Documente Academic
Documente Profesional
Documente Cultură
CC FirewallsApplicationProxyGatewayARC
Încărcat de
shahedctgDescriere originală:
Titlu original
Drepturi de autor
Formate disponibile
Partajați acest document
Partajați sau inserați document
Vi se pare util acest document?
Este necorespunzător acest conținut?
Raportați acest documentDrepturi de autor:
Formate disponibile
CC FirewallsApplicationProxyGatewayARC
Încărcat de
shahedctgDrepturi de autor:
Formate disponibile
Complliiance Component Comp ance Component
DEFIINIITIION DEF N T ON
Name Application-Proxy Gateway Firewalls Application-Proxy Gateway Firewalls combine OSI Layer 7 (Application Layer) functionality with lower layer access control. The application-proxy gateway firewall software performs the routing between the inside and outside interfaces of the firewall. Application-Proxy Gateway Firewalls add to defense in depth when used with other types of firewalls. They strengthen enforcement of security policies and provide user authentication capability. In the event the application-proxy gateway software ceases to function, the firewall system will not pass network packets through the firewall system. Application-Proxy Gateway Firewalls usually have more extensive logging capabilities than packet filter or stateful inspection because they examine the entire network packet rather than just the network addresses and ports. Application-Proxy Gateway Firewalls provide superior authentication than packet filter or stateful inspection packet filter firewalls where network layer addresses can be easily spoofed. Application-Proxy Gateway Firewalls are less vulnerable to address spoofing attacks than packet filter and stateful inspection firewalls.
Description
Rationale
Benefits
NOTE: Application-Proxy Gateway Firewalls are not generally well suited to high-bandwidth or real-time applications. To reduce the load on the firewall, a Dedicated Proxy Server can be used to secure less timesensitive services such as email and most web traffic. Application-Proxy Gateway Firewalls tend to be limited in terms of support for new network applications and protocols. A separate, application-specific proxy agent is required for each type of network traffic that needs to transit a firewall.
ASSOCIIATED ARCHIITECTURE LEVELS ASSOC ATED ARCH TECTURE LEVELS
List the Domain Name List the Discipline Name List the Technology Area Name List Product Component Name Security Technical Controls Secure Gateways and Firewalls
Document the Compliance Component Type Component Sub-type
COMPLIIANCE COMPONENT TYPE COMPL ANCE COMPONENT TYPE
Guideline
COMPLIIANCE DETAIIL COMPL ANCE DETA L
Each individual application-proxy, also referred to as a proxy agent, shall interface directly with the firewall access control rule set to determine whether a given piece of network traffic should be permitted to transit the firewall. Each individual application-proxy shall have the ability to require authentication of each individual network user. This user authentication shall take two or more of the following forms: o o o State the Guideline, Standard or Legislation o User ID and Password Authentication Hardware or Software Token Authentication Source Address Authentication (on dedicated circuits only) Biometric Authentication
Proxy applications should be used for inbound/outbound HTTP connections and for inbound/outbound email that are capable of the following operations: o o o o Blocking Java applets and applications ActiveX and JavaScript filtering Blocking specific MIME extensions Scanning for viruses
Note: This is not a recommendation to enable blocking of active web content, but to be capable of blocking it if necessary. The decision to block active content, excluding viruses, should be weighed carefully, as blocking active content will render many websites unusable or difficult to use. Organizations should not rely solely on the firewall proxies to remove the above content. Document Source Reference #
Standard Organization
Name Contact Information NIST SP 800-41, Guideline for Firewalls and Firewall Policy Website www.csrc.nist.gov/publications/ nistpubs
Government Body
Name Contact Information National Institute of Standards and Technology (NIST) Website http://csrc.nist.gov/
List all Keywords
Dedicated Proxy Server, proxy agent, block, packets, deny, ports, protocols, logging, attacks, Layer 7, application layer, OSI, HTTP, ActiveX, Java, MIME, authentication, spoof
KEYWORDS KEYWORDS
COMPONENT CLASSIIFIICATIION COMPONENT CLASS F CAT ON
Provide the Classification Document the Rationale for Component Classification Emerging Current Twilight Sunset
Rationale for Component Classification
Conditional Use Restrictions
Document the Conditional Use Restrictions
Migration Strategy
Document the Migration Strategy
Impact Position Statement
Document the Position Statement on Impact
CURRENT STATUS CURRENT STATUS
Provide the Current Status) In Development Under Review Approved Rejected
AUDIIT TRAIIL AUD T TRA L
Creation Date Reason for Rejection Last Date Reviewed Reason for Update Last Date Updated 06/08/2004 Date Accepted / Rejected 06/08/2004
S-ar putea să vă placă și
- 08-CH09-CompSec2e-ver02 Firewalls PDFDocument33 pagini08-CH09-CompSec2e-ver02 Firewalls PDFNikunj PatelÎncă nu există evaluări
- Secure Wireless Firewall Integration: Role of The FirewallDocument54 paginiSecure Wireless Firewall Integration: Role of The FirewallFlavio MirandaÎncă nu există evaluări
- FIREWALLDocument26 paginiFIREWALLmanish 2003Încă nu există evaluări
- CH 09Document24 paginiCH 09jahou NoelÎncă nu există evaluări
- Network Security Basic - FirewallDocument7 paginiNetwork Security Basic - FirewallMunfed RanaÎncă nu există evaluări
- Firewall Design Principles: Software Engineering 4C03Document8 paginiFirewall Design Principles: Software Engineering 4C03Ramachandran1707Încă nu există evaluări
- Firewall Abstract)Document2 paginiFirewall Abstract)Nitish Yadav100% (2)
- Firewalls Are Used To Protect Both Home and Corporate NetworksDocument4 paginiFirewalls Are Used To Protect Both Home and Corporate NetworksAnkita SoniÎncă nu există evaluări
- NIS Unit 4Document13 paginiNIS Unit 4manthanjagatkar998Încă nu există evaluări
- Firewalls: Security TechnologiesDocument63 paginiFirewalls: Security TechnologiespiyushÎncă nu există evaluări
- Enterprise Firewall - v1Document28 paginiEnterprise Firewall - v1Hiten SoniÎncă nu există evaluări
- FW - 7Document73 paginiFW - 7etiÎncă nu există evaluări
- Seminar Report on Firewalls Submitted for BSc DegreeDocument17 paginiSeminar Report on Firewalls Submitted for BSc DegreePiYuSH khaTRIÎncă nu există evaluări
- What Is A FirewallDocument6 paginiWhat Is A Firewall42z4bnwc4nÎncă nu există evaluări
- M 3 I N S: Chapter 2: Server Management and FirewallsDocument45 paginiM 3 I N S: Chapter 2: Server Management and FirewallsChetan ChaudhariÎncă nu există evaluări
- FirewallDocument63 paginiFirewallLorie Jane ReyesÎncă nu există evaluări
- Dot1x Dep Guide - CiscoDocument37 paginiDot1x Dep Guide - CiscoJh0n Fredy HÎncă nu există evaluări
- FireDocument61 paginiFireAnuj SinghÎncă nu există evaluări
- Firewall AbstractDocument5 paginiFirewall AbstractSanthoshÎncă nu există evaluări
- Problems Example: All These Example Are Real CasesDocument24 paginiProblems Example: All These Example Are Real CasesvinodraghuÎncă nu există evaluări
- Chapter6 Review Question&ExercisesDocument6 paginiChapter6 Review Question&ExercisesZenric Jr ClareteÎncă nu există evaluări
- Network Security: Lecturer: Guled Yusuf MihileDocument38 paginiNetwork Security: Lecturer: Guled Yusuf MihileOsmanicÎncă nu există evaluări
- Design and Implementation of Linux Firewall PoliciesDocument11 paginiDesign and Implementation of Linux Firewall PoliciesUjjwal pandeyÎncă nu există evaluări
- Sathish P 1011-0986-2050: Resented YDocument18 paginiSathish P 1011-0986-2050: Resented YSathish Parlapelly100% (1)
- Firrewall and Intrusion Prevention SystemDocument23 paginiFirrewall and Intrusion Prevention Systemfatima gullÎncă nu există evaluări
- PCNSE7 - Pass Palo Alto Networks Certified Network Security Engineer ExamDocument37 paginiPCNSE7 - Pass Palo Alto Networks Certified Network Security Engineer ExamSaurabh Gupta100% (1)
- Firewall Chapter Explains Types Like Packet FilteringDocument7 paginiFirewall Chapter Explains Types Like Packet FilteringPrajwal K RÎncă nu există evaluări
- Firewall Audit Check ListDocument7 paginiFirewall Audit Check ListIsaiahÎncă nu există evaluări
- The Modular Firewall Certification Criteria: Glossary - Version 4.1Document3 paginiThe Modular Firewall Certification Criteria: Glossary - Version 4.1Harshit AgrawalÎncă nu există evaluări
- Netwok CDocument36 paginiNetwok CMohammad Jakirul IslamÎncă nu există evaluări
- Design & Implement Firewall Access ControlDocument5 paginiDesign & Implement Firewall Access ControlJijo JamesÎncă nu există evaluări
- Firewalls: Modified From Slides of Lawrie BrownDocument37 paginiFirewalls: Modified From Slides of Lawrie Brownغانم العتيبيÎncă nu există evaluări
- Firewall & It's TypesDocument10 paginiFirewall & It's TypesArslan Kamran JuttÎncă nu există evaluări
- Hardening Network DevicesDocument3 paginiHardening Network DevicesJaime BlancoÎncă nu există evaluări
- Firewall and Intrusion DetectionDocument67 paginiFirewall and Intrusion DetectionsurendarÎncă nu există evaluări
- CheckPoint NIST 800-41 CorrelationDocument27 paginiCheckPoint NIST 800-41 CorrelationjelopezzÎncă nu există evaluări
- Configuration PresentationDocument17 paginiConfiguration PresentationAbhishek kumarÎncă nu există evaluări
- Firewall NewDocument20 paginiFirewall NewSoumya VijoyÎncă nu există evaluări
- A Firewall Is A Set of Related ProgramsDocument11 paginiA Firewall Is A Set of Related ProgramsDeep RandhawaÎncă nu există evaluări
- Homework 6 116Document3 paginiHomework 6 116LuIs I. GuTiÎncă nu există evaluări
- Firewall 86 SlidesDocument86 paginiFirewall 86 SlidesHarneet Singh ChuggaÎncă nu există evaluări
- Types of Firewalls & their ApproachesDocument10 paginiTypes of Firewalls & their ApproachesArslan Kamran JuttÎncă nu există evaluări
- Firewall Audit ChecklistDocument7 paginiFirewall Audit ChecklistAnil ChiplunkarÎncă nu există evaluări
- Essentials Module 2 Security Operating Platform Firewall TechnologyDocument28 paginiEssentials Module 2 Security Operating Platform Firewall TechnologyRiska AmaliaÎncă nu există evaluări
- Unit VDocument53 paginiUnit Vjayaraj2024Încă nu există evaluări
- Specific Instructional Objectives: Encryption/decryption Technique For Transfer of Data Between Two SecureDocument8 paginiSpecific Instructional Objectives: Encryption/decryption Technique For Transfer of Data Between Two SecureGanesh MoteÎncă nu există evaluări
- Firewalls: Presented By: Leary John H. Tambagahan, LPTDocument23 paginiFirewalls: Presented By: Leary John H. Tambagahan, LPTLeary John Herza TambagahanÎncă nu există evaluări
- Firewalls: Laura Mcfall Depaul University School of Computing and Digital MediaDocument84 paginiFirewalls: Laura Mcfall Depaul University School of Computing and Digital MediasuderÎncă nu există evaluări
- Introduction To FirewallsDocument33 paginiIntroduction To FirewallsSwathi Palle100% (1)
- FirewallsDocument30 paginiFirewallsMin Min ZawÎncă nu există evaluări
- Hillario Zidan - 00000050745 - IF673 - A - UTSDocument4 paginiHillario Zidan - 00000050745 - IF673 - A - UTSHillario ZidanÎncă nu există evaluări
- Submitted By: B.S.S Monica B.Sarath Chaitanya Iii/Ivcse Iii/IvcseDocument10 paginiSubmitted By: B.S.S Monica B.Sarath Chaitanya Iii/Ivcse Iii/IvcseSarathchaitanya BeharaÎncă nu există evaluări
- Seminar on Firewall Protection and DesignDocument19 paginiSeminar on Firewall Protection and DesignSachin GoyalÎncă nu există evaluări
- Welcome: Seminar On FirewallDocument15 paginiWelcome: Seminar On FirewallAshish NautiyalÎncă nu există evaluări
- Enterprise Firewall Types: National Security AgencyDocument2 paginiEnterprise Firewall Types: National Security AgencyFelipe Ramirez HerreraÎncă nu există evaluări
- Stateful Inspection FirewallDocument3 paginiStateful Inspection FirewallKhezar Hayat LashariÎncă nu există evaluări
- Importance of Netwrok SecurityDocument4 paginiImportance of Netwrok SecurityPhani KrishnaÎncă nu există evaluări
- Introduction To Firewalls: © N. Ganesan, PH.DDocument57 paginiIntroduction To Firewalls: © N. Ganesan, PH.DXozanÎncă nu există evaluări
- QuestionsDocument43 paginiQuestionssukeerthi bmeÎncă nu există evaluări
- EA5800-X7 Quick Installation Guide 01Document21 paginiEA5800-X7 Quick Installation Guide 01shahedctgÎncă nu există evaluări
- Ethnicraft Catalogus2016 Groot LRDocument212 paginiEthnicraft Catalogus2016 Groot LRshahedctgÎncă nu există evaluări
- HUAWEI Adding An ONU To An OLT Configuration Guide PDFDocument23 paginiHUAWEI Adding An ONU To An OLT Configuration Guide PDFshahedctgÎncă nu există evaluări
- Cortina EPON OLT-User Manual-Comman Line Operation-V1.6 20170301Document249 paginiCortina EPON OLT-User Manual-Comman Line Operation-V1.6 20170301dellaroza2010Încă nu există evaluări
- S9300 V100R006C00 Configuration Guide - EPON 03Document34 paginiS9300 V100R006C00 Configuration Guide - EPON 03shahedctgÎncă nu există evaluări
- MA5800 Brochure V2.1 3Document2 paginiMA5800 Brochure V2.1 3Manuel HijarÎncă nu există evaluări
- BDCOM NMS InstallationDocument7 paginiBDCOM NMS InstallationIngeniero SoporteeaÎncă nu există evaluări
- FD1508GS-GPON-OLTDocument3 paginiFD1508GS-GPON-OLTshahedctgÎncă nu există evaluări
- T Rec G.988 201711 I!!pdf e PDFDocument670 paginiT Rec G.988 201711 I!!pdf e PDFChunder007Încă nu există evaluări
- XGPON Optical Access TransmissionDocument19 paginiXGPON Optical Access TransmissionangelpyÎncă nu există evaluări
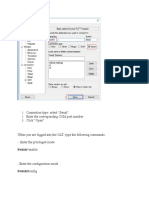
- Connection Type-Select "Serial" Enter The Corresponding COM Port Number Click "Open"Document3 paginiConnection Type-Select "Serial" Enter The Corresponding COM Port Number Click "Open"shahedctgÎncă nu există evaluări
- Unicast Routing CMD Reference Chapter 010001Document378 paginiUnicast Routing CMD Reference Chapter 010001shahedctgÎncă nu există evaluări
- FHL1012B Hardware Description-A01Document32 paginiFHL1012B Hardware Description-A01shahedctgÎncă nu există evaluări
- SMG Wireless Gateway ManualV2.2.0Document95 paginiSMG Wireless Gateway ManualV2.2.0shahedctgÎncă nu există evaluări
- Ethnicraft Catalogus2016 Groot LRDocument212 paginiEthnicraft Catalogus2016 Groot LRshahedctgÎncă nu există evaluări
- Networks Intro PDFDocument9 paginiNetworks Intro PDFTomÎncă nu există evaluări
- Customer Service Incident Report: Print FormDocument1 paginăCustomer Service Incident Report: Print FormshahedctgÎncă nu există evaluări
- Op-Men 99628Document5 paginiOp-Men 99628shahedctgÎncă nu există evaluări
- Customer Service Incident Report: Print FormDocument1 paginăCustomer Service Incident Report: Print FormshahedctgÎncă nu există evaluări
- Network Cameras User ManualDocument92 paginiNetwork Cameras User ManualporvenderÎncă nu există evaluări
- Solarwinds Toolset: Administrator GuideDocument324 paginiSolarwinds Toolset: Administrator GuideYahir PonceÎncă nu există evaluări
- Cambium1000GPSSyncRadio DsDocument2 paginiCambium1000GPSSyncRadio DsshahedctgÎncă nu există evaluări
- Cisco Router Commans Sheet CodesDocument8 paginiCisco Router Commans Sheet CodesGustavo MontanoÎncă nu există evaluări
- Sniffing Basics - MAC Address: Physical StaticDocument12 paginiSniffing Basics - MAC Address: Physical Staticnyonie22messiÎncă nu există evaluări
- MENDocument1 paginăMENshahedctgÎncă nu există evaluări
- BDCOM NMS Installation PDFDocument10 paginiBDCOM NMS Installation PDFshahedctgÎncă nu există evaluări
- MTG1000B Trunk Gateway User ManualDocument123 paginiMTG1000B Trunk Gateway User ManualshahedctgÎncă nu există evaluări
- Route Flap PDFDocument8 paginiRoute Flap PDFshahedctgÎncă nu există evaluări
- EPMP Installation Guide - v1Document15 paginiEPMP Installation Guide - v1shahedctgÎncă nu există evaluări
- Manual - Layer-3 MPLS VPN ExampleDocument7 paginiManual - Layer-3 MPLS VPN ExampleBudi KurniawanÎncă nu există evaluări
- Infoformation Security B IS Lec 2Document12 paginiInfoformation Security B IS Lec 2BSCS4M1033- Muhammad AbdullahÎncă nu există evaluări
- Supplement Cybercrime Presentation Slides. Leicestershire Police - Cybercrime PresentationDocument10 paginiSupplement Cybercrime Presentation Slides. Leicestershire Police - Cybercrime PresentationNicholas LemoniasÎncă nu există evaluări
- IS Unit-2Document125 paginiIS Unit-2Sarath Chandra BanalaÎncă nu există evaluări
- Csvtu Mtech CFIS Syllabus 2nd SemDocument10 paginiCsvtu Mtech CFIS Syllabus 2nd SemShubham KumarÎncă nu există evaluări
- Internet's Growing Role and Cyber Crime RisksDocument13 paginiInternet's Growing Role and Cyber Crime RisksArhamÎncă nu există evaluări
- 1 4Document20 pagini1 4pepelocura2012Încă nu există evaluări
- Information System Security AABFS-Jordan Web Security: SSL and TlsDocument31 paginiInformation System Security AABFS-Jordan Web Security: SSL and TlsManish PopliÎncă nu există evaluări
- Ashish Jangid-19earcs026Document2 paginiAshish Jangid-19earcs026Ashish jangid CS-A 19EARCS026Încă nu există evaluări
- Ubuntu Generate SSH Key Step by StepDocument8 paginiUbuntu Generate SSH Key Step by StepdezaxxlÎncă nu există evaluări
- Forum: Question Of: Student OfficerDocument8 paginiForum: Question Of: Student OfficerZay Ya Phone PyaihÎncă nu există evaluări
- Microsoft Security Intelligence Report Volume 20 - MicrosoftDocument198 paginiMicrosoft Security Intelligence Report Volume 20 - MicrosoftÉcio FerreiraÎncă nu există evaluări
- Forgot Password Best Practices v2.0Document12 paginiForgot Password Best Practices v2.0gaganaroraÎncă nu există evaluări
- HEALTH 10 - Q2 - WK4-doneDocument3 paginiHEALTH 10 - Q2 - WK4-donegraceÎncă nu există evaluări
- Format s2sDocument3 paginiFormat s2sKelson RodriguesÎncă nu există evaluări
- Unit-1 Part-2Document45 paginiUnit-1 Part-2thirumal536Încă nu există evaluări
- Fortinet Single Sign On Polling Mode Windows AD Network PDFDocument6 paginiFortinet Single Sign On Polling Mode Windows AD Network PDFRizky WibowoÎncă nu există evaluări
- FTNT Fast Track Brochure PDFDocument22 paginiFTNT Fast Track Brochure PDFeppoxroÎncă nu există evaluări
- Ransomware - Ransomware Protection GuideDocument7 paginiRansomware - Ransomware Protection GuideDeep PÎncă nu există evaluări
- Web Application Audit ChecklistDocument2 paginiWeb Application Audit Checklistmutlu gündoğduÎncă nu există evaluări
- Endpoint Security Solution GuideDocument21 paginiEndpoint Security Solution GuideGăûřăv Wolvarine ShăřmăÎncă nu există evaluări
- Dual Server Public Key EncryptionDocument5 paginiDual Server Public Key EncryptionVinni SketcherÎncă nu există evaluări
- Access Control Chapter Explains Confidentiality ThreatsDocument3 paginiAccess Control Chapter Explains Confidentiality ThreatsNaveen KumarÎncă nu există evaluări
- AD & Types of AuthenticationDocument3 paginiAD & Types of AuthenticationhfytdyjÎncă nu există evaluări
- Information Technology Act 2000: Salient Features of I.T ActDocument13 paginiInformation Technology Act 2000: Salient Features of I.T ActKaran JaganathÎncă nu există evaluări
- Cse403t HW2 2Document4 paginiCse403t HW2 2jinendran0% (3)
- Emtec Presentation (Newly Edited)Document15 paginiEmtec Presentation (Newly Edited)Mythes JicaÎncă nu există evaluări
- Access Control ModelsDocument35 paginiAccess Control ModelsAnkita Sharma100% (1)
- Advanced Server IPsec ManagementDocument29 paginiAdvanced Server IPsec Management'Hamad AlkhaterÎncă nu există evaluări
- IAM Managing Identity Remains Key To Cyber SecurityDocument48 paginiIAM Managing Identity Remains Key To Cyber Securitykanantaram7197Încă nu există evaluări
- Key Terms To ReviewDocument4 paginiKey Terms To Reviewcram eugnapenÎncă nu există evaluări