Documente Academic
Documente Profesional
Documente Cultură
Cybersecurity References
Încărcat de
PritamDrepturi de autor
Formate disponibile
Partajați acest document
Partajați sau inserați document
Vi se pare util acest document?
Este necorespunzător acest conținut?
Raportați acest documentDrepturi de autor:
Formate disponibile
Cybersecurity References
Încărcat de
PritamDrepturi de autor:
Formate disponibile
Kent, A.D., 2016. Cyber security data sources for dynamic network research.
In Dynamic
Networks and Cyber-Security (pp. 37-65).
Finnemore, M. and Hollis, D.B., 2016. Constructing norms for global cybersecurity. American
Journal of International Law, 110(3), pp.425-479.
Nazir, S., Patel, S. and Patel, D., 2017. Assessing and augmenting SCADA cyber security: A
survey of techniques. Computers & Security, 70, pp.436-454.
Almeshekah, M.H. and Spafford, E.H., 2016. Cyber security deception. In Cyber deception (pp.
23-50). Springer, Cham.
Khatoun, R. and Zeadally, S., 2017. Cybersecurity and privacy solutions in smart cities. IEEE
Communications Magazine, 55(3), pp.51-59.
Yousefi-Azar, M., Varadharajan, V., Hamey, L. and Tupakula, U., 2017, May. Autoencoder-based
feature learning for cyber security applications. In 2017 International joint conference on neural
networks (IJCNN) (pp. 3854-3861). IEEE.
Taylor, P.J., Dargahi, T., Dehghantanha, A., Parizi, R.M. and Choo, K.K.R., 2019. A systematic
literature review of blockchain cyber security. Digital Communications and Networks.
Li, Z., Shahidehpour, M. and Aminifar, F., 2017. Cybersecurity in distributed power
systems. Proceedings of the IEEE, 105(7), pp.1367-1388.
de Bruijn, H. and Janssen, M., 2017. Building cybersecurity awareness: The need for evidence-
based framing strategies. Government Information Quarterly, 34(1), pp.1-7.
Lamba, A., Singh, S., Balvinder, S., Dutta, N. and Rela, S., 2017. Mitigating Cyber Security
Threats of Industrial Control Systems (Scada & Dcs). In 3rd International Conference on
Emerging Technologies in Engineering, Biomedical, Medical and Science (ETEBMS–July 2017).
Schatz, D., Bashroush, R. and Wall, J., 2017. Towards a more representative definition of cyber
security. Journal of Digital Forensics, Security and Law, 12(2), pp.53-74.
Sun, N., Zhang, J., Rimba, P., Gao, S., Zhang, L.Y. and Xiang, Y., 2018. Data-driven cybersecurity
incident prediction: A survey. IEEE Communications Surveys & Tutorials, 21(2), pp.1744-1772.
Hemilä, J., Mikkola, M. and Salonen, J., 2019, December. Management of Cyber Security Threats
in the Factories of the Future Supply Chains. In 9th International Conference on Operations and
Supply Chain Management, OSCM 2019.
Van Schaik, P., Jeske, D., Onibokun, J., Coventry, L., Jansen, J. and Kusev, P., 2017. Risk
perceptions of cyber-security and precautionary behaviour. Computers in Human Behavior, 75,
pp.547-559.
Edgar, T.W. and Manz, D.O., 2017. Research methods for cyber security. Syngress.
Kostopoulos, G., 2017. Cyberspace and cybersecurity. Auerbach Publications.
S-ar putea să vă placă și
- 3.B Poverty Reduction Through Slum Program Collaboration in Kendari City PDFDocument11 pagini3.B Poverty Reduction Through Slum Program Collaboration in Kendari City PDFzen dartÎncă nu există evaluări
- Flood Detector System Using Arduino: Edwin de Guzman, Valerie Shane Cuadra, Aileen Grace de Luna, Christian VillanuevaDocument5 paginiFlood Detector System Using Arduino: Edwin de Guzman, Valerie Shane Cuadra, Aileen Grace de Luna, Christian Villanuevaredmi note3Încă nu există evaluări
- Chapter 9 - Study GuideDocument27 paginiChapter 9 - Study GuideLoretta Lynn AltmayerÎncă nu există evaluări
- Cybersecurity Essentials Chapter 4 Quiz Questions AnswersDocument5 paginiCybersecurity Essentials Chapter 4 Quiz Questions Answersheno ahÎncă nu există evaluări
- Coin Based Mobile ChargerDocument13 paginiCoin Based Mobile ChargerIJRASETPublicationsÎncă nu există evaluări
- 9.poultry Farm Monitoring and Controlling System Using IoTDocument3 pagini9.poultry Farm Monitoring and Controlling System Using IoTTECHer YTÎncă nu există evaluări
- Internship Report Converter VIIDocument30 paginiInternship Report Converter VIIShubham Lathi100% (1)
- Newton's Second Law of Motion: The Atwood MachineDocument4 paginiNewton's Second Law of Motion: The Atwood MachineEarl Mathew DangcalanÎncă nu există evaluări
- Project Proposal TemplateDocument9 paginiProject Proposal TemplateMwotil AlexÎncă nu există evaluări
- Question and Answer, Quiz On Information TechnologyDocument7 paginiQuestion and Answer, Quiz On Information TechnologySandeepÎncă nu există evaluări
- Fundamentals of OutsourcingDocument34 paginiFundamentals of OutsourcingpiÎncă nu există evaluări
- Loans and Savings Management System For Bentuco National High School Faculty CooperativeDocument7 paginiLoans and Savings Management System For Bentuco National High School Faculty CooperativeInternational Journal of Innovative Science and Research TechnologyÎncă nu există evaluări
- Research Paper On QR BasedDocument5 paginiResearch Paper On QR BasedDarshani ShetkarÎncă nu există evaluări
- Capstone ProjectDocument11 paginiCapstone ProjectDave Matthew LibiranÎncă nu există evaluări
- Benthic - Molluscs - Thesis - Proposal SoftboundDocument62 paginiBenthic - Molluscs - Thesis - Proposal SoftboundLonica Shane Buat CamilloÎncă nu există evaluări
- Cyber SecurityDocument6 paginiCyber SecurityDipen TamangÎncă nu există evaluări
- Abey AssefaDocument66 paginiAbey AssefaNaty wayÎncă nu există evaluări
- WSN 3Document79 paginiWSN 3Loya SrijaÎncă nu există evaluări
- An Experimental Evaluation of Similarity-Based and Embedding-Based Link Prediction Methods On GraphsDocument18 paginiAn Experimental Evaluation of Similarity-Based and Embedding-Based Link Prediction Methods On GraphsLewis TorresÎncă nu există evaluări
- Module 1Document21 paginiModule 1MCarl F. ClycyÎncă nu există evaluări
- Instructor Materials Chapter 3: Cybersecurity Threats, Vulnerabilities, and AttacksDocument28 paginiInstructor Materials Chapter 3: Cybersecurity Threats, Vulnerabilities, and AttacksOussama HlaliÎncă nu există evaluări
- Financial Management and Decision Making Enhancement Through Integration of Accounting Information System Among Multi Purpose Cooperatives in General Santos City Chapters 1 and 2 EditedDocument15 paginiFinancial Management and Decision Making Enhancement Through Integration of Accounting Information System Among Multi Purpose Cooperatives in General Santos City Chapters 1 and 2 EditedDenise Jane RoqueÎncă nu există evaluări
- IMRADDocument10 paginiIMRADArnel BandojaÎncă nu există evaluări
- Review of Related Literature and SystemsDocument8 paginiReview of Related Literature and Systemsfrancis albert turalbaÎncă nu există evaluări
- Solar Powered Smart Ultrasonic Insect Repellent With DTMF and Manual Control For AgricultureDocument4 paginiSolar Powered Smart Ultrasonic Insect Repellent With DTMF and Manual Control For AgricultureIJRASETPublicationsÎncă nu există evaluări
- Smart Water Level Monitoring System by Using IOT And: Arduino UNO and GSM ModuleDocument8 paginiSmart Water Level Monitoring System by Using IOT And: Arduino UNO and GSM ModuleEighthSenseGroupÎncă nu există evaluări
- Final DOXupdatedfeb20Document186 paginiFinal DOXupdatedfeb20Neil JohnÎncă nu există evaluări
- Vikas Android (Kotlin) Resume PDFDocument3 paginiVikas Android (Kotlin) Resume PDFSaurav KumarÎncă nu există evaluări
- Chapter 2 Related Literature and StudiesDocument27 paginiChapter 2 Related Literature and StudiesJohn Bryll Puebla AgbayÎncă nu există evaluări
- 14 Cyber Security Awareness 1Document9 pagini14 Cyber Security Awareness 1Michelle EsternonÎncă nu există evaluări
- CH 07Document44 paginiCH 07Varun SrinivasÎncă nu există evaluări
- Alternate Protocol Suites 1Document7 paginiAlternate Protocol Suites 1ultra dubsÎncă nu există evaluări
- General Biology 1 Module 3Document18 paginiGeneral Biology 1 Module 3BarachielÎncă nu există evaluări
- Smart Door Lock SystemDocument8 paginiSmart Door Lock SystemRahul RajendrakumarÎncă nu există evaluări
- Types of Active AttacksDocument5 paginiTypes of Active AttacksRashmi SamarasinghaÎncă nu există evaluări
- Internet Security Chapter SixDocument6 paginiInternet Security Chapter SixTony AprekuÎncă nu există evaluări
- Advantage of Database ApproachDocument2 paginiAdvantage of Database ApproachArup Kumar BoroÎncă nu există evaluări
- UPDATED05!15!22 SmartTrashbin DocuDocument64 paginiUPDATED05!15!22 SmartTrashbin DocuJonathan MartinezÎncă nu există evaluări
- Transformation of Slum and Squatter Settlements ADocument8 paginiTransformation of Slum and Squatter Settlements ANurul Aini100% (1)
- PDF Tagalog - Filipino OrthographyDocument4 paginiPDF Tagalog - Filipino Orthographymelvin ynionÎncă nu există evaluări
- 3i ManuscriptDocument78 pagini3i ManuscriptEldrin MonteclaroÎncă nu există evaluări
- AIW Lab ReportDocument41 paginiAIW Lab ReportDebendra Wagle0% (1)
- Types of Network Interface CardsDocument2 paginiTypes of Network Interface CardsBanjo De los SantosÎncă nu există evaluări
- DBMS Report PDFDocument15 paginiDBMS Report PDFBeast0% (1)
- TCP Attack LabDocument13 paginiTCP Attack LabD CREATIONÎncă nu există evaluări
- Factors Influencing Career Choice in Technical Education Profession Among Colleges of Education Students in Lagos State2Document11 paginiFactors Influencing Career Choice in Technical Education Profession Among Colleges of Education Students in Lagos State2LYNDEN JADENAÎncă nu există evaluări
- Sustainability Plan OutlineDocument14 paginiSustainability Plan OutlineNatasha RostataÎncă nu există evaluări
- Guided and Unguided MediaDocument7 paginiGuided and Unguided Mediakudikala kalabharathiÎncă nu există evaluări
- Abstract Data TypesDocument19 paginiAbstract Data TypesJohn jairo Ramirez perezÎncă nu există evaluări
- Chapter TwoDocument68 paginiChapter TwoTamiru Dereje100% (1)
- VLSI Signal Processing (Major Elective-II)Document2 paginiVLSI Signal Processing (Major Elective-II)Kapil JoshiÎncă nu există evaluări
- Chapter2 SystemsIntegrationApproachesDocument15 paginiChapter2 SystemsIntegrationApproachesKyla PinedaÎncă nu există evaluări
- Child Safety System by Using RF TechnologyDocument25 paginiChild Safety System by Using RF Technologyaravishankar23Încă nu există evaluări
- Research PaperDocument18 paginiResearch PaperEinsbern TVÎncă nu există evaluări
- Web-Based Requisition and Bidding SystemDocument45 paginiWeb-Based Requisition and Bidding SystemTeremaeÎncă nu există evaluări
- Capstone ScriptDocument2 paginiCapstone ScriptNicole Dela TorreÎncă nu există evaluări
- 14 ReferenceDocument10 pagini14 ReferenceHelal Ahmed AponÎncă nu există evaluări
- Embracing The Enigma - Navigating AI's Impact On Global SecurityDocument7 paginiEmbracing The Enigma - Navigating AI's Impact On Global SecurityAbu RayhanÎncă nu există evaluări
- Forensic Computing ReferencesDocument4 paginiForensic Computing ReferencesOnwuegbuzie Innocent U.Încă nu există evaluări
- Cloud RefsDocument23 paginiCloud RefsAtiq jan yousafzaiÎncă nu există evaluări
- IOTTDocument1 paginăIOTTPritamÎncă nu există evaluări
- My ExplanationDocument2 paginiMy ExplanationPritamÎncă nu există evaluări
- XMLSCDocument1 paginăXMLSCPritamÎncă nu există evaluări
- Microcontroller Smoke DetectorDocument41 paginiMicrocontroller Smoke DetectorPritamÎncă nu există evaluări
- Middle Grades ReportDocument138 paginiMiddle Grades ReportcraignewmanÎncă nu există evaluări
- Full Moon RitualsDocument22 paginiFull Moon RitualsJP83% (6)
- Implementation of 7s Framenwork On RestuDocument36 paginiImplementation of 7s Framenwork On RestuMuhammad AtaÎncă nu există evaluări
- Elementary SurveyingDocument19 paginiElementary SurveyingJefferson EscobidoÎncă nu există evaluări
- Articles 62 & 63: Presented By: Muhammad Saad Umar FROM: BS (ACF) - B 2K20Document10 paginiArticles 62 & 63: Presented By: Muhammad Saad Umar FROM: BS (ACF) - B 2K20Muhammad Saad UmarÎncă nu există evaluări
- Radiopharmaceutical Production: History of Cyclotrons The Early Years at BerkeleyDocument31 paginiRadiopharmaceutical Production: History of Cyclotrons The Early Years at BerkeleyNguyễnKhươngDuyÎncă nu există evaluări
- Sale Deed Document Rajyalakshmi, 2222222Document3 paginiSale Deed Document Rajyalakshmi, 2222222Madhav Reddy100% (2)
- RFP On Internal AuditDocument33 paginiRFP On Internal AuditCan dien tu Thai Binh DuongÎncă nu există evaluări
- New Document (116) New Document (115) New Document (1Document9 paginiNew Document (116) New Document (115) New Document (1Manav PARMARÎncă nu există evaluări
- Quarter 2-Module 7 Social and Political Stratification: Department of Education Republic of The PhilippinesDocument21 paginiQuarter 2-Module 7 Social and Political Stratification: Department of Education Republic of The Philippinestricia100% (5)
- Spouses Aggabao V. Parulan, Jr. and Parulan G.R. No. 165803, (September 1, 2010) Doctrine (S)Document9 paginiSpouses Aggabao V. Parulan, Jr. and Parulan G.R. No. 165803, (September 1, 2010) Doctrine (S)RJÎncă nu există evaluări
- Ubi Jus Ibi RemediumDocument9 paginiUbi Jus Ibi RemediumUtkarsh JaniÎncă nu există evaluări
- PED100 Mod2Document3 paginiPED100 Mod2Risa BarritaÎncă nu există evaluări
- Storey Publishing Fall 2017 CatalogDocument108 paginiStorey Publishing Fall 2017 CatalogStorey PublishingÎncă nu există evaluări
- ThesisDocument58 paginiThesisTirtha Roy BiswasÎncă nu există evaluări
- Resume Testing6+ SaptagireswarDocument5 paginiResume Testing6+ SaptagireswarSuresh RamasamyÎncă nu există evaluări
- In Partial Fulfillment of The Requirements in Care of Older Adult (NCM 114)Document2 paginiIn Partial Fulfillment of The Requirements in Care of Older Adult (NCM 114)Karen TangÎncă nu există evaluări
- Arsu and AzizoDocument123 paginiArsu and AzizoZebu BlackÎncă nu există evaluări
- Rizal ExaminationDocument3 paginiRizal ExaminationBea ChristineÎncă nu există evaluări
- Inside Out or Outside inDocument6 paginiInside Out or Outside inΧΡΗΣΤΟΣ ΠΑΠΑΔΟΠΟΥΛΟΣÎncă nu există evaluări
- Scribe FormDocument2 paginiScribe FormsiddharthgamreÎncă nu există evaluări
- Nin/Pmjay Id Name of The Vaccination Site Category Type District BlockDocument2 paginiNin/Pmjay Id Name of The Vaccination Site Category Type District BlockNikunja PadhanÎncă nu există evaluări
- Forecast Error (Control Chart)Document2 paginiForecast Error (Control Chart)Jane OngÎncă nu există evaluări
- Biblehub Com Commentaries Matthew 3 17 HTMDocument21 paginiBiblehub Com Commentaries Matthew 3 17 HTMSorin TrimbitasÎncă nu există evaluări
- Introduction To Sociology ProjectDocument2 paginiIntroduction To Sociology Projectapi-590915498Încă nu există evaluări
- Soal Midtest + Kunci JawabanDocument28 paginiSoal Midtest + Kunci JawabanYuyun RasulongÎncă nu există evaluări
- Names of AllahDocument8 paginiNames of AllahAfshaan BanuÎncă nu există evaluări
- Man Is Made by His BeliefDocument2 paginiMan Is Made by His BeliefLisa KireechevaÎncă nu există evaluări
- Week 6 Starbucks Leading Change 2023Document10 paginiWeek 6 Starbucks Leading Change 2023Prunella YapÎncă nu există evaluări
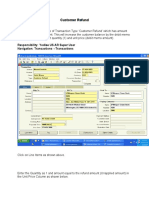
- Customer Refund: Responsibility: Yodlee US AR Super User Navigation: Transactions TransactionsDocument12 paginiCustomer Refund: Responsibility: Yodlee US AR Super User Navigation: Transactions TransactionsAziz KhanÎncă nu există evaluări
- Defensive Cyber Mastery: Expert Strategies for Unbeatable Personal and Business SecurityDe la EverandDefensive Cyber Mastery: Expert Strategies for Unbeatable Personal and Business SecurityEvaluare: 5 din 5 stele5/5 (1)
- The Dark Net: Inside the Digital UnderworldDe la EverandThe Dark Net: Inside the Digital UnderworldEvaluare: 3.5 din 5 stele3.5/5 (104)
- The Internet Con: How to Seize the Means of ComputationDe la EverandThe Internet Con: How to Seize the Means of ComputationEvaluare: 5 din 5 stele5/5 (6)
- Grokking Algorithms: An illustrated guide for programmers and other curious peopleDe la EverandGrokking Algorithms: An illustrated guide for programmers and other curious peopleEvaluare: 4 din 5 stele4/5 (16)
- How to Do Nothing: Resisting the Attention EconomyDe la EverandHow to Do Nothing: Resisting the Attention EconomyEvaluare: 4 din 5 stele4/5 (421)
- Practical Industrial Cybersecurity: ICS, Industry 4.0, and IIoTDe la EverandPractical Industrial Cybersecurity: ICS, Industry 4.0, and IIoTÎncă nu există evaluări
- More Porn - Faster!: 50 Tips & Tools for Faster and More Efficient Porn BrowsingDe la EverandMore Porn - Faster!: 50 Tips & Tools for Faster and More Efficient Porn BrowsingEvaluare: 3.5 din 5 stele3.5/5 (24)
- The Digital Marketing Handbook: A Step-By-Step Guide to Creating Websites That SellDe la EverandThe Digital Marketing Handbook: A Step-By-Step Guide to Creating Websites That SellEvaluare: 5 din 5 stele5/5 (6)
- Nine Algorithms That Changed the Future: The Ingenious Ideas That Drive Today's ComputersDe la EverandNine Algorithms That Changed the Future: The Ingenious Ideas That Drive Today's ComputersEvaluare: 5 din 5 stele5/5 (7)
- Ten Arguments for Deleting Your Social Media Accounts Right NowDe la EverandTen Arguments for Deleting Your Social Media Accounts Right NowEvaluare: 4 din 5 stele4/5 (388)
- The Wires of War: Technology and the Global Struggle for PowerDe la EverandThe Wires of War: Technology and the Global Struggle for PowerEvaluare: 4 din 5 stele4/5 (34)
- CISM Certified Information Security Manager Study GuideDe la EverandCISM Certified Information Security Manager Study GuideÎncă nu există evaluări
- HTML5 and CSS3 Masterclass: In-depth Web Design Training with Geolocation, the HTML5 Canvas, 2D and 3D CSS Transformations, Flexbox, CSS Grid, and More (English Edition)De la EverandHTML5 and CSS3 Masterclass: In-depth Web Design Training with Geolocation, the HTML5 Canvas, 2D and 3D CSS Transformations, Flexbox, CSS Grid, and More (English Edition)Încă nu există evaluări
- Python for Beginners: The 1 Day Crash Course For Python Programming In The Real WorldDe la EverandPython for Beginners: The 1 Day Crash Course For Python Programming In The Real WorldÎncă nu există evaluări
- The Ultimate LinkedIn Sales Guide: How to Use Digital and Social Selling to Turn LinkedIn into a Lead, Sales and Revenue Generating MachineDe la EverandThe Ultimate LinkedIn Sales Guide: How to Use Digital and Social Selling to Turn LinkedIn into a Lead, Sales and Revenue Generating MachineÎncă nu există evaluări
- React.js Design Patterns: Learn how to build scalable React apps with ease (English Edition)De la EverandReact.js Design Patterns: Learn how to build scalable React apps with ease (English Edition)Încă nu există evaluări
- Design That Scales: Creating a Sustainable Design System PracticeDe la EverandDesign That Scales: Creating a Sustainable Design System PracticeÎncă nu există evaluări
- How to Start a Blog with WordPress: Beginner's Guide to Make Money by Writing OnlineDe la EverandHow to Start a Blog with WordPress: Beginner's Guide to Make Money by Writing OnlineEvaluare: 3.5 din 5 stele3.5/5 (2)