Documente Academic
Documente Profesional
Documente Cultură
Metasploit Guide 4: Armitage Cyber Attack Management Gui: You Can Read The, On Searchsecurity - in
Încărcat de
jooker2012Descriere originală:
Titlu original
Drepturi de autor
Formate disponibile
Partajați acest document
Partajați sau inserați document
Vi se pare util acest document?
Este necorespunzător acest conținut?
Raportați acest documentDrepturi de autor:
Formate disponibile
Metasploit Guide 4: Armitage Cyber Attack Management Gui: You Can Read The, On Searchsecurity - in
Încărcat de
jooker2012Drepturi de autor:
Formate disponibile
P a g e |1
Metasploit guide 4: Armitage cyber attack management GUI
Karthik R, Contributor
You can read the original article here, on SearchSecurity.in.
This fourth and final installment of our Metasploit guide takes a look at Armitage, the cyber attack management tool for Metasploit. Armitage provides a GUI for the console-based framework that we covered in the previous three parts of this Metasploit guide. Let us explore exploiting of a vulnerable target using Armitage.
Figure 1: Launching Armitage on Backtrack 5 In Backtrack 5, Armitage can be launched as shown in Figure 1. Once Armitage is launched, a connect screen is displayed as shown in Figure 2. Click the Start MSF button to launch the Metasploit GUI. It is advisable to run the mysql start service command before proceeding with Armitage.
http://searchsecurity.techtarget.in/tutorial/Metasploit-guide-4-Armitage-cyber-attack-management-GUI
P a g e |2
Figure 2: Connect screen The Metasploit connect screen specifies the local host on which Armitage runs, as well as the port number where the database has to connect. The password is encrypted, and the mysql database is used. There is an option for postgresql too. Clicking on Start MSF launches the screen as seen in Figure 3. For the next step in this Metasploit guide, select Hosts > msfscans, and then enter the IP address range as prompted. Once this is done, you are presented with the hosts in a panel to the right, as scanned by msfscan. The panel to the left shows the different modules that are part of the Metasploit package.
http://searchsecurity.techtarget.in/tutorial/Metasploit-guide-4-Armitage-cyber-attack-management-GUI
P a g e |3
Figure 3: Armitage GUI, with the console at the bottom For the next step in this Metasploit guide, we shall do an Nmap scan of the network, using the target as 192.168.13.130. To accomplish this task, select Hosts > Nmap Scans > Intense scans. Various scan options are available, as bundled with the regular Nmap tool, and these can be executed as and when needed. A new scan window opens adjacent to the console, displaying the GUI activities. It identifies all the open ports and services running on them, grabs the banners and identifies the OS on the target. For this Metasploit guide, now select attacks > find attacks to find the applicable attacks with respect to the target. Figure 4 shows the scan result of Nmap in a panel adjacent to the console, clearly indicating the user accounts, workgroups, OS, and other vital information about the system.
http://searchsecurity.techtarget.in/tutorial/Metasploit-guide-4-Armitage-cyber-attack-management-GUI
P a g e |4
Figure 4: Nmap scan result Once the attack analysis is complete, Armitage generates a menu with a list of attacks possible on the target, as shown in Figure 5.
Figure 5: Attack menu with respect to each scanned host The next step in this Metasploit guide is to attempt to revisit the ms03_026_dcom exploit, or the famous RPC DCOM buffer overflow exploit on the target system. Note that this is equivalent to attacking the target using console operations as depicted in the previous installments of this Metasploit guide.
http://searchsecurity.techtarget.in/tutorial/Metasploit-guide-4-Armitage-cyber-attack-management-GUI
P a g e |5
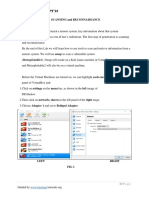
Exploiting browser-based vulnerability on Windows 7 using Armitage: For the first time in this Metasploit guide series, we are covering a Windows 7 penetration method, using a browser-based vulnerability. Within the exploit folder in the left panel, choose windows > browser > ms11_003_ie_css_import vulnerability.
Figure 6: Options of the ms11_003_ie_css_import vulnerability of Windows 7 The values to look out for are LHOST, SRVPORT and URIPATH. The exploit launches a server attacker system, and waits for a connection from the victim. When the victim connects to the URL http://192.168.13.132:8080/ from Internet Explorer, the attacker gains control of the victim, as the Meterpreter shell is planted in the target.
http://searchsecurity.techtarget.in/tutorial/Metasploit-guide-4-Armitage-cyber-attack-management-GUI
P a g e |6
Figure 7: The exploit at work once the victim clicks on the link On being compromised, the color of the victims machine in the panel changes to red.
Figure 8:Post-exploitation attack options available to the user
http://searchsecurity.techtarget.in/tutorial/Metasploit-guide-4-Armitage-cyber-attack-management-GUI
P a g e |7
Post-exploitation phase on Armitage: As seen in Figure 8, the main menu consists of Attack, Login, Meterpreter, Services and Scan operations. The Meterpreter 1 is of interest to us, as it is the shell that provides access to the victim. In the Access sub-menu, we can obtain the password dumps, and also escalate privileges to the target system. The Interact sub-menu opens a shell in the remote system, facilitating manipulation of the system as desired by the attacker. This attack is appropriate when the victim is behind a firewall/NAT, when penetration without social engineering would be extremely complicated. With this article, we conclude the Metasploit guide series. Metasploit can be operated as a console-based framework or as a GUI-based framework using Armitage. Each option has its merits and the choice of which one to use is dependent on the desired exploitation scenarios. Either way, as we have seen in this Metasploit guide series, Metasploit is a powerful framework, so use it wisely and carefully, and never harm anyone by your actions.
About the author: Karthik R is a member of the NULL community. Karthik completed his training for EC-council CEH in December 2010, and is at present pursuing his final year of B.Tech in Information Technology, from National Institute of Technology, Surathkal. Karthik can be contacted on rkarthik.poojary@gmail.com. He blogs at http://www.epsilonlambda.wordpress.co You can subscribe to our twitter feed at @SearchSecIN. You can read the original story here, on
SearchSecurity.in.
http://searchsecurity.techtarget.in/tutorial/Metasploit-guide-4-Armitage-cyber-attack-management-GUI
S-ar putea să vă placă și
- Metasploit - Tutorial Part.1Document7 paginiMetasploit - Tutorial Part.1seyi0Încă nu există evaluări
- Metasploit - Tutorial Part.2Document6 paginiMetasploit - Tutorial Part.2seyi0Încă nu există evaluări
- Armitage ManualDocument17 paginiArmitage Manualhumayunsaggu0% (1)
- BackTrack 5 Tutorial 2Document6 paginiBackTrack 5 Tutorial 2zpoturica569Încă nu există evaluări
- Metasploit Tutorial Part 1: Inside The Metasploit Framework: You Can Read The, On Searchsecurity - inDocument7 paginiMetasploit Tutorial Part 1: Inside The Metasploit Framework: You Can Read The, On Searchsecurity - inprograme infoÎncă nu există evaluări
- Manual ArmitageDocument21 paginiManual ArmitageD'grit Tokan TrickÎncă nu există evaluări
- System Penetration With Metasploit Framework: Ajit Kumar PradhanDocument5 paginiSystem Penetration With Metasploit Framework: Ajit Kumar PradhanXman ReturnsÎncă nu există evaluări
- BackTrack 5 Tutorial 4Document6 paginiBackTrack 5 Tutorial 4zpoturica569Încă nu există evaluări
- Metasploit Basics, Part 15 - Post - Exploitation Fun (Web Cam, Microphone, Passwords and More)Document13 paginiMetasploit Basics, Part 15 - Post - Exploitation Fun (Web Cam, Microphone, Passwords and More)stefan22222222Încă nu există evaluări
- ArmitageDocument39 paginiArmitagekalyanÎncă nu există evaluări
- UNIT 5 PentestDocument20 paginiUNIT 5 PentestOindrila DasÎncă nu există evaluări
- ArmitageDocument54 paginiArmitageworkmumbai3870Încă nu există evaluări
- Lab 19 MetasploitDocument11 paginiLab 19 Metasploitoscar tebarÎncă nu există evaluări
- RDP PenetrationTestingDocument28 paginiRDP PenetrationTestingruben.hernandezg79Încă nu există evaluări
- RDP Pen TestingDocument28 paginiRDP Pen TestingSssssÎncă nu există evaluări
- Use of Metasploit Framework in Kali Linux: April 2015Document9 paginiUse of Metasploit Framework in Kali Linux: April 2015proftechitspecialistÎncă nu există evaluări
- 2.how To Set Up Armitage in Backtrack For Penetration Test - Vishnu ValentinoDocument12 pagini2.how To Set Up Armitage in Backtrack For Penetration Test - Vishnu ValentinocyberssÎncă nu există evaluări
- 01-How To Hack Windows XP Using Metasploit (MS08-067)Document9 pagini01-How To Hack Windows XP Using Metasploit (MS08-067)Alvakonda Venkata PaneendraÎncă nu există evaluări
- 6.system HackingDocument50 pagini6.system Hackingcafenight2547Încă nu există evaluări
- SET-Social Engineering ToolkitDocument5 paginiSET-Social Engineering ToolkitTumwine Kahweza ProsperÎncă nu există evaluări
- MsfpayloadDocument14 paginiMsfpayloadfrogman1001Încă nu există evaluări
- Credential Dumping SecurityDocument14 paginiCredential Dumping SecuritycptraavanÎncă nu există evaluări
- Metasploit: Metasploit Is An Exploitation FrameworkDocument4 paginiMetasploit: Metasploit Is An Exploitation FrameworkrockÎncă nu există evaluări
- Metasploit LabsDocument11 paginiMetasploit Labsshoki666Încă nu există evaluări
- BackTrack 5 Tutorial 3 BackTrackDocument6 paginiBackTrack 5 Tutorial 3 BackTrackmihaiovidiuÎncă nu există evaluări
- MetasploitDocument26 paginiMetasploitDeepak Prakash JayaÎncă nu există evaluări
- Explaining and Configuring NIS (Network Inspection Service) : WWW - It-Training-Grote - deDocument7 paginiExplaining and Configuring NIS (Network Inspection Service) : WWW - It-Training-Grote - deKhodor AkoumÎncă nu există evaluări
- Lab 8 - Gaining Access of Metasploitable Machine Using Metasploit FrameworkDocument1 paginăLab 8 - Gaining Access of Metasploitable Machine Using Metasploit FrameworkPratham PandeyÎncă nu există evaluări
- Penetrating Windows 8 With Syringe UtiliDocument5 paginiPenetrating Windows 8 With Syringe UtiliAGBADAN Yao EricÎncă nu există evaluări
- Use of Metasploit Framework in Kali Linux: April 2015Document9 paginiUse of Metasploit Framework in Kali Linux: April 2015Mouad BelhajÎncă nu există evaluări
- Exploitation of PDF Reader Vulnerabilities Using Metasploit Tool-IJEME-V7-N5-3Document12 paginiExploitation of PDF Reader Vulnerabilities Using Metasploit Tool-IJEME-V7-N5-3Yusuf KılıçÎncă nu există evaluări
- Metasploit Penetration Testing Cookbook: Chapter No. 4 "Client-Side Exploitation and Antivirus Bypass"Document44 paginiMetasploit Penetration Testing Cookbook: Chapter No. 4 "Client-Side Exploitation and Antivirus Bypass"jagdevs7234Încă nu există evaluări
- A Poisoned Apple: The Analysis of Macos Malware Shlayer: By: Minh D. NguyenDocument7 paginiA Poisoned Apple: The Analysis of Macos Malware Shlayer: By: Minh D. NguyencapsÎncă nu există evaluări
- 2021-07-01 - Evasive Techniques Used by Malicious Linux Shell ScriptsDocument8 pagini2021-07-01 - Evasive Techniques Used by Malicious Linux Shell ScriptsRoad Pirate FilmsÎncă nu există evaluări
- Hakin9 EXPLOITING - SOFTWARE TBO (01 - 2013) - Metasploit Tutorials PDFDocument181 paginiHakin9 EXPLOITING - SOFTWARE TBO (01 - 2013) - Metasploit Tutorials PDFjordanofreitas100% (5)
- UntitledDocument45 paginiUntitledWoyÎncă nu există evaluări
- Hackercool - August 2021Document68 paginiHackercool - August 2021Bacho KiroÎncă nu există evaluări
- BackTrack 5 Tutorial 1Document7 paginiBackTrack 5 Tutorial 1carlosbahiavitÎncă nu există evaluări
- FAQ Final Session4Document3 paginiFAQ Final Session4abdelrman moatazÎncă nu există evaluări
- Penetration Testing With Metasploit FrameworkDocument16 paginiPenetration Testing With Metasploit FrameworkrhddevÎncă nu există evaluări
- Met ASP Lo ItDocument16 paginiMet ASP Lo ItpmachinaudÎncă nu există evaluări
- Ethical Hacking Assignment 1Document5 paginiEthical Hacking Assignment 1vilayilvaishnavÎncă nu există evaluări
- Lab 4: Metasploit Framework: CSC 4992 Cyber Security PracticeDocument22 paginiLab 4: Metasploit Framework: CSC 4992 Cyber Security Practiceleyowof787Încă nu există evaluări
- LAB 1 - Scanning - & - Reconnaissance - V1.2Document16 paginiLAB 1 - Scanning - & - Reconnaissance - V1.2Josiah MarcanoÎncă nu există evaluări
- Kali 3Document10 paginiKali 3michal hanaÎncă nu există evaluări
- Armitage Introduction LabDocument19 paginiArmitage Introduction Labsudarshan karkiÎncă nu există evaluări
- UntitledDocument14 paginiUntitledsufiyanÎncă nu există evaluări
- Lab4 Instruction PDFDocument22 paginiLab4 Instruction PDFTester MaheÎncă nu există evaluări
- Hack Like A Pro Metasploit For The Aspiring HackerDocument33 paginiHack Like A Pro Metasploit For The Aspiring HackertarufiÎncă nu există evaluări
- Club Hack Magazine 35 PDFDocument31 paginiClub Hack Magazine 35 PDFLeonardo Herrera RomeroÎncă nu există evaluări
- Introduction To ICC AVR: Setting Up A New Project: NEX Robotics Fire Bird III - ICCAVR ManualDocument12 paginiIntroduction To ICC AVR: Setting Up A New Project: NEX Robotics Fire Bird III - ICCAVR ManualChester Noel Brenes AguirreÎncă nu există evaluări
- Cours3 MetasploitDocument18 paginiCours3 MetasploitNezari SofianeÎncă nu există evaluări
- JTAG Combined Attack: - Another Approach For Fault InjectionDocument5 paginiJTAG Combined Attack: - Another Approach For Fault InjectionJohnny LawrenceÎncă nu există evaluări
- MITM and Reverse TCP Attacks: Department of Mathematical Information Technology, University of Jyv Askyl ADocument6 paginiMITM and Reverse TCP Attacks: Department of Mathematical Information Technology, University of Jyv Askyl Avenkata89Încă nu există evaluări
- CO1508 Computer Systems & Security - Week 02 - Passwords, Patches and Mandatory Access Control (MAC)Document8 paginiCO1508 Computer Systems & Security - Week 02 - Passwords, Patches and Mandatory Access Control (MAC)Edward LeeÎncă nu există evaluări
- ETHICAL HACKING GUIDE-Part 3: Comprehensive Guide to Ethical Hacking worldDe la EverandETHICAL HACKING GUIDE-Part 3: Comprehensive Guide to Ethical Hacking worldÎncă nu există evaluări
- MATLAB Machine Learning Recipes: A Problem-Solution ApproachDe la EverandMATLAB Machine Learning Recipes: A Problem-Solution ApproachÎncă nu există evaluări
- Python for Cybersecurity: Using Python for Cyber Offense and DefenseDe la EverandPython for Cybersecurity: Using Python for Cyber Offense and DefenseÎncă nu există evaluări
- Landcorp FLCC Brochure 2013 v3Document6 paginiLandcorp FLCC Brochure 2013 v3Shadi GarmaÎncă nu există evaluări
- DR Afwan Fajri - Trauma - Juli 2023Document82 paginiDR Afwan Fajri - Trauma - Juli 2023afwan fajriÎncă nu există evaluări
- Financial Management of Public Sector Unit (PSU) - NotesDocument23 paginiFinancial Management of Public Sector Unit (PSU) - Notesbiz19100% (1)
- Poka-Yoke or Mistake Proofing: Historical Evolution.Document5 paginiPoka-Yoke or Mistake Proofing: Historical Evolution.Harris ChackoÎncă nu există evaluări
- Load Schedule: DescriptionDocument1 paginăLoad Schedule: Descriptionkurt james alorroÎncă nu există evaluări
- 5000-5020 en PDFDocument10 pagini5000-5020 en PDFRodrigo SandovalÎncă nu există evaluări
- IELTS Material Writing 1Document112 paginiIELTS Material Writing 1Lê hoàng anhÎncă nu există evaluări
- CP3 - June2019 2Document5 paginiCP3 - June2019 2Sifei ZhangÎncă nu există evaluări
- ABHIGYAN 2020 E-InvitationDocument2 paginiABHIGYAN 2020 E-Invitationchirag sabhayaÎncă nu există evaluări
- Ocr A Level History Russia CourseworkDocument7 paginiOcr A Level History Russia Courseworkbcrqhr1n100% (1)
- (QII-L2) Decorate and Present Pastry ProductsDocument30 pagini(QII-L2) Decorate and Present Pastry ProductsLD 07100% (1)
- PEA Comp Study - Estate Planning For Private Equity Fund Managers (ITaback, JWaxenberg 10 - 10)Document13 paginiPEA Comp Study - Estate Planning For Private Equity Fund Managers (ITaback, JWaxenberg 10 - 10)lbaker2009Încă nu există evaluări
- WeldingDocument23 paginiWeldingMathan EverÎncă nu există evaluări
- Note Hand-Soldering eDocument8 paginiNote Hand-Soldering emicpreampÎncă nu există evaluări
- Eaai S 23 02045 PDFDocument28 paginiEaai S 23 02045 PDFAnjali JainÎncă nu există evaluări
- B.e.eeeDocument76 paginiB.e.eeeGOPINATH.MÎncă nu există evaluări
- U2 KeyDocument2 paginiU2 KeyHằng ĐặngÎncă nu există evaluări
- Review and Basic Principles of PreservationDocument43 paginiReview and Basic Principles of PreservationKarl Marlou Bantaculo100% (1)
- CNC - Rdmacror: Public Static Extern Short Ushort Short Short ShortDocument3 paginiCNC - Rdmacror: Public Static Extern Short Ushort Short Short ShortKession HouÎncă nu există evaluări
- Tutorial 6Document3 paginiTutorial 6Lai Qing YaoÎncă nu există evaluări
- PMDG 737NGX Tutorial 2 PDFDocument148 paginiPMDG 737NGX Tutorial 2 PDFMatt HenryÎncă nu există evaluări
- Wps For Carbon Steel THK 7.11 GtawDocument1 paginăWps For Carbon Steel THK 7.11 GtawAli MoosaviÎncă nu există evaluări
- Lecture 1 Electrolyte ImbalanceDocument15 paginiLecture 1 Electrolyte ImbalanceSajib Chandra RoyÎncă nu există evaluări
- Xii Mathematics CH 01 Question BankDocument10 paginiXii Mathematics CH 01 Question BankBUNNY GOUDÎncă nu există evaluări
- MMB & DFT 2012 Workshop ProceedingsDocument44 paginiMMB & DFT 2012 Workshop ProceedingsFelipe ToroÎncă nu există evaluări
- Star Wars Galactic Connexionstm Galactic Beckett Star Wars Story Connexions CallingDocument4 paginiStar Wars Galactic Connexionstm Galactic Beckett Star Wars Story Connexions CallingJuan TorresÎncă nu există evaluări
- HC+ Shoring System ScaffoldDocument31 paginiHC+ Shoring System ScaffoldShafiqÎncă nu există evaluări
- Ziarek - The Force of ArtDocument233 paginiZiarek - The Force of ArtVero MenaÎncă nu există evaluări
- Case Study Managerial EconomicsDocument4 paginiCase Study Managerial EconomicsZaza Afiza100% (1)
- Quiz 2 I - Prefix and Suffix TestDocument10 paginiQuiz 2 I - Prefix and Suffix Testguait9Încă nu există evaluări