Documente Academic
Documente Profesional
Documente Cultură
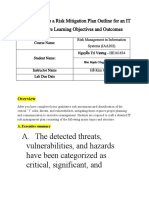
BTEC Level 3 Organisational Systems Security Assignment 1
Încărcat de
treyTitlu original
Drepturi de autor
Formate disponibile
Partajați acest document
Partajați sau inserați document
Vi se pare util acest document?
Este necorespunzător acest conținut?
Raportați acest documentDrepturi de autor:
Formate disponibile
BTEC Level 3 Organisational Systems Security Assignment 1
Încărcat de
treyDrepturi de autor:
Formate disponibile
(Organisational Systems Security)
IT & Business
Unit 7 (Organisational Systems Security)
Assignment 1
Date Set : 4/03/13
298392347.doc
Written By: Kemi Ajose
Verified By: Sharon Muncie
Review Date : 25/03/13
Date Due : 22/04/13
(Organisational Systems Security)
Learning outcomes to be partially or fully covered
On completion of this unit a learner should:
Understand the impact of potential threats to IT systems
Know how organisations can keep systems and data secure.
Understand the organisational issues affecting the security of IT
systems.
Grading criteria
To achieve the Pass criteria
7.P.1
Explain the impact of different types of threat on an organisation.
7.P.2
Describe how physical security measures can help keep systems
secure.
7.P.3
Describe how software and network security can keep systems and
data secure.
To achieve the Merit criteria
7.M.1
Discuss information security
7.M.2
Explain the operation and use of an encryption technique in ensuring
security of transmitted information.
To achieve the Distinction criteria
7.D.1
Discuss different ways of recovering from a disaster.
298392347.doc
Written By: Kemi Ajose
Verified By: Sharon Muncie
(Organisational Systems Security)
Know your threats (Part 1)
Scenario
You work as a junior technician for Your-Tech, a small IT support company
that provides software and hardware support to a number of small and
medium sized businesses.
Your-Tech receives a lot of phone calls from users about security issues so it
is hoped that having this information available to them will reduce the number
of calls. A line manager has asked you to write a short guide to IT security
threats and their impact on the organisations.
Task 1
a) Explain the impact of different types of threats on an organisation. P1
This guide should include:
Potential threats, e.g. malicious damage(internal & external), threats related
to ecommerce, counterfeit goods, technical failures, other e.g. human error,
and theft of equipment.
Malicious damage: internal, external, access causing damage, e.g. viruses.
Access without damage, specific examples e.g. phishing, identity theft,
piggybacking, hacking
Threats related to e-commerce e.g. website defacement, control of access
to data via third party suppliers; other e.g. denial of service attacks
Counterfeit Goods: products, at risk e.g. software DVDs games, music,
distribution. Mechanisms e.g. boot sales, peer to peer networks
Organisational impact: loss of service loss of business or income e.g.
through loss of customer records; increased costs; poor image
b) Discuss information security M1
Add a section to your guide that discusses information security; include
confidentiality, data integrity, data completeness and access to data.
Secure your threats (Part 2)
Scenario
You are to give a presentation to an organisation describing how to keep their
systems and data secure.
Task 2
c) Describe how physical security measures can help keep systems
secure. P2.
This should include locks, visitors passes; sign in/out systems,
biometrics e.g. retinal scans, fingerprint, voice recognition;
others e.g. guards, cable shielding
298392347.doc
Written By: Kemi Ajose
Verified By: Sharon Muncie
(Organisational Systems Security)
Discuss in your presentation all types of physical security that you have
learned.
d) Describe how software and network security can keep systems and
data secure. P3.
This should include call back, Handshaking, diskless networks,
use of backups, Audit logs, firewall configurations, Virus
checking software, use of VPNs, Intrusion detection systems,
password, Level of access to data, software updating.
e) In a report explain the way that data transmitted over a network can be
protected by encryption. M2
The techniques could include public and private key.
f)
Discuss different ways of recovering from a disaster. D1
This should include discussion of how and when e.g. backup
systems, whole system replacement, tiers of recovery could
be used.
298392347.doc
Written By: Kemi Ajose
Verified By: Sharon Muncie
(Organisational Systems Security)
Work to be submitted
A soft plastic folder with:
Unit Record Sheet
Assignment Activity Front Sheet
Title page
Contents page
Completed Tasks for assessment criteria P1, P2, P3, M1, M2 and D1.
Part 1 Report using word document that includes;
o P1: The impact of different types of threat on an organisation.
o M1: Discuss information security
o M2: Explain the operation and use of an encryption technique in
ensuring security of transmitted information.
Part 2 A PowerPoint Presentation that includes
o P2: Physical security measures can help keep systems secure.
o P3: Software and network security can keep systems and data
secure.
Bibliography, Reference, Sources and Website Page/s.
298392347.doc
Written By: Kemi Ajose
Verified By: Sharon Muncie
(Organisational Systems Security)
Recommended Sources:
Indicative reading for learners
Textbooks
Anderson, Jarvis, Kaye, Lawson, McGill, Phillips and Smith Information
Technology: BTEC Level 3 (Book 1, 2010) ISBN 978-1-846909-28-3
Beekman G and Quinn M J Computer Confluence Complete: and
Student CD 1st international edition
(Pearson Education, 2005) ISBN-10 1405835796, ISBN-13 9781405835794
Heathcote P A Level ICT revised edition (Payne Gallway, 2004)
ISBN-10 0953249085,
ISBN-13 978-0953249084
Websites
www.acm.org Association of Computing Machinery
www.bcs.org British Computing Society
www.bsa.org.uk Business Software Alliance
www.fast.org.uk Federation against Software Theft
www.ico.gov.uk Information Commissioners Office
298392347.doc
Written By: Kemi Ajose
Verified By: Sharon Muncie
S-ar putea să vă placă și
- Cybersecurity and Ethical Hacking: Exploring the Dark Art of Ethical Hacking and Penetration TestingDe la EverandCybersecurity and Ethical Hacking: Exploring the Dark Art of Ethical Hacking and Penetration TestingÎncă nu există evaluări
- MCS-054 Block-4Document87 paginiMCS-054 Block-4Kamal TiwariÎncă nu există evaluări
- Security AB Spring 2022 V2Document7 paginiSecurity AB Spring 2022 V2SARA ALABAHRAAÎncă nu există evaluări
- Securing Computer Systems: ObjectivesDocument32 paginiSecuring Computer Systems: Objectivesarun5918Încă nu există evaluări
- Learning Guide #29: Information Technology Support ServiceDocument28 paginiLearning Guide #29: Information Technology Support Serviceabenezer abitiÎncă nu există evaluări
- Security Summative Assignment Summer - 2022 - V2Document7 paginiSecurity Summative Assignment Summer - 2022 - V2M17Încă nu există evaluări
- Chapter 1: (Network Security) : PreambleDocument21 paginiChapter 1: (Network Security) : PreambleArras DaouÎncă nu există evaluări
- Cyber PresentationDocument5 paginiCyber Presentationceedosk1Încă nu există evaluări
- Chapter-9 Security and Privacy Architecture: Technological University (Meiktila) Department of Information TechnologyDocument19 paginiChapter-9 Security and Privacy Architecture: Technological University (Meiktila) Department of Information Technologyfna4463Încă nu există evaluări
- Debremarkos University School of Computing Information Security (Chapter One)Document20 paginiDebremarkos University School of Computing Information Security (Chapter One)tadesse yizengawÎncă nu există evaluări
- Hà Minh Chí (BKC12327) - Assignment 1 lần 1 - securityDocument39 paginiHà Minh Chí (BKC12327) - Assignment 1 lần 1 - securityChí Hà MinhÎncă nu există evaluări
- IM ch01Document11 paginiIM ch01Daniel ClarkÎncă nu există evaluări
- Updated (Week 1 & 2) - 1Document49 paginiUpdated (Week 1 & 2) - 1Muhammad Hassan AwanÎncă nu există evaluări
- Chapter 1 - Introduction To Network SecurityDocument47 paginiChapter 1 - Introduction To Network SecurityXendra AqeylaaÎncă nu există evaluări
- Security SpecsDocument8 paginiSecurity SpecsTee BeeÎncă nu există evaluări
- Prevention, Detection, Recovery E.T.CDocument5 paginiPrevention, Detection, Recovery E.T.Cmahmoud janÎncă nu există evaluări
- Final Report of IT SecurityDocument13 paginiFinal Report of IT Securitydntalk100% (1)
- Running Head: Cybersecurity 1Document6 paginiRunning Head: Cybersecurity 1Mayaka AmosÎncă nu există evaluări
- CSE4482 01 IntroductionDocument56 paginiCSE4482 01 IntroductionNagunuri SrinivasÎncă nu există evaluări
- Cyber Security Draft ModuleDocument24 paginiCyber Security Draft ModuleKasinsa EdwardÎncă nu există evaluări
- Cit 101Document22 paginiCit 101agapenunmi16Încă nu există evaluări
- 15: Security and Cyber LawsDocument49 pagini15: Security and Cyber LawsPixelÎncă nu există evaluări
- Network SecurityDocument53 paginiNetwork SecuritytsayeedctgÎncă nu există evaluări
- Assignment Front Sheet Qualification BTEC Level 5 HND Diploma in Computing Unit Number and Title Unit 5: Security Submission DateDocument11 paginiAssignment Front Sheet Qualification BTEC Level 5 HND Diploma in Computing Unit Number and Title Unit 5: Security Submission DateChopper Tony TonyÎncă nu există evaluări
- Lab6 IAA202Document18 paginiLab6 IAA202Đào Mạnh CôngÎncă nu există evaluări
- Security, Privacy Research Issues in VariousDocument16 paginiSecurity, Privacy Research Issues in VariousquijanodÎncă nu există evaluări
- SLM - Unit 01Document22 paginiSLM - Unit 01SureshÎncă nu există evaluări
- Computer Security Management Class WorkDocument67 paginiComputer Security Management Class WorkShan MayaÎncă nu există evaluări
- Cyber Security Seminar ProjectDocument29 paginiCyber Security Seminar ProjectSolomon SeyoumÎncă nu există evaluări
- Computer Security 1st EditedDocument56 paginiComputer Security 1st Edited974-Abhijeet MotewarÎncă nu există evaluări
- Risk Assessment of It Security Possible Solutions and Mechanisms To Control It Security Risk Unit 8: SecurityDocument15 paginiRisk Assessment of It Security Possible Solutions and Mechanisms To Control It Security Risk Unit 8: SecurityGilian kipkosgeiÎncă nu există evaluări
- Computer Security Module@2022 - 23Document51 paginiComputer Security Module@2022 - 23senawagari07fÎncă nu există evaluări
- Section 2 Security-PolicyDocument18 paginiSection 2 Security-Policyahmadjoe04Încă nu există evaluări
- Chapter 1fundamental of Software SecurityDocument53 paginiChapter 1fundamental of Software SecurityAbiyot egataÎncă nu există evaluări
- L7Document55 paginiL7Faith NyongesaÎncă nu există evaluări
- IT NS 1 - Chapter 1c Operational IssuesDocument5 paginiIT NS 1 - Chapter 1c Operational IssuesGALAPON FRANCISÎncă nu există evaluări
- Day 1Document9 paginiDay 1Kenneth IserhienrhienÎncă nu există evaluări
- Guide LineDocument4 paginiGuide Linehtdrqdxqk7Încă nu există evaluări
- CP5603 Lecture 01 2011-07-26Document90 paginiCP5603 Lecture 01 2011-07-26Suhas Sajitha KailasÎncă nu există evaluări
- IT SecurityDocument18 paginiIT SecurityMestar PerfectÎncă nu există evaluări
- Fundamental Common Technologies MIBA UniversityDocument12 paginiFundamental Common Technologies MIBA UniversityBarty WaineÎncă nu există evaluări
- Computer Security: Introduction: January 3, 2020Document24 paginiComputer Security: Introduction: January 3, 2020Rakesh MatamÎncă nu există evaluări
- CH 10 Privacy and SecurityDocument27 paginiCH 10 Privacy and SecurityMayank ParekhÎncă nu există evaluări
- Cybersecurity IntroductionDocument8 paginiCybersecurity IntroductionArman KoriÎncă nu există evaluări
- Chapter 1 2022Document60 paginiChapter 1 2022Nasis DerejeÎncă nu există evaluări
- Network SecurityDocument10 paginiNetwork SecurityAjao GafarÎncă nu există evaluări
- Chap1 Introduction To Information SecurityDocument14 paginiChap1 Introduction To Information SecurityNitish LokhandeÎncă nu există evaluări
- Network Security Exam Short QuestionsDocument6 paginiNetwork Security Exam Short QuestionsDiom ShresthaÎncă nu există evaluări
- Iaa202 Lab6Document17 paginiIaa202 Lab6Dao Manh Cong (K16HL)Încă nu există evaluări
- Unit 1 IT Systems Protecting Data and InformationDocument9 paginiUnit 1 IT Systems Protecting Data and InformationxfeudalÎncă nu există evaluări
- Design and Implementation of Network SecurityDocument41 paginiDesign and Implementation of Network SecurityManu100% (1)
- 32pdf PDFDocument10 pagini32pdf PDFfaisal saghirÎncă nu există evaluări
- Faculty of Computing and Information TechnologyDocument22 paginiFaculty of Computing and Information TechnologyFred JapÎncă nu există evaluări
- Nota Kuliah 1Document6 paginiNota Kuliah 1joezanderÎncă nu există evaluări
- Chapert 3 and 4 PDF-1Document26 paginiChapert 3 and 4 PDF-1Tora SarkarÎncă nu există evaluări
- International Journal of Multimedia and Ubiquitous EngineeringDocument10 paginiInternational Journal of Multimedia and Ubiquitous EngineeringPeter Osundwa KitekiÎncă nu există evaluări
- Information SecurityDocument6 paginiInformation SecurityMD Nahidur RahmanÎncă nu există evaluări
- Assignment #2 ISDocument3 paginiAssignment #2 ISNarender Singh ChauhanÎncă nu există evaluări
- Network Security Evaluation Based On Information Security: Nayunipatruni SumanDocument5 paginiNetwork Security Evaluation Based On Information Security: Nayunipatruni SumanwisdombasedcomputingÎncă nu există evaluări
- IT10 Module1 MelendresDocument7 paginiIT10 Module1 MelendresValerie MelendresÎncă nu există evaluări
- Name: Course: BTEC National Diploma Unit 42: Spreadsheet Modelling Test Log TemplateDocument5 paginiName: Course: BTEC National Diploma Unit 42: Spreadsheet Modelling Test Log TemplatetreyÎncă nu există evaluări
- Read MeyppppppppppppppoooooDocument2 paginiRead MeyppppppppppppppoooooAnonymous 7dsX2F8nÎncă nu există evaluări
- Roles: Communications and Employability For ITDocument1 paginăRoles: Communications and Employability For ITtreyÎncă nu există evaluări
- Group Profile Student FormDocument2 paginiGroup Profile Student FormtreyÎncă nu există evaluări
- Nat Agepseudocode SP 199900Document1 paginăNat Agepseudocode SP 199900treyÎncă nu există evaluări
- Progress To Date Checklist - Information System. Unit 3 - Lance StanfordDocument2 paginiProgress To Date Checklist - Information System. Unit 3 - Lance StanfordtreyÎncă nu există evaluări
- Ed Qual SS 2013 Update-1Document20 paginiEd Qual SS 2013 Update-1treyÎncă nu există evaluări
- Things To Improve: Trey Ludovice PDP IT System SupportDocument1 paginăThings To Improve: Trey Ludovice PDP IT System SupporttreyÎncă nu există evaluări
- Observation Sheet Group: Communications and Employability For ITDocument1 paginăObservation Sheet Group: Communications and Employability For ITtreyÎncă nu există evaluări
- Unit 6: P. 6 - Use Appropriate Tools To Design A Solution To A Defined RequirementDocument4 paginiUnit 6: P. 6 - Use Appropriate Tools To Design A Solution To A Defined RequirementtreyÎncă nu există evaluări
- Unit 1 P4 Demonstrate A Range of Effective Interpersonal SkillsDocument1 paginăUnit 1 P4 Demonstrate A Range of Effective Interpersonal SkillstreyÎncă nu există evaluări
- BTEC Level 3 Computer Systems Assignment 3 IVDocument10 paginiBTEC Level 3 Computer Systems Assignment 3 IVtreyÎncă nu există evaluări
- Comms Employ Assign 1 2013Document7 paginiComms Employ Assign 1 2013treyÎncă nu există evaluări
- Unit 06 Assignment - Software Design Development 13.14Document10 paginiUnit 06 Assignment - Software Design Development 13.14treyÎncă nu există evaluări
- Key Components For A Workstation To Connect To A Network P3 Unit 9Document1 paginăKey Components For A Workstation To Connect To A Network P3 Unit 9treyÎncă nu există evaluări
- Annotated BibliographyDocument3 paginiAnnotated Bibliographyapi-278315498Încă nu există evaluări
- Group 12 - Contributors: Hajrah Choudhry Vu Pham Nathaniel Lovgren Roozah Khan Joycelyn Joo Teddy SadowskiDocument9 paginiGroup 12 - Contributors: Hajrah Choudhry Vu Pham Nathaniel Lovgren Roozah Khan Joycelyn Joo Teddy SadowskiVũ Khánh PhạmÎncă nu există evaluări
- Cybersecurity Competency Framework - Reference - LinksDocument4 paginiCybersecurity Competency Framework - Reference - LinksGlenn Lelis TabucanonÎncă nu există evaluări
- TH ResourcesDocument3 paginiTH Resourcesz4akmalzÎncă nu există evaluări
- DR APJ Abdul KalamDocument1 paginăDR APJ Abdul KalamParth Goyal100% (1)
- Qrmo Qrma QRMP Qcro QRGP: BulletinDocument4 paginiQrmo Qrma QRMP Qcro QRGP: BulletinIlham Ahmad RosyadiÎncă nu există evaluări
- 1 CorpsDocument206 pagini1 Corpssameera prasathÎncă nu există evaluări
- RRL 6Document15 paginiRRL 6shannen kate acostaÎncă nu există evaluări
- Tuvit Whitepaper Data Center Tsi En50600Document12 paginiTuvit Whitepaper Data Center Tsi En50600saba0707Încă nu există evaluări
- Security Fence and Gates PDFDocument83 paginiSecurity Fence and Gates PDFObrejaÎncă nu există evaluări
- Cybersecurity StrategyDocument15 paginiCybersecurity StrategyMohamed Garba MoussaÎncă nu există evaluări
- Vatican City (C & D) )Document5 paginiVatican City (C & D) )Natoy NatoyÎncă nu există evaluări
- Question BankDocument1 paginăQuestion Bankamritranabhat09Încă nu există evaluări
- Data Security PowerpointDocument25 paginiData Security Powerpointleanna hoyteÎncă nu există evaluări
- Analisis Keamanan Web New Kuta Golf Menggunakan Metode Vulnerability Assessments Dan Perhitungan Security MetriksDocument12 paginiAnalisis Keamanan Web New Kuta Golf Menggunakan Metode Vulnerability Assessments Dan Perhitungan Security MetriksRifky LanaÎncă nu există evaluări
- Ethics AND Armed Forces: Conflict Zone Cyberspace: Prospects For Security and PeaceDocument8 paginiEthics AND Armed Forces: Conflict Zone Cyberspace: Prospects For Security and PeaceAhlem bkhÎncă nu există evaluări
- (White Paper) Multi-Domain Battle: Combined Arms For 21st CenturyDocument4 pagini(White Paper) Multi-Domain Battle: Combined Arms For 21st CenturyA Luta Continua100% (1)
- Fortinet Certification PathDocument1 paginăFortinet Certification Pathtray zeroÎncă nu există evaluări
- Antony Kungu - Final Project AssignmentDocument11 paginiAntony Kungu - Final Project Assignmentapi-420816837Încă nu există evaluări
- Types of HackersDocument2 paginiTypes of Hackersgeetha samynathanÎncă nu există evaluări
- Mutually Assured DestructionDocument11 paginiMutually Assured DestructionAustin MiceliÎncă nu există evaluări
- 06-Keymaking and RekeyingDocument99 pagini06-Keymaking and Rekeyingapi-3777781100% (5)
- Security Guard Assessment and Validation Form - Rev 0Document2 paginiSecurity Guard Assessment and Validation Form - Rev 0kartikeya RanjanÎncă nu există evaluări
- Fy 2021 Dhs Bib Web VersionDocument106 paginiFy 2021 Dhs Bib Web VersionAKADEMY OfficialÎncă nu există evaluări
- ICS Session 04. LECTURE PPT - Ch1. The Need For Cybersecurity v1Document8 paginiICS Session 04. LECTURE PPT - Ch1. The Need For Cybersecurity v1dusexÎncă nu există evaluări
- TB 380-41 Security Procedures For Safeguarding, Accounting and Supply Control of Comsec MaterialDocument248 paginiTB 380-41 Security Procedures For Safeguarding, Accounting and Supply Control of Comsec Materialsergey62Încă nu există evaluări
- Hanazaki Et Al (2012) - Livelihood Diversity, Food Security and ResilienceDocument12 paginiHanazaki Et Al (2012) - Livelihood Diversity, Food Security and ResilienceOnivaldo da Rocha Mendes FilhoÎncă nu există evaluări
- International Journal of Multimedia and Ubiquitous EngineeringDocument10 paginiInternational Journal of Multimedia and Ubiquitous EngineeringPeter Osundwa KitekiÎncă nu există evaluări
- Welcome To Quorum Cyber's Managed Security Operations Centre (SOC)Document2 paginiWelcome To Quorum Cyber's Managed Security Operations Centre (SOC)Com DigfulÎncă nu există evaluări
- The Digital Marketing Handbook: A Step-By-Step Guide to Creating Websites That SellDe la EverandThe Digital Marketing Handbook: A Step-By-Step Guide to Creating Websites That SellEvaluare: 5 din 5 stele5/5 (6)
- Defensive Cyber Mastery: Expert Strategies for Unbeatable Personal and Business SecurityDe la EverandDefensive Cyber Mastery: Expert Strategies for Unbeatable Personal and Business SecurityEvaluare: 5 din 5 stele5/5 (1)
- React.js Design Patterns: Learn how to build scalable React apps with ease (English Edition)De la EverandReact.js Design Patterns: Learn how to build scalable React apps with ease (English Edition)Încă nu există evaluări
- The Designer’s Guide to Figma: Master Prototyping, Collaboration, Handoff, and WorkflowDe la EverandThe Designer’s Guide to Figma: Master Prototyping, Collaboration, Handoff, and WorkflowÎncă nu există evaluări
- Grokking Algorithms: An illustrated guide for programmers and other curious peopleDe la EverandGrokking Algorithms: An illustrated guide for programmers and other curious peopleEvaluare: 4 din 5 stele4/5 (16)
- How to Do Nothing: Resisting the Attention EconomyDe la EverandHow to Do Nothing: Resisting the Attention EconomyEvaluare: 4 din 5 stele4/5 (421)
- Ten Arguments for Deleting Your Social Media Accounts Right NowDe la EverandTen Arguments for Deleting Your Social Media Accounts Right NowEvaluare: 4 din 5 stele4/5 (388)
- Practical Industrial Cybersecurity: ICS, Industry 4.0, and IIoTDe la EverandPractical Industrial Cybersecurity: ICS, Industry 4.0, and IIoTÎncă nu există evaluări
- More Porn - Faster!: 50 Tips & Tools for Faster and More Efficient Porn BrowsingDe la EverandMore Porn - Faster!: 50 Tips & Tools for Faster and More Efficient Porn BrowsingEvaluare: 3.5 din 5 stele3.5/5 (24)
- CISM Certified Information Security Manager Study GuideDe la EverandCISM Certified Information Security Manager Study GuideÎncă nu există evaluări
- HTML5 and CSS3 Masterclass: In-depth Web Design Training with Geolocation, the HTML5 Canvas, 2D and 3D CSS Transformations, Flexbox, CSS Grid, and More (English Edition)De la EverandHTML5 and CSS3 Masterclass: In-depth Web Design Training with Geolocation, the HTML5 Canvas, 2D and 3D CSS Transformations, Flexbox, CSS Grid, and More (English Edition)Încă nu există evaluări
- Nine Algorithms That Changed the Future: The Ingenious Ideas That Drive Today's ComputersDe la EverandNine Algorithms That Changed the Future: The Ingenious Ideas That Drive Today's ComputersEvaluare: 5 din 5 stele5/5 (7)
- Branding: What You Need to Know About Building a Personal Brand and Growing Your Small Business Using Social Media Marketing and Offline Guerrilla TacticsDe la EverandBranding: What You Need to Know About Building a Personal Brand and Growing Your Small Business Using Social Media Marketing and Offline Guerrilla TacticsEvaluare: 5 din 5 stele5/5 (32)
- Tor Darknet Bundle (5 in 1): Master the Art of InvisibilityDe la EverandTor Darknet Bundle (5 in 1): Master the Art of InvisibilityEvaluare: 4.5 din 5 stele4.5/5 (5)
- Evaluation of Some Websites that Offer Virtual Phone Numbers for SMS Reception and Websites to Obtain Virtual Debit/Credit Cards for Online Accounts VerificationsDe la EverandEvaluation of Some Websites that Offer Virtual Phone Numbers for SMS Reception and Websites to Obtain Virtual Debit/Credit Cards for Online Accounts VerificationsEvaluare: 5 din 5 stele5/5 (1)
- Microservices Patterns: With examples in JavaDe la EverandMicroservices Patterns: With examples in JavaEvaluare: 5 din 5 stele5/5 (2)
- The Internet Con: How to Seize the Means of ComputationDe la EverandThe Internet Con: How to Seize the Means of ComputationEvaluare: 5 din 5 stele5/5 (6)
- Summary of Traffic Secrets: by Russell Brunson - The Underground Playbook for Filling Your Websites and Funnels with Your Dream Customers - A Comprehensive SummaryDe la EverandSummary of Traffic Secrets: by Russell Brunson - The Underground Playbook for Filling Your Websites and Funnels with Your Dream Customers - A Comprehensive SummaryÎncă nu există evaluări
- Curating Content Bundle, 2 in 1 Bundle: Content Machine and Manage ContentDe la EverandCurating Content Bundle, 2 in 1 Bundle: Content Machine and Manage ContentEvaluare: 5 din 5 stele5/5 (6)
- TikTok Algorithms 2024 $15,000/Month Guide To Escape Your Job And Build an Successful Social Media Marketing Business From Home Using Your Personal Account, Branding, SEO, InfluencerDe la EverandTikTok Algorithms 2024 $15,000/Month Guide To Escape Your Job And Build an Successful Social Media Marketing Business From Home Using Your Personal Account, Branding, SEO, InfluencerEvaluare: 4 din 5 stele4/5 (4)