Documente Academic
Documente Profesional
Documente Cultură
Toymil Coding Theory Ups 434 2010 PDF
Încărcat de
Tân ChipDescriere originală:
Titlu original
Drepturi de autor
Formate disponibile
Partajați acest document
Partajați sau inserați document
Vi se pare util acest document?
Este necorespunzător acest conținut?
Raportați acest documentDrepturi de autor:
Formate disponibile
Toymil Coding Theory Ups 434 2010 PDF
Încărcat de
Tân ChipDrepturi de autor:
Formate disponibile
Algebraic Coding Theory
Michael Toymil
University of Puget Sound
Math 434, Spring 2010
This work is licensed under the Creative Commons Attribution License
http://creativecommons.org/licenses/by/3.0/
1
1 Introduction
Passing Notes
Suppose you are sitting in your British Literature 223 class (suppose real hard...) and you
are handed a note which reads THIS CLPSS IS BORING. You immediately notice the error
in the note, and in addition to wondering how the author of the note ever got into college,
you wonder what the actual intended message was. Very quickly you replace CLPSS with
CLASS and the meaning becomes clear. Youve just applied some coding theory in your
English class by detecting and correcting an error, but how did you do it? In order to detect
and correct the error so quickly, you made three assumptions:
1. That a correct word will be an English word.
2. That the correct word contains ve letters.
3. That it is more likely that only one letter was incorrect as opposed to two or more.
For now, we will ignore the assumption that the correct word should make sense in the con-
text of entire message. Assumption 2 allowed us to make sense of the errant message, but it
does have a weakness. In the above example CLASS was the only English word we could
make by changing one letter in CLPSS, but what if the received word was CLASK ? Now
by changing one letter we can make words like FLASK and CLASP as well as CLASS.
Using only our assumptions (1 and 2) we cannot justify choosing one word over another,
that is, in this case we cannot correct the error. In some cases our two assumptions may
not even let us catch errors, for example if the received word was an English word, but the
wrong one, say GLASS.
The above situation can be thought of as a simple example of interpreting a message with
a decoding algorithm. This is an absolutely crucial process in elds like telecommunication,
electrical engineering, and computing where data is sent over a noisy channel where it may
be altered before it is received. The main aims of Coding Theory are to detect and correct
transmission errors as thoroughly and rapidly, and thus as eciently as possible. Note that
Coding Theory is NOT cryptography, that is it doesnt protect data from malicious eyes.
The typical model of this system is as follows:
Sender (Message) Encoder Channel (Noise) Decoder Receiver (User)
And now with our note-passing example:
Note in thought form CLASS CLPSS CLASS Comprehended note
We will now begin a mathematical treatment of Coding Theory in order to understand the
development of this fascinating (and useful!) eld of study.
1
2 Preliminaries
2.1 Terms
Coding Theory requires some terminology and denitions. Assume the familiar notions of
groups, rings, elds, and Galois Fields with their standard notation. As in linear algebra,
let V (n, q) be the vector space of dimension n over GF(q) containing sequences of length n
over GF(q). For simplicity denote GF(2) by B (for binary).
Let B
n
, for n N be the set of ordered n-tuples with entries in B. Dene the sum in
B
n
component-wise, and note that B
n
is an Abelian group over this operation with the the
identity as the zero sequence and each element as its own inverse. Now for some coding
theory language.
Denition 1. Dene z as the binary n-tuple of all zeroes, and o as the n-tuple of all ones.
Denition 2. A binary block (m, n)-code consists of an encoding function E : B
m
B
n
and a decoding function D : B
n
B
m
. The elements of Im(E) are called code
words.
An example of a code similar to a binary block is the ASCII character set. Each character
is mapped to an element of B
8
in a text le before it is decoded and presented to the user.
Denition 3. If a, b B
n
, we dene the distance d(a, b) between a and b to be:
d(a, b) =
n
i=1
x
i
x
i
= 0 if a
i
= b
i
x
i
= 1 if a
i
= b
i
where a = a
1
a
2
...a
n
and b = b
1
b
2
...b
n
.
For example, if a = 1001 and b = 1100 then d(a, b) = 2. Note d(a, b) = d(b, a) for all a, b
B
n
Denition 4. If a B
n
, dene the weight wt(a) of a as the number of non-zero components
of a.
For example, if a = 11001 then wt(a) = 5.
Lemma 1. If a, b B
n
, then d(a, b) = wt(a + b).
Proof. This is a consequence of addition in B. Let a = a
1
...a
n
and b = b
1
...b
n
. Note for 1
i n, a
i
+b
i
= 1 if and only if a
i
= b
i
. Hence, (a
i
, b
i
) contributes 1 to wt(a+b) if and only if
it contributes 1 to d(a, b).
With the following denition we can understand our note-passing decoding function in
mathematical terms.
Denition 5. The nearest-neighbor decoding principle states that if a word r B
n
is received and it is a code word, then D(r) = r. If r is not a code word, then we take the
distance of r from all of the code words and nd the least distance, call it d. There exists a
code word a, such that d(a, r) = d. If a is the only code word with d(a, r) = d, then D(r) = a.
If there is another code word, say b, such that d(b, r) = d, then there is a decoding failure.
2
When a word of length n is transmitted and k components of this word are incorrect,
we say that k transmission errors have occured. We build an n-tuple by taking a 1 at each
of these k positions and zeros everywhere else, and call an error vector/word, e. Note
wt(e) = k.
Denition 6. An error word e is detected by a code if a + e is not a code word for any
code word a. If a + e is a code word, then e is undetected.
Denition 7. An error word e is corrected by a code if the decoding function D gives
D(b + e) = b for every code word b.
2.2 Elementary Codes
Denition 8. For a given code, let q be the number of individual detectable error words, r
be the number of correctable error words, and s be the total number of error words. Dene
the performance proportions to be P
d
=
q
s
and P
c
=
r
q
.
The proportions dened above will serve as measurements of a codes error-detecting
and error-correcting performance as we examine dierent types of codes. High performance
proportions are desirable.
Example - The Parity Check
One of the rst ways devised to detect an error in a received word was the parity check. A
(m, m+1) parity check is a binary block(m, m+1)-code. The encoding function simply adds
up the components of the input word (an m-tuple) (mod 2) and appends the result to create
a code word (an m+1-tuple). Thus the codewords are always of even weight. The decoding
function can detect all error words of odd weight, since the addition of such a vector to a
code word, would not be a valid code word. An example is shown below
1001001 a = 10010011, e = 10100001, a + e = 00110010
but a + e is not a codeword since wt(a + e) is odd.
Now let us dig a little deeper. Consider the (2, 3) parity check code. E encodes the message
words as follows:
00 000, 01 011, 10 101, 11 110
The set of code words, C is {000, 011, 101, 110} (isomorphic to a subgroup of Z
2
XZ
2
XZ
2
,
in case you were dying for some group theory.)
Let us notice some things. Note that the distance between any two code words in C is
2. There are 3 possible error vectors of weight 1: 001, 010, 100. Any of these error vectors
added to a code word will not produce a code word and are thus all detected. However, any
error vector of weight 2 is a code word, and will thus go undetected. Our decoding function
cannot correct any errors, however, since for a C and e an error vector of weight 1, a + e
will be equidistant from 3 code words, and so we have a decoding failure.
It is clear that the parity check is not a very good code:
P
d
=
1
2
and P
c
= 0
3
However, this example still has some importance. It turns out that it is not a coincidence
that the weight of the detectable errors was less than the minimum distance of C. Error-
correcting capabilities also depend upon the minimum distance between code words. This
is generalized and solidied by the following theorem.
Theorem 1. A code can detect all errors of weight k or less if and only if the minimum
distance between any two code words is k + 1 or more.
Proof. Let C be the set of all code words of length n of a given code.
() First suppose that for all a, b C, d(a, b) k + 1. Let c C be the transmitted code
word and suppose that the channel introduces the error word e with
wt(e) k
Then the received word is c + e and
d(c + e, c) = wt(c + e + c) (Lemma 1)
= wt(e + (c + c)) = wt(e) k
Thus c + e is not in C and therefore e is detected.
() Suppose that the code can detect all error words of weight k or less. That is, for all e
with wt(e) k and a given c C, c +e is not a code word. Now suppose a, b C and that
d(a, b) k. Let e = a +b. Then wt(e) = wt(a +b) = d(a, b) k. Note a +e = a +a +b = b
which is a code word. This proves that e goes undetected, a contradiction. Therefore
d(a, b) k + 1 for all a, b C
Theorem 2. A code can correct all error words of weight k or less, if and only if the
minimum distance between code words is at least 2k + 1 (given that the nearest neighbor
decoding principle holds).
We will omit the proof for the sake of space.
Example - The Binary Repetition Code
Naturally, we want to detect and correct more errors. With the previous theorems in mind
we know we need to increase the minimum distance between code words. One solution is to
simply repeat bits n times. The binary repetition code of length n or BRC(n) is dened
by the encoding function E
0 z, 1 o
Lemma 2. For a given BRC(n), P
d
= 1 and P
c
=
1
2
(for odd n).
Proof. The set of code words is Im(E) = {z, o}. The minimum distance is simply the
distance between these two elements, given by:
d(z, o) = wt(z +o) = wt(o) = n
4
Theorem 1 ensures that the code can detect error words of weight n 1 or less. That is all
of B
n
except z and o. Consequently, the BRC(n) will detect every error word. Thus
P
d
= 1
Now, Theorem 2 gives that BRC(n) can correct errors of weight
n1
2
or less. The total
number of correctable error words, r, can be derived combinatorially by the following:
for i Z such that 1 i (n 1)/2, r =
(n1)/2
i=1
M(i),
where M(i) =
n!
i!(n i)!
is the number of ways to place i ones in an n-tuple with the rest of
the components zero. Some messy work is omitted to show that
r = 2
n1
1
Finally, since the total number of detectable errors is 2
n
2, we have
P
c
=
2
n1
1
2
n
2
=
1
2
for odd n. An interesting result.
It appears error detection and correction performance remains constant as we increase n for
a BRC(n). This seems counter-intuitive, however, as one would expect some compensation
for inating the size of our code words. Indeed, there is a piece of the puzzle missing. It
turns out that as we increase n, the probability of encountering error words with high enough
weights to go uncorrected is very low. We will not address these probabilities here as we are
more concerned by the theory of coding, not the implementation.
Also, there is an optimization problem at hand as we attempt to balance code word length
(and thus transmission time) and correction/detection performance. The optimal code for
a situation depends on many factors including time constraints, algorithm complexity, and
desired robustness of the code. As we continue our treatment of codes, it will be helpful
collect characterizing information of a code in one place so that we may more easily compare
them.
2.3 Measuring and Comparing the Eciency of Codes
Denition 9. An (n, M, d)-code is a code of length n, containing M codewords, and having
minimum distance d.
In coding theory, a good (n, M, d)-code has small n for fast transmissions, large M
to enable a variety of messages, and a large d to correct many errors. The trick is to
optimize these values for each transmission situation. Looking back at our previous examples
note that the BRC(n) is an (n, 2, n)-code and that the (m, m + 1) parity check code is
an (m + 1, 2
m
, 2)code. Moving forward we will use this characterization as well as the
performance proportions to analyze codes.
5
3 Algebraic Coding Theory
3.1 Linear Codes
Denition 10. A subspace L of V (n, q) is called a linear code of length n over F = GF(q).
Lemma 3. The minimum distance d of a linear code L equals the minimum among with
weights of non-zero code words.
This is a result from group codes, which I have chosen to omit the details of.
Let L be a linear code of length n over F. Let k n be the dimension of L over F
and choose a basis
X
1
, X
2
, ..., X
k
of L over F. Then any element in L is of the form
a
1
X
1
+ a
2
X + ... + a
k
X
k
that is, a linear combination of the basis elements. A message vector a = (a
1
a
2
...a
k
) is thus
encoded. A [n, k, d] linear code has length n, dimension k, and minimum distance d.
Example - A linear Code
Examine the linear code L of length over B with basis
B = {
1
1
0
0
0
1
1
1
1
0
1
0
}
then the encoding function maps the message words using linear combinations of elements
of B as follows:
000 0000, 001 1010, 010 0111, 100 1100, 110 1011, 101 0110, 011 1101, 111 0001
Notice that the set of code words is thus generated by B. Note the minimum distance is 1
since wt(0001) = 1. Thus L is a (4, 8, 1)-code and a [4, 3, 1] linear code.
P
d
= P
c
= 0
Lemma 4. If L is a [n, k, d] linear code over F, then d n k + 1.
Assuming that linear codes exist such that d = n k + 1, let L be such a [n, k, d] linear
code over B. Then L is an (n, 2
k
, n k + 1)code that can thus detect error words of weight
n k or less and correct error words of weight
nk1
2
or less.
6
3.2 Cyclic Codes
Cyclic codes are special sub-class of Linear Codes. They oer a rich algebraic structure as well
as practical advantages in eciency. Unfortunately their performance will not be analyzed
in general here, as nding lower bounds on the minimum distance is a lengthy process.
Instead, we will explore a nice connection between cyclic codes and ideals of polynomial
rings to illustrate the potential for algebra in coding theory.
Denition 11. A linear code L of length n over B is called cyclic if any cyclic shift of a
code word is again a code word, i.e, if (a
0
, a
1
, ..., a
n1
) L then (a
n1
, a
0
, ..., a
n2
) L
An Algebraic Description of Cyclic Codes
Dene a map
: V (n, 2) B[x]/x
n
1
where x
n
1 denotes the ideal of the polynomial ring B[x] generated by x
n
1,by
(a
0
, a
1
, ..., a
n1
) = a
0
+ a
1
x + ... + a
n1
x
n1
+x
n
1
Observe that B[x]/x
n
1 is also a vector space over B (a subspace of vector space of
polynomials over B). It is easy to show is a vector space isomorphism. Let L be a linear
code of length n over B, i.e. L is a subspace of V (n, q). Then, because is an isomorphism
Im(L) is a subspace of B[x]/x
n
1. Let (a
0
, a
1
, ..., a
n1
) L. Then (a
n1
, a
0
, ..., a
n2
) L
if and only if
a
n1
+ a
0
x + ... + a
n2
x
n1
+x
n
1 = x(a
0
+ a
1
x + ... + a
n1
x
n1
) +x
n
1
is in Im(L). Denote a
0
+ a
1
x + ... + a
n1
x
n1
= f(x). Then if both f(x) and xf(x) are in
Im(L), x
2
f(x) is in Im(L) and for 0 i n 1, x
i
f(x) is in Im(L). Since Im(L) is a
vector space, any linear combination of the vectors f(x), xf(x), ..., x
n1
f(x) is also in Im(L).
Therefore, for every polynomial p(x) = b
0
+ b
1
x + ... + b
n1
x
n1
in B[x],
p(x)f(x) = (b
0
+ b
1
x + ... + b
n1
x
n1
)f(x) = b
0
f(x) + b
1
xf(x) + ... + b
n1
x
n1
f(x)
which is a sum of elements of Im(L) and is thus in Im(L).
Hence, Im(L) is an ideal in B[x]/x
n
1
And we can thus regard L as an ideal of B[x]/x
n
1.
This generalizes easily to the ring of polynomials over any nite eld.
3.3 CRC32 - A real-world example
If I may break from strict mathematical rigor for a moment, Id like to point out the kind of
coding performance that is possible using a real-world example, the cyclic redundancy check
or CRC, which is used to encode messages over a wireless ethernet.
7
Cyclic Codes in Terms of Polynomials
We can oer a second denition a cyclic code in terms of a generator polynomial P(x) of
degree n k, by stating that a polynomial of degree less than n is a code polynomial if and
only if it is divisible by P(x), with x
n
1 evenly divisible by P(x). Note that this is a group
code since the sum of two code polynomials will be divisible by P(x).
With this denition we could form code polynomials simply by multiplying our message
polynomials by a suitable P(x). However, in a real transmission situation, this would convo-
lute our data thus making decoding computationally expensive. The following clever method
of encoding is implemented by the CRC.
A CRC code forms code polynomials in which high-order coecients are the message
symbols and low-order coecients are check symbols, which behave much like the parity
check bits do. To encode a message polynomial M(x) of degree k, we divide x
nk
M(x) by a
generator polynomial P(x) of degree n k, and then add the remainder R(x) to x
nk
M(x).
The result
F(x) = x
nk
M(x) + R(x) = Q(x)P(x)
is a code polynomial since it is divisible by P(x).
To check for errors, all we need to do is divide the code polynomial by P(x) and check
to see that the remainder is zero. If so, we assume the message is error-free and we pull o
the k high-order coecients that represent the original message.
The standard CRC-32 code uses the generator polynomial
x
32
+ x
26
+ x
23
+ x
22
+ x
16
+ x
12
+ x
11
+ x
10
+ x
8
+ x
7
+ x
5
+ x
4
+ x
2
+ x + 1
This code has remarkable error-detection properties. For only adding 32 bits onto the
message word, the following are gained:
1. All errors of weight 1 are detected.
2. All burst errors of length 31 or less are detected.
3. All errors of odd weight are detected.
4. Will detect a fraction of 1 2
32
of ALL longer error bursts.
4 Conclusion
In this paper we developed a broad sense of the purpose and practice of Coding Theory.
The general feel of things is that you cannot get all of the best performance traits out of a
single code. Developing codes is a balancing act of redundancy and eciency. With the aid
of Abstract and Linear Algebra, the search for the optimal code is made much more precise.
Youll never think about that phone call or text message the same way again!
8
References
1. Peterson, W. W. and Brown, D. T. (January 1961). Cyclic Codes for Error Detec-
tion. Proceedings of the IRE 49: 228.
2. CRC-32 on http://www.wikipedia.com/
3. Hill, R. A First Course in Coding Theory, Oxford, New York, 1986.
4. Judson, Abstract Algebra: Theory and Applications, 1997.
5. Vermani, L. R. Elements of Algebraic Coding Theory, Chapman and Hall, London,
UK, 1996.
6. C.J.Salwach, Codes That Detect and Correct Errors, The College Mathematics Journal,
Vol. 19, No. 5 (Nov., 1988), pp. 402-416
S-ar putea să vă placă și
- Mobile IPDocument4 paginiMobile IPTân ChipÎncă nu există evaluări
- ProjectReport PDFDocument23 paginiProjectReport PDFTân ChipÎncă nu există evaluări
- Wednesday, October 28, 2015 11:34 AM: Lab RF Page 1Document2 paginiWednesday, October 28, 2015 11:34 AM: Lab RF Page 1Tân ChipÎncă nu există evaluări
- Wednesday, October 28, 2015 11:34 AM: Lab RF Page 1Document2 paginiWednesday, October 28, 2015 11:34 AM: Lab RF Page 1Tân ChipÎncă nu există evaluări
- Mach in PDFDocument1 paginăMach in PDFTân ChipÎncă nu există evaluări
- TIM NotesDocument7 paginiTIM NotesTân ChipÎncă nu există evaluări
- Communication NetworkDocument1 paginăCommunication NetworkTân ChipÎncă nu există evaluări
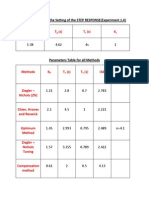
- Parameters From The Setting of The STEP RESPONSE (Experiment 1.4)Document1 paginăParameters From The Setting of The STEP RESPONSE (Experiment 1.4)Tân ChipÎncă nu există evaluări
- MATLAB-Hamming CodesDocument6 paginiMATLAB-Hamming CodesTân ChipÎncă nu există evaluări
- Science Magazine 5684 2004-07-30Document92 paginiScience Magazine 5684 2004-07-30th222bpÎncă nu există evaluări
- Science Magazine 5694 2004-10-08 PDFDocument89 paginiScience Magazine 5694 2004-10-08 PDFTân ChipÎncă nu există evaluări
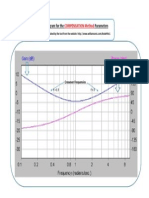
- BODE Diagramm For The COMPENSATION Method ParametersDocument1 paginăBODE Diagramm For The COMPENSATION Method ParametersTân ChipÎncă nu există evaluări
- Some Basic Block Codes - 2804Document3 paginiSome Basic Block Codes - 2804Tân ChipÎncă nu există evaluări
- Event: Selectionchanged: Callback Files Generated by Guide: - Code Files (.M) and FIG-Files (.Fig)Document1 paginăEvent: Selectionchanged: Callback Files Generated by Guide: - Code Files (.M) and FIG-Files (.Fig)Tân ChipÎncă nu există evaluări
- I2C TestDocument3 paginiI2C TestTân ChipÎncă nu există evaluări
- Eula Microsoft Visual StudioDocument3 paginiEula Microsoft Visual StudioqwwerttyyÎncă nu există evaluări
- MSP430 C Compiler Programming GuideDocument242 paginiMSP430 C Compiler Programming Guidecharles_sieÎncă nu există evaluări
- 1.1.1 Reed - Solomon Code:: C F (U, U, , U, U)Document4 pagini1.1.1 Reed - Solomon Code:: C F (U, U, , U, U)Tân ChipÎncă nu există evaluări
- Decoding of Convolutional CodesDocument3 paginiDecoding of Convolutional CodesTân ChipÎncă nu există evaluări
- Eula Microsoft Visual StudioDocument3 paginiEula Microsoft Visual StudioqwwerttyyÎncă nu există evaluări
- Eula Microsoft Visual StudioDocument3 paginiEula Microsoft Visual StudioqwwerttyyÎncă nu există evaluări
- Eula Microsoft Visual StudioDocument3 paginiEula Microsoft Visual StudioqwwerttyyÎncă nu există evaluări
- Eula Microsoft Visual StudioDocument3 paginiEula Microsoft Visual StudioqwwerttyyÎncă nu există evaluări
- Makalah Penelitian Tentang LingkunganDocument1 paginăMakalah Penelitian Tentang LingkunganDedi IrhandiÎncă nu există evaluări
- Versuch 5: in Simulation Using Serial InterfaceDocument1 paginăVersuch 5: in Simulation Using Serial InterfaceTân ChipÎncă nu există evaluări
- Eula Microsoft Visual StudioDocument3 paginiEula Microsoft Visual StudioqwwerttyyÎncă nu există evaluări
- Eula Microsoft Visual StudioDocument3 paginiEula Microsoft Visual StudioqwwerttyyÎncă nu există evaluări
- Coding TheoryDocument67 paginiCoding Theorytrungnv2803Încă nu există evaluări
- Aata 20110810Document438 paginiAata 20110810Tram VoÎncă nu există evaluări
- The Subtle Art of Not Giving a F*ck: A Counterintuitive Approach to Living a Good LifeDe la EverandThe Subtle Art of Not Giving a F*ck: A Counterintuitive Approach to Living a Good LifeEvaluare: 4 din 5 stele4/5 (5794)
- The Little Book of Hygge: Danish Secrets to Happy LivingDe la EverandThe Little Book of Hygge: Danish Secrets to Happy LivingEvaluare: 3.5 din 5 stele3.5/5 (400)
- Shoe Dog: A Memoir by the Creator of NikeDe la EverandShoe Dog: A Memoir by the Creator of NikeEvaluare: 4.5 din 5 stele4.5/5 (537)
- Hidden Figures: The American Dream and the Untold Story of the Black Women Mathematicians Who Helped Win the Space RaceDe la EverandHidden Figures: The American Dream and the Untold Story of the Black Women Mathematicians Who Helped Win the Space RaceEvaluare: 4 din 5 stele4/5 (895)
- The Yellow House: A Memoir (2019 National Book Award Winner)De la EverandThe Yellow House: A Memoir (2019 National Book Award Winner)Evaluare: 4 din 5 stele4/5 (98)
- The Emperor of All Maladies: A Biography of CancerDe la EverandThe Emperor of All Maladies: A Biography of CancerEvaluare: 4.5 din 5 stele4.5/5 (271)
- A Heartbreaking Work Of Staggering Genius: A Memoir Based on a True StoryDe la EverandA Heartbreaking Work Of Staggering Genius: A Memoir Based on a True StoryEvaluare: 3.5 din 5 stele3.5/5 (231)
- Never Split the Difference: Negotiating As If Your Life Depended On ItDe la EverandNever Split the Difference: Negotiating As If Your Life Depended On ItEvaluare: 4.5 din 5 stele4.5/5 (838)
- Grit: The Power of Passion and PerseveranceDe la EverandGrit: The Power of Passion and PerseveranceEvaluare: 4 din 5 stele4/5 (588)
- On Fire: The (Burning) Case for a Green New DealDe la EverandOn Fire: The (Burning) Case for a Green New DealEvaluare: 4 din 5 stele4/5 (74)
- Elon Musk: Tesla, SpaceX, and the Quest for a Fantastic FutureDe la EverandElon Musk: Tesla, SpaceX, and the Quest for a Fantastic FutureEvaluare: 4.5 din 5 stele4.5/5 (474)
- Devil in the Grove: Thurgood Marshall, the Groveland Boys, and the Dawn of a New AmericaDe la EverandDevil in the Grove: Thurgood Marshall, the Groveland Boys, and the Dawn of a New AmericaEvaluare: 4.5 din 5 stele4.5/5 (266)
- The Unwinding: An Inner History of the New AmericaDe la EverandThe Unwinding: An Inner History of the New AmericaEvaluare: 4 din 5 stele4/5 (45)
- Team of Rivals: The Political Genius of Abraham LincolnDe la EverandTeam of Rivals: The Political Genius of Abraham LincolnEvaluare: 4.5 din 5 stele4.5/5 (234)
- The World Is Flat 3.0: A Brief History of the Twenty-first CenturyDe la EverandThe World Is Flat 3.0: A Brief History of the Twenty-first CenturyEvaluare: 3.5 din 5 stele3.5/5 (2259)
- The Gifts of Imperfection: Let Go of Who You Think You're Supposed to Be and Embrace Who You AreDe la EverandThe Gifts of Imperfection: Let Go of Who You Think You're Supposed to Be and Embrace Who You AreEvaluare: 4 din 5 stele4/5 (1090)
- The Hard Thing About Hard Things: Building a Business When There Are No Easy AnswersDe la EverandThe Hard Thing About Hard Things: Building a Business When There Are No Easy AnswersEvaluare: 4.5 din 5 stele4.5/5 (344)
- The Sympathizer: A Novel (Pulitzer Prize for Fiction)De la EverandThe Sympathizer: A Novel (Pulitzer Prize for Fiction)Evaluare: 4.5 din 5 stele4.5/5 (121)
- Her Body and Other Parties: StoriesDe la EverandHer Body and Other Parties: StoriesEvaluare: 4 din 5 stele4/5 (821)
- English MCQs For UGC NET - True Blue GuideDocument13 paginiEnglish MCQs For UGC NET - True Blue GuideTrue Blue GuideÎncă nu există evaluări
- Free PDF Reader Sony Ericsson w595Document2 paginiFree PDF Reader Sony Ericsson w595AdamÎncă nu există evaluări
- Chapter 3 Roots of EquationDocument57 paginiChapter 3 Roots of EquationJosafet Gutierrez MasaoayÎncă nu există evaluări
- Excel TrainingDocument23 paginiExcel TrainingsefanitÎncă nu există evaluări
- Cungte's ThesisDocument84 paginiCungte's Thesisapi-3804018Încă nu există evaluări
- Adjective Adverb Worksheets 2 - GrammarBankDocument3 paginiAdjective Adverb Worksheets 2 - GrammarBankNilson Guevara BenavidesÎncă nu există evaluări
- So..that... - Such... That...Document5 paginiSo..that... - Such... That...Ristia Nurul KamilaÎncă nu există evaluări
- TensesDocument2 paginiTensesMarcu RaileanÎncă nu există evaluări
- SPFX NotesDocument9 paginiSPFX NotespriyakantbhaiÎncă nu există evaluări
- Obedience (Beginner 1 B) .A1 Movers 9 Test 3 Reading & Writing (P 1-6) .Document19 paginiObedience (Beginner 1 B) .A1 Movers 9 Test 3 Reading & Writing (P 1-6) .Umroh SyafitriÎncă nu există evaluări
- 11. प्रशासन - प्रशासन-यातायात व्यवस्थापन सहायक तह ४Document7 pagini11. प्रशासन - प्रशासन-यातायात व्यवस्थापन सहायक तह ४Karna RishavÎncă nu există evaluări
- Sports: Fill in The Crossword and Find The Hidden WordsDocument2 paginiSports: Fill in The Crossword and Find The Hidden WordsArturo Fuentes BravoÎncă nu există evaluări
- OGG Best Practice Configuring OGG Monitor v07Document39 paginiOGG Best Practice Configuring OGG Monitor v07Naresh SundaraneediÎncă nu există evaluări
- LBS CodeDocument9 paginiLBS CodeKishore Kumar RaviChandranÎncă nu există evaluări
- About PronounsDocument2 paginiAbout PronounsLawrence OrqueroÎncă nu există evaluări
- Data Strucuture McqsDocument8 paginiData Strucuture McqsDr ManiÎncă nu există evaluări
- EE329 Summary 1Document5 paginiEE329 Summary 1Uji CobaÎncă nu există evaluări
- MacKenzie - Vanguard Lying DownDocument7 paginiMacKenzie - Vanguard Lying DownSergey MinovÎncă nu există evaluări
- Process Description and ControlDocument42 paginiProcess Description and ControlPaolo LegaspiÎncă nu există evaluări
- Joblana Test (JL Test) English Section Sample PaperDocument4 paginiJoblana Test (JL Test) English Section Sample PaperLots infotechÎncă nu există evaluări
- Master SymbolDocument3 paginiMaster Symbolapi-26172340100% (1)
- PDF Export User Guide v10Document22 paginiPDF Export User Guide v10rfffffÎncă nu există evaluări
- Lua Programming - Syntax, Concep - Alexander AronowitzDocument382 paginiLua Programming - Syntax, Concep - Alexander Aronowitzbearmiinator100% (2)
- English Phonetics - Task 2 - Practical Exercises FINISHED WITH LINKDocument4 paginiEnglish Phonetics - Task 2 - Practical Exercises FINISHED WITH LINKjonathanmplusÎncă nu există evaluări
- CV - Muhsin Mashkur-1Document7 paginiCV - Muhsin Mashkur-1Mokhter AhmadÎncă nu există evaluări
- Articles CommonDocument2 paginiArticles CommonAbdullah Al MamunÎncă nu există evaluări
- Koi Desh PunjaboN Sohna NaDocument12 paginiKoi Desh PunjaboN Sohna Nahirdaypallsingh2241Încă nu există evaluări
- Priority Queues With Simple Queue ServiceDocument6 paginiPriority Queues With Simple Queue Servicelokenders801Încă nu există evaluări
- Dokumen - Tips Yue Liang Dai Biao Wo de Xin Fingerstyle TabDocument3 paginiDokumen - Tips Yue Liang Dai Biao Wo de Xin Fingerstyle TabChristian NathanÎncă nu există evaluări
- WebDocument2 paginiWebHazimah SabarudinÎncă nu există evaluări