Documente Academic
Documente Profesional
Documente Cultură
What Is SSL Offloading?: SSL Acceleration SSL Termination
Încărcat de
syed_engrTitlu original
Drepturi de autor
Formate disponibile
Partajați acest document
Partajați sau inserați document
Vi se pare util acest document?
Este necorespunzător acest conținut?
Raportați acest documentDrepturi de autor:
Formate disponibile
What Is SSL Offloading?: SSL Acceleration SSL Termination
Încărcat de
syed_engrDrepturi de autor:
Formate disponibile
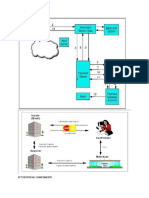
Offload SSL encryption
SSL offloading relieves a Web server of the processing burden of encrypting and/or decrypting
traffic sent via SSL, the security protocol that is implemented in every Web browser. The
processing is offloaded to a separate device designed specifically to perform SSL
acceleration or SSL termination.
What is SSL Offloading?
When traffic is sent via SSL security protocol to web servers, these servers have to
encrypt and/or decrypt all the traffic in order to take appropriate action. This is CPU
intensive and places a heavy strain on the web server, affecting its performance in
application delivery. In SSL Offloading, this burden is “offloaded” or moved from the web
server’s CPU to another device/computer that takes care of all encryption and
decryption, freeing the web server to be utilized for other tasks.
As SSL offloaders can decrypt the data, intrusion detection systems, virus
detection systems and the application layer firewall can analyze the incoming traffic
more effectively and block suspicious data packets.
Types of SSL Offloading
There are two different techniques for SSL offloading - SSL termination and SSL
bridging.
What is SSL Termination?
SSL termination refers to the process that occurs at the server end of an SSL
connection, where the data traffic is decrypted, i.e. where it transitions from encrypted to
unencrypted form.
What is SSL Bridging?
SSL bridging or SSL initiation is performed by a device at the edge of a network. It first
decrypts SSL traffic and then re-encrypts, and then sends it to the Web server. This
process also happens vice-versa - It also decrypts the encrypted response it receives
from the Web server re-encrypts it and then sends it to the client (browser). SSL
bridging is useful for performing deep-packet inspection of the data to verify if the SSL-
encrypted data is safe and does not contain any malicious content. There are three
types of SSL bridging possibilities - HTTPS-to-HTTPS bridging, HTTPS-to-HTTP
bridging and HTTP-to-HTTPS bridging.
Security Implications of SSL Offloading
SSL offloading has significant advantages as it boosts the performance of Web servers,
ensuring faster traffic between the client (customer) and the Web server.
However, the risk with typical SSL offloading is that the data traffic passes in
unencrypted form when moving from off-loader to the Web server. This can be
considered to be secure as this process takes place within the internal network of the
enterprise, which would be protected by Firewalls. However, if this Firewall is located on
the network edge, it carries more risk as the unencrypted data can be compromised.
Any client who connects to the Web server via SSL will believe that the data will travel
in encrypted form throughout the journey to the server. They may not know that
technologies such as SSL offloading are being used. If in the rare possibility there had
been a breach and data had been compromised in transit between the SSL offloader
and the Web server, the client may legally sue the enterprise if confidential or sensitive
data had been compromised.
Ref: https://securebox.comodo.com/ssl-sniffing/ssl-offloading/
Encrypting and decrypting network traffic is a very CPU-intensive task for servers. The
initial session setup in particular, demands the most of a CPU. The general purpose
CPUs of server hardware will take a significant hit when a website migrates towards
2048-bit or higher SSL keys.
When upgrading from 1024-bit to 2048-bit keys, the CPU usage typically increases 4–7
times. For 4096-bit keys, server CPUs are bound to reach their limits at typical volumes.
The industry is quickly upgrading to 2048-bit keys; the minimum key length changed
from 1024 to 2048-bit. Certificate Authorities (CAs) no longer provide certificates with
key lengths smaller than 2048-bit.
THREATS CAN HIDE IN ENCRYPTED SSL TRAFFIC
To prevent cyber-attacks, enterprises need to inspect incoming and outgoing traffic for
threats. Unfortunately, attackers are increasingly turning to encryption to evade
detection. With more and more applications using encrypting data- in fact, today, NSS
Labs predicts 75% of Web traffic will be encrypted by 2019 -organizations that do not
inspect SSL communications are providing an open door for attackers to infiltrate
defenses and for malicious insiders to steal sensitive data.
S-ar putea să vă placă și
- Securing .NET Web Services with SSL: How to Protect “Data in Transit” between Client and Remote ServerDe la EverandSecuring .NET Web Services with SSL: How to Protect “Data in Transit” between Client and Remote ServerÎncă nu există evaluări
- SSL y Protocolos de SeguridadDocument12 paginiSSL y Protocolos de Seguridadfrida ortizÎncă nu există evaluări
- Secure Socket Layer (SSL) : Divey Gupta Sunny Gajjar B.Tech-IV Computer Engg. NIT-SuratDocument22 paginiSecure Socket Layer (SSL) : Divey Gupta Sunny Gajjar B.Tech-IV Computer Engg. NIT-SuratSunny Kishorbhai GajjarÎncă nu există evaluări
- Encrypted Threat Protection: White PaperDocument7 paginiEncrypted Threat Protection: White PaperswsloanÎncă nu există evaluări
- DiniDocument20 paginiDiniiraj shaikhÎncă nu există evaluări
- The Concise Guide to SSL/TLS for DevOpsDe la EverandThe Concise Guide to SSL/TLS for DevOpsEvaluare: 4.5 din 5 stele4.5/5 (2)
- U4 4 Secured Socket LayerDocument22 paginiU4 4 Secured Socket LayerNeetishÎncă nu există evaluări
- SSL Decryption - Uncovering The New Infrastructure Blind Spot - Gigamon WhitepaperDocument6 paginiSSL Decryption - Uncovering The New Infrastructure Blind Spot - Gigamon WhitepaperGigamonÎncă nu există evaluări
- EC II CH 3 5Document19 paginiEC II CH 3 5Ness Wadia College of Coomerce PuneÎncă nu există evaluări
- Security ProtocolsDocument4 paginiSecurity Protocolsapi-3701346Încă nu există evaluări
- Protocol World Wide Web Web Servers Browsers URL Web Page HTMLDocument3 paginiProtocol World Wide Web Web Servers Browsers URL Web Page HTMLSumathi SelvarajÎncă nu există evaluări
- 5.3 Secure Socket Layer (SSL)Document4 pagini5.3 Secure Socket Layer (SSL)Aryan PanchalÎncă nu există evaluări
- SSL - Secured Socket Layer - DetailsDocument8 paginiSSL - Secured Socket Layer - DetailsJust Imagine YaarÎncă nu există evaluări
- Choosing A Cloud Hosting Provider With ConfidenceDocument6 paginiChoosing A Cloud Hosting Provider With ConfidencenaoexisteÎncă nu există evaluări
- HTTP SecureDocument6 paginiHTTP SecureFRANCESCO222Încă nu există evaluări
- Choosing A Cloud ProviderDocument9 paginiChoosing A Cloud ProviderGabriel GiraldoÎncă nu există evaluări
- SSL VPN For CLNDocument29 paginiSSL VPN For CLNVJ SNGÎncă nu există evaluări
- Benefits of SSL: Why Use SSL? To Encrypt Sensitive InformationDocument6 paginiBenefits of SSL: Why Use SSL? To Encrypt Sensitive InformationNishu KprÎncă nu există evaluări
- SSL and TLS: Privacy & IntegrityDocument4 paginiSSL and TLS: Privacy & IntegrityVishesh TripathiÎncă nu există evaluări
- Secure Socket Layer: M S.Bhiogade Patni Computer Services, Mumbai, IndiaDocument6 paginiSecure Socket Layer: M S.Bhiogade Patni Computer Services, Mumbai, Indiadidiey87Încă nu există evaluări
- 165 TY B KenilSeminarDocument30 pagini165 TY B KenilSeminarB K EnterpriseÎncă nu există evaluări
- SSLDocument122 paginiSSLKabilan KabilÎncă nu există evaluări
- SSL (Secure Socket Layer)Document52 paginiSSL (Secure Socket Layer)Smita R. S.Încă nu există evaluări
- DocumentDocument1 paginăDocumentHassan AhmadÎncă nu există evaluări
- Secure Socket Layer (SSL)Document47 paginiSecure Socket Layer (SSL)Wasif ImranÎncă nu există evaluări
- SSL - Secure Sockets LayerDocument12 paginiSSL - Secure Sockets LayerAli. RaoÎncă nu există evaluări
- Analyzing Forget SSL Certificates in The Wild PDFDocument15 paginiAnalyzing Forget SSL Certificates in The Wild PDFblob mlÎncă nu există evaluări
- Network Security Unit 4Document32 paginiNetwork Security Unit 4Satyam PandeyÎncă nu există evaluări
- Enabling SSL or TLS in Oracle EBSDocument29 paginiEnabling SSL or TLS in Oracle EBSKris Karr0% (1)
- Secure Socket LayerDocument14 paginiSecure Socket LayerbetoplapaÎncă nu există evaluări
- E Commm PDFDocument5 paginiE Commm PDFChamoadh DissanayakeÎncă nu există evaluări
- BlueCoat Decrypting SSLDocument15 paginiBlueCoat Decrypting SSLRichardÎncă nu există evaluări
- Assignment #1: Submit To: Mr. Junaid MuzaffarDocument4 paginiAssignment #1: Submit To: Mr. Junaid MuzaffarHamza TararÎncă nu există evaluări
- Security in e - CommerceDocument4 paginiSecurity in e - CommerceAlex T BinoyÎncă nu există evaluări
- Web Security and ProtocolsDocument35 paginiWeb Security and ProtocolsFarhan KhurshidÎncă nu există evaluări
- REMOTE ACCESS VPN- SSL VPN: A deep dive into SSL VPN from basicDe la EverandREMOTE ACCESS VPN- SSL VPN: A deep dive into SSL VPN from basicEvaluare: 5 din 5 stele5/5 (1)
- SSL Acceleration: Deployment Strategies For Enterprise SecurityDocument8 paginiSSL Acceleration: Deployment Strategies For Enterprise SecurityMyOwnScribdAccountÎncă nu există evaluări
- Document 376700.1 PDFDocument26 paginiDocument 376700.1 PDFChristiam NiñoÎncă nu există evaluări
- SSL - Secure Sockets LayerDocument15 paginiSSL - Secure Sockets Layerhareem100Încă nu există evaluări
- Secure Hosting With Lets Encrypt in IIS (1) .PPSXDocument43 paginiSecure Hosting With Lets Encrypt in IIS (1) .PPSXAshwani ParasharÎncă nu există evaluări
- Symantec SSL Visibility Appliance: Data SheetDocument6 paginiSymantec SSL Visibility Appliance: Data SheetDebojit GoswamiÎncă nu există evaluări
- SSL CertificationDocument9 paginiSSL Certificationraktim4uÎncă nu există evaluări
- SSL - Secured Socket LayerDocument4 paginiSSL - Secured Socket LayerJust Imagine YaarÎncă nu există evaluări
- A Quick Guide To: SSL/TLS CertificatesDocument9 paginiA Quick Guide To: SSL/TLS CertificatesGrandy DadderÎncă nu există evaluări
- F5 SSL Orchestrator and Symantec DLP: SSL Visibility and Content AdaptionDocument26 paginiF5 SSL Orchestrator and Symantec DLP: SSL Visibility and Content Adaptionalways_redÎncă nu există evaluări
- Radware SSLiDocument6 paginiRadware SSLitarun vermaÎncă nu există evaluări
- What Is SSL?Document13 paginiWhat Is SSL?Pusapati Ramesh babuÎncă nu există evaluări
- ParthDocument20 paginiParthParth KshatriyaÎncă nu există evaluări
- Secure Socket Layer: Barnali Gupta BanikDocument35 paginiSecure Socket Layer: Barnali Gupta BanikbarnaliguptabanikÎncă nu există evaluări
- Secure Socket LayerDocument4 paginiSecure Socket LayerAkhilJaanuÎncă nu există evaluări
- Decryption Why Where and HowDocument6 paginiDecryption Why Where and HowfanvantanÎncă nu există evaluări
- QuestionsDocument4 paginiQuestionsSrinivas Naidu T SÎncă nu există evaluări
- Secure Communication Channels: Secure Sockets Layer (SSL)Document5 paginiSecure Communication Channels: Secure Sockets Layer (SSL)Mani ShankarÎncă nu există evaluări
- How To Implement and Test SSL Decryption - Knowledge Base - Palo Alto NetworksDocument13 paginiHow To Implement and Test SSL Decryption - Knowledge Base - Palo Alto NetworksR2D2 SanshiroÎncă nu există evaluări
- CCN Case StudyDocument13 paginiCCN Case StudyGaurang Gawas100% (1)
- Cloud Application and Network Security 1-9-2023Document7 paginiCloud Application and Network Security 1-9-2023Amit SinsinwarÎncă nu există evaluări
- Apache 2 With SSLDocument31 paginiApache 2 With SSLHari KrishnaÎncă nu există evaluări
- How SSL Works: Web Browser SSL CertificateDocument3 paginiHow SSL Works: Web Browser SSL CertificateSamrah QamarÎncă nu există evaluări
- Introduction To Sockets Layer: SecureDocument12 paginiIntroduction To Sockets Layer: SecurePankaj MalviyaÎncă nu există evaluări
- QuestionsDocument4 paginiQuestionssyed_engrÎncă nu există evaluări
- Web AuthenticationDocument7 paginiWeb Authenticationsyed_engrÎncă nu există evaluări
- Cisco Juniper CommandsDocument2 paginiCisco Juniper Commandssyed_engrÎncă nu există evaluări
- Smart AccountDocument26 paginiSmart Accountsyed_engrÎncă nu există evaluări
- Lab 18 OspfDocument7 paginiLab 18 Ospfsyed_engrÎncă nu există evaluări
- Services-Routers-Isr/product Data Sheet0900aecd8016e845.htmlDocument2 paginiServices-Routers-Isr/product Data Sheet0900aecd8016e845.htmlsyed_engrÎncă nu există evaluări
- 03 Annex III Presentation 1 Project - Risk - ManagementDocument73 pagini03 Annex III Presentation 1 Project - Risk - ManagementJoseph AlcoranÎncă nu există evaluări
- Is UpDocument2 paginiIs Upsyed_engrÎncă nu există evaluări
- SUG541 - Advanced Photogrammetry - Steps Involved in Using Stereo Aerial Triangulation SoftwareDocument22 paginiSUG541 - Advanced Photogrammetry - Steps Involved in Using Stereo Aerial Triangulation Softwaremruzainimf100% (1)
- LCGC Eur Burke 2001 - Missing Values, Outliers, Robust Stat and NonParametric PDFDocument6 paginiLCGC Eur Burke 2001 - Missing Values, Outliers, Robust Stat and NonParametric PDFaloediyahÎncă nu există evaluări
- Identifying Object Relationships, Attributes and MethodsDocument19 paginiIdentifying Object Relationships, Attributes and MethodsGeetha ReddyÎncă nu există evaluări
- ANSI/BICSI 005-2016: Electronic Safety and Security (ESS) System Design and Implementation Best PracticesDocument28 paginiANSI/BICSI 005-2016: Electronic Safety and Security (ESS) System Design and Implementation Best PracticesJonnas Câmara de AbreuÎncă nu există evaluări
- IC Social Media Marketing Plan Template 8957Document5 paginiIC Social Media Marketing Plan Template 8957JamesÎncă nu există evaluări
- PVCMC 0296 Us - tcm106 35825Document233 paginiPVCMC 0296 Us - tcm106 35825enrique.riera7693Încă nu există evaluări
- Freebitco - in Script MULTIPLY BTC BONUS 2020Document2 paginiFreebitco - in Script MULTIPLY BTC BONUS 2020Mohammadreza EmamiÎncă nu există evaluări
- Schedule For Theory Examination (Even Sem.) - 2011-2012 B.Tech., First Year-Ii SemesterDocument66 paginiSchedule For Theory Examination (Even Sem.) - 2011-2012 B.Tech., First Year-Ii SemesterSheetal P. ManiÎncă nu există evaluări
- B.Tech (PT) - Mathematics - II YEAR - III SEM - (R) 2012 PDFDocument15 paginiB.Tech (PT) - Mathematics - II YEAR - III SEM - (R) 2012 PDFmohamed irshadÎncă nu există evaluări
- PP 90264 LIMS Integration Compliance ArabLab2017 PP90264 enDocument25 paginiPP 90264 LIMS Integration Compliance ArabLab2017 PP90264 enPaten PisanÎncă nu există evaluări
- S+ I/O: HAI805 & HAO805 HART I/O: Symphony PlusDocument4 paginiS+ I/O: HAI805 & HAO805 HART I/O: Symphony PlusMD. AL MUZAHIDÎncă nu există evaluări
- Parkinson Disease DetectionDocument5 paginiParkinson Disease DetectionMaximiliano ThiagoÎncă nu există evaluări
- DM-HROD-2021-0340 Central Office Learning and Development Program COLDP Program Offerings For DepEd CO Personnel1Document2 paginiDM-HROD-2021-0340 Central Office Learning and Development Program COLDP Program Offerings For DepEd CO Personnel1Nestor DawatonÎncă nu există evaluări
- SEO AdTech Dave ChaffeyDocument44 paginiSEO AdTech Dave ChaffeysrinivasÎncă nu există evaluări
- THEORY For Wein Bridge Oscillator Using Ic 741 Op AmpDocument1 paginăTHEORY For Wein Bridge Oscillator Using Ic 741 Op AmpPurnima Sri Sai100% (1)
- SimpsonDocument5 paginiSimpsonWazi UddinÎncă nu există evaluări
- Epicor Price Checker FS A4 ENSDocument2 paginiEpicor Price Checker FS A4 ENSJuan Sebastián SánchezÎncă nu există evaluări
- Information Sciences: Decui Liang, Bochun YiDocument18 paginiInformation Sciences: Decui Liang, Bochun YiRico Bayu WiranataÎncă nu există evaluări
- T2K13 SeedsDocument16 paginiT2K13 SeedsRyan Thomas100% (8)
- Sage X3 Partner Learning Catalog - 2020 - FINAL OctDocument50 paginiSage X3 Partner Learning Catalog - 2020 - FINAL OctDinesh PandianÎncă nu există evaluări
- Assignment 2Document33 paginiAssignment 2Yusra GulfamÎncă nu există evaluări
- Sip Series PDocument69 paginiSip Series PSyed Rahmath AliÎncă nu există evaluări
- Datasheet D7050 B6 Data Sheet enUS 2706872715Document2 paginiDatasheet D7050 B6 Data Sheet enUS 2706872715Waldemar Alvares RezendeÎncă nu există evaluări
- Year 6 Week 1 Lesson 1 Main Focus Prior Knowledge Key Vocabulary Curriculum ObjectivesDocument19 paginiYear 6 Week 1 Lesson 1 Main Focus Prior Knowledge Key Vocabulary Curriculum Objectiveslenson kinyuaÎncă nu există evaluări
- LOGAN UputstvoDocument231 paginiLOGAN Uputstvosdunja100% (2)
- An Automation PCI Allocation Method For eNodeB and Home eNodeB CellDocument4 paginiAn Automation PCI Allocation Method For eNodeB and Home eNodeB CellurfriendlyjoeÎncă nu există evaluări
- Lesson Plan: Redesign Classroom FurnitureDocument19 paginiLesson Plan: Redesign Classroom FurnitureMariaÎncă nu există evaluări
- Eagle Point Tutorial - Cross SectionDocument9 paginiEagle Point Tutorial - Cross Sectionqadiradnan7177100% (6)
- Thesis Margins WordDocument8 paginiThesis Margins Wordjpcbobkef100% (2)
- PPC Portfolio PDFDocument11 paginiPPC Portfolio PDFMirena Boycheva50% (2)