Each node in the network having a specific fixed number of nodes connected to it at the next lower level in the hierarchy, the number; being referred to as the 'branching factor' of the hierarchical tree. This tree has individual peripheral nodes. 1.) A network that is based upon the physical hierarchical topology must have at least three levels in the hierarchy of the tree, since a network with a central 'root' node and only one hierarchical level below it would exhibit the physical topology of a star. 2.) A network that is based upon the physical hierarchical topology and with a branching factor of 1 would be classified as a physical linear topology. 3.) The branching factor, f, is independent of the total number of nodes in the network and, therefore, if the nodes in the network require ports for connection to other nodes the total number of ports per node may be kept low even though the total number of nodes is large this makes the effect of the cost of adding ports to each node totally dependent upon the branching factor and may therefore be kept as low as required without any effect upon the total number of nodes that are possible. 4.) The total number of point-to-point links in a network that is based upon the physical hierarchical topology will be one less than the total number of nodes in the network. 5.) If the nodes in a network that is based upon the physical hierarchical topology are required to perform any processing upon the data that is transmitted between nodes in the network, the nodes that are at higher levels in the hierarchy will be required to perform more processing operations on behalf of other nodes than the nodes that are lower in the hierarchy. Such a type of network topology is very useful and highly recommended.
Ethernet (802.3) Ethernet is the most widely-installed local area network (LAN) technology. Ethernet was originally developed by Xerox from an earlier specification called Alohanet and then developed further by Xerox, DEC, and Intel. An Ethernet LAN typically uses coaxial cable or special grades of twisted pair wires. Ethernet is also used in wireless. Ethernet is standardized as IEEE 802.3 that specifies a CSMA/CD bus network. CSMA/CD (Carrier Sense Multiple Access / Collision Detect) is used to detect the collision in the network. An Ethernet CSMA/CD can be implemented using a Bus or even a Star topology. Common Ethernet types:
802.3 Ethernet frame format:
Preamble: An 8 byte pattern of binary 1s and 0s used to establish synchronization. The last bit of the preamble is always 0. Start Frame Delimiter: An 8 bit pattern indicating the formal start of the frame. Destination Address: An address specifying a specific destination station, a group of stations, or all stations in the LAN. This address can be 16 bits or 48 bits in length, but all stations in the LAN must adhere to one format or the other. Source Address: The address of the originating station. This address has the same length requirements as the destination address.
Length: The length measured in bytes, of the actual data, indicating the 802.2 header. This is a 16 bit field. Following the header is the 802.2 header and the actual data. At the end of the data is the 802.3 trailer, which includes: Padding: Extra, non-data bytes can be inserted into the frame to make the overall frame length more palatable to the physical network. Frame check sequence: At the end of the frame is a 32 bit Cyclic Redundancy Check (CRC) on the data starting with the destination addresses the terminating at the end of the data (not including any padding). CSMA/CD (Carrier Sense Multiple Access / Collision Detection) CSMA/CD is the protocol used in Ethernet networks to ensure that only one network node is transmitting on the network wire at any one time. Carrier Sense means that every Ethernet device listens to the Ethernet wire before it attempts to transmit. If the Ethernet device senses that another device is transmitting, it will wait to transmit. Multiple Access means that more than one Ethernet device can be sensing (listening and waiting to transmit) at a time. Collision Detection means that when multiple Ethernet devices accidentally transmit at the same time, they are able to detect this error.
Fig: Simplified CSMA/CD algorithm Advantages of Ethernet Short access delay at low load. MAC management is relatively simple, distributed. Huge installed base and significant operational experience. Disadvantages of Ethernet Operation at high traffic load is problematic. Variable/Unbounded delay-not well suited for real-time applications.
10
Substantial analog component (collision detection). Token Bus (802.4)
Token Bus is a 4 Mbps Local Area Networking technology created by IBM to connect their terminals to IBM mainframes. It is a type of local-area network (LAN) that has a bus topology and uses a token -passing mechanism to regulate traffic on the bus. A token bus network is very similar to a token ring network; the main difference being that the endpoints of the bus do not meet to form a physical ring. Token bus networks are defined by the IEEE 802.4 standard Token bus utilized a copper coaxial cable to connect multiple end stations (terminals, workstations, shared printers etc.) to the mainframe. The coaxial cable served as a common communication bus and a token was created by the Token Bus protocol to manage or 'arbitrate' access to the bus. Any station that holds the token packet has permission to transmit data. The station releases the token when it is done communicating or when a higher priority device needs to transmit (such as the mainframe). This keeps two or more devices from transmitting information on the bus at the same time and accidentally destroying the transmitted data. Token Bus suffered from two limitations. Any failure in the bus caused all the devices beyond the failure to be unable to communicate with the rest of the network. Second, adding more stations to the bus was somewhat difficult. Any new station that was improperly attached was unlikely to be able to communicate and all devices beyond it were also affected. Thus, token bus networks were seen as somewhat unreliable and difficult to expand and upgrade. 802.4 Token Bus frame format
11
Preamble: One or more bytes used for synchronization pattern. Start Frame Delimiter: An 8 bit pattern signaling the start of the Frame. Frame Control: A 1 byte field used to indicate if the frame. Contains actual data or if it is a control message. Destination Address: An address specifying a specific destination station, a group of stations, or all stations in the LAN. This address can be 16 bits or 48 bits in length, but all stations in the LAN must adhere to one format or the other. Source Address: The address of the originating station. This address has the same length requirements as the destination address. Following this header is the 802.2 header and the actual data. At the end of the data is the 802.4 trailer, which includes the following: Frame Check Sequence: At the end of the frame is a 32 bit Cyclic Redundancy Check (CRC) on the data starting with the frame control field and terminating at the end of the data. End Delimiter: The 8 bit pattern signaling the end of the frame. The last two bits of this field signal if the frame is the last frame to be transmitted and whether any station has detected an error in the frame. Advantages of Token Bus Access delay at all traffic loads is needed. Priority-based access intra-station supports multiple type services. Decentralized MAC management is supported. Disadvantages of Token Bus Distributed MAC management requires complicated recovery procedure. Substantial analog component.
Token Ring (802.5)
Token Ring was created by IBM to compete with the DIX Standard of Ethernet (DEC/Intel/Xerox) and to improve upon their previous Token Bus technology. It is defined by the IEEE 802.5 standard. A Token Ring network is a local area network (LAN) in which all computers are connected in a ring or star topology and a bit- or token-passing scheme is used in order to prevent the collision of data between two computers that want to send messages at the same time. The Token Ring protocol is the second most widely-used protocol on local area networks after Ethernet. It uses a special three-byte frame called a token that travels around the ring. Token-possession grants the possessor permission to transmit on the medium. Token ring frames travel completely around the loop. Token
12
Ring also comes in standard 4 and 16 Mbps and high-speed Token Ring at 100 Mbps (IEEE 802.5t) and 1Gbps (IEEE 802.5v).
802.5 Token Ring frame format
Start frame delimiter: An 8 bit-pattern signaling the start of the frame. Access control: An 8 bit field used for priority and maintenance control. Most important, one bit of this field is the token bit. If set to 1, the frame contains data. If set to 0, the frame is actually a token that can be seized by a station waiting to transmit. Also note that when the token bit is set to 0, the entire frame consists only of the start frame delimiter, the access control byte and the end delimiter, the access control message. Frame control: A 1 byte field used to indicate if the frame contains actual data or a control message. Destination address: An address specifying a specific destination station, a group of stations, or all stations in the LAN. This address can be 16 bits or 48 bits in length, but all stations in the LAN must adhere to one format or the other. Source address: The address of the originating station. This address has the same length requirements as the destination address. Following this header is the 802.2 header and the actual data. At the end of the data is the 802.5 trailer that includes the following: Frame Check Sequence: At the end of the frame is 32 bit Cyclic Redundancy Check (CRC) on the data starting with the Frame Control field and terminating at the end of data. End delimiter: The 8 bit pattern signaling the end of the frame. The last two bits of this field signal if the frame is the last frame to be transmitted and whether any station has detected an error in the frame. Frame Status: An 8 bit pattern indicating whether a station has recognized the frame and also if the frame has been copied (received). Advantages of Token Ring Access delay at all traffic loads is bounded. Media independent Star topology eases network management.
13
Disadvantages of Token Ring Priority-based access may starve some stations. Centralised monitor station may be a single point of failure
FDDI (Fiber Distributed Data Interface) The Fiber Distributed Data Interface (FDDI) specifies a 100-Mbps token passing, dual ring LAN using fiberoptic cable. FDDI is frequently used as high-speed backbone technology because of its support for high bandwidth and greater distances than copper. It should be noted that relatively recently, a related copper specification, called Copper Distributed Data Interface (CDDI) has emerged to provide 100-Mbps service over copper. CDDI is the implementation of FDDI protocols over twisted pair copper wire. FDDI user dual ring architecture with traffic on each ring flowing in opposite direction (called Counter-rotating). The dual-rings consist of a primary and a secondary ring. During normal operation, the primary ring is used for data transmission, and the secondary ring remains idle. The primary purpose of the dual rings, as will be discussed in detail later in this chapter, is to provide superior reliability and robustness. The Figure shows the counterrotating primary and secondary FDDI rings.
FDDI frame format
Preamble: A unique sequence that prepares each station for an upcoming frame. Start Delimiter: Indicates the beginning of a frame by employing a signaling pattern that differentiates it from the rest of the frame. Frame Control: Indicates the size of the address field and whether the frame contains asynchronous or synchronous data, among other control information. Destination Address: Contains a unicast (singular), multicast (group), or broadcast (every station) address. As with Ethernet and token ring addresses, FDDI destination addresses are 6-bytes long. Source Address: Identifies the single station that sent the frame. As with Ethernet and Token Ring addresses FDDI source addresses are 6-bytes long. Data: Contains either information, destined for an upper-layer protocol or control information.
14
Frame Check Sequence (FCS): Filled by the source station with a calculated Cyclic Redundancy Check value dependent on frame contents (as with Token Ring and Ethernet). The destination address recalculates the values to determine whether the frame was damaged in transmit. If so, the frame is discarded. End delimiter: Contains unique symbols, which cannot be data symbols that indicate the end of the frame. Frame Status: Allows the source stations to determine whether an error occurred and whether the frame was recognized and copied by a receiving station.
X. 25
X.25 is an International Telecommunication Union-Telecommunication Standardization Sector (ITU-T)
protocol standard for WAN communications that defines how connections between user devices and network devices are established and maintained. X.25 is designed to operate effectively regardless of the type of systems connected to the network. It is typically used in the packet-switched networks (PSN) of common carriers, such as the telephone companies. Subscribers are charged based on their use of the network. X.25 network contains three general categories of devices: Data Terminal Equipment (DTE) - end systems that communicate across the X.25 network (terminals, PCs, Network hosts) Data Circuit-terminating Equipment (DCE) - communication devices that provide interface between DTE & PSE (modems, packet switches) Packet-Switching Exchange (PSE) - switches that compose the bulk of the carrier's network and transfer data from one DTE device to another through the X.25 PSN
In addition to the above components, an X. 25 network also consisted of a Packet Assembler / Dissembler (PAD), which waited for 128 bytes from the terminal before it sent off a packet, and likewise, broke the packet up at the receiver side to give the illusion of a stream. A virtual circuit is a logical connection created to ensure reliable communication between two network devices. A virtual circuit denotes the existence of a logical, bidirectional path from one DTE device to another across an X.25 network. Multiple virtual circuits (logical connections) can be multiplexed onto a single physical circuit (a physical connection). Virtual circuits are de-multiplexed at the remote end, and data is sent to the appropriate destinations.
Switched virtual circuits (SVCs) are temporary connections used for sporadic data transfers. They require that
two DTE devices establish, maintain, and terminate a session each time the devices need to communicate. Permanent virtual circuits (PVCs) are permanently established connections used for frequent and consistent
15
data transfers. PVCs do not require that sessions be established and terminated. Therefore, DTEs can begin transferring data whenever necessary because the session is always active.
Mapping of X. 25 Protocol suite to the OSI reference model Frame Relay Frame relay is a telecommunication service designed for cost-efficient data transmission for intermittent traffic between LANs and between end-points in a WAN. Frame relay puts data in a variable-size unit called a frame and leaves any necessary error correction (retransmission of data) up to the end-points, which speeds up overall data transmission. The network provides a Virtual Circuit (VC), which means that the customer sees a continuous, dedicated connection without having to pay for a full-time leased line; while the service provider figures out the route each frame travels to its destination and can charge based on usage. The Frame Relay frame is transmitted to its destination by way of virtual circuits (logical paths from an originating point in the network) to a destination point. Virtual circuits may be permanent (PVCs) or switched (SVCs). PVCs are set up administratively by the network manager for a dedicated point-to-point connection; SVCs are set up on a call-by-call basis. Advantages of Frame Relay Frame Relay offers an attractive alternative to both dedicated lines and X.25 networks for connecting LANs to bridges and routers. The success of the Frame Relay protocol is based on the following two underlying factors: Because virtual circuits consume bandwidth only when they transport data, many virtual circuits can exist simultaneously across a given transmission line. In addition, each device can use more of the bandwidth as necessary, and thus operate at higher speeds. The improved reliability of communication lines and increased error-handling sophistication at end stations allows the Frame Relay protocol to discard erroneous frames and thus eliminate timeconsuming error-handling processing.
Frame Relay Header structure
16
Frame Relay versus X.25 X.25 provides quality of service and error-free delivery, whereas, Frame Relay was designed to relay data as quickly as possible over low error networks X.25 prepares and sends packets, while Frame Relay prepares and sends frames. X.25 packets contain several fields used for error checking and flow control, most of which are not used by Frame Relay. The frames in Frame Relay contain an expanded link layer address field that enables Frame Relay nodes to direct frames to their destinations with minimal processing. The elimination of functions and fields over X.25 allows Frame Relay to move data more quickly, but leaves more room for errors and larger delays should data need to be retransmitted. X.25 packet switched networks typically allocated a fixed bandwidth through the network for each X.25 access, regardless of the current load. Frame Relay networks; on the other hand, can dynamically allocate bandwidth at both the physical and logical channel level. Switched Multi-megabit Data Service (SMDS) Switched Multi-megabit Data Service (SMDS) is defined as a high speed packet switching data service. It is a high-speed, connectionless, public data service that extends Local Area Network, Metropolitan or Wide Area Networks. SMDS uses fiber or copper-based media for data transmission. SMDS data units encapsulate entire IEEE 802.3, IEEE 802.5 and Fiber Distributed Data Interface (FDDI) frames. SMDS provides data service features which include: High-speed, low-delay & connectionless data transport: For data transmission there is no call set up required and packets are sent out immediately when they receive it. Multicasting: SMDS handles group addressing. CCITT E.164 addressing: Standard telephone numbers are used for SMDS address. It supports for important protocols used in LAN & WAN. It provides Network scalability and SNMP based network management It validates source/destination address for the secure interconnection of LANs and distributed clientserver applications SMDS Network Components: customer premises equipment (CPE) carrier equipment subscriber network interface (SNI) For communications between CPE and SMDS carrier equipment the SMDS Interface Protocol (SIP) is used. SIP offers connectionless service over the subscriber network interface (SNI) and allows the CPE to access the SMDS network. SIP is based on the Distributed Queue Dual Bus IEEE 802.6 standard across metropolitan-area networks. DQDB supports SIP because it is an open standard for all the SMDS features. In addition, DQDB designed for compatibility with current carrier transmission standards and it is aligned with emerging standards for Broadband ISDN, which interoperates with broadband video and voice services. ISDN (Integrated Services Digital Network) Integrated Services Digital Network (ISDN) is a set of communications standards for simultaneous digital transmission of voice, video, data, and other network services over the traditional circuits of the public
17
switched telephone network (PSTN). It offers circuit-switched connections for voice and data; or packetswitched connections for data; and can support data transfer rates up to 64 Kbps. Major applications of ISDN include: Internet access Telecommuting/remote access to corporate computing Video conferencing Small and home office data networking There are 2 levels of ISDN services: BRI (Basic Rate Interface) The BRI consists of two 64 Kbps B-channels and one 16 Kbps D- channel. Thus, a BRI can have up to 128 Kbps service. PRI (Primary Rate Interface) The PRI consists of 23 B-channels and one 64 Kpbs D-channel in the United States /or 30 B-channels and 1 D-channel in Europe.
The Bearer channel (B) is a standard 64 kbit/s voice channel that can also be used to carry data. Some Bchannels are limited to 56 kbps. The Delta channels (D) carry control and signaling information Narrowband & Broadband ISDN The Narrowband ISDN (N-ISDN) is based on the use of a 64 kbps channel as the basic unit of switching and has a circuit switching orientation. It carries voice information in a narrow band of frequencies. The major technical contribution of the narrowband ISDN effort has been the Frame Relay. The Broadband ISDN (B-ISDN), on the other hand, supports very high data rates (100s of Mbps) and has a packet switching orientation. Broadband refers to telecommunication in which a wide band of frequencies is available to transmit information. Because a wide band of frequencies is available, information can be multiplexed and sent on many different frequencies or channels within the band concurrently, allowing more information to be transmitted in a given amount of time. The major technical contribution of the B-ISDN effort has been asynchronous transfer mode, also known as cell relay Asynchronous Transfer Mode (ATM) Asynchronous Transfer Mode (ATM) is a standard switching technique designed to unify telecommunication and computer networks. It uses asynchronous time-division multiplexing, and it encodes data into small, fixedsized cells. It was designed for a network that must handle both traditional high-throughput data traffic (e.g., file transfers), and real-time, low-latency content such as voice and video. ATM uses a connection-oriented model in which a virtual circuit must be established between two endpoints before the actual data exchange begins. Asynchronous Transfer Mode (ATM) is a high speed Link Layer (Layer 2) network protocol. ATM can be used to provide access to the physical layer, such as ADSL, for higher layer protocols such as PPP and TCP/IP. ATM is one of the key technologies for enabling broadband on ADSL, and is well suited to such purposes as real-time voice and video. Major characteristics of ATM No Master Clock
18
Virtual Circuits Cell based Cell Switching Embraced by the highly available telephone network Connection oriented Fixed size cells 53 bytes (5 bytes header / 48 bytes payload) Handles both constant and variable rate traffic Bit-by-bit error checking and correction ATM Cell format GFC 4 bit GFC VPI VCI VCI Type CLP HEC (CRC-8) 8 16 3 1 8 (Generic Flow Control) (Virtual Path ID) (Virtual Circuit ID) VPI + VCI together identify a Virtual Circuit uniquely Type 1st bit: management/user data 2nd bit: EFCI (Explicit Forward Congestion Indication) 3rd bit: segmenting and reassembling CLP (Cell Loss Priority) HEC (CRC) Header Error Control (Cyclic Redundancy Check) VPI Payload 48 bytes
The ATM Protocol Reference Model
The Physical Layer The lowest layer in the ATM protocol is the Physical layer. This layer describes the physical transmission of information through an ATM network. It is not actually defined with respect to this new technology. The absence of a Physical layer definition results from the design goal of ATM to operate on various physical interfaces or media types. Thus, instead of defining a specific Physical layer, ATM depends on the Physical layers defined in other networking protocols. Types of physical media specified for ATM include shielded and unshielded twisted-pair, coaxial cable, and fiber-optic cable, which provide cell transport capabilities ranging from a T1 rate of 1.544Mbps to a SONET range of 622Mbps. The ATM Layer The ATM layer represents the physical interface between the ATM Adaptation Layer (AAL) and the Physical layer. Thus, the ATM layer is responsible for relaying cells from the AAL to the Physical layer for transmission, and in the opposite direction from the Physical layer to the AAL for use in an endpoint. When transporting cells to the Physical layer, the ATM layer is responsible for generating the five-byte cell header for each cell.
19
When receiving cells from the Physical layer, the ATM layer performs a reverse operation, extracting the fivebyte header from each cell. The actual manner by which the ATM layer performs its relaying function depends on the location of the layer at a switch or at an endpoint. If the ATM layer is located in an endpoint, it receives a stream of cells from the Physical layer and transmits either cells with new data or empty cells if there is no data to send to the AAL. When located in a switch, the ATM layer is responsible for determining where incoming cells are routed and for multiplexing cells by placing cells from individual connections into a single-cell stream. The ATM Adaptation Layer The ATM Adaptation layer (AAL) represents the top layer in the ATM Protocol model. This layer is responsible for providing an interface between higher-layer protocols and the ATM layer. Because this interface normally occurs based on a voice, data, or video application accessing an ATM network, the operations performed by the AAL occur at endpoints and not at ATM switches. Thus, the AAL is to reside at ATM endpoints. The primary function of the ATM Adaptation layer is format conversion. That is, the AAL maps the data stream originated by the higher-layer protocol into the 48-byte payload of ATM cells, with the header placement being assigned by the ATM layer. In the reverse direction, the AAL receives the payload of ATM cells in 48byte increments from the ATM layer and maps those increments into the format recognized by the higherlayer protocol. Advantage of ATM over Ethernet / Token-Ring / FDDI ATM helps obtaining full bandwidth access to ATM switches for individual workstations and enabling attaching devices to operate at different operating rates The selection of a 53-byte cell length results in a minimum of latency in comparison to the packet length of traditional LANs Ethernet Cabling T-568A Straight-through
T-568B Straight-through
20
Crossover Ethernet Cable
Basic Theory
IP Address Classification Range of 1st Octet (Decimal) 0 127 128 191 192 223 224 239 Range of 1st Octet (Binary) 00000000 01111111 10000000 10111111 11000000 11011111 11100000 11101111 No. of Valid Networks 27 2 = 126 2(6+8) = 16,384 2(5+8+8) = 2,09,7152 No. of Valid Hosts per network 224 2 = 16,777,214 216 2 = 65,534 28 2 = 254
IP Class A B C D
Leading Bits 0 10 110 1110
Network ID W W.X W.X.Y
Host ID X.Y.Z Y.Z Z
21
1111
240 255
11110000 11111111
22
S-ar putea să vă placă și
- Physical LayerDocument20 paginiPhysical LayerVitthal KodgirwarÎncă nu există evaluări
- Operating SystemDocument74 paginiOperating Systemsunnysaini090Încă nu există evaluări
- Motherboard and Its ComponentsDocument5 paginiMotherboard and Its ComponentsVenky MudavathÎncă nu există evaluări
- IP HeaderDocument3 paginiIP HeaderAshis KumarÎncă nu există evaluări
- IctdipNetworking NotesDocument86 paginiIctdipNetworking NotesJoshua Kioko100% (1)
- Module 4-Motherboard.18214342Document59 paginiModule 4-Motherboard.18214342Fercie Q. EngresoÎncă nu există evaluări
- RTOS Based Embedded System DesignDocument16 paginiRTOS Based Embedded System DesignSagar DhapkeÎncă nu există evaluări
- Simple Important Computer AbbreviationsDocument2 paginiSimple Important Computer AbbreviationsSvb CharyÎncă nu există evaluări
- Message Queues, Mailboxes, and Pipes - RTOSDocument4 paginiMessage Queues, Mailboxes, and Pipes - RTOSDeepak Reddy100% (2)
- DBMS Tutorial PDFDocument66 paginiDBMS Tutorial PDFSwathiÎncă nu există evaluări
- 3 GSM Traffic ManagementDocument58 pagini3 GSM Traffic ManagementEldine100% (1)
- Arm9 Embedded Book-GuideDocument67 paginiArm9 Embedded Book-GuideNguyễn Trường ĐứcÎncă nu există evaluări
- Interview QuestionsDocument15 paginiInterview QuestionssaurabhÎncă nu există evaluări
- Drive Test PDFDocument3 paginiDrive Test PDFRaymond Katungi100% (1)
- NetworkingDocument12 paginiNetworkingCharanjit Singh Saini0% (1)
- Unit 2 8086 System Bus Structures FullunitDocument36 paginiUnit 2 8086 System Bus Structures Fullunitlauro eugin brittoÎncă nu există evaluări
- IP AddressingDocument38 paginiIP AddressingSara ElkadyÎncă nu există evaluări
- Term Paper On Embedded SystemDocument11 paginiTerm Paper On Embedded Systemsupreetsingh1960% (1)
- Computer Networks Lecture NotesDocument50 paginiComputer Networks Lecture NotesRam Kumar0% (1)
- Serial Port InterfacingDocument5 paginiSerial Port Interfacingyampire100% (1)
- RF Drive Test Over ViewsDocument11 paginiRF Drive Test Over ViewsMustafa Bin AmarÎncă nu există evaluări
- 8257 DMA Controller:: To Fetch The Instruction To Decode The Instruction and To Execute The InstructionDocument25 pagini8257 DMA Controller:: To Fetch The Instruction To Decode The Instruction and To Execute The Instructionsatyanarayana12Încă nu există evaluări
- Failure ClassificationDocument2 paginiFailure ClassificationJoker 2610Încă nu există evaluări
- CoCubes Exam QuesDocument4 paginiCoCubes Exam QuesRavi Karthik100% (1)
- TCP in Wireless DomainDocument30 paginiTCP in Wireless DomainMurugan Antham RÎncă nu există evaluări
- Cross-Layer Resource Allocation in Wireless Communications: Techniques and Models from PHY and MAC Layer InteractionDe la EverandCross-Layer Resource Allocation in Wireless Communications: Techniques and Models from PHY and MAC Layer InteractionÎncă nu există evaluări
- Chapter5-The Memory SystemDocument78 paginiChapter5-The Memory SystemAvirup RayÎncă nu există evaluări
- Network and Internet-Computer Fundamentals-Lecture Notes PDFDocument12 paginiNetwork and Internet-Computer Fundamentals-Lecture Notes PDFKomal Singh67% (3)
- Lan, Wan, ManDocument20 paginiLan, Wan, ManCatherine JoyÎncă nu există evaluări
- Database System NotesDocument83 paginiDatabase System NotesHamid Haleem100% (3)
- WT Final Notes 2015Document164 paginiWT Final Notes 2015Nilesh PatilÎncă nu există evaluări
- Ec 407 Computer Communication: Pg. 1 Department of EceDocument25 paginiEc 407 Computer Communication: Pg. 1 Department of EceNandu V SÎncă nu există evaluări
- Fundamentals of InternetDocument31 paginiFundamentals of InternetYogendra Singh ChaharÎncă nu există evaluări
- Aim: To Understand The Cellular Frequency Reuse ConceptDocument9 paginiAim: To Understand The Cellular Frequency Reuse ConceptRajÎncă nu există evaluări
- Unit IDocument53 paginiUnit INameis GirishÎncă nu există evaluări
- Lecture 2 - ARM Instruction SetDocument42 paginiLecture 2 - ARM Instruction SetSuhaib AbugderaÎncă nu există evaluări
- OSI Reference ModelDocument45 paginiOSI Reference ModelBong SemanaÎncă nu există evaluări
- Computer Network ModelDocument14 paginiComputer Network ModelDan TamiruÎncă nu există evaluări
- 03-MAC Address PDFDocument12 pagini03-MAC Address PDFsuresh1776job80% (5)
- Introduction To Embedded SystemsDocument14 paginiIntroduction To Embedded SystemsrajeshÎncă nu există evaluări
- 8237 Dma ControllerDocument14 pagini8237 Dma ControllerSAIF ULLAH100% (1)
- TCP Ip QuestionsDocument3 paginiTCP Ip QuestionsTremo EnaÎncă nu există evaluări
- Introduction To NetworkingDocument72 paginiIntroduction To NetworkingHimanshu GuptaÎncă nu există evaluări
- Dynamic Random Access MemoryDocument20 paginiDynamic Random Access MemoryNahum QuirosÎncă nu există evaluări
- The Fork Join Framework in Java7Document6 paginiThe Fork Join Framework in Java7Nguyen Duc ToanÎncă nu există evaluări
- Unit 6 Memory OrganizationDocument24 paginiUnit 6 Memory OrganizationAnurag GoelÎncă nu există evaluări
- Books 9Document30 paginiBooks 9arjun singhÎncă nu există evaluări
- TDMA - Time Division Multiple AccessDocument13 paginiTDMA - Time Division Multiple AccessBejetaÎncă nu există evaluări
- Computer Networks NotesDocument420 paginiComputer Networks Notesbobsgally100% (1)
- TMS320F28335 DSP Development BoardDocument6 paginiTMS320F28335 DSP Development BoardDeepika SharmaÎncă nu există evaluări
- Carrier Sense Multiple Access With Collision Detection (CSMA/CD)Document7 paginiCarrier Sense Multiple Access With Collision Detection (CSMA/CD)Juicy69MannÎncă nu există evaluări
- GSM Interview Questions and AnswersDocument11 paginiGSM Interview Questions and AnswersadnangulzarÎncă nu există evaluări
- Android ArchitectureDocument106 paginiAndroid ArchitectureAsad Butt100% (1)
- Computer Networks Assignment QuestionsDocument8 paginiComputer Networks Assignment Questionsmayank27jaitly100% (1)
- Lte Netnumen InstallationDocument75 paginiLte Netnumen InstallationnazilaÎncă nu există evaluări
- 3-Chapter - 10 - RTOS - Task CommunicationDocument9 pagini3-Chapter - 10 - RTOS - Task CommunicationBhuvana GowdaÎncă nu există evaluări
- Os Notes PDFDocument115 paginiOs Notes PDFVishnu PalÎncă nu există evaluări
- DBMS Unit 4Document19 paginiDBMS Unit 4RajeshkumarSinghÎncă nu există evaluări
- Telecomms ConceptsDocument111 paginiTelecomms ConceptsKAFEEL AHMED KHANÎncă nu există evaluări
- TCP - IP Model - Intro NotesDocument3 paginiTCP - IP Model - Intro NotesAnonymous OsssbjÎncă nu există evaluări
- Electronic CommerceDocument87 paginiElectronic CommerceHeta DesaiÎncă nu există evaluări
- Unit 3Document55 paginiUnit 3Heta DesaiÎncă nu există evaluări
- Practical Assignment For DBMSDocument2 paginiPractical Assignment For DBMSHeta Desai100% (2)
- Addressing Modes: Heta J Desai SDJDocument10 paginiAddressing Modes: Heta J Desai SDJHeta DesaiÎncă nu există evaluări
- Network Router: Determine The Best Path For Sending DataDocument4 paginiNetwork Router: Determine The Best Path For Sending DataHeta DesaiÎncă nu există evaluări
- Hardware Equipments HubDocument2 paginiHardware Equipments HubHeta DesaiÎncă nu există evaluări
- The Stages of Problem-Solving Notes: SYBCA - Heta DesaiDocument8 paginiThe Stages of Problem-Solving Notes: SYBCA - Heta DesaiHeta DesaiÎncă nu există evaluări
- Gateways in NetworkingDocument2 paginiGateways in NetworkingHeta DesaiÎncă nu există evaluări
- Enterprise Resource PlanningDocument4 paginiEnterprise Resource PlanningHeta DesaiÎncă nu există evaluări
- IP Address - What Is IP Address?: ComputerDocument56 paginiIP Address - What Is IP Address?: ComputerHeta DesaiÎncă nu există evaluări
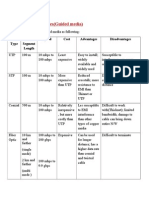
- Comparing Media Types (Guided Media) : Media Type Max. Segment Length Speed Cost Advantages DisadvantagesDocument1 paginăComparing Media Types (Guided Media) : Media Type Max. Segment Length Speed Cost Advantages DisadvantagesHeta DesaiÎncă nu există evaluări
- Network Bridges: What Is The Use of BridgeDocument2 paginiNetwork Bridges: What Is The Use of BridgeHeta DesaiÎncă nu există evaluări
- E CommerceDocument48 paginiE CommerceHeta DesaiÎncă nu există evaluări
- Is Called A Protocol.: Protocol Is A Standard Procedure and Format That Two Data Communication DevicesDocument7 paginiIs Called A Protocol.: Protocol Is A Standard Procedure and Format That Two Data Communication DevicesHeta DesaiÎncă nu există evaluări
- For Sybca - Heta Desai: Student Notes On Information SystemDocument56 paginiFor Sybca - Heta Desai: Student Notes On Information SystemHeta DesaiÎncă nu există evaluări
- IP Address - What Is IP Address?: ComputerDocument56 paginiIP Address - What Is IP Address?: ComputerHeta DesaiÎncă nu există evaluări
- Networking TechnologiesDocument16 paginiNetworking TechnologiesHeta DesaiÎncă nu există evaluări
- Chap 05 Network LayerDocument104 paginiChap 05 Network LayerPallawi PriyamwadaÎncă nu există evaluări
- T Rec Q.921 199303 S!!PDF eDocument172 paginiT Rec Q.921 199303 S!!PDF eEdgar Marlon Santos FernandezÎncă nu există evaluări
- Brkcrs-3035 - Vss - AdvancedDocument93 paginiBrkcrs-3035 - Vss - AdvancedEdon BlakajÎncă nu există evaluări
- Lab 2 Iperf CommandDocument5 paginiLab 2 Iperf CommandEvelina DumitrescuÎncă nu există evaluări
- Aviatrix ACE by PaingpeaceDocument43 paginiAviatrix ACE by PaingpeaceBalan Wv100% (4)
- OS6350 AOS 6.7.2 R07 CLI Reference Guide PDFDocument2.974 paginiOS6350 AOS 6.7.2 R07 CLI Reference Guide PDFstillÎncă nu există evaluări
- Cisco Basic SecurityDocument58 paginiCisco Basic SecurityPhuong PhamÎncă nu există evaluări
- 21CS62 Tie SimpDocument4 pagini21CS62 Tie Simpvtuhub2021Încă nu există evaluări
- VoIP ProtocolsDocument1 paginăVoIP ProtocolsSk NaveedÎncă nu există evaluări
- Unps Lab Manual PDFDocument23 paginiUnps Lab Manual PDFshubhÎncă nu există evaluări
- 1.1.1.2 Packet Tracer - Test Connectivity With TracerouteDocument4 pagini1.1.1.2 Packet Tracer - Test Connectivity With TraceroutePaulo StevenÎncă nu există evaluări
- Ch.6-Routing Theory and Dynamic Routing Operations-2 PDFDocument38 paginiCh.6-Routing Theory and Dynamic Routing Operations-2 PDFArad RezaÎncă nu există evaluări
- Ping and TracerouteDocument10 paginiPing and TraceroutejayÎncă nu există evaluări
- DMZ - Best Practices - VSDDocument5 paginiDMZ - Best Practices - VSDKashif Aziz Awan100% (1)
- InRouter305 - PRDT Spec - V1.0 April 2021 - InHand NetworksDocument4 paginiInRouter305 - PRDT Spec - V1.0 April 2021 - InHand NetworksPiterÎncă nu există evaluări
- PDFDocument3 paginiPDFRohit Kumar DasÎncă nu există evaluări
- Red Hat Enterprise Linux-9-Configuring and Managing Networking-En-usDocument357 paginiRed Hat Enterprise Linux-9-Configuring and Managing Networking-En-us6342434Încă nu există evaluări
- Windows IP Commands - Ipconfig-Nslookup-Ping-Tracert EtcDocument9 paginiWindows IP Commands - Ipconfig-Nslookup-Ping-Tracert EtcMosesÎncă nu există evaluări
- Cisco Unity Messaging Integration: Cisco Unity and Cisco Unity Connection Configuration ChecklistDocument6 paginiCisco Unity Messaging Integration: Cisco Unity and Cisco Unity Connection Configuration ChecklistRa YuthÎncă nu există evaluări
- Edennington - Wordpress - Com - 2014 - 11 - 05 - Find The Port A Host Is Connected To in A Fabricpath Fabric - AmpDocument6 paginiEdennington - Wordpress - Com - 2014 - 11 - 05 - Find The Port A Host Is Connected To in A Fabricpath Fabric - AmpAditya NandwaniÎncă nu există evaluări
- Utopion Simplex ProtocolDocument16 paginiUtopion Simplex Protocolhema channaboinaÎncă nu există evaluări
- Insys MRO-L200 4G Router Quick Installation GuideDocument5 paginiInsys MRO-L200 4G Router Quick Installation GuideTimang LhangÎncă nu există evaluări
- Chapter 7 Lab 7-1, Synchronizing Campus Network Devices Using Network Time Protocol (NTP)Document15 paginiChapter 7 Lab 7-1, Synchronizing Campus Network Devices Using Network Time Protocol (NTP)diego rubioÎncă nu există evaluări
- LT 4100 Accredited Solution OnSatMail Rev. 1.00Document1 paginăLT 4100 Accredited Solution OnSatMail Rev. 1.00ahmedÎncă nu există evaluări
- بكالوريوس - تخصص دعم انظمة شبكات الحاسبDocument57 paginiبكالوريوس - تخصص دعم انظمة شبكات الحاسبSULTAN SksaÎncă nu există evaluări
- Encapsulation and Framing Efficiency of DVB-S2 SatDocument13 paginiEncapsulation and Framing Efficiency of DVB-S2 SatkakaÎncă nu există evaluări
- EN Datasheet TEG-25GECTX (v1.0R)Document3 paginiEN Datasheet TEG-25GECTX (v1.0R)JerryÎncă nu există evaluări
- Is It Possible To Limit How Many Clients Are Able To Connect To An AccessDocument15 paginiIs It Possible To Limit How Many Clients Are Able To Connect To An Accessatik rahmanÎncă nu există evaluări
- Physical Layer-SwitchingDocument42 paginiPhysical Layer-SwitchingPalashAhujaÎncă nu există evaluări
- Xgs3700 Stack STP LACPDocument9 paginiXgs3700 Stack STP LACPCuong TranÎncă nu există evaluări