Documente Academic
Documente Profesional
Documente Cultură
Assymetric Key Cryptography
Încărcat de
kathiravanTitlu original
Drepturi de autor
Formate disponibile
Partajați acest document
Partajați sau inserați document
Vi se pare util acest document?
Este necorespunzător acest conținut?
Raportați acest documentDrepturi de autor:
Formate disponibile
Assymetric Key Cryptography
Încărcat de
kathiravanDrepturi de autor:
Formate disponibile
Cryptography and network system
Anna University
Unit III
1. _________ refers to the weakness in the security system.
A. Threat
B. Vulnerability
C. Control
D. Intrusion
2. An analyst can determine an algorithm with sufficient _____.
A. Money
B. Time
C. Key
D. Computer data storage
3. Time taken to apply an algorithm in ______ is proportional to the length of the message.
A. Trigrams
B. Diagrams
C. Encipherment Complexity
D. User domain
4. The purpose of computer security is to prevent ______ from doing the _______.
A. attacks, harm
B. attackers, damage
C. threat, needful
D. employees, interference
5. The value of _____ and _____ should not be forgotten when we consider how to enforce security.
A. policies, expectations
B. policies, procedures
C. community standards, expectations
D. community standards, policies
6. When an action attempts to compromises the security of information owned by a firm, it is
called____.
A. Computer security
B. Internal security
C. Security attack
D. Threat
7. You can generate “random” numbers from any ______.
A. Music
B. Book
C. Object
D. All of the above
8. Computer security is needed in a business organisation to prevent damage caused by_____.
A. Employees
B. Intruders
C. Users
D. Suppliers
9. Transposition is also known as ______.
A. Permutation
B. Combination
C. Variation
D. Binomial variation
10. Substitution is an ______ way of encryption.
A. Unacceptable
B. Acceptable
C. Correct
D. Incorrect
11. Which of the following are the corporate-level responsibilities?
A. Accounting
B. Personal activities
C. Team level activities
D. Accounting and Personal activities
12. The characteristic pattern of groups of three letters is called ______.
A. Trigram
B. Encipherment Complexity
C. Diagram
D. One-Time Pad
13. ______ is the process of encoding a plain text to cipher text.
A. Decryption
B. Cryptanalysis
C. Cryptosystem
D. Encryption
14. Book Cipher uses ______ numbers is any book.
A. Sequential
B. Random
C. Both random and sequential
D. Odd
15. Which of the following is yet to achieve extensive adoption?
A. AES
B. DES
C. RSA
D. PSA
16. Secret key is another name for __________.
A. Stream encryption
B. Symmetric encryption
C. Asymmetric encryption
D. Block encryption
17. Block transformation does not depend on which of the following?
A. Control information
B. User information
C. Symbol
D. Key
18. A cryptanalyst is confronted by how many situations?
A. Four
B. Three
C. Five
D. Six
19. How many users can use a secret key?
A. Three
B. One
C. Two
D. Four
20. One of the major drawbacks of the symmetric system is _____.
A. Key Distribution
B. Key Diffusion
C. Key Confusion
D. Key Construction
21. Repeat cycles are used in ________.
A. AES and RSA
B. AES and DES
C. DES and RSA
D. RSA and VAN
22. ______ operation provides diffusion.
A. Add Subkey
B. Byte Substitution
C. Shift Row
D. Mix Column
23. Each cycle of AES algorithm consists of _____ steps.
A. Three
B. Four
C. Two
D. Five
24. Procedure for _____ is C = E(k1, D(k2, E(k1,m))).
A. Triple DES
B. Double DES
C. DES
D. RSA
25. Public key system is best used for _____.
A. Key exchange
B. Authentication
C. Key exchange and Authentication
D. Validation
26. Asymmetric encryption offers a procedure that wraps the protected information in _______
package(s).
A. Two
B. Three
C. Four
D. One
27. The property of hiding implementation and other design decisions of a component is called___.
A. Modularity
B. Encapsulation
C. Polymorphism
D. Information Hiding
28. Fence forms a boundary between _____ and user.
A. File
B. Operating system
C. Memory
D. Central Processing Unit (CPU)
29. Share by capabilities is an extension of __________.
A. Limit object sharing
B. Share all or nothing
C. Limited access sharing
D. Limited use of an object
30. In a ______, the frequency of appearance of letter groups can be used to match up plaintext letters
that have been separated in a ciphertext.
A. Digram
B. Columnar Transposition
C. Book Cipher
D. Vernam Cipher
S-ar putea să vă placă și
- Design and Analysis of Cryptographic AlgrithmDocument273 paginiDesign and Analysis of Cryptographic AlgrithmToanÎncă nu există evaluări
- Verification Approach For ASIC Generic IP Functional VerificationDocument3 paginiVerification Approach For ASIC Generic IP Functional VerificationMohammad Seemab AslamÎncă nu există evaluări
- UVM Based Verification of CAN Protocol Controller Using System VerilogDocument5 paginiUVM Based Verification of CAN Protocol Controller Using System VerilogEditor IJRITCCÎncă nu există evaluări
- SystemVerilog 3.0d.VCS7.1 Beta PDFDocument314 paginiSystemVerilog 3.0d.VCS7.1 Beta PDFlaurent_pubsÎncă nu există evaluări
- System Ver I Log Functional CoverageDocument12 paginiSystem Ver I Log Functional CoverageLakshmisree SajitÎncă nu există evaluări
- Cache Attacks On Arm Thesis PDFDocument103 paginiCache Attacks On Arm Thesis PDFJohn NihaÎncă nu există evaluări
- Xge Mac SpecDocument24 paginiXge Mac Spechackdrag100% (1)
- Amba 3 Axi Protocol Checker: User GuideDocument58 paginiAmba 3 Axi Protocol Checker: User GuidepriyajeejoÎncă nu există evaluări
- Implementation of DDR4 Using System Verilog: GuideDocument16 paginiImplementation of DDR4 Using System Verilog: GuideDhanya KÎncă nu există evaluări
- AHB Lite SpecificationDocument72 paginiAHB Lite SpecificationSuyog Avinash ChutkeÎncă nu există evaluări
- Kactus2: Hierarchical Design Tutorial: Version Date Author CommentsDocument19 paginiKactus2: Hierarchical Design Tutorial: Version Date Author Commentsmuhammad shafiÎncă nu există evaluări
- USB3 Verification Requirement Specification 0.2Document34 paginiUSB3 Verification Requirement Specification 0.2Sachin Kumar JainÎncă nu există evaluări
- Introducing The AMBA Coherent Hub InterfaceDocument57 paginiIntroducing The AMBA Coherent Hub InterfaceHsin-Chu ChenÎncă nu există evaluări
- Verilog Interview QuestionsDocument7 paginiVerilog Interview QuestionsVishal K SrivastavaÎncă nu există evaluări
- RTL Coding Styles That Yield Simulation and Synthesis MismatchesDocument15 paginiRTL Coding Styles That Yield Simulation and Synthesis Mismatchesajaysimha_vlsiÎncă nu există evaluări
- Missing Link: Testbench To DUT Connection by David RichDocument9 paginiMissing Link: Testbench To DUT Connection by David RichapninexÎncă nu există evaluări
- Solution Lab CryptoDocument7 paginiSolution Lab CryptoSyaza IbrahimÎncă nu există evaluări
- Amba 5 Ahb SpecDocument86 paginiAmba 5 Ahb SpecBo LuÎncă nu există evaluări
- Primetime: User Guide: Distributed Multiscenario AnalysisDocument95 paginiPrimetime: User Guide: Distributed Multiscenario AnalysisYongwoo KimÎncă nu există evaluări
- How To Use TRACE32Document7 paginiHow To Use TRACE32Vasile Morariu100% (1)
- VCMDocument522 paginiVCMSai Kumar NallagangulaÎncă nu există evaluări
- ThesisDocument65 paginiThesis쯔엉당꽝/학생/정보통신공학Încă nu există evaluări
- Urg Ug PDFDocument36 paginiUrg Ug PDFKing KhanÎncă nu există evaluări
- PCI-Express ArchitectureDocument89 paginiPCI-Express ArchitectureAhmad F. Mahmood100% (1)
- Rent AgreementDocument3 paginiRent AgreementRAJARAJESHWARI M GÎncă nu există evaluări
- Implementation and Veri Fication of Pci Express Interface in A SocDocument5 paginiImplementation and Veri Fication of Pci Express Interface in A SocMeghana VeggalamÎncă nu există evaluări
- Chapter 11 Cryptographic Hash FunctionsDocument38 paginiChapter 11 Cryptographic Hash FunctionsNimas APÎncă nu există evaluări
- Verification of Driver Logic Using Ambaaxi UvmDocument10 paginiVerification of Driver Logic Using Ambaaxi UvmAnonymous e4UpOQEPÎncă nu există evaluări
- Io MultiplexingDocument19 paginiIo Multiplexingsubramanyam62Încă nu există evaluări
- Lesson 1: Introduction To Computers and ProgrammingDocument31 paginiLesson 1: Introduction To Computers and ProgrammingKrizaleih QuiñonesÎncă nu există evaluări
- SDC AnDocument5 paginiSDC AnRoberto de MedeirosÎncă nu există evaluări
- 2012 DVCon SystemVerilog 2012 PaperDocument13 pagini2012 DVCon SystemVerilog 2012 Papercoolkad81Încă nu există evaluări
- Thesis PDFDocument122 paginiThesis PDFA Divya PreethaÎncă nu există evaluări
- XCELIUM BASIC Vs ADVANCED PROFILERDocument9 paginiXCELIUM BASIC Vs ADVANCED PROFILERPriya JeejoÎncă nu există evaluări
- 2005-SNUG-Paper SystemVerilog Unique and PriorityDocument24 pagini2005-SNUG-Paper SystemVerilog Unique and Priorityvaibhav27aprilÎncă nu există evaluări
- Ams Lec 01 Introduction v01Document136 paginiAms Lec 01 Introduction v01Ahmed AtefÎncă nu există evaluări
- Verification Test Question Paper - MavenDocument4 paginiVerification Test Question Paper - Mavenaman nigamÎncă nu există evaluări
- UVM Usage For Dynamic Reconfiguration of Complex Designs DVCon India 2014 PaperDocument12 paginiUVM Usage For Dynamic Reconfiguration of Complex Designs DVCon India 2014 PaperKunal PanchalÎncă nu există evaluări
- Ankit ResumeDocument3 paginiAnkit ResumenikkyjÎncă nu există evaluări
- CummingsSNUG2006Boston SystemVerilog EventsDocument42 paginiCummingsSNUG2006Boston SystemVerilog EventsRam KrishnaÎncă nu există evaluări
- The Missing Link: The Testbench To Dut Connection: David Rich - Mentor A Siemens BusinessDocument10 paginiThe Missing Link: The Testbench To Dut Connection: David Rich - Mentor A Siemens BusinessMarko NedicÎncă nu există evaluări
- ARM7 Processor FamilyDocument8 paginiARM7 Processor FamilySaravana KumarÎncă nu există evaluări
- UVM SequencesDocument13 paginiUVM SequenceskartikÎncă nu există evaluări
- 17ec53 - Verilog HDL - CombinedDocument124 pagini17ec53 - Verilog HDL - Combinedrachitha sÎncă nu există evaluări
- Phy Interface Pci Express Sata Usb30 ArchitecturesDocument81 paginiPhy Interface Pci Express Sata Usb30 ArchitecturesHardik TrivediÎncă nu există evaluări
- Linking Novas Files With Simulators and Enabling FSDB DumpingDocument134 paginiLinking Novas Files With Simulators and Enabling FSDB Dumpinghdpisces88% (8)
- DFT QuestionsDocument8 paginiDFT QuestionsTarun g100% (1)
- Dma ControllerDocument166 paginiDma ControllerpraveenbhongiriÎncă nu există evaluări
- 15cs338e-15cs338e-Database Security and Privacy - MCQDocument6 pagini15cs338e-15cs338e-Database Security and Privacy - MCQalgatesgiri0% (1)
- EXAM Questions For The Course TTM4135 - Information Security June 2011Document12 paginiEXAM Questions For The Course TTM4135 - Information Security June 2011Noor ThamerÎncă nu există evaluări
- Sic Final (E-Next - In) (E-Next - In)Document56 paginiSic Final (E-Next - In) (E-Next - In)Prathamesh BhosaleÎncă nu există evaluări
- Grade 6 End of Term Test 15-03-24Document5 paginiGrade 6 End of Term Test 15-03-24Priscilla GotoreÎncă nu există evaluări
- App Dev and Emerging TecDocument4 paginiApp Dev and Emerging TecGUMARANG CHARYANNÎncă nu există evaluări
- Information and Network Security Set 1Document6 paginiInformation and Network Security Set 1Sanpreet SinghÎncă nu există evaluări
- EXAM Questions For The Course TTM4135 - Information Security May 2012Document12 paginiEXAM Questions For The Course TTM4135 - Information Security May 2012Noor ThamerÎncă nu există evaluări
- TYBSc (IT) - Sem VI-Sample QuestionsDocument11 paginiTYBSc (IT) - Sem VI-Sample QuestionsRavishankar YadavÎncă nu există evaluări
- Data Science QuestionsDocument5 paginiData Science QuestionsPoonam SharmaÎncă nu există evaluări
- Railway Junior EngineerDocument15 paginiRailway Junior EngineerNavanit KumarÎncă nu există evaluări
- Assignment 2Document7 paginiAssignment 2nazurahÎncă nu există evaluări
- Vocabulary Related To TechnologyDocument6 paginiVocabulary Related To Technologyestefania aranda jimenezÎncă nu există evaluări
- (CONSOLE) Dress - Undress Anyone - Skyrim Mod Talk - The Nexus ForumsDocument3 pagini(CONSOLE) Dress - Undress Anyone - Skyrim Mod Talk - The Nexus ForumsHugoÎncă nu există evaluări
- Standby - FAQ - Oracle Technology Stack - How To Speed Up and Troubleshooting MRP (Log Apply Rate of A Standby Database) Stuck IssuesDocument1 paginăStandby - FAQ - Oracle Technology Stack - How To Speed Up and Troubleshooting MRP (Log Apply Rate of A Standby Database) Stuck IssuessbabuindÎncă nu există evaluări
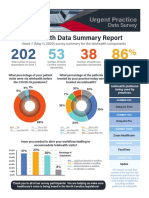
- UPDS Telehealth Data ReportDocument3 paginiUPDS Telehealth Data ReportCorey LarkinsÎncă nu există evaluări
- AWS Solution Architect Syllabus - by Murali P N, Besant TechnologiesDocument7 paginiAWS Solution Architect Syllabus - by Murali P N, Besant TechnologiesBhartish HogadeÎncă nu există evaluări
- MSBI Training PDFDocument4 paginiMSBI Training PDFSachin Bisht100% (1)
- Transparent Image Layer Diffusion Using Latent TransparencyDocument45 paginiTransparent Image Layer Diffusion Using Latent Transparencydaniel.finlandÎncă nu există evaluări
- Sr. No. Key Computer Architecture Computer OrganizationDocument11 paginiSr. No. Key Computer Architecture Computer OrganizationKashif ZamanÎncă nu există evaluări
- Kelas 7 SMP 7402 Inggris Bab 2 IntroducingDocument4 paginiKelas 7 SMP 7402 Inggris Bab 2 IntroducingCorry IntanÎncă nu există evaluări
- Construction Management and EconomicsDocument24 paginiConstruction Management and EconomicsEyob MitekuÎncă nu există evaluări
- Continues Integration Automation Using Jenkins: Java and Open Source CompetencyDocument31 paginiContinues Integration Automation Using Jenkins: Java and Open Source CompetencySamarthÎncă nu există evaluări
- Mortra Trackmaster TMX Field Service Manual - Part 1Document126 paginiMortra Trackmaster TMX Field Service Manual - Part 1Bagas Bxa100% (1)
- ME MECHANICAL Product Design and DevelopmentDocument48 paginiME MECHANICAL Product Design and DevelopmentgauthamkitÎncă nu există evaluări
- Elmer OverviewDocument10 paginiElmer OverviewAbirami RajagopalÎncă nu există evaluări
- المحاضرة 11Document19 paginiالمحاضرة 11هبة نبيل بالخيرÎncă nu există evaluări
- D Murli - Creating Multilingual Website (English - Hindi - Punjabi) Using ASPDocument6 paginiD Murli - Creating Multilingual Website (English - Hindi - Punjabi) Using ASPmrpraveenmÎncă nu există evaluări
- All CCDocument66 paginiAll CCsukoymambo0% (1)
- Super Road Blaster ManualDocument4 paginiSuper Road Blaster Manualmartinadan0% (1)
- A Matlab Tool For Speech Processing Analysis and Recognition Sar LabDocument19 paginiA Matlab Tool For Speech Processing Analysis and Recognition Sar LabAkalu AyenewÎncă nu există evaluări
- Fortios v6.4.13 Release NotesDocument42 paginiFortios v6.4.13 Release NotesAlex10505Încă nu există evaluări
- Java Projects-Applet-SwingsDocument20 paginiJava Projects-Applet-SwingsPravin RajÎncă nu există evaluări
- DVLSI Expt 1Document3 paginiDVLSI Expt 1vickyÎncă nu există evaluări
- 小样本学习研究综述 赵凯琳Document21 pagini小样本学习研究综述 赵凯琳Yong FuÎncă nu există evaluări
- WK3 HandoutDocument12 paginiWK3 HandoutjasonÎncă nu există evaluări
- Inglés Grado 9 TallerDocument5 paginiInglés Grado 9 TallerLady LopezÎncă nu există evaluări
- CS-04 GTC-A/B/C Manual Rotation and AOP Run CompletedDocument2 paginiCS-04 GTC-A/B/C Manual Rotation and AOP Run CompletedShivamÎncă nu există evaluări
- G07L 4G GPS Tracker User ManualDocument6 paginiG07L 4G GPS Tracker User ManualGuido OlaveÎncă nu există evaluări
- MDT Installation Guide Step by StepDocument15 paginiMDT Installation Guide Step by Steptahazzad hossainÎncă nu există evaluări
- GDG 2020-2022 Group - 1: Change Is in The AirDocument17 paginiGDG 2020-2022 Group - 1: Change Is in The AirHarsha OjhaÎncă nu există evaluări