Documente Academic
Documente Profesional
Documente Cultură
ISSL ORAL QUESTIONS
Încărcat de
Jeevjyot Singh Chhabda0 evaluări0% au considerat acest document util (0 voturi)
58 vizualizări8 paginiiasl,unit wise
Titlu original
IASL Oral Question Bank
Drepturi de autor
© © All Rights Reserved
Formate disponibile
PDF, TXT sau citiți online pe Scribd
Partajați acest document
Partajați sau inserați document
Vi se pare util acest document?
Este necorespunzător acest conținut?
Raportați acest documentiasl,unit wise
Drepturi de autor:
© All Rights Reserved
Formate disponibile
Descărcați ca PDF, TXT sau citiți online pe Scribd
0 evaluări0% au considerat acest document util (0 voturi)
58 vizualizări8 paginiISSL ORAL QUESTIONS
Încărcat de
Jeevjyot Singh Chhabdaiasl,unit wise
Drepturi de autor:
© All Rights Reserved
Formate disponibile
Descărcați ca PDF, TXT sau citiți online pe Scribd
Sunteți pe pagina 1din 8
ISSL ORAL QUESTIONS
1. What is a security mechanism?
Ans: A Security mechanism is any process that is designed to detect, prevent, or recover
from a security attack.
2. What is meant by threat?
Ans: A potential for violation of security, which exists when there is a circumstances,
capability, action or event that could breach security and cause harm. That is, a threat is a
possible danger that might exploit vulnerability.
. What is Enci!herment?
Ans: The use of mathematical algorithms to transform data into a form that is not readily
intelligible. The transformation and subsequent recovery of the data depend on an
algorithm and zero or more encryption keys.
". What are the #$ur basic tas%s in &esi'nin' a !articu(ar security ser)ice?
Ans: our basic tasks in designing a particular security service are!
1. "esign an algorithm for performing the security#related transformation. The algorithm
should be such that an opponent cannot defeat its purpose.
$. %enerate the secret information to be used with the algorithm.
&. "evelop methods for the distribution and sharing of the secret information
'. Specify a protocol to be used by the two principals that makes use of the security
algorithm and the secret information to achieve a particular security.
*. What is a !assi)e attac%?
Ans: (assive attacks are in the nature of eavesdropping on, or monitoring of, transmissions.
Two types of passive attacks are release of message contents and traffic analysis
+. What is an acti)e attac%?
Ans: An active attack involves some modification of the data stream or the creation of a
false.
,. What are the as!ects $# in#$rmati$n security?
Ans: There are three aspects of the information security. i. e. Security attack, Security
mechanism, Security Service
-. List s$me c$mm$n in#$rmati$n inte'rity #uncti$ns?
Ans! )dentification, Authorization, *oncurrence, +iability, ,ndorsement, -alidation, Time
of occurrence, .egistration
.. /e#ine a threat?
Ans: A potential for violation of security, which exists when there is a circumstances,
capability, action or event that could breach security and cause harm. That is, a threat is a
possible danger that might exploit vulnerability.
10. /e#ine an attac%?
Ans: An attack on system security that derives from an intelligent threat! that is an
intelligent act that is a deliberate attempt to evade security services and violate the security
policy of a system.
11. List e s$me e1am!(e $# security attac%s?
%ain unauthorized access to information
"isavow responsibility or liability for information the cheater did originate.
,nlarge cheater/s legitimate license .
(ervert the function of software, typically by adding a covert function.
*ause others to violate a protocol by means of introducing incorrect information.
12. What are the essentia( in're&ients $# a symmetric ci!her?
Ans: A symmetric encryption scheme has five ingredients! (laintext, ,ncryption
algorithm, Secret 0ey, *ipher text, "ecryption algorithm.
1. What are the t2$ basic #uncti$ns use& in the encry!ti$n a('$rithm?
Ans: All the encryption algorithms are based on two general principles!
Substituti$n: )n which each element in the plaintext is mapped into another
element.
Trans!$siti$n: )n which elements in the plaintext are rearranged. The fundamental
requirement is that no information be lost.
1'. 3$2 many %eys are re4uire& #$r t2$ !e$!(e t$ c$mmunicate )ia a ci!her?
Ans: )f both sender and receiver use the same key, the system is referred as symmetric,
single#key, secret#key or conventional encryption. )f both sender and receiver use a
different key, the system is referred as asymmetric, two#key or public key encryption.
1*. What are the t2$ 'enera( a!!r$aches t$ attac%in' a ci!her?
Ans: The general two approaches for attacking a cipher
1. 5ry!tana(ysis: *ryptanalytic attacks rely on the nature of the algorithm plus
perhaps some knowledge of the general characteristics of the plaintext or even some
samples plaintext#cipher text pairs.
2. 6rute7#$rce attac%: The attacker tries every possible key on a piece of cipher text
until an intelligible translation into plaintext is obtained.
1+. /e#ine the 5aesar ci!her?
Ans: The *aesar cipher involves replacing each letter of the alphabet with the letter
standing three places down the alphabet .The alphabet is wrapped around, so that the
letter following 2 is A.
* 3 , 4p5 3 4p 6 &5 mod 4$75
The general *aesar cipher algorithm is
* 3 , 4p5 3 4p 6 k5 mod 4$75
8here k takes the value in the range 1 to $9
The decryption algorithm is
p 3 "4*5 3 4* # k5 mod 4$75
1:. /e#ine the m$n$a(!habetic ci!her?
Ans: A dramatic increase in the key space is achieved by allowing an arbitrary
substitution. There are $7; possible keys. )t is referred to as monoalphabetic substitution
cipher, because a single cipher alphabet is used per message.
1-. /e#ine the 8(ay#air ci!her?
Ans: The (layfair cipher treats the diagrams in the plaintext as single units and translates
these units into cipher text diagrams. This algorithm is based on the use of a 9 by 9
matrix of letters constructed using keyword.
1.. What is the &i##erence bet2een a m$n$a(!habetic ci!her an& a !$(ya(!habetic
ci!her?
Ans: )n monoalphabetic cipher single cipher alphabet is used per message. <ut in
polyalphabetic cipher there are multiple cipher text letters for each plaintext letter, one
for each unique letter of keyword.
20. What is !r$&uct ci!her?
Ans: (roduct cipher has the performance of two or more basic ciphers in sequence is such
a way that the final result or product is cryptographically stronger than any of the
component ciphers.
21. What is the &i##erence bet2een /i##usi$n an& 5$n#usi$n?
Ans: )n /i##usi$n the statistical structure of the plaintext is dissipated into long range
statistics of the cipher text. This is achieved by having each plaintext digit affect the value
of many cipher text digits. 5$n#usi$n seeks to make a relationship between the statistics of
the cipher text and the value of the encryption key as complex as possible. Thus even if the
attacker can get some handle on the statistics of the cipher text, the way in which the key
was used to produce that cipher text is so complex as to make it difficult to deduce the key.
22 E1!(ain the a)a(anche e##ect=
Ans: A desirable property of any encryption algorithm is that a small change in either the
plaintext or the key should produce a significant change in the ciphertext. )n particular, a
change ) one of the plaintext or one bit of the key should produce a change in many bits of
the cipher text.
$&. What is a brute #$rce attac%?
Ans! A brute force attack consists of trying every possible code, combination, or password
until you find the right one.
$'. What is /ES?
Ans! ",S is a symmetric cipher defined in ederal )nformation (rocessing 4)(S5 Standard
>umber '7 in 1?:: as the federal government approved encryption algorithm for sensitive
but non#classified information. ",S utilizes a 97#bit key. This key size is vulnerable to a
brute force attack using current technology.
$9. What are the E56 an& 565 9$&es?
Ans: 8hen we use a block cipher to encrypt a message of arbitrary length, we use
techniques that are known as modes of operation for the block cipher. )n ,*< mode, each
plaintext block is encrypted independently with the block cipher. ,*< mode is as secure as
the underlying block cipher. )n *<* mode, each plaintext block is exclusive#@.ed with
previous ciphertext block, then encrypted
2+. What are the 5:6 an& O:6 m$&es?
Ans: The *ipher eedback 4*<5 mode and the @utput eedback 4@<5 mode are two
more standard modes of operation for a block cipher. )n 5:6 mode, the previous ciphertext
block is encrypted and the output produced is combined with the plaintext block using
exclusive#or to produce the current ciphertext block. )t is possible to define *< mode so
that it uses feedback that is less than one full data block. O:6 mode is similar to the *<
mode except that the quantity exclusive#@.ed with each plaintext block is generated
independently of both the plaintext and ciphertext. The encryption of a plaintext block is
derived by taking the exclusive#@. of the plaintext block with the relevant data block.
2,.What is a cry!t$($'y?
Ans: *ryptology is the science which incorporates both cryptography and cryptanalysis.
$A. What is cry!tana(ysis?
Ans! *ryptanalysis is the science of making encrypted data unencrypted.
2... What are symmetric an& asymmetric ci!hers?
Ans! )n a symmetric cipher, both parties must agree on the encryption key in advance.
Symmetric systems are also known as shared secret systems or private key systems.
)n an asymmetric cipher, the key is negotiated between the parties during communication.
)n an asymmetric system, each person has two keys. @ne key, the public key, is shared
publicly. The second key, the private key, should never be shared with anyone.
0.What is the /i##ie73e((man %ey e1chan'e=
Ans: The purpose for this algorithm is to enable two users to exchange a key securely that
can then be used for subsequent encryption of messages. )t depends for its effectiveness on
the difficulty of computing discrete logarithms.
1.What is a !rime number?
Ans! A prime number is an integer that can only be divided without remainder by positive
and negative values of itself and 1.
2. /e#ine :ermat;s the$rem?
Ans! ermat/s theorem states that, if p is prime number and a is a positive integer not
divisible by p then a
p#1
3 1 4mod p5
. What is a tra!&$$r $ne72ay #uncti$n?
Ans: A trapdoor one#way function is a one#way function for which the inverse direction is
easy given a certain piece of information 4the trapdoor5, but difficult otherwise.
&'.Str$n' 8rimes are necessary in RSA?
Ans: )n the literature pertaining to .SA, it has often been suggested that in choosing a key
pair, one should use so#called BstrongB primes p and q to generate the modulus n. Strong
primes are those with certain properties that make the product n hard to factor by specific
factoring methodsC such properties have included, for example, the existence of a large
prime factor of p#1 and a large prime factor of p61. The reason for these concerns is that
some factoring methods are especially suited to primes p such that p #1 or p61 has only
small factorsC strong primes are resistant to these attacks.
&9. What is the E(<ama( 5ry!t$system?
Ans! The ,l%amal system is a public#key cryptosystem based on the discrete logarithm
problem. )t consists of both encryption and signature algorithms. The encryption algorithm
is similar in nature to the "iffie#Dellman key agreement protocol. The system parameters
consist of a prime p and an integer g, whose powers modulo p generate a large number of
elements, as in "iffie#Dellman. Alice has a private key a and a public key y, where
y 3 g
a
4mod p5. Suppose <ob wishes to send a message m to Alice. <ob first generates a
random number k less than p. De then computes y
1
3 g
k
4mod p5 and y
$
3 m xor y
k
, where
E@. denotes the bit#wise exclusive#or. <ob sends 4y
1
,y
$
5 to Alice.
+. What are E((i!tic 5ur)e 5ry!t$systems?
Ans! ,lliptic curve cryptosystems are analogs of public#key cryptosystems such as .SA
and ,l%amal in which modular multiplication is replaced by the elliptic curve addition
operation. The curves used in elliptic curve analogs of discrete logarithm cryptosystems
are normally of the form y
$
3 x
&
6 ax 6 b 4mod p5, where p is prime. The problem tapped
by the discrete logarithm analogs in elliptic curves is the elliptic curve logarithm problem,
defined as follows! given a point % on an elliptic curve with order r 4number of points on
the curve5 and another point F on the curve, find a unique x 4G x r # 15 such that F 3 x%,
i.e., F is the xth multiple of %.
&:. What is /i##erentia( 5ry!tana(ysis?
Ans! "ifferential cryptanalysis is a type of attack that can be mounted on iterative block
ciphers. "ifferential cryptanalysis is basically a chosen plaintext attack and relies on an
analysis of the evolution of the differences between two related plaintexts as they are
encrypted under the same key. <y careful analysis of the available data, probabilities can
be assigned to each of the possible keys and eventually the most probable key is identified
as the correct one.
-. What is Linear 5ry!tana(ysis?
Ans! +inear cryptanalysis is a known plaintext attack and uses a linear approximation to
describe the behavior of the block cipher. %iven sufficient pairs of plaintext and
corresponding ciphertext, bits of information about the key can be obtained and increased
amounts of data will usually give a higher probability of success.
. *<* mode is as secure as the underlying block cipher against standard attacks.
.. A(ice 2ants t$ 'enerate a !air $# RSA !ub(ic an& !ri)ate %eys. She starts by
se(ectin' t2$ !rimes ! = * an& 4 = ,.
a. 5$m!ute n> ?n@.
Ans! n 3 pq 3 9 x : 3 &9
4n5 3 4p#154q#15 3 49#154:#15 3 'x7 3 $'
b. In se(ectin' a &ecry!ti$n ?!ri)ate@ %ey &> A(ice &eci&es &= is n$t '$$&> 2hy?
She se(ects & = 11 instea&. Which is the c$rrect encry!ti$n ?!ub(ic@ %ey> e
1
= 11 $r
e
2
= 1 ?
Ans! d3& is not good because gcd4d, 4n55 3 gcd4&, $'5 is not 1.
e
1
3 11 is the correct encryption key because d e
1
3 11x1131$13 1 mod 4n5
c. Su!!$se 6$b 2ants t$ sen& a messa'e 9= t$ A(ice. Which %ey sh$u(& he use?
What;s the ci!herte1t he sen&s t$ A(ice?
Ans! * 3 H
e
mod > 3 4&&5
11
mod &9 3 4#$5
11
mod &9 3 #1A mod &9 3 1: mod &9
&. A#ter A(ice recei)es the ci!herte1t> h$2 &$es she &ecry!t?
Ans! H 3 *
d
mod > 3 41:5
11
mod &9 3 &&
e. I# A(ice 2ant t$ sen& 6 a si'ne& messa'e> 'i)en 9; = +> 2hat 2$u(& A(ice sen&?
Ans! Sign4H/5 3 4H/5
d
mod > 3 475
11
mod &9 3 7 I 4&75
9
mod &9 3 7 I 415
9
mod &9 3 7
#. 3$2 &$es 6$b )eri#y the messa'e is sent by A(ice?
Ans! H/ 3 4Sign4H/55
e
mod >
1". 5$nsi&er a /i##ie73e((man scheme 2ith a c$mm$n !rime 4 = 11 an& a
!rimiti)e r$$t =2. sh$2 that 2 is a !rimiti)e r$$t $# 11.
Ans:
$ mod 11 3 $
$
$
mod 11 3 '
$
&
mod 11 3 A
$
'
mod 11 3 9
$
9
mod 11 3 1G
$
7
mod 11 3 ?
$
:
mod 11 3 :
$
A
mod 11 3 &
$
?
mod 11 3 7
$
1G
mod 11 3 1 Since $
i
mod 11 for GJiJ11 contains all numbers from 1 to 11#1,
the size of this set is equal to 4q5, the order of q. Dence $ is a primitive root of
11.
b. I# user A has !ub(ic %ey A
A
= .> 2hat is A;s !ri)ate %ey B
A
?
rom the above values, $
7
mod 11 3 ?, therefore E
A
3 7.
c. I# user 6 has !ub(ic %ey A
6
= > 2hat is the share& secret %ey C?
0 3 4F
<
5
EA
mod q 3 4&5
7
mod 11 3 &
"0. :$r ($n' messa'es> RSA 2i(( be a!!(ie& in b($c%s. I# the b($c% is )ery sma((> say
it c$ntains $n(y $ne (etter in each b($c%> 2i(( the encry!ti$n be secure?
Ans: N$. )f the block contains only one letter, then each letter will be mapped to a
fixed replacement. Thus it will become a substitution cipher 4e.g. Honoalphabetic
Substitution5, and the cipher can be broken using frequency analysis.
"1.What are the essentia( in're&ients $# a !ub(ic7%ey &irect$ry?
Ans:
The authority maintains a directory with a entry for each participant.
,ach participant registers a public key with the directory authority.
A participant may replace the existing key with a new one at any time.
(eriodically, the authority publishes the entire directory or updates to the directory.
(articipants could also access the directory electronically.
"2. What is !ub(ic7%ey certi#icate?
Ans: The public#key authority could be a bottleneck in the system, for a Kser must appeal
to the authority for a public key for every other user that it wishes to contact. As before
the directory of names and public keys maintained by the authority is vulnerable to
tempering.
".What are the re4uirements #$r the use $# a !ub(ic7%ey certi#icate scheme?
Ans:
Any participant can read a certificate to determine the name and public key of
the certificate/s owner.
Any participant can verify that the certificate originated from the certificate
authority and is not counterfeit.
@nly the certificate authority can create and update certificates.
Any participant can verify the currency of the certificate.
"".What is the Li#e 5yc(e $# a Cey?
Ans: 0eys have limited lifetimes for a number of reasons. The most important reason is
protection against cryptanalysis. ,ach time the key is used, it generates a number of
ciphertexts. ord describes the life cycle of a key as follows!
key generation and possibly registration for a public key
key distribution
key activationLdeactivation
key replacement or key update
key revocation
key termination, involving destruction and possibly archival
"*. What is a 3ash :uncti$n?
Ans: A hash function D is a transformation that takes a variable#size input m and returns a
fixed#size string, which is called the hash value h 4that is, h 3 D4m55. Dash functions with
Must this property have a variety of general computational uses, but when employed in
cryptography the hash functions are usually chosen to have some additional properties.
The basic requirements for a cryptographic hash function are!
the input can be of any length,
the output has a fixed length,
D4x5 is relatively easy to compute for any given x ,
D4x5 is one#way,
D4x5 is collision#free.
"+.What ty!es $# attac%s are a&&resse& by messa'e authenticati$n?
Ans:
5$ntent m$&i#icati$n: 7 *hanges to the contents of the message
Se4uence m$&i#icati$n: 7 Any modification to a sequence of messages between
parties, including insertion, deletion, and reordering.
Timin' m$&i#icati$n: 7 "elay or replay of messages.
",. What is the use $# &i'ita( si'nature?
Ans! "ata appended to, or a data unit that allows a recipient of the data unit to prove the
source and integrity if the data unit and protect against forgery
'A.What t2$ (e)e(s $# #uncti$na(ity c$m!rise a messa'e authenticati$n $r &i'ita(
si'nature mechanism?
Ans: Two levels of functionality comprise a message authentication or digital signature
mechanisms are +ow#level authentication and Digher#level authentication. At the lower
level there must be some sort of function that produces an authenticator! a value to be used
to authenticate a message. This lower level function is then used as primitive in a higher#
level authentication protocol that enables a receiver to verify the authenticity of message.
"..What is a messa'e authenticati$n c$&e?
Ans: An alternative authentication technique involves the use of a small fixed size block of
data, known as a cryptographic checksum or HA* that is appended to the message.
*0.What is the &i##erence bet2een a messa'e authenticati$n c$&e an& a $ne72ay hash
#uncti$n?
Ans: The difference between an HA* and a one#way hash function is that unlike an HA*,
a hash code does not use a key but is a function only of the input message.
91.Is it necessary t$ rec$)er the secret %ey in $r&er t$ attac% a 9A5 a('$rithm?
Ans: A number of keys will produce the correct HA* and the opponent has no way of
knowing which the correct key is. @n an average $
4n#k5
keys produce a match. Therefore
attacks do not require the discovery of the key.
*2.What is the &i##erence bet2een a str$n' an& a 2ea% c$((isi$n resistance?
Ans:
or any given value h it is computationally infeasible to find yLx with D4y53D4x5.This is
Nweak collision resistanceO. )t is a one#way property. )t is easy to generate a code given
a message, but almost impossible to do the reverse.
)t is computationally infeasible to find any pair4x,y5 such that D4x53D4y5.This is Nstrong
collision resistanceO. This guarantees that an alternative message hashing to the same
value as a given message cannot be found. This prevents forgery.
9&.What is the #uncti$n $# a c$m!ressi$n #uncti$n in a hash #uncti$n?
Ans: The hash function involves repeated use of a compression function. The motivation
is that if the compression function is collision resistant, then the hash function is also
collision resistant function. So a secure hash function can be produced.
*". What is a birth&ay attac%?
Ans! A birthday attack is a name used to refer to a class of brute#force attacks. )t gets its
name from the surprising result that the probability that two or more people in a group of
$& share the same birthday is greater than 1L$C such a result is called a birthday paradox.
**. What is the uti(ity $# a &etache& si'nature?
Ans: A detached signature may be stored and transmitted separately from the message
it signs. This is useful in several contexts. A user may wish to maintain a separate
signature log of all messages sent or received. A detached signature of an executable
program can detect subsequent virus infection. inally detached signature can be used
when more than one party must sign a document, such as legal contract.
*+. Why &$es 8<8 'enerate a si'nature be#$re a!!(yin' c$m!ressi$n?
Ans: The signature is generated before compression due to $ reasons!
1. )t is preferable to sign an uncompressed message so that one can store only the
uncompressed message together with the signature for future verification
$. ,ven if one were willing to generate dynamically a recompressed message for
verification, (%(/s compression algorithm presents a difficulty
*,. Why is R +" c$n)ersi$n use#u( #$r emai( 'enerati$n?
Ans: The .adix 7' conversion is performed before the segmentation of the messages
take place. The use of radix 7' is that it converts he input stream to &&P. The radix 7'
converts the input stream to a radix 7' format
*-. What is 9I9E?
1. Ans: Hultipurpose )nternet Hail ,xtensions 4H)H,5 is an extension to the .*
A$$ framework that is intended to address some of the problems and limitations of
these uses of SHT(.
*.. What is SD9I9E?
Ans: SecureLHultipurpose )nternet Hail ,xtension is a security enhancement to the
H)H, )nternet e#mail format standard, based on technology from .SA "ata Security.
)t is ability to sign andLor encrypt messages.
7G. What ser)ices are !r$)i&e& by I8Sec?
Ans: Services provided by )(Sec
Access control
*onnectionless integrity
"ata origin authentication
.eMection of replayed packets
+1. What is the &i##erence bet2een Trans!$rt m$&e an& Tunne( m$&e?
Ans:
Trans!$rt m$&e Tunne( m$&e
1. )t provides protection for upper
layer protocols.
$. Ksed for end#to#end
communication between two host
&. AD! Authenticates )( payload
and selected portions of )( header
and )(v7 extension header
1. )t provides protection to the entire )(
packet.
$. )t is used when one or both ends of an
SA is a security gateway, such as
firewall or router that implement )(Sec.
&. Authenticates entire inner )( packet plus
selected portions of outer )( header and
outer )(v7 extension headers.
+2. What is re!(ay attac%?
Ans: A replay attack is one which an attacker obtains a copy of an authenticated packet
and later transmits it to the intended destination.
S-ar putea să vă placă și
- Network Design and Security ManagementDocument52 paginiNetwork Design and Security ManagementmehraDpaÎncă nu există evaluări
- U21CS601 CT Unit 123 Part B QADocument13 paginiU21CS601 CT Unit 123 Part B QASanthosh kannaÎncă nu există evaluări
- Computer Security AsDocument4 paginiComputer Security AsHagos gebreslasieÎncă nu există evaluări
- Cns Unit I Two MarksDocument5 paginiCns Unit I Two MarksBharathiÎncă nu există evaluări
- Is Lab ManualDocument114 paginiIs Lab ManualprathamgunjÎncă nu există evaluări
- Symmetric Cipher ModelDocument17 paginiSymmetric Cipher ModelAsif KoujaganurÎncă nu există evaluări
- Network Security NotesDocument170 paginiNetwork Security NotesJega DeesanÎncă nu există evaluări
- CS8792 CNS Two Marks Questions With AnswersDocument15 paginiCS8792 CNS Two Marks Questions With Answerslavanyaraju4985Încă nu există evaluări
- Stream Ciphers ExplainedDocument9 paginiStream Ciphers ExplainedSemsem SameerÎncă nu există evaluări
- Classical Encryption TechniquesDocument12 paginiClassical Encryption Techniquessushantluitel39Încă nu există evaluări
- Chapter 2 & 3Document20 paginiChapter 2 & 3Yakubu AliuÎncă nu există evaluări
- 598 3156 1 PBDocument8 pagini598 3156 1 PBstephenlim7986Încă nu există evaluări
- Traditional Symmetric CiphersDocument124 paginiTraditional Symmetric Cipherssanthosh RÎncă nu există evaluări
- 02 - Chapter 2 - Conventional Encryption and Message ConfidentialityDocument16 pagini02 - Chapter 2 - Conventional Encryption and Message ConfidentialityShreesha N RodriguesÎncă nu există evaluări
- Notes of Unit-1 Information SecurityDocument18 paginiNotes of Unit-1 Information SecurityAbhishek NarwariyaÎncă nu există evaluări
- 137 - CS8792, CS6701 Cryptography and Network Security - 2 Marks With Answers 3Document13 pagini137 - CS8792, CS6701 Cryptography and Network Security - 2 Marks With Answers 3Lionel Bharath RazerÎncă nu există evaluări
- 4 Cry PaDocument28 pagini4 Cry PaVenkata AppajiÎncă nu există evaluări
- Cryptography AssignmentDocument7 paginiCryptography Assignmentarijitsinha99Încă nu există evaluări
- Encryption StandardsDocument76 paginiEncryption Standardsbhasker7100% (1)
- Part ADocument14 paginiPart AHANISHA SAALIHÎncă nu există evaluări
- Rsa DocumentationDocument61 paginiRsa DocumentationPrasad NamaÎncă nu există evaluări
- Implementation of Aes and Blowfish AlgorithmDocument4 paginiImplementation of Aes and Blowfish AlgorithmInternational Journal of Research in Engineering and TechnologyÎncă nu există evaluări
- BT0088: Cryptography and Network Security - AssignmentDocument6 paginiBT0088: Cryptography and Network Security - AssignmentPawan Mall100% (1)
- Data Encryption Techniques and StandardsDocument59 paginiData Encryption Techniques and StandardsRajan Jamgekar100% (1)
- Introduction Graphic in PCDocument43 paginiIntroduction Graphic in PChahajsÎncă nu există evaluări
- CryptographyDocument5 paginiCryptographyJoelÎncă nu există evaluări
- Nadar Saraswathi College Cryptography QuestionsDocument12 paginiNadar Saraswathi College Cryptography Questionsdurai muruganÎncă nu există evaluări
- If You Have To Both Encrypt and Compress Data During Transmission, Which Would You Do First, and Why?Document20 paginiIf You Have To Both Encrypt and Compress Data During Transmission, Which Would You Do First, and Why?Pallavi BhartiÎncă nu există evaluări
- Weak and Semi-Weak Keys in DESDocument10 paginiWeak and Semi-Weak Keys in DESAbdulrahman RadeefÎncă nu există evaluări
- CSS Lab Manual - PrintDocument45 paginiCSS Lab Manual - PrintXavier TxAÎncă nu există evaluări
- SecurityDocument4 paginiSecuritysujitha14Încă nu există evaluări
- An Established New Symmetric Key Cipher PDFDocument18 paginiAn Established New Symmetric Key Cipher PDFMd. Anisur RahmanÎncă nu există evaluări
- Types of Encryption Ciphers ExplainedDocument9 paginiTypes of Encryption Ciphers ExplainedEng-Mushtaq HejairaÎncă nu există evaluări
- IT1352 Cryptography and Network SecurityDocument29 paginiIT1352 Cryptography and Network SecurityVishnupriya OmprakashÎncă nu există evaluări
- 137 - CS8792, CS6701 Cryptography and Network Security - 2 Marks With Answers 2Document17 pagini137 - CS8792, CS6701 Cryptography and Network Security - 2 Marks With Answers 2Lionel Bharath RazerÎncă nu există evaluări
- Symmetric Encryption, DES, AES, MAC, Hash Algorithms, HMACDocument76 paginiSymmetric Encryption, DES, AES, MAC, Hash Algorithms, HMACMukesh86% (7)
- Chapter 3 Encryption Principles and AlgorithmsDocument25 paginiChapter 3 Encryption Principles and AlgorithmsHiziki TareÎncă nu există evaluări
- CssDocument29 paginiCssArjun RawalÎncă nu există evaluări
- Securing Network Transactions - Pptx/vijetha BhatDocument27 paginiSecuring Network Transactions - Pptx/vijetha BhatVijetha bhatÎncă nu există evaluări
- Dhanalakshmi College of Engineering, ChennaiDocument12 paginiDhanalakshmi College of Engineering, ChennaiJayanthiVSÎncă nu există evaluări
- Unit IIDocument27 paginiUnit II20AD022 KAMALI PRIYA SÎncă nu există evaluări
- NSC Word All Unit QBDocument45 paginiNSC Word All Unit QByuvaraaj aletiÎncă nu există evaluări
- Index 2. Cryptography-Purpose 3. Types of Cryptographic AlgorithmsDocument12 paginiIndex 2. Cryptography-Purpose 3. Types of Cryptographic Algorithmstimothyosaigbovo3466Încă nu există evaluări
- VTU Network Security (10ec832) Unit-2 Notes..Document91 paginiVTU Network Security (10ec832) Unit-2 Notes..jayanthdwijesh h p100% (3)
- Cryptography & Network SecurityDocument25 paginiCryptography & Network Securityrrs_1988Încă nu există evaluări
- Cns FinalDocument59 paginiCns FinalAnita Martin100% (1)
- Chapter - 1Document31 paginiChapter - 1Subathra Devi MourouganeÎncă nu există evaluări
- Java ProjectDocument60 paginiJava ProjectAnkitaRaoÎncă nu există evaluări
- New Microsoft Word DocumentDocument8 paginiNew Microsoft Word Documentarmaan rathoreÎncă nu există evaluări
- Aias Assessment FinalsDocument10 paginiAias Assessment FinalsLexy Ira CapaoÎncă nu există evaluări
- Question Paper With Some ProjectsDocument37 paginiQuestion Paper With Some ProjectsBASHYAM PÎncă nu există evaluări
- Cholantechnology 4@Document32 paginiCholantechnology 4@ஸ்ரீ கண்ணன்Încă nu există evaluări
- Cryptography and Network Security Module 2 QuestionsDocument8 paginiCryptography and Network Security Module 2 QuestionsSubhadip MajiÎncă nu există evaluări
- Symmetric Encryption ExplainedDocument11 paginiSymmetric Encryption ExplainedAbdullah Al-HallakÎncă nu există evaluări
- Computer Security: Computer Threats and EncryptionDocument21 paginiComputer Security: Computer Threats and EncryptionPro NebyuÎncă nu există evaluări
- Application and Implementation of DES Algorithm Based on FPGADe la EverandApplication and Implementation of DES Algorithm Based on FPGAÎncă nu există evaluări
- New Frontiers in Cryptography: Quantum, Blockchain, Lightweight, Chaotic and DNADe la EverandNew Frontiers in Cryptography: Quantum, Blockchain, Lightweight, Chaotic and DNAÎncă nu există evaluări
- Pro Cryptography and Cryptanalysis: Creating Advanced Algorithms with C# and .NETDe la EverandPro Cryptography and Cryptanalysis: Creating Advanced Algorithms with C# and .NETÎncă nu există evaluări
- Simple Steps to Data Encryption: A Practical Guide to Secure ComputingDe la EverandSimple Steps to Data Encryption: A Practical Guide to Secure ComputingÎncă nu există evaluări
- LectureNote 03 Memory 2Document10 paginiLectureNote 03 Memory 2Jeevjyot Singh ChhabdaÎncă nu există evaluări
- Computer Architecture, A Quantitative Approach (Solution For 5th Edition)Document91 paginiComputer Architecture, A Quantitative Approach (Solution For 5th Edition)Harish Athuru43% (7)
- Vintage Days Schedule of Events - 2016Document1 paginăVintage Days Schedule of Events - 2016Jeevjyot Singh ChhabdaÎncă nu există evaluări
- Discrete Math - Mathematics For Computer ScienceDocument339 paginiDiscrete Math - Mathematics For Computer ScienceNungu Sungi100% (1)
- GRE Test Taker BrochureDocument8 paginiGRE Test Taker BrochureJeevjyot Singh ChhabdaÎncă nu există evaluări
- BE Information Technology CourseDocument41 paginiBE Information Technology CourseRia VijÎncă nu există evaluări
- Discrete Math - Mathematics For Computer ScienceDocument339 paginiDiscrete Math - Mathematics For Computer ScienceNungu Sungi100% (1)
- SynonymDocument18 paginiSynonymJeevjyot Singh ChhabdaÎncă nu există evaluări
- Customer Letter - AppleDocument3 paginiCustomer Letter - ApplePramod Govind SalunkheÎncă nu există evaluări
- F5 Configuration - HTTPS WSS OffloadingDocument28 paginiF5 Configuration - HTTPS WSS Offloadingo0000oÎncă nu există evaluări
- Solaris 10 System Administrator Collection System Administration Guide Ip Services PDFDocument820 paginiSolaris 10 System Administrator Collection System Administration Guide Ip Services PDFakdenizerdemÎncă nu există evaluări
- Microsoft Technical Reference Guide For CMMC v2 - (Public Preview) - 20220304Document280 paginiMicrosoft Technical Reference Guide For CMMC v2 - (Public Preview) - 20220304Malik100% (1)
- Step-by-Step Instructions On Using Popplet in Your ClassroomDocument2 paginiStep-by-Step Instructions On Using Popplet in Your ClassroomKawita Letchmanan KawiÎncă nu există evaluări
- ITS Technologies for Improving Transportation SafetyDocument21 paginiITS Technologies for Improving Transportation SafetySumanth BsÎncă nu există evaluări
- Operator's Manual For Arc Welding: Motoman XRC 2001 ControllerDocument436 paginiOperator's Manual For Arc Welding: Motoman XRC 2001 ControllerAnonymous oTrMzaÎncă nu există evaluări
- BE/B1 Student Experiments With RSA Encryption AlgorithmDocument6 paginiBE/B1 Student Experiments With RSA Encryption Algorithmtheconqueror01Încă nu există evaluări
- AadhaarDocument1 paginăAadhaarJayesh ShahÎncă nu există evaluări
- Sharp XE-A203 Elsctronic Cash Register SMDocument31 paginiSharp XE-A203 Elsctronic Cash Register SMDoru RazvanÎncă nu există evaluări
- Nextiva 6 4 AE SpecificationsDocument28 paginiNextiva 6 4 AE SpecificationsAnyi AcevedoÎncă nu există evaluări
- ESE 2020 Notes Basics of Energy and EnvironmentDocument133 paginiESE 2020 Notes Basics of Energy and EnvironmentsubhajitÎncă nu există evaluări
- BMW x3 Brochure November 2017 v2Document22 paginiBMW x3 Brochure November 2017 v2GOKUL PRASADÎncă nu există evaluări
- AR150&160&200&1200&2200&3200 V200R005C00 Configuration Guide - Reliability 01 PDFDocument276 paginiAR150&160&200&1200&2200&3200 V200R005C00 Configuration Guide - Reliability 01 PDFmeryamrezaÎncă nu există evaluări
- Hafiz Muhammad Muazzam: Address: House No. 345 Shamsabad Colony, Multan. Mob: 0332 604 6090 EmailDocument6 paginiHafiz Muhammad Muazzam: Address: House No. 345 Shamsabad Colony, Multan. Mob: 0332 604 6090 EmailHafizMuhammadMuazzamÎncă nu există evaluări
- 4Document284 pagini4YAZAN ABD ALRAZAKÎncă nu există evaluări
- Handbook of Security BlundersDocument10 paginiHandbook of Security BlundersRoger JohnstonÎncă nu există evaluări
- BK&RSA - Page 25 - Programmers PDFDocument11 paginiBK&RSA - Page 25 - Programmers PDFAnonymous e6G8WLNe0% (1)
- Instructions For Haryana State NTSE (Stage-1) 2016.Document2 paginiInstructions For Haryana State NTSE (Stage-1) 2016.Saksham HoodaÎncă nu există evaluări
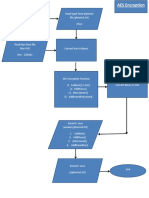
- AES Algorithm Flow ChartDocument3 paginiAES Algorithm Flow Chartchernwei0% (1)
- Introduction To Industrial Security Concept: Computer Arts and Technological College IncDocument19 paginiIntroduction To Industrial Security Concept: Computer Arts and Technological College IncWilliam L. Apuli IIÎncă nu există evaluări
- BMA Innothon SFIMAR Barclays SrudentsDocument2 paginiBMA Innothon SFIMAR Barclays SrudentsMovil MathiasÎncă nu există evaluări
- CIPP:A Blueprint PDFDocument2 paginiCIPP:A Blueprint PDFroruangÎncă nu există evaluări
- BT Buys Counterpane To Boost IT Security Services: ... Continued From Page 1Document1 paginăBT Buys Counterpane To Boost IT Security Services: ... Continued From Page 1s_sarfaraz64Încă nu există evaluări
- SADP User ManualDocument34 paginiSADP User ManualJuan Emilio CucumidesÎncă nu există evaluări
- Digital Lock For Aluminium Door Kaadas SeriesDocument2 paginiDigital Lock For Aluminium Door Kaadas Serieserick jokoÎncă nu există evaluări
- Teacher 02051107103Document17 paginiTeacher 02051107103Pawan KumarÎncă nu există evaluări
- Memo 201412: Official Statement Re System FailureDocument4 paginiMemo 201412: Official Statement Re System FailureAteneo COMELEC100% (1)
- ReviewDocument3 paginiReviewsuperhookup86% (7)
- La Paz National High School Borrower's SlipDocument1 paginăLa Paz National High School Borrower's SlipJeffrey Salinas60% (5)