Documente Academic
Documente Profesional
Documente Cultură
VPNs Provide Secure Virtual Connections Over Public Networks
Încărcat de
Shrikant JadhavDescriere originală:
Titlu original
Drepturi de autor
Formate disponibile
Partajați acest document
Partajați sau inserați document
Vi se pare util acest document?
Este necorespunzător acest conținut?
Raportați acest documentDrepturi de autor:
Formate disponibile
VPNs Provide Secure Virtual Connections Over Public Networks
Încărcat de
Shrikant JadhavDrepturi de autor:
Formate disponibile
Virtual Private Networks
Many companies have offices and plants scattered over many cities, sometimes over multiple countries. In the olden days, before public data networks, it was common for such companies to lease lines from the telephone company between some or all pairs of locations. Some companies still do this. A network built up from company computers and leased telephone lines is called a private network. An example private network connecting three locations is shown in
Fig. (a) A leased-line private network. (b) A virtual private network. Private networks work fine and are very secure. If the only lines available are the leased lines, no traffic can leak out of company locations and intruders have to physically wiretap the lines to break in, which is not easy to do. The problem with private networks is that leasing a single T1 line costs thousands of dollars a month and T3 lines are many times more expensive. When public data networks and later the Internet appeared, many companies wanted to move their data (and possibly voice) traffic to the public network, but without giving up the security of the private network. This demand soon led to the invention of VPNs (Virtual Private Networks), which are overlay networks on top of public networks but with most of the properties of private networks. They are called ''virtual'' because they are merely an illusion, just as virtual circuits are not real circuits and virtual memory is not real memory. Although VPNs can be implemented on top of ATM (or frame relay), an increasingly popular approach is to build VPNs directly over the Internet. A common design is to equip each office with a firewall and create tunnels through the Internet between all pairs of offices, as illustrated in Fig. 8-30(b). If IPsec is used for the tunneling, then it is possible to aggregate all traffic between any two pairs of offices onto a single authenticated, encrypted SA, thus providing integrity control, secrecy, and even considerable immunity to traffic analysis. When the system is brought up, each pair of firewalls has to negotiate the parameters of its SA, including the services, modes, algorithms, and keys. Many firewalls have VPN capabilities built in, although some ordinary routers can do this as well. But since firewalls are primarily in the security business, it is natural to have the tunnels begin and end at the firewalls, providing a clear separation between the company and the Internet. Thus, firewalls, VPNs, and IPsec with ESP in tunnel mode are a natural combination and widely used in practice. Once the SAs have been established, traffic can begin flowing. To a router within the Internet, a packet traveling along a VPN tunnel is just an ordinary packet. The only thing unusual about it is the presence of the IPsec header after the IP header, but since these extra headers have no effect on the forwarding process, the routers do not care about this extra header. A key advantage of organizing a VPN this way is that it is completely transparent to all user software. The firewalls set up and manage the SAs. The only person who is even aware of this setup is the system administrator who has to configure and manage the firewalls. To everyone else, it is like having a leased-line private network again. For more about VPNs, see (Brown, 1999; and Izzo, 2000).
8.6.4 Wireless Security
It is surprisingly easy to design a system that is logically completely secure by using VPNs and firewalls, but that, in practice, leaks like a sieve. This situation can occur if some of the machines are wireless and use radio communication, which passes right over the firewall in
both directions. The range of 802.11 networks is often a few hundred meters, so anyone who wants to spy on a company can simply drive into the employee parking lot in the morning, leave an 802.11-enabled notebook computer in the car to record everything it hears, and take off for the day. By late afternoon, the hard disk will be full of valuable goodies. Theoretically, this leakage is not supposed to happen. Theoretically, people are not supposed to rob banks, either. Much of the security problem can be traced to the manufacturers of wireless base stations (access points) trying to make their products user friendly. Usually, if the user takes the device out of the box and plugs it into the electrical power socket, it begins operating immediately nearly always with no security at all, blurting secrets to everyone within radio range. If it is then plugged into an Ethernet, all the Ethernet traffic suddenly appears in the parking lot as well. Wireless is a snooper's dream come true: free data without having to do any work. It therefore goes without saying that security is even more important for wireless systems than for wired ones. In this section, we will look at some ways wireless networks handle security. Some additional information can be found in (Nichols and Lekkas, 2002). 802.11 Security The 802.11 standard prescribes a data link-level security protocol called WEP (Wired Equivalent Privacy), which is designed to make the security of a wireless LAN as good as that of a wired LAN. Since the default for wired LANs is no security at all, this goal is easy to achieve, and WEP achieves it, as we shall see. When 802.11 security is enabled, each station has a secret key shared with the base station. How the keys are distributed is not specified by the standard. They could be preloaded by the manufacturer. They could be exchanged in advance over the wired network. Finally, either the base station or user machine could pick a random key and send it to the other one over the air encrypted with the other one's public key. Once established, keys generally remain stable for months or years. WEP encryption uses a stream cipher based on the RC4 algorithm. RC4 was designed by Ronald Rivest and kept secret until it leaked out and was posted to the Internet in 1994. As we have pointed out before, it is nearly impossible to keep algorithms secret, even when the goal is guarding intellectual property (as it was in this case) rather than security by obscurity (which was not the goal with RC4). In WEP, RC4 generates a keystream that is XORed with the plaintext to form the ciphertext. Each packet payload is encrypted using the method of Fig. 8-31. First the payload is checksummed using the CRC-32 polynomial and the checksum appended to the payload to form the plaintext for the encryption algorithm. Then this plaintext is XORed with a chunk of keystream its own size. The result is the ciphertext. The IV used to start RC4 is sent along with the ciphertext. When the receiver gets the packet, it extracts the encrypted payload from it, generates the keystream from the shared secret key and the IV it just got, and XORs the keystream with the payload to recover the plaintext. It can then verify the checksum to see if the packet has been tampered with.
Packet encryption using WEP. While this approach looks good at first glance, a method for breaking it has already been published (Borisov et al., 2001). Below we will summarize their results. First of all, surprisingly many installations use the same shared key for all users, in which case each user can read all the other users' traffic. This is certainly
equivalent to Ethernet, but it is not very secure. But even if each user has a distinct key, WEP can still be attacked. Since keys are generally stable for long periods of time, the WEP standard recommends (but does not mandate) that IV be changed on every packet to avoid the keystream reuse attack we discussed in Sec. 8.2.3. Unfortunately, many 802.11 cards for notebook computers reset IV to 0 when the card is inserted into the computer, and increment it by one on each packet sent. Since people often remove and reinsert these cards, packets with low IV values are common. If Trudy can collect several packets sent by the same user with the same IV value (which is itself sent in plaintext along with each packet), she can compute the XOR of two plaintext values and probably break the cipher that way. But even if the 802.11 card picks a random IV for each packet, the IVs are only 24 bits, so after 224 packets have been sent, they have to be reused. Worse yet, with randomly chosen IVs, the expected number of packets that have to be sent before the same one is used twice is about 5000, due to the birthday attack described in Sec. 8.4.4. Thus, if Trudy listens for a few minutes, she is almost sure to capture two packets with the same IV and same key. By XORing the ciphertexts she is able to obtain the XOR of the plaintexts. This bit sequence can be attacked in various ways to recover the plaintexts. With some more work, the keystream for that IV can also be obtained. Trudy can continue working like this for a while and compile a dictionary of keystreams for various IVs. Once an IV has been broken, all the packets sent with it in the future (but also in the past) can be fully decrypted. Furthermore, since IVs are used at random, once Trudy has determined a valid (IV, keystream) pair, she can use it to generate all the packets she wants to using it and thus actively interfere with communication. Theoretically, a receiver could notice that large number of packets suddenly all have the same IV, but (1) WEP allows this, and (2) nobody checks for this anyway. Finally, the CRC is not worth much, since it is possible for Trudy to change the payload and make the corresponding change to the CRC, without even having to remove the encryption In short, breaking 802.11's security is fairly straightforward, and we have not even listed all the attacks Borisov et al. found.
Congestion Control Algorithms
When too many packets are present in (a part of) the subnet, performance degrades. This situation is called congestion. Figure 5-25 depicts the symptom. When the number of packets dumped into the subnet by the hosts is within its carrying capacity, they are all delivered (except for a few that are afflicted with transmission errors) and the number delivered is proportional to the number sent. However, as traffic increases too far, the routers are no longer able to cope and they begin losing packets. This tends to make matters worse. At very high trafffic, performance collapses completely and almost no packets are delivered.
When too much traffic is offered, congestion sets in and performance degrades sharply. Congestion can be brought on by several factors. If all of a sudden, streams of packets begin arriving on three or four input lines and all need the same output line, a queue will build up. If there is insufficient memory to hold all of them, packets will be lost. Adding more memory may help up to a point, but Nagle (1987) discovered that if routers have an
infinite amount of memory, congestion gets worse, not better, because by the time packets get to the front of the queue, they have already timed out (repeatedly) and duplicates have been sent. All these packets will be dutifully forwarded to the next router, increasing the load all the way to the destination. Slow processors can also cause congestion. If the routers' CPUs are slow at performing the bookkeeping tasks required of them (queueing buffers, updating tables, etc.), queues can build up, even though there is excess line capacity. Similarly, low-bandwidth lines can also cause congestion. Upgrading the lines but not changing the processors, or vice versa, often helps a little, but frequently just shifts the bottleneck. Also, upgrading part, but not all, of the system, often just moves the bottleneck somewhere else. The real problem is frequently a mismatch between parts of the system. This problem will persist until all the components are in balance. It is worth explicitly pointing out the difference between congestion control and flow control, as the relationship is subtle. Congestion control has to do with making sure the subnet is able to carry the offered traffic. It is a global issue, involving the behavior of all the hosts, all the routers, the store-and-forwarding processing within the routers, and all the other factors that tend to diminish the carrying capacity of the subnet. Flow control, in contrast, relates to the point-to-point traffic between a given sender and a given receiver. Its job is to make sure that a fast sender cannot continually transmit data faster than the receiver is able to absorb it. Flow control frequently involves some direct feedback from the receiver to the sender to tell the sender how things are doing at the other end. To see the difference between these two concepts, consider a fiber optic network with a capacity of 1000 gigabits/sec on which a supercomputer is trying to transfer a file to a personal computer at 1 Gbps. Although there is no congestion (the network itself is not in trouble), flow control is needed to force the supercomputer to stop frequently to give the personal computer a chance to breathe. At the other extreme, consider a store-and-forward network with 1-Mbps lines and 1000 large computers, half of which are trying to transfer files at 100 kbps to the other half. Here the problem is not that of fast senders overpowering slow receivers, but that the total offered traffic exceeds what the network can handle. The reason congestion control and flow control are often confused is that some congestion control algorithms operate by sending messages back to the various sources telling them to slow down when the network gets into trouble. Thus, a host can get a ''slow down'' message either because the receiver cannot handle the load or because the network cannot handle it. We will come back to this point later. We will start our study of congestion control by looking at a general model for dealing with it. Then we will look at broad approaches to preventing it in the first place. After that, we will look at various dynamic algorithms for coping with it once it has set in.
S-ar putea să vă placă și
- Virtual Private Networks: (A) A Leased-Line Private Network. (B) A Virtual Private NetworkDocument5 paginiVirtual Private Networks: (A) A Leased-Line Private Network. (B) A Virtual Private NetworkShrikant JadhavÎncă nu există evaluări
- Wireless WEP CrackDocument5 paginiWireless WEP Crack4gen_2Încă nu există evaluări
- WLAN Security: Overview: Saad Hamid, MSEE-12Document6 paginiWLAN Security: Overview: Saad Hamid, MSEE-12Faizan SabirÎncă nu există evaluări
- Lecture 43-52Document37 paginiLecture 43-52Anish SharmaÎncă nu există evaluări
- IEEE Paper Review On Wireless Security and LoopholesDocument4 paginiIEEE Paper Review On Wireless Security and LoopholesMahesh SainiÎncă nu există evaluări
- REMOTE ACCESS VPN- SSL VPN: A deep dive into SSL VPN from basicDe la EverandREMOTE ACCESS VPN- SSL VPN: A deep dive into SSL VPN from basicEvaluare: 5 din 5 stele5/5 (1)
- TTM4137 EssayDocument4 paginiTTM4137 EssayMark SuarezÎncă nu există evaluări
- Hack Wifi - TR SOFTDocument61 paginiHack Wifi - TR SOFTAhmed Saeed0% (1)
- 0072262877_chapter_17Document18 pagini0072262877_chapter_17josivan souzaÎncă nu există evaluări
- Chapter 6 Wireless SecurityDocument8 paginiChapter 6 Wireless SecurityShashant SakhareÎncă nu există evaluări
- Firewalls in Virtual Private Network-A New ApproachDocument14 paginiFirewalls in Virtual Private Network-A New ApproachkarthikÎncă nu există evaluări
- Complete Ethical Hacking: Zero To Mastery Networking TermsDocument9 paginiComplete Ethical Hacking: Zero To Mastery Networking Termscooldude_82Încă nu există evaluări
- Open Wifi VPNDocument5 paginiOpen Wifi VPNd14n4dÎncă nu există evaluări
- 8.1 Security (Examples)Document4 pagini8.1 Security (Examples)Koocker JoysonÎncă nu există evaluări
- Wireless LAN Security Protocols ComparedDocument4 paginiWireless LAN Security Protocols ComparedLisa FowlerÎncă nu există evaluări
- Cybersecurity - IntermediateDocument1.008 paginiCybersecurity - IntermediateKhoa TranÎncă nu există evaluări
- Encryption in Wireless SystemsDocument5 paginiEncryption in Wireless SystemsNeatStickÎncă nu există evaluări
- Paper On Penetration SystemDocument5 paginiPaper On Penetration Systemsumit meshramÎncă nu există evaluări
- Full 7970Document20 paginiFull 7970Cosmin AndreiÎncă nu există evaluări
- Wi-Fi: Wi-Fi For "Wireless Fidelity", Is A Set of Standards ForDocument18 paginiWi-Fi: Wi-Fi For "Wireless Fidelity", Is A Set of Standards Forvivek_juyal2007Încă nu există evaluări
- Chapter 8. Ipsec Chapter 8. Ipsec: Virtual Private Networks (VPN'S)Document15 paginiChapter 8. Ipsec Chapter 8. Ipsec: Virtual Private Networks (VPN'S)gcmaciasÎncă nu există evaluări
- I Hacked My Secure Wireless Network: Here's How It's Done: George GardnerDocument10 paginiI Hacked My Secure Wireless Network: Here's How It's Done: George GardnerbibhutibhusanmohantyÎncă nu există evaluări
- Wireless Network Security Explained in 40 CharactersDocument4 paginiWireless Network Security Explained in 40 CharactersZam ZamÎncă nu există evaluări
- RSA Algorithm Key Generation and Encryption ProcessDocument12 paginiRSA Algorithm Key Generation and Encryption ProcessBIJOY MAJUMDERÎncă nu există evaluări
- CBCN4103 Answer2Document15 paginiCBCN4103 Answer2Ryan JeeÎncă nu există evaluări
- Network Security Fundamentals Guide Solutions Chapter 7Document5 paginiNetwork Security Fundamentals Guide Solutions Chapter 7Mohlomphegi Bennet AphaneÎncă nu există evaluări
- Hacking and Defending in Wireless Networks: A.S.Syed Navaz, K.GirijaDocument4 paginiHacking and Defending in Wireless Networks: A.S.Syed Navaz, K.GirijaagentxsterÎncă nu există evaluări
- Sans Institute Infosec Reading Room: Interested in Learning More About Security?Document16 paginiSans Institute Infosec Reading Room: Interested in Learning More About Security?Jack Fortozo VarelaÎncă nu există evaluări
- Security Fundamentals II Protecting Data With Protocol SecurityDocument5 paginiSecurity Fundamentals II Protecting Data With Protocol SecurityKristopher CharlesÎncă nu există evaluări
- Virtual Private NetworkDocument37 paginiVirtual Private NetworkVinayKumarSinghÎncă nu există evaluări
- Introducing Wireless NetworksDocument5 paginiIntroducing Wireless NetworksAlexsandre MichelsÎncă nu există evaluări
- Set up IPsec Site-to-Site VPNs Between OfficesDocument3 paginiSet up IPsec Site-to-Site VPNs Between OfficesVisakh VijayÎncă nu există evaluări
- IJCER (WWW - Ijceronline.com) International Journal of Computational Engineering ResearchDocument5 paginiIJCER (WWW - Ijceronline.com) International Journal of Computational Engineering ResearchInternational Journal of computational Engineering research (IJCER)Încă nu există evaluări
- Wireless LAN SecurityDocument9 paginiWireless LAN Securityusmanghani.ugÎncă nu există evaluări
- CI-02 Aug05Document26 paginiCI-02 Aug05AKHIL HARIÎncă nu există evaluări
- LAN (Local Area Network) : LAN Stands For Local Area Network. It's A Group of Computers Which All Belong To TheDocument7 paginiLAN (Local Area Network) : LAN Stands For Local Area Network. It's A Group of Computers Which All Belong To TheIas Aspirant AbhiÎncă nu există evaluări
- Improving Your Wireless SecurityDocument8 paginiImproving Your Wireless SecuritypanzettaÎncă nu există evaluări
- Wired Equivalent Privacy: (WEP) : 17th of April, 2003Document6 paginiWired Equivalent Privacy: (WEP) : 17th of April, 2003api-19505025Încă nu există evaluări
- Wireless TechnologiesDocument45 paginiWireless TechnologiesKenneth O'BrienÎncă nu există evaluări
- Wireshark Tutorial - Network & Passwords SnifferDocument12 paginiWireshark Tutorial - Network & Passwords SnifferPutri Ivana DanielleÎncă nu există evaluări
- Unit - IV Wireless Security: Mention Advantages of Wireless Network. - 5Document12 paginiUnit - IV Wireless Security: Mention Advantages of Wireless Network. - 5VinayrajÎncă nu există evaluări
- Security in Adhoc NetworkDocument6 paginiSecurity in Adhoc NetworkAnupriya VÎncă nu există evaluări
- PXC 3871031Document4 paginiPXC 3871031Chairi ZohraÎncă nu există evaluări
- 2002 A Practical Approach To Identifying and Tracking Unauthorized 80211 Cards and Access PointsDocument26 pagini2002 A Practical Approach To Identifying and Tracking Unauthorized 80211 Cards and Access PointsMood IndigoÎncă nu există evaluări
- Mavridis WirelessAttacksDocument5 paginiMavridis WirelessAttacksArghya MukherjeeÎncă nu există evaluări
- Echo on a Chip - Secure Embedded Systems in Cryptography: A New Perception for the Next Generation of Micro-Controllers handling Encryption for Mobile MessagingDe la EverandEcho on a Chip - Secure Embedded Systems in Cryptography: A New Perception for the Next Generation of Micro-Controllers handling Encryption for Mobile MessagingÎncă nu există evaluări
- Report - Wired Equivalent Privacy (WEP)Document5 paginiReport - Wired Equivalent Privacy (WEP)David DasieÎncă nu există evaluări
- OSI model, VPN types, and multiple access techniquesDocument13 paginiOSI model, VPN types, and multiple access techniquesYasir ButtÎncă nu există evaluări
- Competitor: Virtual TunnelDocument14 paginiCompetitor: Virtual TunnelVitthal ChaudhariÎncă nu există evaluări
- Overview of WLAN SecurityDocument7 paginiOverview of WLAN Securityclu5t3rÎncă nu există evaluări
- Wireless Security and Pentest Tutorial Using BacktrackDocument65 paginiWireless Security and Pentest Tutorial Using BacktrackRaluca MunteanuÎncă nu există evaluări
- TCP IP HijackingDocument4 paginiTCP IP HijackingPranay Patel100% (1)
- Report SSLDocument31 paginiReport SSLAwadheshKSinghÎncă nu există evaluări
- V Unit - Wireless Network SecurityDocument22 paginiV Unit - Wireless Network SecurityBRINDHA C it2018Încă nu există evaluări
- 802.11i Encryption Key Distribution Using Quantum CryptographyDocument12 pagini802.11i Encryption Key Distribution Using Quantum Cryptographyaimen_riyadhÎncă nu există evaluări
- Registration Number: CUPB/MTECH-CS/SET/CST/2013-2014/05 CBS.506Document4 paginiRegistration Number: CUPB/MTECH-CS/SET/CST/2013-2014/05 CBS.506Lisa FowlerÎncă nu există evaluări
- Wi-Fi VulnerabilitiesDocument2 paginiWi-Fi Vulnerabilitiesdumitru.alexandru.z5vÎncă nu există evaluări
- An SSL Decryption 4035Document4 paginiAn SSL Decryption 4035Tryphon Tso-hunterÎncă nu există evaluări
- WCDMA UTRAN Signaling Procedures and StructureDocument83 paginiWCDMA UTRAN Signaling Procedures and StructureBruno AndradeÎncă nu există evaluări
- Introduction To Cellular Mobile CommunicationsDocument22 paginiIntroduction To Cellular Mobile Communicationsapi-3717973100% (1)
- CalibrationListing REL 32d International 370a430HPDocument161 paginiCalibrationListing REL 32d International 370a430HPAnonymous nhF45CÎncă nu există evaluări
- Soal Ujian BHS Inggris KLS Xii 2023Document11 paginiSoal Ujian BHS Inggris KLS Xii 2023Haerul anamÎncă nu există evaluări
- Set up bandwidth sharing with Gargoyle routerDocument6 paginiSet up bandwidth sharing with Gargoyle routerDarko MilovanovićÎncă nu există evaluări
- L2VPN ArchitecturesDocument651 paginiL2VPN Architecturestudocris100% (3)
- Eda 1200Document52 paginiEda 1200Jaime Colvatel100% (1)
- Huawei Telecom Equipment for SaleDocument9 paginiHuawei Telecom Equipment for SalepapisÎncă nu există evaluări
- Smooth Wall BasicDocument7 paginiSmooth Wall BasicWally BrownÎncă nu există evaluări
- CMX 138 AdsDocument71 paginiCMX 138 AdsAhmad UmerÎncă nu există evaluări
- CDACDocument16 paginiCDACSmita SakhareÎncă nu există evaluări
- Datasheet S4-WiFi-ST GBR V2.5 2023 06Document2 paginiDatasheet S4-WiFi-ST GBR V2.5 2023 06Bianca OlaruÎncă nu există evaluări
- ABB Drives Function Blocks For Siemens PLCs Quick-Start-Up Guide B A4Document139 paginiABB Drives Function Blocks For Siemens PLCs Quick-Start-Up Guide B A4Automation WorksÎncă nu există evaluări
- Fortiweb Cloud: A Full-Featured Waf That'S Easy To Deploy and ManageDocument3 paginiFortiweb Cloud: A Full-Featured Waf That'S Easy To Deploy and ManageJohnÎncă nu există evaluări
- PIX Firewall 520Document24 paginiPIX Firewall 520seshuaravapalliÎncă nu există evaluări
- pk80 Bluetooth Proximity Reader - 20230323 PDFDocument4 paginipk80 Bluetooth Proximity Reader - 20230323 PDFconstantin larcoÎncă nu există evaluări
- Analog Discovery 2 - Pocket Lab for Engineering TestsDocument1 paginăAnalog Discovery 2 - Pocket Lab for Engineering TeststomichelÎncă nu există evaluări
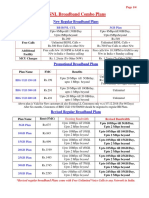
- BSNL All Plans - BB LL FTTH Mobile Aseem Wings Amazon CashbackDocument4 paginiBSNL All Plans - BB LL FTTH Mobile Aseem Wings Amazon Cashbackankushmangal83Încă nu există evaluări
- Beckhoff Bus Coupler BK3100Document95 paginiBeckhoff Bus Coupler BK3100pandhuÎncă nu există evaluări
- FH PlanningDocument68 paginiFH PlanningwonypayukÎncă nu există evaluări
- Linksys Router Login Guide and IssuesDocument4 paginiLinksys Router Login Guide and IssuesSyeda Maarij HassanÎncă nu există evaluări
- MSS LogDocument69 paginiMSS LogNikhil ShahÎncă nu există evaluări
- T2 BookDocument4 paginiT2 Bookirain04Încă nu există evaluări
- Catalogues: Rabigh II Project Interconnecting Package (UO1)Document206 paginiCatalogues: Rabigh II Project Interconnecting Package (UO1)dodonggÎncă nu există evaluări
- Adv7340 7341 PDFDocument108 paginiAdv7340 7341 PDFTheotech EletronÎncă nu există evaluări
- Chap 12Document24 paginiChap 12Smily TheresaÎncă nu există evaluări
- Comparison GPS GLONASS Galileo PLNRaju2Document38 paginiComparison GPS GLONASS Galileo PLNRaju2Saurabh SumanÎncă nu există evaluări
- 07 TN - SP005 - E1 - 1 GNGP Interface and GTP Protocol-34Document34 pagini07 TN - SP005 - E1 - 1 GNGP Interface and GTP Protocol-34IyesusgetanewÎncă nu există evaluări
- Cable Locating, Detection & Cable Fault Finding For 11kV & 33kV, GuidebookDocument168 paginiCable Locating, Detection & Cable Fault Finding For 11kV & 33kV, GuidebookmaungsoekhinÎncă nu există evaluări