Documente Academic
Documente Profesional
Documente Cultură
Chapter 4: Introduction To TCP/IP Protocols: Objectives
Încărcat de
shahzaibarshad66Descriere originală:
Titlu original
Drepturi de autor
Formate disponibile
Partajați acest document
Partajați sau inserați document
Vi se pare util acest document?
Este necorespunzător acest conținut?
Raportați acest documentDrepturi de autor:
Formate disponibile
Chapter 4: Introduction To TCP/IP Protocols: Objectives
Încărcat de
shahzaibarshad66Drepturi de autor:
Formate disponibile
Chapter 4: Introduction to TCP/IP Protocols
Objectives
Identify and explain the functions of the core TCP/IP protocols
Explain how the TCP/IP protocols correlate to layers of the OSI model
Discuss addressing schemes for TCP/IP in IPv4 and IPv6 protocols
Describe the purpose and implementation of DNS (Domain Name System) and DHCP (Dynamic Host
Configuration Protocol)
Identify the well-known ports for key TCP/IP services
Describe common Application layer TCP/IP protocols
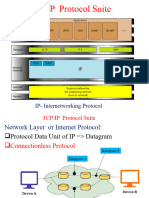
Characteristics of TCP/IP (Transmission Control Protocol/ Internet Protocol)
Protocol Suite
TCP/IP
Subprotocols
TCP, IP, UDP, ARP
Developed by Department of Defense
ARPANET (1960s)
Internet precursor
Popularity
Low cost
Communicates between dissimilar platforms
Open nature
Routable
Spans more than one LAN (LAN segment)
Flexible
Runs on combinations of network operating systems or network media
Disadvantage: requires more configuration
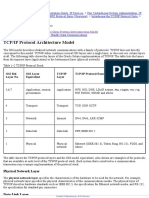
The TCP/IP Core Protocols
TCP/IP suite subprotocols
Operates in Transport or Network layers of OSI model
Provide basic services to protocols in other layers
Most significant protocols in TCP/IP
TCP
IP
TCP (Transmission Control Protocol)
Transport layer protocol
Provides reliable data delivery services
Connection-oriented subprotocol
Establish connection before transmitting, with the TCP Handshake
Sequencing and checksums
Flow control
Transmitter waits for ACK before sending more
TCP segment format
Encapsulated by IP datagram in Network layer
Becomes IP datagrams data
CNIT 106 Bowne
Page 1 of 21
Chapter 4: Introduction to TCP/IP Protocols
TCP Segment
Important TCP Header Fields
Flags, especially SYN and ACK
Indicates purpose of segment
Source Port and Destination Port
Guides data to the correct process on the destination computer
SEQ number and ACK number
Used to arrange
segments in the
correct order
TCP Handshake
Computer A sends SYN to Computer B
SYN flag set
SEQ field: Random initial sequence
number (ISN)
ACK field: Empty (zeroes)
Computer B replies with SYN/ACK
SYN and ACK
flags set
SEQ field: Computer B's random initial
sequence number (ISN)
ACK field: Computer A's ISN plus 1
Computer A responds with ACK
ACK flag set
SEQ field: Computer A's ISN plus 1
ACK field: Computer B's ISN plus 1
Ending a TCP Session
FIN flag indicates transmission end
CNIT 106 Bowne
Page 2 of 21
Chapter 4: Introduction to TCP/IP Protocols
Wireshark Demonstration
Relative SEQ and ACK numbers at top
Absolute SEQ and ACK values at bottom, in hexadecimal
UDP (User Datagram Protocol)
Transport layer
protocol
Provides unreliable
data delivery
services
Connectionless
transport service
No assurance
packets received
in correct
sequence
No guarantee
packets received
at all
No error checking,
sequencing
Lacks sophistication
More efficient than TCP
Useful situations
Great volume of data transferred quickly
CNIT 106 Bowne
Page 3 of 21
Chapter 4: Introduction to TCP/IP Protocols
IP (Internet Protocol)
Network layer protocol
Routes packets using IP addresses
Enables TCP/IP to internetwork
Routers move IP packets move from one network to another
Unreliable, connectionless protocol
No guaranteed data delivery, no handshake
Some higher level protocols provide reliability, like TCP
Important IP Header Fields
TTL (Time to Live)
Decreases by one for each router the packet passes through (a "hop")
When TTL reaches zero, the packet is discarded
Source Destination IP Addresses
Used to deliver packet and response
ICMP (Internet Control Message Protocol)
Network layer protocol
Reports on data delivery success/failure
Announces transmission failures to sender
Network congestion
Data fails to reach destination
Data discarded: TTL expired
ICMP cannot correct errors
Provides critical network problem troubleshooting information
IGMP (Internet Group Management Protocol)
Network layer protocol
Manages multicasting
Allows one node to send data to defined group of nodes
Uses
Internet teleconferencing
Routers sending traffic reports to each other
CNIT 106 Bowne
Page 4 of 21
Chapter 4: Introduction to TCP/IP Protocols
ARP (Address Resolution Protocol)
Network layer protocol
Obtains a MAC address from an IP address
ARP table (ARP cache)
Computers store recently-used MAC-to-IP address mappings
Increases efficiency
Controlled by ARP command
ARP Demonstration
ARP -D *
Clears
the
ARP cache
ARP -A
Shows the ARP cache
S
RARP (Reverse Address Resolution Protocol)
Converts MAC address to IP Address
Obsoletereplaced by DHCP
IPv4 Addressing
IPv4 Addressing
Networks recognize two addresses
Logical (Network layer)
Physical (MAC, hardware) addresses
IP protocol handles logical addressing
Specific parameters
Unique 32-bit number
Divided into four octets (sets of eight bits)
Separated by periods
Example: 144.92.43.178
IP address information
CNIT 106 Bowne
Page 5 of 21
Chapter 4: Introduction to TCP/IP Protocols
Network Class determined by first octet
Class A, Class B, Class C
Class D, Class E rarely used (never assign)
Class D: value between 224 and 230
Multicasting
Class E: value between 240 and 254
Experimental use
CNIT 106 Bowne
Page 6 of 21
Chapter 4: Introduction to TCP/IP Protocols
Eight bits have 256 combinations
Networks use 1 through 254
0: reserved as placeholder
10.0.0.0
255: reserved for broadcast transmission
255.255.255.255
Class A devices
Share same first octet (bits 0-7)
Network ID
Host: second through fourth octets (bits 8-31)
Class B devices
Share same first two octet (bits 0-15)
Host: second through fourth octets (bits 16-31)
Class C devices
Share same first three octet (bits 0-23)
Host: second through fourth octets (bits 24-31)
Running out of addresses
Loop back address
Loopback test
Windows XP, Vista
Unix, Linux
CNIT 106 Bowne
IPv6 incorporates new addressing scheme
First octet equals 127 (127.0.0.1)
Attempting to connect to own machine
Powerful troubleshooting tool
ipconfig command
ifconfig command
Page 7 of 21
Chapter 4: Introduction to TCP/IP Protocols
Binary and Dotted Decimal Notation
Decimal number between 0 and 255 represents each binary octet
Period (dot) separates each decimal
Dotted decimal address has binary equivalent
Converting each octet
Remove decimal points
Subnet Mask
Identifies every device on TCP/IP-based network
32-bit number (net mask)
Identifies devices subnet
Combines with device IP address
Informs network about segment, network where device attached
Four octets (32 bits)
Expressed in binary or dotted decimal notation
Assigned same way as IP addresses
Manually, or automatically (via DHCP)
Subnetting
Subdividing network single class into multiple, smaller logical networks
(segments)
Control network traffic
Make best use of limited number of IP addresses
Subnet mask varies depending on subnetting
Nonsubnetted networks use defaults
Assigning IP Addresses
Government-sponsored organizations
Dole out IP address blocks to companies
IANA, ICANN, RIRs
Companies, individuals
Obtain IP addresses from ISPs
Every network node must have unique IP address
Otherwise it cannot send or receive Internet packets
Static and Automatic IP Address Assignment
Static IP address
Manually typed into each device
Modify client workstation TCP/IP properties
Only way to change
Human error cause duplicates
Automatic IP addressing
BOOTP and DHCP
Reduce duplication error
CNIT 106 Bowne
Page 8 of 21
Chapter 4: Introduction to TCP/IP Protocols
BOOTP (Bootstrap Protocol)
Mid-1980s
Application layer protocol
Central list
IP addresses, associated devices MAC addresses
Assign client IP addresses dynamically
Dynamic IP address
Assigned to device upon request
Changeable
BOOTP process
Client connects to network
Sends broadcast message asking for IP address
Includes clients NIC MAC address
BOOTP server looks up clients MAC address in BOOTP table
Responds to client
Clients IP address
Server IP address
Server host name
Default router IP address
Process resembles RARP
Difference
RARP requests, responses not routable
RARP only capable of issuing IP address to client
BOOTP may issue additional information (clients subnet mask)
BOOTP surpassed by DHCP (Dynamic Host Configuration Protocol)
More sophisticated IP addressing utility
DHCP requires little intervention
BOOTP difficult to maintain on large networks
DHCP (Dynamic Host Configuration Protocol)
Assigns network device unique IP address
Automatically
Application layer protocol
Developed by IETF (BOOTP replacement)
Operation
Similar to BOOTP
Lower administrative burden
Administrator does not maintain table
Requires DHCP service on DHCP server
Reasons to Use DHCP
Saves time spent assigning IP addresses
Prevents accidental duplicate IP addresses
Allows users to move devices (like laptops) without having to change their TCP/IP configuration
CNIT 106 Bowne
Page 9 of 21
Chapter 4: Introduction to TCP/IP Protocols
DHCP Leasing Process
Device borrows (leases) IP address
Devices use IP address temporarily
Specified time limit
Lease time
Determine when client obtains IP address at log on
User may force lease termination
DHCP service configuration
Specify leased address range
Configure lease duration
Several steps to negotiate clients first lease
Terminating a DHCP Lease
Lease expiration
Automatic
Established in server configuration
Manually terminated at any time
Clients TCP/IP configuration
Servers DHCP configuration
Circumstances requiring lease termination
DHCP server fails and replaced
Windows: release of TCP/IP settings
DHCP services run on several server types
Installation and configurations vary
CNIT 106 Bowne
Page 10 of 21
Chapter 4: Introduction to TCP/IP Protocols
APIPA (Automatic Private IP Addressing)
Client cannot communicate without valid IP address
What if DHCP server not running?
Microsoft Windows offers Automatic Private IP Addressing
Provides IP address automatically
IANA (Internet Assigned Numbers Authority) reserved predefined pool of addresses
169.254.0.0 through 169.254.255.255
APIPA
Assigns a random IP address from the 169.254.y.x range
Assigns default Class B subnet mask
255.255.0.0
Disadvantage
Computer only communicates with other nodes using addresses in APIPA
range
Cannot normally connect to the Internet with a 169.254.y.z address
APIPA suitable use
Small networks: no DHCP servers
APIPA unsuitable use
Networks communicating with other subnets, WAN
APIPA enabled by default: OK
First checks for DHCP server
Allows DHCP server to assign addresses
Does not reassign new address if static
Works with DHCP clients
Disabled in registry
IPv6 Addressing
IP next generation (IPng)
IPv6 support
Delay in implementation
IPv6 advantages
Replacing IPv4 (gradually)
Most new applications, servers, network devices
Cost of upgrading infrastructure
More efficient header, better security, better prioritization provisions,
automatic IP address configuration
Billions of additional IP addresses
Difference between IPv4 and IPv6 addresses
Size
IPv4: 32 bits
IPv6: eight 16-bit fields (128 bits)
IPv6: 296 (4 billion times 4 billion times 4 billion) available IP addresses
Representation
IPv4: binary numbers separated by period
IPv6: hexadecimal numbers separated by colon
IPv6 shorthand: :: any number of multiple, zero-value fields
CNIT 106 Bowne
Page 11 of 21
Chapter 4: Introduction to TCP/IP Protocols
Demo: IPv6 Addresses in Windows 7
US Government requires IPv6 compatibility on its devices now
Links Ch 4f, 4g
Difference between IPv4 and IPv6 addresses (contd.)
Representation (contd.)
IPv6 loopback address is 0:0:0:0:0:0:0:1
Abbreviated loopback address ::1
Scope
IPv6 addresses can reflect scope of transmissions recipients
Unicast address represents single device interface
Multicast address represents multiple interfaces (often on multiple devices)
Difference between IPv4 and IPv6 addresses (contd.)
Scope (contd.)
Anycast address represents any one interface from a group of interfaces
Any one can accept transmission
Format Prefix (IPv6)
Beginning of address
Variable-length field
Indicates address type: unicast, multicast, anycast
Sockets and Ports
Processes assigned unique port numbers
Processs socket
Port number plus host machines IP address
Port numbers
Simplify TCP/IP communications
Ensures data transmitted correctly
Example
Telnet port number: 23
IPv4 host address: 10.43.3.87
Socket address: 10.43.3.87:23
Port number range: 0 to 65535
Three types
Well Known Ports
Range: 0 to 1023
Operating system or administrator use
Registered Ports
CNIT 106 Bowne
Page 12 of 21
Chapter 4: Introduction to TCP/IP Protocols
Range: 1024 to 49151
Network users, processes with no special privileges
Dynamic and/or Private Ports
Range: 49152 through 65535
No restrictions
Using Non-Standard Ports
A server could be configured to use an unusual port, such as a Web server on port 8080
Not good idea: standards violation
Sometimes done for security or testing
Host Names and DNS (Domain Name System)
TCP/IP addressing
Long, complicated numbers
Good for computers
People remember words better
Internet authorities established Internet node naming system
Host
Internet device
CNIT 106 Bowne
Page 13 of 21
Chapter 4: Introduction to TCP/IP Protocols
Host name
Name describing device
Group of computers belonging to same organization
Share common part of IP address
Domain Names
Domain
Domain name
Identifies domain (loc.gov)
Associated with company, university, government organization
Fully qualified host name (jasmine.loc.gov)
Local host name plus domain name
Label (character string)
Separated by dots
Represents level in domain naming hierarchy
Example: www.google.com
Top-level domain (TLD): com
Second-level domain: google
Third-level domain: www
Second-level domain
May contain multiple third-level domains
CNIT 106 Bowne
Page 14 of 21
Chapter 4: Introduction to TCP/IP Protocols
ICANN established domain naming conventions
ICANN approved over 240 country codes
Host and domain names restrictions
Any alphanumeric combination up to 63 characters
Include hyphens, underscores, periods in name
No other special characters
Hosts Files
ARPAnet used HOSTS.TXT file
Associated host names with IP addresses
Host matched by one line
Identifies hosts name, IP address
Alias provides nickname
UNIX-/Linux-based
computer
Host file called hosts, located in the /etc directory
Windows 9x, NT, 2000, XP, Vista computer
Host file called hosts
Located in %systemroot%\system32\drivers\etc folder
Windows Hosts File
Rarely used, but still present
DNS (Domain Name System)
Hierarchical Distributed Database
Associates domain names with IP addresses
DNS refers to:
Application layer service accomplishing association
Organized system of computers; databases making association possible
DNS redundancy
Many computers across globe related in hierarchical manner
Root servers
13 computers (ultimate authorities)
Name servers (DNS servers)
Servers that contain databases of associated names, IP addresses
Provide information on request
To convert names like www.ccsf.edu into IP addresses like 147.144.1.212
CNIT 106 Bowne
Page 15 of 21
Chapter 4: Introduction to TCP/IP Protocols
This process is called name resolution
CNIT 106 Bowne
Page 16 of 21
Chapter 4: Introduction to TCP/IP Protocols
Resource record
Dependent on function
Name field
Type field
Class field
Time to Live field
CNIT 106 Bowne
Describes one piece of DNS database information
Many different types
Contents
Page 17 of 21
Chapter 4: Introduction to TCP/IP Protocols
Data length field
Actual data
Demo: CCSFs Name Servers
Configuring DNS
Large organizations
Often maintain two name servers
Primary and secondary
Ensures Internet connectivity
Each device must know how to find server
Automatically by DHCP
Manually configure workstation TCP/IP properties
DDNS (Dynamic DNS)
Allows a user to host a Web site on a computer with a dynamic IP address
Process
Service provider runs program on users computer
Notifies service provider when IP address changes
Service providers server launches routine to automatically update DNS
record
Effective throughout Internet in minutes
Not as good as a real static IP address
Larger organizations pay for statically assigned IP address
Application Layer Protocols
Work over TCP or UDP plus IP
Translate user requests
Into format readable by network
HTTP
Application layer protocol central to using Web
BOOTP and DHCP
Automatic address assignment
CNIT 106 Bowne
Page 18 of 21
Chapter 4: Introduction to TCP/IP Protocols
Telnet
Terminal emulation protocol
Log on to remote hosts
Using TCP/IP protocol suite
TCP connection established
Keystrokes on users machine act like keystrokes on remotely connected machine
Often connects two dissimilar systems
Can control remote host
Drawback
Notoriously insecure
FTP (File Transfer Protocol)
Send and receive files via TCP/IP
Host running FTP server portion
Accepts commands from host running FTP client
FTP commands
Operating systems command prompt
No special client software required
FTP hosts allow anonymous logons
After connected to host
Additional commands available
Type help
Graphical FTP clients
MacFTP, WS_FTP, CuteFTP, SmartFTP
Rendered command-line method less common
FTP file transfers directly from modern Web browser
Point browser to FTP host
Move through directories, exchange files
SFTP
More secure
TFTP (Trivial File Transfer Protocol)
Enables file transfers between computers
Simpler (more trivial) than FTP
TFTP relies on Transport layer UDP
Connectionless
Does not guarantee reliable data delivery
No ID and password required
Security risk
No directory browsing allowed
Useful to load data, programs on diskless workstation
Used to put software on IP phones and routers
NTP (Network Time Protocol)
Synchronizes network computer clocks
Depends on UDP Transport layer services
Benefits from UDPs quick, connectionless nature
Time sensitive
Cannot wait for error checking
Time synchronization importance
Routing
Time-stamped security methods
CNIT 106 Bowne
Page 19 of 21
Chapter 4: Introduction to TCP/IP Protocols
CNIT 106 Bowne
Maintaining accuracy, consistency between multiple storage systems
Page 20 of 21
Chapter 4: Introduction to TCP/IP Protocols
NNTP (Network News Transfer Protocol)
Facilitates newsgroup messages exchange
Between multiple servers, users
Similar to e-mail
Provides means of conveying messages
Differs from e-mail
Distributes messages to wide group of users at once
User subscribes to newsgroup server host
News servers
Central collection, distribution point for newsgroup messages
PING (Packet Internet Groper)
Provides verification
TCP/IP installed, bound to NIC, configured correctly, communicating with
network
Host responding
Uses ICMP services
Send echo request and echo reply messages
Determine IP address validity
Ping IP address or host name
Ping loopback address: 127.0.0.1
Determine if workstations TCP/IP services running
Operating system determines Ping command options, switches, syntax
Last modified 9-14-09
CNIT 106 Bowne
Page 21 of 21
S-ar putea să vă placă și
- TCP/IP ConceptsDocument23 paginiTCP/IP ConceptsLuis CadenaÎncă nu există evaluări
- TCP/IP Protocol Suite and IP AddressingDocument31 paginiTCP/IP Protocol Suite and IP AddressingHungry LadyÎncă nu există evaluări
- Network+ Guide To Networks, Fourth EditionDocument51 paginiNetwork+ Guide To Networks, Fourth EditionDebasis SahooÎncă nu există evaluări
- TCP-IP Networking BasicsDocument73 paginiTCP-IP Networking Basicssaihunter100% (1)
- Basic Computer NetworkDocument60 paginiBasic Computer NetworkneerajnepalÎncă nu există evaluări
- Internet Working Session IDocument82 paginiInternet Working Session IkevotooÎncă nu există evaluări
- CCNA 1 v3.0 Module 9 TCP/IP Protocol Suite and IP AddressingDocument33 paginiCCNA 1 v3.0 Module 9 TCP/IP Protocol Suite and IP AddressingNgging White HatÎncă nu există evaluări
- Experiment No.10 AIM: Configuring TCP/IP On Windows Operating Systems TheoryDocument5 paginiExperiment No.10 AIM: Configuring TCP/IP On Windows Operating Systems TheorysachinÎncă nu există evaluări
- Network+ Guide To Networks 5 Edition: Introduction To TCP/IP ProtocolsDocument88 paginiNetwork+ Guide To Networks 5 Edition: Introduction To TCP/IP ProtocolsRyan OrtegaÎncă nu există evaluări
- Networking Technologies and E-Commerce: Session 3 Dr. Devendra Kumar PuniaDocument40 paginiNetworking Technologies and E-Commerce: Session 3 Dr. Devendra Kumar PuniaAnubha JindalÎncă nu există evaluări
- Unit Objective: Identify TCP/IP Properties, and Identify Common Ports and ProtocolsDocument33 paginiUnit Objective: Identify TCP/IP Properties, and Identify Common Ports and ProtocolsSean DickersonÎncă nu există evaluări
- September 2000: Software Reference IP 1Document189 paginiSeptember 2000: Software Reference IP 1niko67Încă nu există evaluări
- Tcpi IpDocument97 paginiTcpi Ipcborn99100% (1)
- Network+ Guide To NetworksDocument67 paginiNetwork+ Guide To NetworksSamin AfnanÎncă nu există evaluări
- TCP IP & AddressesDocument18 paginiTCP IP & Addresses366VEDANTI BACHCHUWARÎncă nu există evaluări
- Internet ProtocolDocument120 paginiInternet Protocoldeepsj1988100% (1)
- TCP/IP Fundamentals: Chapter ObjectivesDocument27 paginiTCP/IP Fundamentals: Chapter Objectiveschetana sidigeÎncă nu există evaluări
- Chapter 4 TCP IP Reference ModelDocument43 paginiChapter 4 TCP IP Reference Modelamanuelfitsum589Încă nu există evaluări
- 2.1 Internet PrinciplesDocument33 pagini2.1 Internet PrinciplesSwetha ChintalÎncă nu există evaluări
- Internet Protocols g10 Chs EdzDocument49 paginiInternet Protocols g10 Chs EdzJoan SarahanÎncă nu există evaluări
- ObjectivesDocument19 paginiObjectivesthinhbgcnttÎncă nu există evaluări
- Unit VDocument33 paginiUnit VErwin VunguÎncă nu există evaluări
- Hct6000 Tcpip OptionDocument14 paginiHct6000 Tcpip OptionGerman DfrÎncă nu există evaluări
- Course: Instructed byDocument21 paginiCourse: Instructed byanurag_0290Încă nu există evaluări
- ChapterDocument57 paginiChapterYomif NiguseÎncă nu există evaluări
- The TCP/IP Protocol Suite: Network Interface LayerDocument18 paginiThe TCP/IP Protocol Suite: Network Interface LayergunapalshettyÎncă nu există evaluări
- Unit Iv-1Document33 paginiUnit Iv-1InnocentÎncă nu există evaluări
- Salesian Polytechnical University Systems Engineering: Networks IiDocument8 paginiSalesian Polytechnical University Systems Engineering: Networks Iisony_w200Încă nu există evaluări
- Tcp/Ip Model: Application LayerDocument3 paginiTcp/Ip Model: Application LayerVikas SharmaÎncă nu există evaluări
- TCP IP ModelDocument31 paginiTCP IP ModelJaveed AhamedÎncă nu există evaluări
- Internet ProtocolDocument4 paginiInternet ProtocolMark Lester PicazoÎncă nu există evaluări
- TCP/IP Model: CPE 401 / 601 Computer Network SystemsDocument59 paginiTCP/IP Model: CPE 401 / 601 Computer Network Systemsvaibhav aroraÎncă nu există evaluări
- TCP/IP Protocol Architecture Model: Previous: Protocol Layers and The Open Systems Interconnection ModelDocument5 paginiTCP/IP Protocol Architecture Model: Previous: Protocol Layers and The Open Systems Interconnection ModelGreen ZoneÎncă nu există evaluări
- How TCP-IP WorksDocument29 paginiHow TCP-IP WorksJames GeorgeÎncă nu există evaluări
- CCNA 640-802: Chapter 2: Introduction To TCP/IPDocument24 paginiCCNA 640-802: Chapter 2: Introduction To TCP/IPJoyÎncă nu există evaluări
- CCN Unit-01 (B)Document56 paginiCCN Unit-01 (B)Basavaraj ShellikeriÎncă nu există evaluări
- Ccna Intro: Chapter - 2Document9 paginiCcna Intro: Chapter - 2Amritpal SinghÎncă nu există evaluări
- Ccna Notes Full PDFDocument33 paginiCcna Notes Full PDFKo Pyae79% (19)
- Networks2 OdtDocument8 paginiNetworks2 Odtumang goelÎncă nu există evaluări
- Address Resolution ProtocolDocument5 paginiAddress Resolution ProtocolTushar VermaÎncă nu există evaluări
- MODULE 9 - TCP/IP Protocol Suite and IP AddressingDocument7 paginiMODULE 9 - TCP/IP Protocol Suite and IP AddressingGrecu GianiÎncă nu există evaluări
- CH 7 - Internet Protocol and IP AddressingDocument22 paginiCH 7 - Internet Protocol and IP Addressingmelkamu debasÎncă nu există evaluări
- Transmission Control Protocol (TCP) / Internet Protocol (Ip)Document24 paginiTransmission Control Protocol (TCP) / Internet Protocol (Ip)Harshitha BaranikaÎncă nu există evaluări
- Internet ProtocolsDocument40 paginiInternet ProtocolsPepeÎncă nu există evaluări
- Network+ Exam Cram Study SheetDocument3 paginiNetwork+ Exam Cram Study SheetDan Sheets86% (21)
- Hari Krishna Raju Kanekal Nomus Comm-SystemsDocument155 paginiHari Krishna Raju Kanekal Nomus Comm-Systemsharikrishna242424Încă nu există evaluări
- IPv6 PDFDocument155 paginiIPv6 PDFharikrishna242424Încă nu există evaluări
- Network+ Guide To Networks 6 Edition: Introduction To TCP/IP ProtocolsDocument68 paginiNetwork+ Guide To Networks 6 Edition: Introduction To TCP/IP Protocolsjking174Încă nu există evaluări
- TCP/IP Model: CSM-4401 Network ProgrammingDocument59 paginiTCP/IP Model: CSM-4401 Network ProgrammingAbraham GadissaÎncă nu există evaluări
- Imp For InterviewDocument16 paginiImp For InterviewPravin PuriÎncă nu există evaluări
- Understanding An Ip Address Learning ObjectivesDocument10 paginiUnderstanding An Ip Address Learning ObjectivesbwijjayÎncă nu există evaluări
- Introduction To TC PipDocument20 paginiIntroduction To TC PipJESUS JHOJANSON BERMEJO LLANOSÎncă nu există evaluări
- Chapter 2 Data Communications Lecture 2.2Document26 paginiChapter 2 Data Communications Lecture 2.2Deepak SutharÎncă nu există evaluări
- F5 101 - Application Delivery Fundamentals: Part 1: Networking BasicsDocument26 paginiF5 101 - Application Delivery Fundamentals: Part 1: Networking BasicsAgus HerdiyanaÎncă nu există evaluări
- Internetworking With TCP/IP (ETC003) : © Adrian Popescu, 2003, 2004Document5 paginiInternetworking With TCP/IP (ETC003) : © Adrian Popescu, 2003, 2004Rohit KshirsagarÎncă nu există evaluări
- Network LayerDocument22 paginiNetwork LayerRashed SobujÎncă nu există evaluări
- Cis81 E1 5 NetworkLayerDocument42 paginiCis81 E1 5 NetworkLayerEwa LisekÎncă nu există evaluări
- CCST Cisco Certified Support Technician Study Guide: Networking ExamDe la EverandCCST Cisco Certified Support Technician Study Guide: Networking ExamÎncă nu există evaluări
- Analyzing Network Traffic With Wireshark 3e - Mason BurtonDocument24 paginiAnalyzing Network Traffic With Wireshark 3e - Mason Burtonmasonburton56Încă nu există evaluări
- Qos Class Mark PoliceDocument22 paginiQos Class Mark PoliceNelsonbohrÎncă nu există evaluări
- Configure IP AddressesDocument1 paginăConfigure IP AddressesmichaelÎncă nu există evaluări
- Enterprise Branch Architecture Design OverviewDocument28 paginiEnterprise Branch Architecture Design OverviewRuchir PokharnaÎncă nu există evaluări
- E-DATA MU200 SpecsheetDocument2 paginiE-DATA MU200 Specsheetعقود السمÎncă nu există evaluări
- Configuração Huawei Ma5600Document3 paginiConfiguração Huawei Ma5600Aires JuniorÎncă nu există evaluări
- DO Ambassadors 2014Document140 paginiDO Ambassadors 2014viatr0nicÎncă nu există evaluări
- XV102 - IHM Eaton MoellerDocument48 paginiXV102 - IHM Eaton MoellerChico SantanaÎncă nu există evaluări
- Sangfor NGAF v8.0.47 User Manual enDocument664 paginiSangfor NGAF v8.0.47 User Manual enharry chan PutraÎncă nu există evaluări
- DHCP Sim Troubleshooting - CCNA 200-125 Labs Simulator: You Can Download This Lab and Practice With Packet TracerDocument8 paginiDHCP Sim Troubleshooting - CCNA 200-125 Labs Simulator: You Can Download This Lab and Practice With Packet Tracerergu vfuko fghuiÎncă nu există evaluări
- snmp card user's manual 说明书Document12 paginisnmp card user's manual 说明书Welton CorreiaÎncă nu există evaluări
- Network MidtermDocument24 paginiNetwork MidtermPrincess Dndoon GÎncă nu există evaluări
- AvalancheDocument74 paginiAvalancheDanielGuinterÎncă nu există evaluări
- BGP Soft Reset Enhancement: Feature OverviewDocument14 paginiBGP Soft Reset Enhancement: Feature OverviewTIBUS145Încă nu există evaluări
- Ccna Training Ccnav3 - New Questions 4Document31 paginiCcna Training Ccnav3 - New Questions 4Remi PaternackÎncă nu există evaluări
- Vrealize Operations Manager Best Practices 8.1Document24 paginiVrealize Operations Manager Best Practices 8.1walexmueeÎncă nu există evaluări
- 20410B Course Lab Answer KeyDocument80 pagini20410B Course Lab Answer KeyNguyen PhuongÎncă nu există evaluări
- Web-Admin Configuration Manual: Altai C1N Series Wifi Ap/CpeDocument120 paginiWeb-Admin Configuration Manual: Altai C1N Series Wifi Ap/CpeosvaldoÎncă nu există evaluări
- IT1Document16 paginiIT1Shaikh Ahsan AliÎncă nu există evaluări
- Deep Sea Electronics PLC Dse8004 10" Overview Screen Installation Instructions Dse8004 10" Overview ScreenDocument84 paginiDeep Sea Electronics PLC Dse8004 10" Overview Screen Installation Instructions Dse8004 10" Overview ScreenOreonnyr SouzaÎncă nu există evaluări
- 11g Rac Failover Testing v1-0Document12 pagini11g Rac Failover Testing v1-0gmasayÎncă nu există evaluări
- Soal CiscoDocument8 paginiSoal CiscoAngga PriatmaÎncă nu există evaluări
- Configuration WorksheetDocument30 paginiConfiguration WorksheetSami DziriÎncă nu există evaluări
- Cisco SG-350 Switch and Fortigate Firewall Configuration: Ask QuestionDocument9 paginiCisco SG-350 Switch and Fortigate Firewall Configuration: Ask QuestionRaneesh RamesanÎncă nu există evaluări
- DVR Usermanual v1.2Document31 paginiDVR Usermanual v1.2Arthur CerqueiraÎncă nu există evaluări
- System Admin QuestionsDocument9 paginiSystem Admin QuestionsNagaraju KasaÎncă nu există evaluări
- Mountain Sky TCSDocument32 paginiMountain Sky TCSDirlatÎncă nu există evaluări
- S6700 V100R006C00 Typical Configuration Examples 02Document857 paginiS6700 V100R006C00 Typical Configuration Examples 02GerardoÎncă nu există evaluări
- MTCRE Koleksi Hasan - IDN Garut 1Document27 paginiMTCRE Koleksi Hasan - IDN Garut 1Ujang DianÎncă nu există evaluări
- 1 GCP Cheatsheet CloudDocument3 pagini1 GCP Cheatsheet CloudMukeshBhardwajÎncă nu există evaluări