Documente Academic
Documente Profesional
Documente Cultură
Security Trends in Healthcare
Încărcat de
MSFTSIRDrepturi de autor
Formate disponibile
Partajați acest document
Partajați sau inserați document
Vi se pare util acest document?
Este necorespunzător acest conținut?
Raportați acest documentDrepturi de autor:
Formate disponibile
Security Trends in Healthcare
Încărcat de
MSFTSIRDrepturi de autor:
Formate disponibile
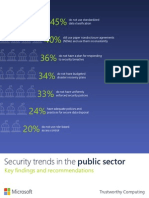
do not use standardized data
classification
39%
have a disaster
recovery program
31%
do not have asset management policies
and conduct asset discovery manually
28%
have ineffective controls for removing or changing
access when employees leave or are reassigned
25%
have immature
security policies
23%
cannot prevent a power outage
from affecting their organization
23%
conduct system-wide data backups
that are tested regularly
51%
Security trends in healthcare
Key findings and recommendations
Trustworthy Computing
This document is for informational purposes only. MICROSOFT MAKES NO
WARRANTIES, EXPRESS, IMPLIED, OR STATUTORY, AS TO THE INFORMATION IN THIS
DOCUMENT.
This document is provided as-is. Information and views expressed in this document,
including URL and other Internet website references, may change without notice. You
bear the risk of using it.
Microsoft is a registered trademark or trademark of Microsoft Corporation in the United
States and/or other countries.
Copyright 2014 Microsoft Corporation. All rights reserved.
2 SECURITY TRENDS
Security trends in
healthcare
The worldwide need for quick access to meaningful medical information is an increasing
challenge for healthcare organizations. Almost 50% of hospitals and 40% of ambulatory
practices are implementing self-service portals,
1
and a 75% increase in medical cybercrime over
the course of two years
2
has increased concerns about securitybecause more self-service
capabilities may increase opportunities for criminals to find new ways of stealing sensitive
medical information through drive-by download and phishing attacks.
Cloud computing can help improve the security profiles of healthcare organizations by shifting
to cloud service providers (CSPs) the burden of assuring safe, secure computing practices. CSPs
strive to maintain secure operations and will work with healthcare providers to help minimize
security threats. In addition, CSPs that work with electronic health records (EHRs) must abide by
stringent regulations, such as the Health Insurance Portability and Accountability Act (HIPAA) in
the US, to ensure data is securely maintained. In short, cloud-based solutions could address the
needs of medical practitioners while reducing or mitigating risk.
Although the cloud offers considerable benefits, organizations that adopt cloud-based solutions
can also benefit from having an understanding of the relative maturity of their own security
practices. The security trends that are identified in this report result from anonymized data that
was collected from 12,000 respondents to a survey that was conducted during the period of
November 2012 to February 2014. The trends are representative of a worldwide sample.
For more information, including worldwide results and tables from which the findings were
created, see www.microsoft.com/trustedcloud.
1
Terry, K. (2013, 12 23). 5 Trends For Health CIOs In 2014 -
www.informationweek.com/healthcare/mobile-and-wireless/5-trends-for-health-cios-in-2014/d/d-id/1113133
2
D., Gary R. Gordon Ed (2013, 07). The Growing Threat of Medical Identity Fraud: A Call to Action (PDF) -
http://medidfraud.org/wp-content/uploads/2013/07/MIFA-Growing-Threat-07232013.pdf
APRIL 2014 3
Key Findings
of surveyed healthcare organizations have immature security
policies
This condition may result in major breaches of regulatory requirements and may hinder an
organizations ability to enforce procedures.
34% of all industries surveyed worldwide do not have effective security policies, which suggests
that healthcare organizations (at 23%) are more mature in this regard.
Recommendation
Healthcare organizations should have centrally managed information security policies that
conform to industry best practices with regard to security, privacy, and risk management.
CSPs will typically implement such policies and will help ensure that they are integrated with
asset management, physical security, and access control policies. Regular audits help ensure
effectiveness and compliance.
of surveyed healthcare organizations have ineffective controls
for removing or changing access when employees leave or are
reassigned
Without management accountability, terminated or reassigned employees can maintain
unauthorized access.
31% of all industries surveyed worldwide have ineffective controls for changing access when
employees leave or are reassigned, which suggests that healthcare organizations (at 26%) are
more mature in this regard.
In addition, 26% of healthcare organizations do not centrally manage, log, and audit physical
access to facilities. Even with role-based key cards, without logging and auditing access,
healthcare organizations may risk unauthorized entry into sensitive areas.
The human factor is one of the most important contributors to the success of an information
security plan, but also presents one of the biggest risks. Malicious or disgruntled personnel with
access to important information assets can be a significant threat to the safety and security of
those assets. Even people without malicious intent can pose a danger if they don't clearly
understand their information security responsibilities.
23%
26%
4 SECURITY TRENDS
Recommendation
Restrict access by role and also by need to know. Limit the number of people who can grant
authorizations to a relatively small set of trusted staff members, and track authorizations using a
ticketing/access system. Review and regularly update a list of authorized personnel.
Major CSPs typically conduct regular pre-hire and post-hire background checks on their
employees.
of surveyed healthcare organizations do not use standardized
data classification
Some organizations have policies for personally identifiable information (PII) but lack
procedures or standard terminology that adequately protect patient information while allowing
providers the ability to get their jobs done.
42% of all industries surveyed worldwide do not use standardized data classification, which
suggests that healthcare organizations (at 39%) are more mature in this regard.
Data classification, which involves associating each data asset with a standard set of attributes,
can help an organization identify which assets require special handling to provide security and
privacy protection.
Recommendation
Organizations need to ensure that data stores that contain confidential data are classified as
sensitive assets that require an elevated level of security.
CSPs typically classify data and other assets according to well-defined policies, which dictate a
standard set of security and privacy attributes among others.
of surveyed healthcare organizations conduct system-wide
data backups that are tested regularly
Also, almost 27% of healthcare organizations expect individuals to be responsible for ensuring
the correct means of disposal of sensitive data.
49% of all industries surveyed worldwide conduct system-wide data backups that are tested
regularly, which suggests that healthcare organizations (at 52%) are more mature in this regard.
A data backup and recovery plan defines the approach an organization takes to back up and to
recover data in case of need.
39%
52%
APRIL 2014 5
Recommendation
Organizations should have a data backup and recovery plan that assigns clear responsibilities to
specific personnel and defines objectives for backup and recovery. Also, strong policies that
govern the proper disposal of electronic and paper records help prevent sensitive data from
unauthorized disclosure. An effective data disposal policy provides guidance on how and where
to dispose of data safely and securely, and provides users with the necessary tools for complying
with the policy.
CSPs typically maintain a data backup and recovery framework that is consistent with industry
practices. In addition, electronic data stored by CSPs is typically subject to strong data disposal
policies that are derived from data classification programs and that require disposed media to
be destroyed or sanitized as outlined by a data retention and recovery program.
of surveyed healthcare organizations do not have asset
management policies and conduct asset discovery manually
34% of all industries surveyed worldwide do not have effective asset management policies,
which suggests that healthcare organizations (at 28%) are more mature in this regard.
In addition, only 42% of healthcare organizations self-identified themselves as mature in their
use of asset management policies to protect assets such as equipment, pharmaceuticals, and
patient records.
Asset management makes it possible to keep track of important information about IT assets,
including ownership, location, changes, and age. A comprehensive asset management program
is an important prerequisite for ensuring that facilities and equipment remain secure and
operational.
Recommendation
Asset owners need to classify and protect their assets and maintain up-to-date information
about asset management, location, and security.
CSPs typically use formal asset management policies that require all assets to be accounted for
and have designated asset owners. A typical CSP maintains an inventory of major hardware
assets used in their cloud infrastructure environment, and conducts regular audits to verify the
inventory.
28%
6 SECURITY TRENDS
of surveyed healthcare organizations have a disaster recovery
program
Also, only 24% regularly test their disaster recovery site, which puts them at potential risk for
untimely interruptions.
35% of all industries surveyed worldwide do not have disaster recovery programs, which
suggests that healthcare organizations (at 31%) are more mature in this regard.
A disaster recovery plan defines the approach and steps that an organization will take to resume
operations under adverse conditions such as natural disasters, attacks, or unrest.
Recommendation
A disaster recovery plan should be created that assigns clear responsibilities to specific
personnel; defines objectives for recovery; delineates standards for notification, escalation, and
deceleration; and provides for training all appropriate parties.
CSPs typically maintain disaster recovery frameworks that are consistent with industry practices.
of surveyed healthcare organizations cannot prevent a power
outage from affecting their organization
Redundant systems provide continuity of operations if a disruption occurs.
26% of all industries surveyed worldwide cannot prevent a power outage from affecting their
organization, which suggests that healthcare organizations (at 23%) are more mature in this
regard
Without redundancy, a data center can become a single point of failure that threatens the
routine operations of an organization.
Recommendation
Power systems should use dedicated 24x7 uninterruptible power supply (UPS) equipment and
backup generators, and all critical electrical components should be constantly monitored. Power
systems include all critical electrical components, including transfer switches, main switchgear,
and power management modules.
CSPs typically have dedicated operations center facilities that monitor critical support systems
like power.
31%
23%
References for additional reading
TwC Trusted Cloud
http://www.microsoft.com/twcloud
Secure Software Trends in Healthcare (PDF)
http://aka.ms/SDLHealthcare
S-ar putea să vă placă și
- Microsoft Security Intelligence Report Volume 16Document152 paginiMicrosoft Security Intelligence Report Volume 16MSFTSIRÎncă nu există evaluări
- Developing A National Strategy For CybersecurityDocument24 paginiDeveloping A National Strategy For CybersecurityMSFTSIRÎncă nu există evaluări
- Security Trends in The Public SectorDocument8 paginiSecurity Trends in The Public SectorMSFTSIRÎncă nu există evaluări
- Security Trends in Retail OrganizationsDocument8 paginiSecurity Trends in Retail OrganizationsMSFTSIRÎncă nu există evaluări
- CISO Perspectives Today's RiskDocument4 paginiCISO Perspectives Today's RiskMSFTSIRÎncă nu există evaluări
- Microsoft Security Intelligence Report Volume 15 Key Findings SummaryDocument24 paginiMicrosoft Security Intelligence Report Volume 15 Key Findings SummaryMSFTSIRÎncă nu există evaluări
- An Introduction To Designing Reliable Cloud Services January 2014Document14 paginiAn Introduction To Designing Reliable Cloud Services January 2014MSFTSIRÎncă nu există evaluări
- Security Trends in Financial ServicesDocument8 paginiSecurity Trends in Financial ServicesMSFTSIRÎncă nu există evaluări
- The Microsoft Approach To Compliance in The CloudDocument12 paginiThe Microsoft Approach To Compliance in The CloudMSFTSIRÎncă nu există evaluări
- Microsoft Security Intelligence Report Volume 15Document160 paginiMicrosoft Security Intelligence Report Volume 15MSFTSIRÎncă nu există evaluări
- CISO Perspectives Data ClassificationDocument5 paginiCISO Perspectives Data ClassificationMSFTSIRÎncă nu există evaluări
- Microsoft Security Response Center (MSRC) Progress Report 2013Document27 paginiMicrosoft Security Response Center (MSRC) Progress Report 2013MSFTSIRÎncă nu există evaluări
- Data Classification For Cloud ReadinessDocument22 paginiData Classification For Cloud ReadinessHarkirat Singh50% (2)
- Cybersecurity Risk ParadoxDocument12 paginiCybersecurity Risk ParadoxMSFTSIRÎncă nu există evaluări
- Five Principles For Shaping Cybersecurity NormsDocument12 paginiFive Principles For Shaping Cybersecurity NormsMSFTSIRÎncă nu există evaluări
- AppLocker Design GuideDocument82 paginiAppLocker Design GuideMSFTSIR100% (1)
- Whitepaper: Evaluating Microsoft's Protection Performance and Capabilities Protection Performance and CapabilitiesDocument13 paginiWhitepaper: Evaluating Microsoft's Protection Performance and Capabilities Protection Performance and CapabilitiesMSFTSIRÎncă nu există evaluări
- Trends in Cloud Computing Cloud Security Readiness ToolDocument40 paginiTrends in Cloud Computing Cloud Security Readiness ToolChristian Paul Manalo TaburadaÎncă nu există evaluări
- Problem Management For Reliable Online Services PDFDocument16 paginiProblem Management For Reliable Online Services PDFsaad14014Încă nu există evaluări
- Microsoft Security Intelligence Report Volume 14 EnglishDocument120 paginiMicrosoft Security Intelligence Report Volume 14 EnglishMSFTSIRÎncă nu există evaluări
- CISO Perspectives On ComplianceDocument4 paginiCISO Perspectives On ComplianceMSFTSIRÎncă nu există evaluări
- Resilience by Design For Cloud ServicesDocument19 paginiResilience by Design For Cloud ServicesMSFTSIRÎncă nu există evaluări
- Learn How Socio-Economic Factors Affect Regional Malware RatesDocument27 paginiLearn How Socio-Economic Factors Affect Regional Malware RatesMSFTSIRÎncă nu există evaluări
- Deploying Highly Available and Secure Cloud SolutionsDocument26 paginiDeploying Highly Available and Secure Cloud SolutionsMSFTSIRÎncă nu există evaluări
- Mitigating Pass-The-Hash (PTH) Attacks and Other Credential Theft Techniques - EnglishDocument82 paginiMitigating Pass-The-Hash (PTH) Attacks and Other Credential Theft Techniques - EnglishMSFTSIRÎncă nu există evaluări
- Microsoft Malware Protection Center Threat Report: RootkitsDocument16 paginiMicrosoft Malware Protection Center Threat Report: RootkitsMSFTSIRÎncă nu există evaluări
- Determined Adversaries and Targeted AttacksDocument22 paginiDetermined Adversaries and Targeted AttacksMSFTSIRÎncă nu există evaluări
- MSRC Progress Report 2012Document33 paginiMSRC Progress Report 2012MSFTSIRÎncă nu există evaluări
- Microsoft Security Intelligence Report Volume 13 EnglishDocument146 paginiMicrosoft Security Intelligence Report Volume 13 EnglishNeagu JellyÎncă nu există evaluări
- Shoe Dog: A Memoir by the Creator of NikeDe la EverandShoe Dog: A Memoir by the Creator of NikeEvaluare: 4.5 din 5 stele4.5/5 (537)
- Grit: The Power of Passion and PerseveranceDe la EverandGrit: The Power of Passion and PerseveranceEvaluare: 4 din 5 stele4/5 (587)
- Hidden Figures: The American Dream and the Untold Story of the Black Women Mathematicians Who Helped Win the Space RaceDe la EverandHidden Figures: The American Dream and the Untold Story of the Black Women Mathematicians Who Helped Win the Space RaceEvaluare: 4 din 5 stele4/5 (890)
- The Yellow House: A Memoir (2019 National Book Award Winner)De la EverandThe Yellow House: A Memoir (2019 National Book Award Winner)Evaluare: 4 din 5 stele4/5 (98)
- The Little Book of Hygge: Danish Secrets to Happy LivingDe la EverandThe Little Book of Hygge: Danish Secrets to Happy LivingEvaluare: 3.5 din 5 stele3.5/5 (399)
- On Fire: The (Burning) Case for a Green New DealDe la EverandOn Fire: The (Burning) Case for a Green New DealEvaluare: 4 din 5 stele4/5 (73)
- The Subtle Art of Not Giving a F*ck: A Counterintuitive Approach to Living a Good LifeDe la EverandThe Subtle Art of Not Giving a F*ck: A Counterintuitive Approach to Living a Good LifeEvaluare: 4 din 5 stele4/5 (5794)
- Never Split the Difference: Negotiating As If Your Life Depended On ItDe la EverandNever Split the Difference: Negotiating As If Your Life Depended On ItEvaluare: 4.5 din 5 stele4.5/5 (838)
- Elon Musk: Tesla, SpaceX, and the Quest for a Fantastic FutureDe la EverandElon Musk: Tesla, SpaceX, and the Quest for a Fantastic FutureEvaluare: 4.5 din 5 stele4.5/5 (474)
- A Heartbreaking Work Of Staggering Genius: A Memoir Based on a True StoryDe la EverandA Heartbreaking Work Of Staggering Genius: A Memoir Based on a True StoryEvaluare: 3.5 din 5 stele3.5/5 (231)
- The Emperor of All Maladies: A Biography of CancerDe la EverandThe Emperor of All Maladies: A Biography of CancerEvaluare: 4.5 din 5 stele4.5/5 (271)
- The Gifts of Imperfection: Let Go of Who You Think You're Supposed to Be and Embrace Who You AreDe la EverandThe Gifts of Imperfection: Let Go of Who You Think You're Supposed to Be and Embrace Who You AreEvaluare: 4 din 5 stele4/5 (1090)
- The World Is Flat 3.0: A Brief History of the Twenty-first CenturyDe la EverandThe World Is Flat 3.0: A Brief History of the Twenty-first CenturyEvaluare: 3.5 din 5 stele3.5/5 (2219)
- Team of Rivals: The Political Genius of Abraham LincolnDe la EverandTeam of Rivals: The Political Genius of Abraham LincolnEvaluare: 4.5 din 5 stele4.5/5 (234)
- The Hard Thing About Hard Things: Building a Business When There Are No Easy AnswersDe la EverandThe Hard Thing About Hard Things: Building a Business When There Are No Easy AnswersEvaluare: 4.5 din 5 stele4.5/5 (344)
- Devil in the Grove: Thurgood Marshall, the Groveland Boys, and the Dawn of a New AmericaDe la EverandDevil in the Grove: Thurgood Marshall, the Groveland Boys, and the Dawn of a New AmericaEvaluare: 4.5 din 5 stele4.5/5 (265)
- The Unwinding: An Inner History of the New AmericaDe la EverandThe Unwinding: An Inner History of the New AmericaEvaluare: 4 din 5 stele4/5 (45)
- The Sympathizer: A Novel (Pulitzer Prize for Fiction)De la EverandThe Sympathizer: A Novel (Pulitzer Prize for Fiction)Evaluare: 4.5 din 5 stele4.5/5 (119)
- Her Body and Other Parties: StoriesDe la EverandHer Body and Other Parties: StoriesEvaluare: 4 din 5 stele4/5 (821)
- Exploratory EssayDocument9 paginiExploratory Essayapi-237899225Încă nu există evaluări
- A Recurrent Quest For Corporate Governance in India Revisiting The Imbalanced Scales of Shareholders' Protection in Tata Mistry CaseDocument17 paginiA Recurrent Quest For Corporate Governance in India Revisiting The Imbalanced Scales of Shareholders' Protection in Tata Mistry CaseSupriya RaniÎncă nu există evaluări
- BP - Electrical PermitDocument2 paginiBP - Electrical PermitDwinix John CabañeroÎncă nu există evaluări
- Edsml Assignment SCM 2 - Velux GroupDocument20 paginiEdsml Assignment SCM 2 - Velux GroupSwapnil BhagatÎncă nu există evaluări
- Rapport 2019 de La NHRC de Maurice: Découvrez Le Rapport Dans Son IntégralitéDocument145 paginiRapport 2019 de La NHRC de Maurice: Découvrez Le Rapport Dans Son IntégralitéDefimediaÎncă nu există evaluări
- Aristotle Model of CommunicationDocument4 paginiAristotle Model of CommunicationSem BulagaÎncă nu există evaluări
- HRM Assessment (Final Copy) - Home Loan Experts Nepal - EMBA Fall 2020Document33 paginiHRM Assessment (Final Copy) - Home Loan Experts Nepal - EMBA Fall 2020Rajkishor YadavÎncă nu există evaluări
- Emanel Et - Al Informed Consent Form EnglishDocument6 paginiEmanel Et - Al Informed Consent Form English4w5jpvb9jhÎncă nu există evaluări
- How To Configure User Accounts To Never ExpireDocument2 paginiHow To Configure User Accounts To Never ExpireAshutosh MayankÎncă nu există evaluări
- Hackers Speaking Test ReviewDocument21 paginiHackers Speaking Test ReviewMark Danniel SaludÎncă nu există evaluări
- Retail investment: Addressing timing and pricing issues through SIPsDocument52 paginiRetail investment: Addressing timing and pricing issues through SIPsMauryanÎncă nu există evaluări
- The Rocky Mountain WestDocument202 paginiThe Rocky Mountain WestYered Canchola100% (1)
- Murder in Baldurs Gate Events SupplementDocument8 paginiMurder in Baldurs Gate Events SupplementDavid L Kriegel100% (3)
- Irregular verbs guideDocument159 paginiIrregular verbs guideIrina PadureanuÎncă nu există evaluări
- Class Xi BST Chapter 6. Social Resoposibility (Competency - Based Test Items) Marks WiseDocument17 paginiClass Xi BST Chapter 6. Social Resoposibility (Competency - Based Test Items) Marks WiseNidhi ShahÎncă nu există evaluări
- Indian Accounting StandardsDocument4 paginiIndian Accounting StandardsManjunatha B KumarappaÎncă nu există evaluări
- FX MKT Insights Jun2010 Rosenberg PDFDocument27 paginiFX MKT Insights Jun2010 Rosenberg PDFsuksesÎncă nu există evaluări
- 79.1 Enrico vs. Heirs of Sps. Medinaceli DigestDocument2 pagini79.1 Enrico vs. Heirs of Sps. Medinaceli DigestEstel Tabumfama100% (1)
- Pub. 127 East Coast of Australia and New Zealand 10ed 2010Document323 paginiPub. 127 East Coast of Australia and New Zealand 10ed 2010joop12Încă nu există evaluări
- Vodafone service grievance unresolvedDocument2 paginiVodafone service grievance unresolvedSojan PaulÎncă nu există evaluări
- 3.1.bauer Martin-Resistance To New Technology Nuclear Power, Information Technology and Biotechnology 1995Document436 pagini3.1.bauer Martin-Resistance To New Technology Nuclear Power, Information Technology and Biotechnology 1995Anonymous 2o0az0zOJÎncă nu există evaluări
- Audit of Allocations to LGUsDocument7 paginiAudit of Allocations to LGUsRhuejane Gay MaquilingÎncă nu există evaluări
- Pharma: Conclave 2018Document4 paginiPharma: Conclave 2018Abhinav SahaniÎncă nu există evaluări
- TARIFFS AND POLITICS - EVIDENCE FROM TRUMPS Trade War - Thiemo Fetze and Carlo Schwarz PDFDocument25 paginiTARIFFS AND POLITICS - EVIDENCE FROM TRUMPS Trade War - Thiemo Fetze and Carlo Schwarz PDFWilliam WulffÎncă nu există evaluări
- Construction Management Guideline (Provisional Edition)Document97 paginiConstruction Management Guideline (Provisional Edition)Kaung Myat HtunÎncă nu există evaluări
- Client Portfolio Statement: %mkvalDocument2 paginiClient Portfolio Statement: %mkvalMonjur MorshedÎncă nu există evaluări
- 1Document1 pagină1MariaMagubatÎncă nu există evaluări
- IEC 60050-151-2001 Amd2-2014Document8 paginiIEC 60050-151-2001 Amd2-2014mameri malekÎncă nu există evaluări
- Project Report Final PDFDocument74 paginiProject Report Final PDFSaurav KumarÎncă nu există evaluări
- Ray Kroc's Visionary Leadership at McDonald'sDocument4 paginiRay Kroc's Visionary Leadership at McDonald'sViknesh Kumanan100% (1)