Documente Academic
Documente Profesional
Documente Cultură
A Robust Image Watermarking Using Two Level DCT and Wavelet Packet Denoising
Încărcat de
Bodhankar Santosh KumarTitlu original
Drepturi de autor
Formate disponibile
Partajați acest document
Partajați sau inserați document
Vi se pare util acest document?
Este necorespunzător acest conținut?
Raportați acest documentDrepturi de autor:
Formate disponibile
A Robust Image Watermarking Using Two Level DCT and Wavelet Packet Denoising
Încărcat de
Bodhankar Santosh KumarDrepturi de autor:
Formate disponibile
A Robust Image Watermarking using Two Level DCT and Wavelet
Packets De-noising
Introduction
In this paper we present a blind low frequency watermarking scheme on
gray level images, which is based on DCT transform and spread spectrum
communications technique. We compute the DCT of non overlapping 8x8 blocks of the
host image, and then using the DC coefficients of each block we construct a low-
resolution approximation image. We apply block based DCT on this approximation
image, then a pseudo random noise sequence is added into its high frequencies.
For detection, we extract the approximation image from the watermarked
image, then the same pseudo random noise sequence is generated, and its correlation is
computed with high frequencies of the watermarked approximation image. In our
method, higher robustness is obtained because of embedding the watermark in low
frequency. In addition, higher imperceptibility is gained by scattering the watermark's bit
in different blocks.
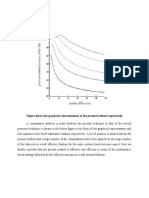
We evaluated the robustness of the proposed technique against many
common attacks such as JPEG compression, additive Gaussian noise and median filter.
Compared with related works, our method proved to be highly resistant in cases of
compression and additive noise, while preserving high PSNR for the watermarked
images.
In recent years, many digital watermarking techniques have been
proposed to protect the copyright of digital multimedia data. Watermark embedding is
performed in many domains such as spatial, Fourier transform, DCT and DWT. One of
the commonly used domains for embedding a watermark in an image is the DCT. DCT
splits up the image into the frequency bands, so upon the application, the watermark can
be embedded in different frequencies. Furthermore, the sensitivity of human visual
system to DCT frequencies has been extensively studied; which resulted in the
recommended JPEG quantization table. These results can be used for predicting and
minimizing the visual impact of distortion caused by embedding the watermark.
If we know the image compression domain, for example DCT, then it
is better to embed watermark in those DCT compression process. Since we are able to
anticipate which DCT coefficients will be quantized by the compression scheme, we can
choose not to embed the watermark in those coefficients. This approach can be extended
to compression methods in other domains, as well. Furthermore, it is a common practice
to apply additive noise for watermark embedding and use the correlation techniques for
detection. In watermarking technique is provided in which a watermark is embedded as
pseudo-random noise sequences into middle-frequency range of the image.
The major objective of this paper is to develop a watermarking
algorithm based on DCT and spread spectrum communications in such a way that it is
highly robust with respect to JPEG compression and also other common attacks.
Compared with similar works, our method provided the highest robustness for extracted
watermark especially when JPEG compression was applied to the watermarked image. In
addition, this high level of robustness did not decrease its PSNR.
Methodology
In this paper, we propose a novel watermarking scheme which is based on
low frequencies of DCT transform and spread spectrum watermarking. In this method all
the DC components of the block DCT transform of the original image are grouped
together to form a pseudo image called DC image. Then each bit of the watermark is
scattered through the high frequencies of DCT transform of this DC image. In other
word, each bit is scattered in 64 blocks of the original image. Therefore, we obtain the
robustness because of embedding the watermark in low frequency and gain the
imperceptibility by scattering the watermark's bit in different block. We then compute the
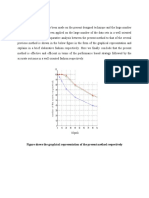
NC4 and PSNR to judge the robustness and the invisibility of the watermarking
algorithm. The PSNR values for watermarked images are all greater than 38 dB, which is
the empirical value for the image without any perceivable degradation.
We assume that the host image is of size 5128512. BDCT is applied
on 8*8 non overlapping blocs. Then to embed the watermark only the dc coefficient is
selected out of the 64 dc coefficients. In each bloc DC coefficient is the most important
coefficient which has the largest value. Embedding watermark in DC coefficient makes
the watermark robust against many attacks. Those selected coefficients are then mapped
into a reduced image which is called low-resolution approximation image (LRAI).
Therefore, the size of extracted LRAI is always 1/ 64 of the host image. For example for
512x512 host images, the size of extracted LRAI is always 64x64 pixels. After extracting
LRAI from host image, the extracted LRAI is divided into 8x8 non-overlapping blocks
and BDCT of each block is calculated. Then according to the value of watermark bit
which is going to be embedded in each block, a pseudo random noise sequence is added
to the high frequencies of DCT transform of each 8x8 block of LRAI. Coefficients in the
low and middle frequencies that are copied over to the watermarked LRAI remain
unaffected.
We should note here that two separate pseudo random noise
sequences are used to represent the bit values of 0 and 1. Furthermore, by choosing these
two pseudo random noise sequences to be as un-correlated as possible, we can
significantly reduce the rate of false detection. Then each block is inverse-transformed to
give us watermarked LRAI. The final step to construct the watermarked image is to
replace the DC coefficients of LRAI with their corresponding watermarked ones, and
then compute the IDCT transform of each 8x8 block of watermarked LRAI.
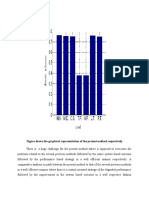
Figure shows the watermark embedded procedure
Applications
Copyright watermarking
Fingerprint watermarking
Broadcast watermarking
Annotation watermarking
Integrity watermarking
Data hiding watermarking
References
1. Lu C.-S., "Multimedia Security: Steganography and Digital Watermarking Techniques
for Protection of Intellectual Property", Idea Group Publishing, 2005, ISBN: 1-59140-
192-5
2. Katzenbeisser S. and Petitcolas A.-P., "Information Hiding Techniques for
Steganography and Digital Watermarking," Artech House, January 2000, ISBN:
1580530354.
3. Voloshynovskiy S. and Deguillaume F., "Information-Theoretic Data-Hiding: Recent
Achievements And Open Problems", International Journal of Image and Graphics, Vol. 5,
No. 1, p. 5–36, 2005
S-ar putea să vă placă și
- An Effective Strategy of The Transporation System Oriented Agent StrategyDocument4 paginiAn Effective Strategy of The Transporation System Oriented Agent StrategyBodhankar Santosh KumarÎncă nu există evaluări
- Routing Topolgy Based Ample SystemDocument4 paginiRouting Topolgy Based Ample SystemBodhankar Santosh KumarÎncă nu există evaluări
- ConclusionDocument1 paginăConclusionBodhankar Santosh KumarÎncă nu există evaluări
- MethodologyDocument1 paginăMethodologyBodhankar Santosh KumarÎncă nu există evaluări
- Key WordsDocument1 paginăKey WordsBodhankar Santosh KumarÎncă nu există evaluări
- Design of Malware Spread Oriented Decentralisation Based P2P Dynamic NetworksDocument4 paginiDesign of Malware Spread Oriented Decentralisation Based P2P Dynamic NetworksBodhankar Santosh KumarÎncă nu există evaluări
- Efficient Framework Oriented Caching StrategyDocument4 paginiEfficient Framework Oriented Caching StrategyBodhankar Santosh KumarÎncă nu există evaluări
- Design of The Mobile Commerce in The Pattern of Prediction and MiningDocument1 paginăDesign of The Mobile Commerce in The Pattern of Prediction and MiningBodhankar Santosh KumarÎncă nu există evaluări
- Block DiagramDocument1 paginăBlock DiagramBodhankar Santosh KumarÎncă nu există evaluări
- Key WordsDocument1 paginăKey WordsBodhankar Santosh KumarÎncă nu există evaluări
- Design of The Attribute Oriented Key Policy For The Decentralization Based Preserving PrivacyDocument1 paginăDesign of The Attribute Oriented Key Policy For The Decentralization Based Preserving PrivacyBodhankar Santosh KumarÎncă nu există evaluări
- Block DiagramDocument1 paginăBlock DiagramBodhankar Santosh KumarÎncă nu există evaluări
- Expected ResultsDocument2 paginiExpected ResultsBodhankar Santosh KumarÎncă nu există evaluări
- ConclusionDocument1 paginăConclusionBodhankar Santosh KumarÎncă nu există evaluări
- Design of Theft Electricity Control Using System of Prepaid Energy MeterDocument4 paginiDesign of Theft Electricity Control Using System of Prepaid Energy MeterBodhankar Santosh KumarÎncă nu există evaluări
- Key WordsDocument1 paginăKey WordsBodhankar Santosh KumarÎncă nu există evaluări
- Block DiagramDocument1 paginăBlock DiagramBodhankar Santosh KumarÎncă nu există evaluări
- Design of The Method Related To Hiding Packets Against Jamming Oriented AttacksDocument1 paginăDesign of The Method Related To Hiding Packets Against Jamming Oriented AttacksBodhankar Santosh KumarÎncă nu există evaluări
- Expected ResultsDocument1 paginăExpected ResultsBodhankar Santosh KumarÎncă nu există evaluări
- ConclusionDocument1 paginăConclusionBodhankar Santosh KumarÎncă nu există evaluări
- MethodologyDocument1 paginăMethodologyBodhankar Santosh KumarÎncă nu există evaluări
- Design of Theft Electricity Control Using System of Prepaid Energy MeterDocument4 paginiDesign of Theft Electricity Control Using System of Prepaid Energy MeterBodhankar Santosh KumarÎncă nu există evaluări
- Expected ResultsDocument1 paginăExpected ResultsBodhankar Santosh KumarÎncă nu există evaluări
- Block DiagramDocument1 paginăBlock DiagramBodhankar Santosh KumarÎncă nu există evaluări
- New Microsoft Office Word DocumentDocument1 paginăNew Microsoft Office Word DocumentBodhankar Santosh KumarÎncă nu există evaluări
- Data Integrity Based Co Operative PossessionDocument1 paginăData Integrity Based Co Operative PossessionBodhankar Santosh KumarÎncă nu există evaluări
- ConclusionDocument1 paginăConclusionBodhankar Santosh KumarÎncă nu există evaluări
- New Microsoft Office Word DocumentDocument1 paginăNew Microsoft Office Word DocumentBodhankar Santosh KumarÎncă nu există evaluări
- Key WordsDocument1 paginăKey WordsBodhankar Santosh KumarÎncă nu există evaluări
- ConclusionDocument1 paginăConclusionBodhankar Santosh KumarÎncă nu există evaluări
- The Yellow House: A Memoir (2019 National Book Award Winner)De la EverandThe Yellow House: A Memoir (2019 National Book Award Winner)Evaluare: 4 din 5 stele4/5 (98)
- Hidden Figures: The American Dream and the Untold Story of the Black Women Mathematicians Who Helped Win the Space RaceDe la EverandHidden Figures: The American Dream and the Untold Story of the Black Women Mathematicians Who Helped Win the Space RaceEvaluare: 4 din 5 stele4/5 (895)
- The Subtle Art of Not Giving a F*ck: A Counterintuitive Approach to Living a Good LifeDe la EverandThe Subtle Art of Not Giving a F*ck: A Counterintuitive Approach to Living a Good LifeEvaluare: 4 din 5 stele4/5 (5794)
- The Little Book of Hygge: Danish Secrets to Happy LivingDe la EverandThe Little Book of Hygge: Danish Secrets to Happy LivingEvaluare: 3.5 din 5 stele3.5/5 (400)
- Devil in the Grove: Thurgood Marshall, the Groveland Boys, and the Dawn of a New AmericaDe la EverandDevil in the Grove: Thurgood Marshall, the Groveland Boys, and the Dawn of a New AmericaEvaluare: 4.5 din 5 stele4.5/5 (266)
- Shoe Dog: A Memoir by the Creator of NikeDe la EverandShoe Dog: A Memoir by the Creator of NikeEvaluare: 4.5 din 5 stele4.5/5 (537)
- Elon Musk: Tesla, SpaceX, and the Quest for a Fantastic FutureDe la EverandElon Musk: Tesla, SpaceX, and the Quest for a Fantastic FutureEvaluare: 4.5 din 5 stele4.5/5 (474)
- Never Split the Difference: Negotiating As If Your Life Depended On ItDe la EverandNever Split the Difference: Negotiating As If Your Life Depended On ItEvaluare: 4.5 din 5 stele4.5/5 (838)
- Grit: The Power of Passion and PerseveranceDe la EverandGrit: The Power of Passion and PerseveranceEvaluare: 4 din 5 stele4/5 (588)
- A Heartbreaking Work Of Staggering Genius: A Memoir Based on a True StoryDe la EverandA Heartbreaking Work Of Staggering Genius: A Memoir Based on a True StoryEvaluare: 3.5 din 5 stele3.5/5 (231)
- The Emperor of All Maladies: A Biography of CancerDe la EverandThe Emperor of All Maladies: A Biography of CancerEvaluare: 4.5 din 5 stele4.5/5 (271)
- The World Is Flat 3.0: A Brief History of the Twenty-first CenturyDe la EverandThe World Is Flat 3.0: A Brief History of the Twenty-first CenturyEvaluare: 3.5 din 5 stele3.5/5 (2259)
- On Fire: The (Burning) Case for a Green New DealDe la EverandOn Fire: The (Burning) Case for a Green New DealEvaluare: 4 din 5 stele4/5 (73)
- The Hard Thing About Hard Things: Building a Business When There Are No Easy AnswersDe la EverandThe Hard Thing About Hard Things: Building a Business When There Are No Easy AnswersEvaluare: 4.5 din 5 stele4.5/5 (344)
- Team of Rivals: The Political Genius of Abraham LincolnDe la EverandTeam of Rivals: The Political Genius of Abraham LincolnEvaluare: 4.5 din 5 stele4.5/5 (234)
- The Unwinding: An Inner History of the New AmericaDe la EverandThe Unwinding: An Inner History of the New AmericaEvaluare: 4 din 5 stele4/5 (45)
- The Gifts of Imperfection: Let Go of Who You Think You're Supposed to Be and Embrace Who You AreDe la EverandThe Gifts of Imperfection: Let Go of Who You Think You're Supposed to Be and Embrace Who You AreEvaluare: 4 din 5 stele4/5 (1090)
- The Sympathizer: A Novel (Pulitzer Prize for Fiction)De la EverandThe Sympathizer: A Novel (Pulitzer Prize for Fiction)Evaluare: 4.5 din 5 stele4.5/5 (121)
- Her Body and Other Parties: StoriesDe la EverandHer Body and Other Parties: StoriesEvaluare: 4 din 5 stele4/5 (821)
- Music Genre Classification For Indian MuDocument9 paginiMusic Genre Classification For Indian MuKakasdÎncă nu există evaluări
- Speech Processing For Machine Learning - Filter Banks, Mel-Frequency Cepstral Coefficients (MFCCS) and What's In-Between - Haytham FayekDocument19 paginiSpeech Processing For Machine Learning - Filter Banks, Mel-Frequency Cepstral Coefficients (MFCCS) and What's In-Between - Haytham Fayekbagustris8140Încă nu există evaluări
- Implementation of Cordic Algorithm Using Matlab & VHDL For Wlan ReceiverDocument3 paginiImplementation of Cordic Algorithm Using Matlab & VHDL For Wlan ReceiverHemant SaraswatÎncă nu există evaluări
- Review Article: Fast Transforms in Image Processing: Compression, Restoration, and ResamplingDocument24 paginiReview Article: Fast Transforms in Image Processing: Compression, Restoration, and ResamplingManu ManuÎncă nu există evaluări
- Discrete Cosine TransformDocument12 paginiDiscrete Cosine TransformGeleta AmanÎncă nu există evaluări
- Fast Fourier TransformDocument14 paginiFast Fourier TransformIraj ToloueÎncă nu există evaluări
- JPEG DECODER USING VHDL AND IMPLEMENTING IT ON FPGA SPARTAN 3A KItProject Main Report1Document21 paginiJPEG DECODER USING VHDL AND IMPLEMENTING IT ON FPGA SPARTAN 3A KItProject Main Report1Sachin RathodÎncă nu există evaluări
- DIP Question BankDocument9 paginiDIP Question Bankapi-3772517Încă nu există evaluări
- Exercises From Linear Algebra, Signal Processing, and Wavelets. A Unified Approach. MATLAB VersionDocument71 paginiExercises From Linear Algebra, Signal Processing, and Wavelets. A Unified Approach. MATLAB VersionAfsaneh ShakeriÎncă nu există evaluări
- A Steganography Scheme On JPEG Compressed Cover Image With High Embedding CapacityDocument23 paginiA Steganography Scheme On JPEG Compressed Cover Image With High Embedding Capacitychinnujan24Încă nu există evaluări
- VHDL Implementation of Wavelet Packet Transforms Using SIMULINK ToolsDocument10 paginiVHDL Implementation of Wavelet Packet Transforms Using SIMULINK ToolszhiwaÎncă nu există evaluări
- Assessment of PragmaticsDocument8 paginiAssessment of PragmaticslifeÎncă nu există evaluări
- Speech Emotion Recognition With Deep LearningDocument10 paginiSpeech Emotion Recognition With Deep LearningkarenÎncă nu există evaluări
- R 2008 M.E. Applied Electronics SyllabusDocument31 paginiR 2008 M.E. Applied Electronics SyllabusisasenthilÎncă nu există evaluări
- Digital Image Processing - S. Jayaraman, S. Esakkirajan and T. Veerakumar PDFDocument112 paginiDigital Image Processing - S. Jayaraman, S. Esakkirajan and T. Veerakumar PDFchiragÎncă nu există evaluări
- DIP SyllabusDocument2 paginiDIP SyllabusvenuraoÎncă nu există evaluări
- HH 3Document23 paginiHH 3hmm raniaÎncă nu există evaluări
- Term Paper About Computer ScienceDocument8 paginiTerm Paper About Computer Sciencedelhwlwgf100% (1)
- Digital Image Processing (Image Compression)Document38 paginiDigital Image Processing (Image Compression)MATHANKUMAR.S100% (2)
- Video Coding Format - WikipediaDocument10 paginiVideo Coding Format - WikipediaMr. MeÎncă nu există evaluări
- Brain Tumor MriDocument23 paginiBrain Tumor MrisekharraoÎncă nu există evaluări
- Copy Move Forgery Based On DWT-DCTDocument4 paginiCopy Move Forgery Based On DWT-DCTShiva KeeÎncă nu există evaluări
- Lab Manual of DSIPDocument22 paginiLab Manual of DSIPRohan BorgalliÎncă nu există evaluări
- Convolutional Neural PDFDocument187 paginiConvolutional Neural PDFearthgod2504Încă nu există evaluări
- Thesis Video WatermarkingDocument6 paginiThesis Video WatermarkingPayToWriteAPaperLubbock100% (4)
- Bijupatnaikuniversity of Technology, Odisha: Curriculum and SyllabusDocument23 paginiBijupatnaikuniversity of Technology, Odisha: Curriculum and Syllabusdilliprout.caplet2016Încă nu există evaluări
- Data Hiding Using Video Steganography - A SurveyDocument8 paginiData Hiding Using Video Steganography - A SurveySwetha AmmukuttyÎncă nu există evaluări
- The Naturalized Role-Play: An Innovative Methodology in Cross-Cultural and Interlanguage Pragmatics ResearchDocument24 paginiThe Naturalized Role-Play: An Innovative Methodology in Cross-Cultural and Interlanguage Pragmatics ResearchTuan AnhÎncă nu există evaluări
- Jpeg PPT NotesDocument24 paginiJpeg PPT Notesfmail667Încă nu există evaluări