Documente Academic
Documente Profesional
Documente Cultură
B.Tech Sem6 Ucoe
Încărcat de
Raghav BhandariTitlu original
Drepturi de autor
Formate disponibile
Partajați acest document
Partajați sau inserați document
Vi se pare util acest document?
Este necorespunzător acest conținut?
Raportați acest documentDrepturi de autor:
Formate disponibile
B.Tech Sem6 Ucoe
Încărcat de
Raghav BhandariDrepturi de autor:
Formate disponibile
B.
TECH THIRD YEAR
COMPUTER ENGINEERING
(Batch 2012)
Session (2014-15)
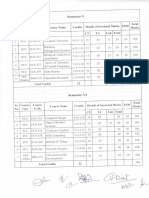
SCHEME OF PAPERS
SIXTH SEMESTER (COMPUTER ENGINEERING)
S.
Subject Code Subject Name
No.
1.
CPE-307
RDBMS using SQL and PL/SQL
2.
CPE-308
Computer Graphics
3.
CPE-309
Compiler Design
4.
CPE-310
DotNet Programming
5.
CPE-357
Relational Database Management System Lab
6.
CPE-358
Computer Graphics Lab
7.
CPE-360
DotNet Programming Lab
8.
Elective-II *
9.
Elective-III **
Total
Total Contact Hours = 30
ELECTIVE II FOR SIXTH SEMESTER (COMPUTER ENGINEERING)*
S.
Subject Code Subject Name
No.
1
CPE-311
Parallel Computing
2
CPE-312
Multimedia Systems
1.
CPE-313
Software Project Management
2.
CPE-314
Distributed Computing
3.
MBA-5011
Foundation of Financial Accounting
*CHOOSE ANY ONE FROM THE LIST
T P Cr.
3
3
3
3
0
0
0
3
3
18
1
1
1
1
0
0
0
1
1
6
T P Cr.
3
3
3
3
3
1
1
1
1
1
ELECTIVE III FOR SIXTH SEMESTER (COMPUTER ENGINEERING)**
S.
Subject Code Subject Name
L
No.
1.
CPE-315
Network Security
3
2.
CPE-316
ATM Networks
3
3.
CPE-317
Grid Computing
3
4.
CPE-318
Business Intelligence
3
5.
MBA-5012
Foundations of Managerial Accounting
3
**CHOOSE ANY ONE FROM THE LIST
0
0
0
0
2
2
2
0
0
6
0
0
0
0
0
3.5
3.5
3.5
3.5
1.0
1.0
1.0
3.5
3.5
24
3.5
3.5
3.5
3.5
3.5
T P Cr.
1
1
1
1
1
0
0
0
0
0
3.5
3.5
3.5
3.5
3.5
CPE-357, CPE-358 and CPE-360 are practical papers only. There will not be any theory
examination for these papers.
CPE-307
RDBMS using SQL and PL/SQL
L
Cr
3.5
Section A
Introduction of DBMS:
Types of DBMS and their advantages and disadvantages, DBMS architecture, Enhanced-ER
(EER) Model Concepts, EER-to-Relational Mapping, Data Abstraction and Knowledge
embedded SQL, Query by example.
Distributed Databases and Client-Server Architecture: Introduction to Distributed DBMS
Concepts, Client-Server Architecture Overview, Data Fragmentation, Replication, and Allocation
Techniques for Distributed Database Design, Types of Distributed Database Systems.
Database Security: Types of Security, Control Measures, DB security and DBA, Access
protection, Discretionary Access Control based on granting and revoking privileges
Section B
Overview of SQL:
Introduction to SQL Server and Oracle Server. Select, Insert, Update, Delete Commands
Inbuilt function (string, numeric and date), joins, create table and constraints, Data Dictionary,
views, Grant Revoke
Section C
PL/SQL: Block structure, data types, creation of variable, scope, nested blocks, control
structures, cursors and its types
Section D
Procedures and types of parameter passing
Functions both inbuilt and user defined
Packages both user defined and inbuilt
Triggers and its types
Recommended Books :
1. Navathe and Elmasri, Fundamentals of Database Systems, Pearson education
2. Korth and Silberschatz Abraham, Database Concepts, McGraw Hall, 1991.
3. An introduction to database system by C.J.Date (Addison Welsey, Publishing house) Latest
edition.
4. Bipin Desai, Database System, TMG
5. Prateek Bhatia, Database Management system, Kalyani Publishers
CPE-308
COMPUTER GRAPHICS
L
3
T
1
P
0
Cr
3.5
Section-A
Raster CRTs, Raster and Random Scan Displays, Display
Controllers and Processors, Graphics Input Devices, Applications of Computer Graphics.
RASTER SCAN CONVERSION ALGORITHMS: Line Drawing Algorithms (DDA &
Bresenhams), Circle Drawing Algorithms (Mid Point and Bresenhams).
GRAPHICS HARDWARE:
Section-B
Basic Transformations,
(Translation, Rotation and Scaling) Matrix Representation and Homogenous Coordinates, Shear
and Reflection Transformations, Composite Transformations.
FILLING: Region filling Algorithms (Boundary Fill and Flood Fill).
TWO-DIMENSIONAL
GEOMETRIC
TRANSFORMATIONS:
Section-C
WINDOWING AND CLIPPING: Viewing pipeline, viewing transformations. 2-D Clipping
algorithms- Line clipping algorithms (Cohen Sutherland, Liang Barsky algorithm) Polygon
clipping (Sutherland Hodgeman polygon clipping, Weiler and Atherton polygon clipping).
THREE-DIMENSIONAL GEOMETRIC TRANSFORMATIONS: Basic Transformations:
(Translation, Scaling, Rotation) Composite transformations.
Section-D
PROJECTIONS: Parallel and Perspective.
VISIBLE SURFACE DETECTION METHODS: Depth Buffer Method, A-Buffer Method, Scan
Line Method, Area Subdivision Method.
Shading: Gouraud and Phong Shading Algorithms, Properties of Bezier and B-Spline Curves.
Recommended Books:
1. Computer Graphics: By Donald Hearn, M. Pauline Baker
2. Computer Graphics (Schaum Series ) by Lipschutz (MC Graw Hill)
3. Principles of Interactive Computer graphics: By W.M. Newman, R.Sproull
4. Fundamentals of Interactive Computer Graphics: By J.D. Foley, A. Van Dam
5. Computer Graphics Using OPEN GL: By F.S. Hill Jr.
6. Computer Graphics: Roy A. Plastock, Gordon Kalley.
CPE - 309
COMPILER DESIGN
L
3
T
1
P
0
Cr
3
Section A
INTRODUCTION TO COMPILING:
Compilers Analysis of the source program Phases of a compiler Cousins of the Compiler
Grouping of Phases Compiler construction tools Lexical Analysis Role of Lexical Analyzer
Input Buffering Specification of Tokens.
Section B
SYNTAX ANALYSIS: Role of the parser Writing Grammars Context-Free Grammars Top
Down parsing Recursive Descent Parsing Predictive Parsing Bottom-up parsing Shift
Reduce Parsing Operator Precedent Parsing LR Parsers SLR Parser Canonical LR Parser
LALR Parser.
Section C
INTERMEDIATE CODE GENERATION: Intermediate languages Declarations Assignment
Statements Boolean Expressions Case Statements Back patching Procedure calls.
Section D
CODEGENERATION: Issues in the design of code generator The target machine Runtime
Storage management Basic Blocks and Flow Graphs Next-use Information A simple Code
generator DAG representation of Basic Blocks Peephole Optimization.
CODE OPTIMIZATION AND RUN TIME ENVIRONMENTS: Introduction Principal Sources
of Optimization Optimization of basic Blocks Introduction to Global Data Flow Analysis
Runtime Environments Source Language issues Storage Organization Storage Allocation
strategies Access to non-local name Parameter Passing.
Recommended Books :
1. Alfred Aho, Ravi Sethi, Jeffrey D Ullman, Compilers Principles, Techniques and Tools,
Pearson Education Asia, 2003.
2. Allen I. Holub Compiler Design in C, Prentice Hall of India, 2003.
3. C. N. Fischer and R. J. LeBlanc, Crafting a compiler with C, Benjamin Cummings,
2003.
4. J.P. Bennet, Introduction to Compiler Techniques, Second Edition, Tata McGraw-Hill,
2003.
5. Henk Alblas and Albert Nymeyer, Practice and Principles of Compiler Building with
C, PHI, 2001.
6. Kenneth C. Louden, Compiler Construction: Principles and Practice, Thompson
Learning, 2003
CPE-310
DotNet Programming
L
3
T
1
P
0
Cr
3.5
Section A
Introduction to DotNet Framework. Design Features: Interoperability, Common Language
Runtime Engine, Language Independence, Base Class Library, Simplified Deployment, Security,
Portability. Architecture: Common Language Infrastructure (CLI), Class Library, Security,
Memory management
Section B
Introduction to VB.Net: Language Basics: Data Types, Variables, Arrays, Strings, Control
Structures, Procedures, Functions.
Designing User Interface: TextBox, Label, Button, ListBox, ComboBox, Radio Button,
CheckBox, Timer, Dialog Box, Progress Bar etc, Specifying event handlers, Adding Menus,
MDI.
Section C
Object & Classes, Namespaces, Error Handling, Debugging
Using ADO.Net: Connection, Data Adapter, Data Sets, Data Commands, Advance Data Bound
Controls, Introduction to Crystal Reports
Section D
Building a custom window control: Adding new properties, methods and events, testing a
control, enhancing existing controls
Introduction to ASP.Net: Web Controls, Validating Controls
Recommended Books :
1.
2.
3.
Brian Siler & Jeff Spotts, Microsoft Visual Basic.Net
Matthew MacDonald, .NET Insight for VB Developers
Mastering in VB.Net
CPE 314
DISTRIBUTED COMPUTING
L
3
T
1
P
0
Cr
3.5
Section A
Introduction: Motivation, objectives, characterization
& classification of
distributed
systems. Distributed system architecture. Hardware & software issues, Communication: Layered
protocols, Client server protocols, RPC, group communication.
Coordination, synchronization & consistency: Logical clocks, Physical clocks, mutual
exclusion, election algorithms, atomic broadcast, sequential consistency transaction distributed
consensus, Threads: Thread synchronization, implementation issues, and threads vs. RPC.
Section B
Models of distributed computing: Client - Server Architectures : Challenges, Design,
Methodology, Intranets and Groupware. Group models and peer to peer: Groups for service
replication/ reliability, groups for parallelism / performance, client/ server vs. peer-to-peer,
multicast.
Section C
Distributed file system: Security, Naming/ location transparency, R/W semantics, cache
coherence, replication. Load Balancing Distributed shared memory.
Distributed multimedia system: Introduction, characteristics, and resource management stream
adaptation
Section D
Fault tolerant distributed systems: Introduction, dependability, faults vs. errors vs. failure,
space time and value redundancy, fault tolerant architecture, failure detection algorithms,
partitioning, FT consensus.
Security techniques, cryptographic algorithms, authentication and access control.
Recommended Books :
1. Distributed systems, concepts and design, 3rd Edition, Addison Wesley by George
Colouris, Jean Dollimore and Tim Kinder berg.
2. Distributed system, 2nd Edition, Addison Wesley by Sape Mull ender.
3. Distributed Computing, Principles and applications, M.L.Liu, Pearson Education
CPE - 315
NETWORK SECURITY
L
3
T
1
P
0
Cr
3.5
SECTION A
BASIC ENCRYPTION AND DECRYPTION: Attackers and Types of threats, challenges for
information security, Encryption Techniques, Classical Cryptographic Algorithms:
Monoalphabetic Substitutions such as the Caesar Cipher, Cryptanalysis of Monoalphabetic
ciphers, Polyalphabetic Ciphers such as Vigenere, Vernam Cipher, Stream and Block Ciphers.
SECTION B
SECRET KEY SYSTEMS: The Data encryption Standard (DES), Analyzing and Strengthening of
DES, Introduction to Advance Encryption Standard (AES)
PUBLIC KEY ENCRYPTION SYSTEMS: Concept and Characteristics of Public Key Encryption
system, Introduction to Merkle-Hellman Knapsacks, Rivets Shamir-Adlman (RSA)
Encryption.
SECTION C
HASH ALGORITHMS: Hash Algorithms, Message Digest Algorithms such as MD4 and MD5,
Secure Hash Algorithms such as SH1 and SHA2.
NETWORK SECURITY: Network Security Issues such as Impersonation, Message
Confidentiality, Message Integrity, Code Integrity, Denial of Service, Firewalls, DMZs, Virtual
Private Networks, Network Monitoring and Diagnostic Devices.
SECTION D
WEB SECURITY: Web Servers, Secure Electronic Mail, Enhanced Email, Pretty Good Privacy,
Public Key Cryptography Standards
ETHICAL HACKING: Introduction to Ethical Hacking, Terminology, Hackers, Crackers, and
Other Related Terms, Hactivism, Threats, Hacking History ,Ethical Hacking Objectives and
Motivations. .
Recommended Books:
1. Principles of Cryptography, William Stallings, Pearson Education
2. Security in Computing (Second Edition), Charles P.Pfleeger, 1996, Prentice Hall
International, Inc.
3. Cryptography & Network Security, Atul Kahate, TMH
CPE-357
Relational Database Management System Lab
L
0
T
0
OBJECTIVE
1. The students are required to do exercises / projects in database design
2. Implementation of SQL queries DDL, DML, DCL
3. Implementation of PL/SQL
a. Block Structure, Variables
b. Control Structure
c. Cursors
d. Procedures
e. Functions
f. Packages
g. Triggers
P
2
Cr
1.0
CPE 358
COMUPTER GRAPHICS LAB
L
Cr
1.0
OBJECTIVE:The students are required to do exercises on various computer graphics algorithms in either C/C+
+ Language. Implement following using various algorithms:
1. Line drawing
2. Line clipping
3. circle drawing
4. area clipping
5. drawing of some 2-D pictures
6. 2-D transformations: rotation, translation etc
7. Shading
8. Line Hidding
Finally design some Ads., Game etc using all the above or built in commands.
CPE-360
DotNet Programming Lab
L
0
OBJECTIVE
The students are required to do exercises / projects:
1. Implementation of Iterative Structures.
2. Implementation of Conditional Structures.
T
0
P
2
Cr
1.0
3. Split & join functions in String.
4. Implementation of class.
5. Use of Textbox, Label, Buttons component.
6. Use of Timer, Progress Bar, Menu Bar component.
7. Use of ListBox, ComboBox, CheckBox, Radio Button component.
8. Implementation of Graphics methods.
9. Creating a window control.
10. Database Connectivity.
S-ar putea să vă placă și
- 6th SemesterDocument12 pagini6th SemestervigitÎncă nu există evaluări
- CPE - 301 SYSTEM ANALYSIS AND DESIGNDocument9 paginiCPE - 301 SYSTEM ANALYSIS AND DESIGNTajinder VashishtÎncă nu există evaluări
- PTU M.Tech Computer Science Study SchemeDocument24 paginiPTU M.Tech Computer Science Study SchemeJetesh DevgunÎncă nu există evaluări
- 1st Sem MCADocument6 pagini1st Sem MCArohietsharmaaÎncă nu există evaluări
- MCA 2015syllabus PDFDocument46 paginiMCA 2015syllabus PDFmidhulÎncă nu există evaluări
- Advance Computer Architecture & Peripherals: Duration 3 Hours 3 1 2 6 70 22Document7 paginiAdvance Computer Architecture & Peripherals: Duration 3 Hours 3 1 2 6 70 22Yogendra AgnihotriÎncă nu există evaluări
- 3rd CSE IT New Syllabus 2019 20Document19 pagini3rd CSE IT New Syllabus 2019 20Harsh Vardhan HBTUÎncă nu există evaluări
- IDE-1 Courses SyllabusDocument8 paginiIDE-1 Courses SyllabusPulluru Sreenivas Sai LokeshÎncă nu există evaluări
- 5 Sem SyllabusDocument13 pagini5 Sem Syllabusviswasknit100% (2)
- Syllabus B Tech CSE 3rd Year (6th Sem Non-Credit Based) KUKDocument10 paginiSyllabus B Tech CSE 3rd Year (6th Sem Non-Credit Based) KUKz1111234Încă nu există evaluări
- Kuk 6 ThsemesterDocument17 paginiKuk 6 ThsemesterAakash SharmaÎncă nu există evaluări
- SylabiiDocument6 paginiSylabiiashit kumarÎncă nu există evaluări
- CA 1804 Discrete Structures: Department of Computer Applications (MCA)Document25 paginiCA 1804 Discrete Structures: Department of Computer Applications (MCA)ramsethu12Încă nu există evaluări
- IT UG - New SyllabusDocument48 paginiIT UG - New SyllabusParush AryaÎncă nu există evaluări
- MG University Mca 4th Sem SyllabusDocument18 paginiMG University Mca 4th Sem Syllabusnoblesivankutty100% (1)
- Master of Science (M.SC.) - Computer Science Curriculum - 2013Document50 paginiMaster of Science (M.SC.) - Computer Science Curriculum - 2013muralikrish14uÎncă nu există evaluări
- Cse2003 Computer-Architecture-And-Organization LT 1.0 1 Cse2003Document3 paginiCse2003 Computer-Architecture-And-Organization LT 1.0 1 Cse2003Sunil KumarÎncă nu există evaluări
- SyllabusDocument36 paginiSyllabusJenitha JoelÎncă nu există evaluări
- 5th Sem SyllabiDocument12 pagini5th Sem Syllabiinamwani08Încă nu există evaluări
- Computer UG New Syllabus.Document46 paginiComputer UG New Syllabus.Ujjawal TyagiÎncă nu există evaluări
- Academic Regulations Course Structure AND Detailed Syllabus: Computer Science and EngineeringDocument20 paginiAcademic Regulations Course Structure AND Detailed Syllabus: Computer Science and EngineeringneczuberbashaÎncă nu există evaluări
- MCA SEMESTER 3 SYSTEM SOFTWARE COURSEDocument4 paginiMCA SEMESTER 3 SYSTEM SOFTWARE COURSErahulrnair4u_5534754Încă nu există evaluări
- Syllabus For Third Semester Operating SystemDocument10 paginiSyllabus For Third Semester Operating SystemMicÎncă nu există evaluări
- BE VII Sem Comp SC - Doc120813082355Document13 paginiBE VII Sem Comp SC - Doc120813082355palakÎncă nu există evaluări
- Sem-4 CSEDocument7 paginiSem-4 CSEdattpatel2020Încă nu există evaluări
- Computer Aided Management: Subject Code: CAMDocument4 paginiComputer Aided Management: Subject Code: CAMPomil LuthraÎncă nu există evaluări
- PSC Lecture NotesDocument11 paginiPSC Lecture NotesseravanaÎncă nu există evaluări
- MSC ct5 IVDocument9 paginiMSC ct5 IVBewic JohnÎncă nu există evaluări
- Syllabus Computer ApplicationDocument13 paginiSyllabus Computer Applicationsinghsamiksha347Încă nu există evaluări
- Computer System Architecture: Course ContentsDocument5 paginiComputer System Architecture: Course Contentsammar jamalÎncă nu există evaluări
- 10348Document54 pagini10348sania2011Încă nu există evaluări
- The Night Before ExamsDocument10 paginiThe Night Before ExamsPrashanth AcharÎncă nu există evaluări
- Thapar MCA Syllabus PDFDocument53 paginiThapar MCA Syllabus PDFsunnykinger100% (2)
- Cse PDFDocument55 paginiCse PDFNikhil PhulÎncă nu există evaluări
- Syllabus CS-0000 V Sem All SubjectDocument11 paginiSyllabus CS-0000 V Sem All Subject12ashivangtiwariÎncă nu există evaluări
- PGDCA SyllabusDocument10 paginiPGDCA SyllabusAnonymous l5X3VhTÎncă nu există evaluări
- SyllabusDocument2 paginiSyllabusrishabhtak16Încă nu există evaluări
- Week Wise Syllabus 1st SemesterDocument7 paginiWeek Wise Syllabus 1st SemesterRehman Ahmad ChÎncă nu există evaluări
- Choose Any One From The ListDocument18 paginiChoose Any One From The ListlavandeepÎncă nu există evaluări
- Mca 5th SemDocument6 paginiMca 5th SemNitin AhluwaliaÎncă nu există evaluări
- Anna University, Chennai: Affiliated InstitutionsDocument7 paginiAnna University, Chennai: Affiliated InstitutionsShama AnvarÎncă nu există evaluări
- B.Sc. Computer Science Syllabus under CBCSDocument27 paginiB.Sc. Computer Science Syllabus under CBCSVelrone Pierson AlvaresÎncă nu există evaluări
- Data Structures and Algorithms CS201Document88 paginiData Structures and Algorithms CS201ApÎncă nu există evaluări
- Mahamaya Technical University: SyllabusDocument25 paginiMahamaya Technical University: SyllabusakttripathiÎncă nu există evaluări
- CO SyllDocument82 paginiCO SyllSaurabh YadavÎncă nu există evaluări
- Computer Programming: Course OverviewDocument2 paginiComputer Programming: Course OverviewJanus Raymond TanÎncă nu există evaluări
- C# AND .NET FRAMEWORKDocument2 paginiC# AND .NET FRAMEWORKYunusitboss IrshadÎncă nu există evaluări
- PGDCA SyllabusDocument16 paginiPGDCA SyllabusMr freakyÎncă nu există evaluări
- 4 Year B.Tech CSE FullSyllabusDocument37 pagini4 Year B.Tech CSE FullSyllabusgmttmÎncă nu există evaluări
- Compiler SyllabusDocument2 paginiCompiler Syllabusanils3kumarÎncă nu există evaluări
- Cse Programming For Problem Solving Lecture NotesDocument185 paginiCse Programming For Problem Solving Lecture NotesTAMMISETTY VIJAY KUMARÎncă nu există evaluări
- Computer-Aided Design TechniquesDe la EverandComputer-Aided Design TechniquesE. WolfendaleÎncă nu există evaluări
- Software Engineering for Embedded Systems: Methods, Practical Techniques, and ApplicationsDe la EverandSoftware Engineering for Embedded Systems: Methods, Practical Techniques, and ApplicationsEvaluare: 2.5 din 5 stele2.5/5 (2)
- Mastering MATLAB: A Comprehensive Journey Through Coding and AnalysisDe la EverandMastering MATLAB: A Comprehensive Journey Through Coding and AnalysisÎncă nu există evaluări
- Campus Recruitment Program 2014-2015: Eligibility Criteria and Roles at InfosysDocument1 paginăCampus Recruitment Program 2014-2015: Eligibility Criteria and Roles at InfosysRaghav BhandariÎncă nu există evaluări
- M341 xUG GLB enDocument67 paginiM341 xUG GLB enRaghav BhandariÎncă nu există evaluări
- 01-Introduction To Artificial IntelligenceDocument0 pagini01-Introduction To Artificial IntelligencesatyakishoreakulaÎncă nu există evaluări
- Cryptography ForouzanDocument56 paginiCryptography ForouzanRaghav BhandariÎncă nu există evaluări
- Models of Distributed SystemDocument13 paginiModels of Distributed SystemRaghav BhandariÎncă nu există evaluări
- AmbiguityDocument9 paginiAmbiguityRaghav BhandariÎncă nu există evaluări
- Unit - 2 Part 1 - CNSDocument44 paginiUnit - 2 Part 1 - CNSPushkal KS VaidyaÎncă nu există evaluări
- Flask WerkzeugDocument6 paginiFlask WerkzeugTgowtham ArasuÎncă nu există evaluări
- Information Security Imp +past PaperDocument34 paginiInformation Security Imp +past PaperRana SaaBÎncă nu există evaluări
- Midterm SamplesolutionsDocument6 paginiMidterm Samplesolutionspicolo1Încă nu există evaluări
- 16 - HTTP Vs HtppsDocument49 pagini16 - HTTP Vs HtppsGi jiÎncă nu există evaluări
- Cloudstack InstallationDocument167 paginiCloudstack InstallationErt ElletsÎncă nu există evaluări
- Guidelines for Selecting and Configuring TLS ImplementationsDocument73 paginiGuidelines for Selecting and Configuring TLS ImplementationshumdilÎncă nu există evaluări
- Chapter 13 - SecurityDocument59 paginiChapter 13 - SecurityTresor BrouÎncă nu există evaluări
- Final Online Job Tracking System in Dmu TownDocument70 paginiFinal Online Job Tracking System in Dmu TownKassie MezgebuÎncă nu există evaluări
- Network Security Multiple Choice Questions and Answers PDF ExamRadarDocument9 paginiNetwork Security Multiple Choice Questions and Answers PDF ExamRadarNIRMALYA_NJRCS100% (1)
- Interview Questions 1Document16 paginiInterview Questions 1Selva GaneshÎncă nu există evaluări
- IPsec Overhead Analysis for Mobile DevicesDocument17 paginiIPsec Overhead Analysis for Mobile DevicesSiti NurhawaÎncă nu există evaluări
- CNS Module4Document13 paginiCNS Module4Sagar B SÎncă nu există evaluări
- Annexes To The PSDSRC Final ReportDocument53 paginiAnnexes To The PSDSRC Final ReportNicholasFCheongÎncă nu există evaluări
- Week 10 OS Protection and SecurityDocument80 paginiWeek 10 OS Protection and SecuritySC20A942 Jeme Beseka FonchamÎncă nu există evaluări
- SCORE Oracle v3.1Document149 paginiSCORE Oracle v3.1ranusofiÎncă nu există evaluări
- Academy of TechnologyDocument2 paginiAcademy of TechnologyRanajit BiswasÎncă nu există evaluări
- Project Hamilton Phase 1 WhitepaperDocument44 paginiProject Hamilton Phase 1 WhitepaperGANESHÎncă nu există evaluări
- SAP PasswordDocument10 paginiSAP PasswordElena PuscuÎncă nu există evaluări
- L11 - Cryptographic Hash FunctionsDocument71 paginiL11 - Cryptographic Hash FunctionsTrịnh Phương QuangÎncă nu există evaluări
- Cryptanalysis of An Efficient Biometrics-Based Remote User Authentication Scheme Using Smart CardsDocument4 paginiCryptanalysis of An Efficient Biometrics-Based Remote User Authentication Scheme Using Smart Cardsvol2no3Încă nu există evaluări
- Private Key Hacking PDFDocument49 paginiPrivate Key Hacking PDFrqi11100% (5)
- Blockchain Dictionary: A Concise Guide to Key Blockchain TermsDocument2 paginiBlockchain Dictionary: A Concise Guide to Key Blockchain TermsVijay DinanathÎncă nu există evaluări
- Elliptic Curve Hierarchical Deterministic Private Key Sequences: Bitcoin Standards and Best PracticesDocument53 paginiElliptic Curve Hierarchical Deterministic Private Key Sequences: Bitcoin Standards and Best PracticesAngelescu ConstantinÎncă nu există evaluări
- Hybrid Model For Securing E-Commerce TransactionDocument7 paginiHybrid Model For Securing E-Commerce TransactionIJAET JournalÎncă nu există evaluări
- ACTUALTESTS Cisco 350-018 Exam Q and A 03 16 2005 PDFDocument204 paginiACTUALTESTS Cisco 350-018 Exam Q and A 03 16 2005 PDFStefan DumitrescuÎncă nu există evaluări
- Security & Anti-Forensics PDFDocument75 paginiSecurity & Anti-Forensics PDFCharly C. Gamao100% (1)
- CompTIA Security+ (SY0-501) Cert Prep:1 Threats, Attacks, and VulnerabilitiesDocument32 paginiCompTIA Security+ (SY0-501) Cert Prep:1 Threats, Attacks, and VulnerabilitiesMohannad JabaitiÎncă nu există evaluări
- Real Estat Agency Mobile ApplicationDocument39 paginiReal Estat Agency Mobile Applicationاحسن الغيثيÎncă nu există evaluări
- Chapter 12 - Hash and MAC AlgorithmsDocument17 paginiChapter 12 - Hash and MAC AlgorithmsPkumar ChoureÎncă nu există evaluări