Documente Academic
Documente Profesional
Documente Cultură
An SSL Decryption 4035
Încărcat de
Tryphon Tso-hunterTitlu original
Drepturi de autor
Formate disponibile
Partajați acest document
Partajați sau inserați document
Vi se pare util acest document?
Este necorespunzător acest conținut?
Raportați acest documentDrepturi de autor:
Formate disponibile
An SSL Decryption 4035
Încărcat de
Tryphon Tso-hunterDrepturi de autor:
Formate disponibile
Application Note
SSL Decryption
Introduction
SSL encryption is the cornerstone technology that makes the Internet secure. Email, e-commerce, voice-over-IP, online banking, remote
health, and countless other services are kept secure with SSL. Unfortunately, most of that traffic goes uninspected because many
security and performance monitoring tools lack the ability to see inside the encrypted sessions. Monitoring application performance
and network usage patterns becomes impossible if you cannot determine which applications are running over the network. Even worse,
malware can create SSL sessions to hide its activity, confident that security tools will neither inspect nor block the traffic. The very
technology that makes the Web secure can become a threat vector.
Decrypting SSL traffic requires knowledge of the keys used for encryption. The public keys are clearly visible at the start of the
transaction, but access to the private keys is controlled by the administrator.
Key Customer Applications
SSL Decryption is required for a variety of applications:
Malware Detection: Once malware exploits a host, it can complete the kill chain using SSL transactions
Data Loss Prevention: Whether initiated by malware or a user from inside the corporate firewall, confidential data and files can be
encrypted and leaked using SSL connections
Application Performance Monitoring: Key business applications use SSL to ensure authentication, but this obscures data required
for proper monitoring
Cloud Services Monitoring: Secure services running in the cloud, including Web applications, all look the same at the TCP/IP layer
and it is not until the SSL sessions are decrypted that they can be differentiated and monitored
Existing Solutions
SSL decryption is available directly on some monitoring tools. However, those solutions tend to cause a severe performance degradation
and are also very expensive. Offloading SSL decryption not only allows the tool to return to full performance, but also eliminates
the need to have multiple decryption licenses for multiple tools. Furthermore, SSL decryption on a specific security appliance, for
example, does not help with other tools, such as application performance monitoring; Gigamon can supply decrypted traffic to both
simultaneously. Clearly, by delivering SSL decryption as a common service to the connected monitoring and security tools, the overall
efficiency, security and performance of the infrastructure can be maximized.
Existing inline technologies, such as SSL proxies and application load balancers, provide SSL decryption, but they are not optimized for a
visibility architecture. They lack the scalability to handle traffic from multiple TAPs across the network or to filter and replicate decrypted
to multiple monitoring tools. With limited modularity or extensibility, increasing SSL throughput often requires new hardware. Lastly,
they provide no visibility functionality or traffic intelligence for non-encrypted traffic.
2014-2015 Gigamon. All rights reserved.
Application Note: SSL Decryption
Gigamon Solution
Given that Gigamons Unified Visibility Fabric has access to the bidirectional traffic, it has the ability to observe the exchange of public
keys at the start of the transaction. Once the administrator loads the private keys, they are securely stored on the system. The power
of the GigaSMART traffic intelligence engine can then decrypt the traffic and forward it to tools for analysis. Each GigaSMART module
contains high-performance compute engines that have hardware performance accelerators to handle SSL traffic.
SSL Decryption is not limited to specific ingress ports or where the GigaSMART engine is located within the Visibility Fabric. Any traffic
received on any network port in the cluster of Gigamon Visibility Fabric nodes can take advantage of SSL Decryption. And that traffic
can be sent to any tool ports in the cluster. This is an important attribute because not every node in the cluster needs to have the SSL
Decryption capability. Additional Flow Mapping technology and/or GigaSMART applications can also be applied to decrypted traffic.
Furthermore, additional SSL Decryption throughput can be achieved by adding more GigaSMART modules to the cluster, allowing
inspection to grow as SSL processing needs increase.
Because SSL traffic can contain sensitive user data, special care must be taken to ensure that this data remains secure. After decrypting
the packets, they can be sliced to remove irrelevant or private payload data. Alternatively, fields within the payload can be masked.
In both cases, private data is never stored, read, or analyzed by the monitoring tools. This helps keep networks within regulatory
compliance and greatly simplifies the auditing process.
Proper handling of the private keys is vital to maintain security compliance. Gigamon only allows keys to be uploaded, changed,
or deleted by users designated by the administrator. Keys are encrypted using a special password which is distinct from the generic
system admin password.
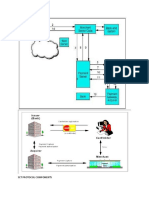
Figure 1: The steps to SSL Decryption
The Steps to SSL Decryption
3
2
Visibility Fabric
4
1. Tap the network and connect it to Gigamons
Visibility Fabric.
2. Select which flows to monitor and the
GigaSMART engine will identify the exchange
of public keys at the start of the transaction.
3. The private keys, which have been uploaded
by the administrator, are encrypted and stored
under tight password and role-based access controls.
4. GigaSMART then uses the private and public
keys to decrypt the SSL traffic.
5. The clear packets can be sent directly to your
monitoring tools or additional Flow Mapping
and GigaSMART operations can be applied.
2014-2015 Gigamon. All rights reserved.
Application Note: SSL Decryption
Key Features
First in the Industry to Integrate SSL Decryption into a Unified Visibility Fabric
Decrypt traffic from anywhere within the Visibility Fabric and send to any connected tools
With Flow Mapping technology, direct any user-defined flows, not just those on port 443, for decryption
SSL3, TLS 1.0, 1.1 and 1.2 Support
Public key: RSA
Symmetric key algorithms: AES, 3DES, DES, RC4, CAMELLIA, SEED, IDEA
Hashing algorithms: MD5, SHA1, SHA2
Supported applications: HTTPS, FTPS and SMTP, IMAP, POP3 with StartTLS
Supported key sizes: 128, 256, 512, 1024, 2048, and 4096
SSL Decryption Statistics
Idle sessions and reusable keys
Session-level Stats: packets, discards, errored packets, resumptions
Secure Storage of Private Keys
Encryption with independent password
Restricted key access based on role-based access controls
Key Benefits
Obtain Visibility to Encrypted Traffic
Enable malware detection, intrusion detection, data loss prevention, network forensics
Send clear traffic to application performance management, network performance monitoring, customer experience
management tools
Integrate SSL Inspection into a Multi-Tiered Security Solution
Prevent malware from hiding within uninspected SSL sessions
Forward any traffic that does not match known flows to GigaSMART for decryption
Decrypt traffic from the cloud and/or remote sites
Improve Tool Performance
Offload SSL Decryption to the Visibility Fabric, freeing tool resources for packet analysis
Apply decryption once for all tools rather than separately on each tool
Chain Multiple GigaSMART Applications Together
Terminate tunnels sent from GigaVUE-VM, remote sites, and/or ERSPAN
Apply Flow Mapping and SSL Decryption
Use Adaptive Packet Filtering for L7-based packet forwarding
Obscure private data with packet slicing or masking
2014-2015 Gigamon. All rights reserved.
Feature Brief: SSL Decryption
Physical
Web server connect
requests to NPM/CEM
Remote site
traffic to DLP
Virtual
Flow Mapping
GigaVUE-VM
SSL Decryption
Adaptive Packet
Filtering
Tunnel
Termination
GigaVUE-VM
East-West traffic between
virtual workloads to IPS
Visibility Fabric
Figure 2: Combine SSL Decryption with GigaSMART services such as tunnel de-encapsulation and Adaptive
Packet Filtering
Summary
SSL is a vital Internet technology upon which more and more applications will rely. However, it severely limits visibility for both
performance and security monitoring. The growing security threat posed by uninspected SSL sessions increases the urgency for
inspecting SSL traffic. By decrypting SSL traffic for out-of-band monitoring Gigamon provides visibility where none existed. Rather than
turning a blind eye to SSL traffic, the full capabilities of Flow Mapping technology and GigaSMART traffic intelligence can be applied.
Decrypting SSL is a tremendous processing burden for monitoring tools that do it themselves; this greatly inhibits tool performance
and increases the cost of monitoring. By supplying clear, decrypted traffic to multiple tools, Gigamon can be implemented to provide
immediate value and return on investment in capital expenditure, licensing fees, and management costs.
About Gigamon
Gigamon provides an intelligent Unified Visibility Fabric to enable the management of increasingly complex networks. Gigamon
technology empowers infrastructure architects, managers and operators with pervasive visibility and control of traffic across both
physical and virtual environments without affecting the performance or stability of the production network. Through patented
technologies, centralized management and a portfolio of high availability and high density fabric nodes, network traffic is intelligently
delivered to management, monitoring and security systems. Gigamon solutions have been deployed globally across enterprise, data
centers and service providers, including over half of the Fortune 100 and dozens of government and state and local agencies.
For more information about the Gigamon Unified Visibility Fabric visit: www.gigamon.com
2014-2015 Gigamon. All rights reserved. Gigamon and the Gigamon logo are trademarks of Gigamon in the United States and/or
other countries. Gigamon trademarks can be found at www.gigamon.com/legal-trademarks. All other trademarks are the trademarks
of their respective owners. Gigamon reserves the right to change, modify, transfer, or otherwise revise this publication without notice.
3300 Olcott Street, Santa Clara, CA 95054 USA | +1 (408) 831-4000 | www.gigamon.com
4035-03 07/15
S-ar putea să vă placă și
- Symantec SSL Visibility Appliance: Data SheetDocument6 paginiSymantec SSL Visibility Appliance: Data SheetDebojit GoswamiÎncă nu există evaluări
- SSL Visibility Appliance enDocument4 paginiSSL Visibility Appliance enDebojit GoswamiÎncă nu există evaluări
- Encrypted Threat Protection: White PaperDocument7 paginiEncrypted Threat Protection: White PaperswsloanÎncă nu există evaluări
- Bcs Ds SSL Visibility SV800-SV1800-SV2800-SV3800 en v4fDocument3 paginiBcs Ds SSL Visibility SV800-SV1800-SV2800-SV3800 en v4fPrateek PorwalÎncă nu există evaluări
- SSL Decryption - Uncovering The New Infrastructure Blind Spot - Gigamon WhitepaperDocument6 paginiSSL Decryption - Uncovering The New Infrastructure Blind Spot - Gigamon WhitepaperGigamonÎncă nu există evaluări
- The F5 SSL Orchestrator and Cisco Firepower SolutionDocument39 paginiThe F5 SSL Orchestrator and Cisco Firepower Solutionalways_redÎncă nu există evaluări
- SSL VPN CheckpointDocument24 paginiSSL VPN CheckpointTruong LanÎncă nu există evaluări
- F5 SSL Orchestrator and Symantec DLP: SSL Visibility and Content AdaptionDocument26 paginiF5 SSL Orchestrator and Symantec DLP: SSL Visibility and Content Adaptionalways_redÎncă nu există evaluări
- The F5 SSL Orchestrator and Palo Alto Networks Next-Gen Firewall SolutionDocument39 paginiThe F5 SSL Orchestrator and Palo Alto Networks Next-Gen Firewall Solutionalways_redÎncă nu există evaluări
- F5 SSL Orchestrator and Fireeye NX: SSL Visibility With Service ChainingDocument20 paginiF5 SSL Orchestrator and Fireeye NX: SSL Visibility With Service Chainingalways_redÎncă nu există evaluări
- Pa 3200 SeriesDocument4 paginiPa 3200 SeriesJackkyz RockkerzÎncă nu există evaluări
- Decryption Why Where and HowDocument6 paginiDecryption Why Where and HowfanvantanÎncă nu există evaluări
- Decrypting SSL/TLS Traffic For Hidden Threats Detection: Conference PaperDocument5 paginiDecrypting SSL/TLS Traffic For Hidden Threats Detection: Conference Paperlai khoiÎncă nu există evaluări
- Pa 5200 SeriesDocument4 paginiPa 5200 Serieszain jamalÎncă nu există evaluări
- PA-5200 Series: HighlightsDocument4 paginiPA-5200 Series: HighlightsvlimbadiÎncă nu există evaluări
- pa-7500Document5 paginipa-7500sonyalmafittÎncă nu există evaluări
- Highlights: by Palo Alto Networks - PA-220 - DatasheetDocument4 paginiHighlights: by Palo Alto Networks - PA-220 - DatasheetvlimbadiÎncă nu există evaluări
- Ixia-SV-WP-Role of Active SSL DecryptionDocument7 paginiIxia-SV-WP-Role of Active SSL Decryptionliuyq7809Încă nu există evaluări
- Security ProtocolsDocument4 paginiSecurity Protocolsapi-3701346Încă nu există evaluări
- Bcs Ds BlueCoat Encrypted TAP en v1dDocument2 paginiBcs Ds BlueCoat Encrypted TAP en v1dNancy DrewerÎncă nu există evaluări
- Advanced Firewall 2016 Web enDocument3 paginiAdvanced Firewall 2016 Web enAlberto FernandezÎncă nu există evaluări
- Zcertificate Intelligence Center DatasheetDocument3 paginiZcertificate Intelligence Center Datasheetcharanmann9165Încă nu există evaluări
- pa-3400-seriesDocument7 paginipa-3400-seriessonyalmafittÎncă nu există evaluări
- Pa 3200 SeriesDocument4 paginiPa 3200 SeriesBatkhishig Tumen-OidovÎncă nu există evaluări
- Ipsec and SSL VPN Deployment Considerations: in This DocumentDocument8 paginiIpsec and SSL VPN Deployment Considerations: in This DocumentGiorgos FotopoulosÎncă nu există evaluări
- pa-5450-seriesDocument7 paginipa-5450-seriessonyalmafittÎncă nu există evaluări
- Pa 5200 SeriesDocument4 paginiPa 5200 SeriesAlberto Huamani CanchizÎncă nu există evaluări
- Pa 800 DatasheetDocument4 paginiPa 800 DatasheettxÎncă nu există evaluări
- E-Commerce Security Best PracticesDocument19 paginiE-Commerce Security Best PracticesNess Wadia College of Coomerce PuneÎncă nu există evaluări
- SecureSpan SOA Gateway Gateway & Software AGDocument4 paginiSecureSpan SOA Gateway Gateway & Software AGLayer7TechÎncă nu există evaluări
- Securing .NET Web Services with SSL: How to Protect “Data in Transit” between Client and Remote ServerDe la EverandSecuring .NET Web Services with SSL: How to Protect “Data in Transit” between Client and Remote ServerÎncă nu există evaluări
- Pa 800Document4 paginiPa 800Batkhishig Tumen-OidovÎncă nu există evaluări
- Best Practices DecryptionDocument5 paginiBest Practices DecryptionPartha DashÎncă nu există evaluări
- Pa 220Document4 paginiPa 220Abel De Los SantosÎncă nu există evaluări
- SSL Insight Hardening and Best Practices GuideDocument16 paginiSSL Insight Hardening and Best Practices Guideradix82Încă nu există evaluări
- SSL Offloading Relieves Server CPU LoadDocument2 paginiSSL Offloading Relieves Server CPU Loadsyed_engrÎncă nu există evaluări
- Architecture, Design, Data Storage and Network RequirementsDocument27 paginiArchitecture, Design, Data Storage and Network RequirementsThuy PhamÎncă nu există evaluări
- Pa 5200 SeriesDocument6 paginiPa 5200 SeriesnnÎncă nu există evaluări
- CISSP Revision NotesDocument36 paginiCISSP Revision NotesAman DeepÎncă nu există evaluări
- Mobile App Security Checklist enDocument30 paginiMobile App Security Checklist enTalo NguyenÎncă nu există evaluări
- Secure Networking 101 MACsec, IPsec, and SSL BasicsDocument10 paginiSecure Networking 101 MACsec, IPsec, and SSL BasicsazertyÎncă nu există evaluări
- Mobile App Security Checklist EsDocument30 paginiMobile App Security Checklist EsIsrael FloresÎncă nu există evaluări
- Pa 5400 SeriesDocument6 paginiPa 5400 Seriesw.meloÎncă nu există evaluări
- Globalprotect Cloud Service DsDocument4 paginiGlobalprotect Cloud Service DssasÎncă nu există evaluări
- Sa Series SSL VPN AppliancesDocument12 paginiSa Series SSL VPN AppliancesYeng Yee NgÎncă nu există evaluări
- Cisco ASA V Palo Alto ComparisonDocument1 paginăCisco ASA V Palo Alto ComparisonProdec_Networks100% (1)
- Transport Layer Protection Cheat SheetDocument6 paginiTransport Layer Protection Cheat SheetRoman PotapovÎncă nu există evaluări
- Mobile App Security Checklist enDocument30 paginiMobile App Security Checklist enHiko KikoÎncă nu există evaluări
- Pa 5200 SeriesDocument6 paginiPa 5200 SeriesJonathan QuilacioÎncă nu există evaluări
- Secure Socket LayerDocument14 paginiSecure Socket LayerbetoplapaÎncă nu există evaluări
- Blue Coat Product OverviewDocument6 paginiBlue Coat Product OverviewBrijesh BhatiyaÎncă nu există evaluări
- Ssl/Tls Trends, Practices, and Futures: Brian A. Mchenry, Security Solutions Architect @bamchenryDocument34 paginiSsl/Tls Trends, Practices, and Futures: Brian A. Mchenry, Security Solutions Architect @bamchenryDhananjai SinghÎncă nu există evaluări
- Firewall Features Overview PDFDocument5 paginiFirewall Features Overview PDFElliott longÎncă nu există evaluări
- Security in e - CommerceDocument4 paginiSecurity in e - CommerceAlex T BinoyÎncă nu există evaluări
- Achieve High-Performance SSL Visibility and Inspection With FortiadcDocument3 paginiAchieve High-Performance SSL Visibility and Inspection With Fortiadclai khoiÎncă nu există evaluări
- Mpki SSL Services Agreement Service Description PDFDocument15 paginiMpki SSL Services Agreement Service Description PDFDlablo Auguts ThabluechaiÎncă nu există evaluări
- Secure Data Exchange Via HSMDocument3 paginiSecure Data Exchange Via HSMLayer7TechÎncă nu există evaluări
- Oil Gas Industry Solution BriefDocument3 paginiOil Gas Industry Solution BriefZahra GhÎncă nu există evaluări
- Bank Reduces Security Threats by Using SSL DecryptionDocument4 paginiBank Reduces Security Threats by Using SSL Decryptionlai khoiÎncă nu există evaluări
- SSL VPN : Understanding, evaluating and planning secure, web-based remote accessDe la EverandSSL VPN : Understanding, evaluating and planning secure, web-based remote accessÎncă nu există evaluări
- Inner Class in JavaDocument15 paginiInner Class in JavaTryphon Tso-hunterÎncă nu există evaluări
- A Design Oscillator Baed PUF On FPGADocument6 paginiA Design Oscillator Baed PUF On FPGATryphon Tso-hunterÎncă nu există evaluări
- State-Of-cybersecurity Res Eng 0316Document23 paginiState-Of-cybersecurity Res Eng 0316Tryphon Tso-hunterÎncă nu există evaluări
- VN Enisa Stage 2015 01Document4 paginiVN Enisa Stage 2015 01Tryphon Tso-hunterÎncă nu există evaluări
- Lab5 Zybo XilinxDocument10 paginiLab5 Zybo XilinxTryphon Tso-hunterÎncă nu există evaluări
- The Walrasian Output Beats The MarketsDocument4 paginiThe Walrasian Output Beats The MarketsTryphon Tso-hunterÎncă nu există evaluări
- A Robust and Efficient Detection Model of DDoS Attack For Cloud ServicesDocument14 paginiA Robust and Efficient Detection Model of DDoS Attack For Cloud ServicesTryphon Tso-hunterÎncă nu există evaluări
- εισαγωγή στην θεωρία του ρίσκουDocument20 paginiεισαγωγή στην θεωρία του ρίσκουTryphon Tso-hunterÎncă nu există evaluări
- Social Semiotics History Is Never SureDocument11 paginiSocial Semiotics History Is Never SureTryphon Tso-hunterÎncă nu există evaluări
- Eu DirectiveDocument3 paginiEu DirectiveTryphon Tso-hunterÎncă nu există evaluări
- νομισματική θεωρία και πολιτική μέρος βDocument15 paginiνομισματική θεωρία και πολιτική μέρος βTryphon Tso-hunterÎncă nu există evaluări
- Sample Configuration WLAN - 110x - WLAN - 210x - v1 - 04Document8 paginiSample Configuration WLAN - 110x - WLAN - 210x - v1 - 04Sherry lyneÎncă nu există evaluări
- Introduction to Port Scanning with NmapDocument9 paginiIntroduction to Port Scanning with NmapshahrukhÎncă nu există evaluări
- IMS Design and Log Analysis: Reference ManualDocument179 paginiIMS Design and Log Analysis: Reference ManualryadavÎncă nu există evaluări
- Make WiFi Vending Machine with Raspberry PiDocument7 paginiMake WiFi Vending Machine with Raspberry PiRonnie dyÎncă nu există evaluări
- Security of BIOS/UEFI System Firmware From Attacker and Defender PerspectivesDocument20 paginiSecurity of BIOS/UEFI System Firmware From Attacker and Defender PerspectivesCuong TranÎncă nu există evaluări
- IIB Admin and Development Useful CommandsDocument7 paginiIIB Admin and Development Useful Commandspradeep bvnÎncă nu există evaluări
- Tera Romm 4Document6 paginiTera Romm 4Temp TÎncă nu există evaluări
- Aberdeen CFTS Case StudyDocument2 paginiAberdeen CFTS Case StudyAndima Jeff HardyÎncă nu există evaluări
- Presentation On Oracle CloudDocument8 paginiPresentation On Oracle CloudKumar rÎncă nu există evaluări
- Research PaperDocument5 paginiResearch PaperMilan PanchalÎncă nu există evaluări
- Pace 921VNX Wireless DSL VoIP GatewayDocument2 paginiPace 921VNX Wireless DSL VoIP GatewayPaul CassellsÎncă nu există evaluări
- CIS Oracle Solaris 11.2 Benchmark v1.1.0Document91 paginiCIS Oracle Solaris 11.2 Benchmark v1.1.0DavidÎncă nu există evaluări
- GlobalProtect Admin Guide PANOS 8.0Document254 paginiGlobalProtect Admin Guide PANOS 8.0Khánh NguyễnÎncă nu există evaluări
- DNS Server Global Query Block ListDocument10 paginiDNS Server Global Query Block ListSławek TurekÎncă nu există evaluări
- IDOC To File Scenario Using XML HTTP Port and IDOC Bundling ConceptsDocument7 paginiIDOC To File Scenario Using XML HTTP Port and IDOC Bundling ConceptsUmesh NanjaiahÎncă nu există evaluări
- CWLan GuideDocument406 paginiCWLan GuideDonald HermanÎncă nu există evaluări
- Maxwell Software Installation Guide 2018Document53 paginiMaxwell Software Installation Guide 2018jpmsxploitÎncă nu există evaluări
- 1 Introduction of Data Communication and Computer Networks Goals Applications of NetworksDocument15 pagini1 Introduction of Data Communication and Computer Networks Goals Applications of NetworksSuyasha JainÎncă nu există evaluări
- Nevion Cp560 Data Sheet r1513Document4 paginiNevion Cp560 Data Sheet r1513dominhsonÎncă nu există evaluări
- 01 50003 0201 20131018 D - FINAL - Student - Book (WaterMarked)Document224 pagini01 50003 0201 20131018 D - FINAL - Student - Book (WaterMarked)Jack Suarez ZamudioÎncă nu există evaluări
- 05 Power ControlDocument57 pagini05 Power ControlTHENRAL SARATHÎncă nu există evaluări
- Micro Focus Container Deployment Foundation: Planning GuideDocument45 paginiMicro Focus Container Deployment Foundation: Planning GuideJason GomezÎncă nu există evaluări
- Cisco MerakiDocument4 paginiCisco MerakiMinh Hoàng100% (1)
- 26 Engines Detected This File: DetectionDocument2 pagini26 Engines Detected This File: DetectionСтив ИгалÎncă nu există evaluări
- Network Functions Virtualization NFV (PDFDrive)Document184 paginiNetwork Functions Virtualization NFV (PDFDrive)sultan alahmariÎncă nu există evaluări
- Tadiran Coral IPX NewDocument48 paginiTadiran Coral IPX NewYuvrajsinh ChauhanÎncă nu există evaluări
- Faststart-Guide-3 4 2Document11 paginiFaststart-Guide-3 4 2SabÎncă nu există evaluări
- Unit Plan - Data Communications and NetworksDocument6 paginiUnit Plan - Data Communications and Networksapi-29749719350% (2)
- Domain Name (IT Act) - 1Document9 paginiDomain Name (IT Act) - 1Afsana AliÎncă nu există evaluări
- Cisco Live - Examining Cisco TrustSecDocument61 paginiCisco Live - Examining Cisco TrustSecsomeonenice100% (1)