Documente Academic
Documente Profesional
Documente Cultură
CNS 320 Week3 Lab
Încărcat de
alb3rtlinDrepturi de autor
Formate disponibile
Partajați acest document
Partajați sau inserați document
Vi se pare util acest document?
Este necorespunzător acest conținut?
Raportați acest documentDrepturi de autor:
Formate disponibile
CNS 320 Week3 Lab
Încărcat de
alb3rtlinDrepturi de autor:
Formate disponibile
CNS 320 COMPUTER FORENSICS & INCIDENT RESPONSE
Week 3 Lab
Copyright 2012, John McCash. This work may be copied, modified, displayed and distributed under conditions set forth in the Creative Commons AttributionNoncommercial License. To view a copy of this license, visit http://creativecommons.org/licenses/by-nc/2.0/ or send a letter to Creative Commons, 559 Nathan Abbott Way, Stanford, California 94305, USA.
For convenience, escalate to a root shell
sudo bash You should still have both images mounted in your Linux SIFT Kit
If not, refer to last weeks lab for how to mount them back up
Regripper on the Linux SIFT Kit
So for example:
/usr/local/bin/rip.pl -r "/home/sansforensics/Desktop/mou nt_points/windows_mount/Docume nts and Settings/Mr. Evil/NTUSER.DAT" -f ntuser (Quotes are necessary around file or folder paths that include spaces)
reglookup-recover (One of the utilities for extracting deleted registry content)
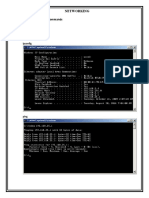
rip.pl and reglookup-recover on dblake system hive
Note the complimentary information in the output
See the deleted registry service key for mdd? Thats a physical memory acquisition tool that was run on this host before the disk image was acquired. It installs and subsequently removes a device driver
Lab #3 Part 1: Registry Hive Extraction
You have the two parts of a Computer Forensics Reference Dataset image in the files 4Dell Latitude CPi(1).E01 and 4Dell Latitude CPi(1).E01 on your lab system. From your Windows Sift Kit VM, open this disk image in FTK Imager, and extract some of the registry hives Examine these files using Regedit, AccessData Registry Viewer, and Regripper
8
Run FTK Imager Add Evidence Item
Image File
Browse to First Image Segment Hit Finish
First Hive to Export: NTUSER.DAT under account: Mr. Evil
Right-click & select Export Files`
Select destination E:\ Hit OK
Select Additional Registry Hives and export the same way
Lab #2 Part 2: Registry Hive Examination with Regedit
Generally more trouble than its worth except on a live system. Even then, lack of date visibility is problematic Regedit is also not read-only To examine non-native hive files, you have to mount them, using load hive under some other key such as HKEY_USERS
Run Regedit
Load Hive
Select Hive File to Load
Type key name to mount hive as
External System hive now visible under local HKEY_USERS
When finished, select hive mount point, and click Unload Hive
Lab #2 Part 3: Registry Examination with AccessData Registry Viewer
Run it Click No to run in demo mode Click Open & Select Hive File
Select Hive File to Examine
System in AccessData Registry Viewer
Lab #2 Part 4: Registry Examination with Yaru
Run Yaru Select Open Hive Browse to Hive File
Yaru deleted key/value recovery example
Current System Name
Current Timezone Information
Last System Shutdown Date/Time
Lab #2 Part 5: Registry Examination with Regripper
Run Regripper Select Hive to Process Provide output filename Select Plugin File (type of registry hive to process) Rip It (Do this for each of the Hive files we exported)
Run Regripper on Exported SAM Hive
Excerpt from SAM Hive Regripper Output (1)
Username : Mr. Evil [1003] Full Name : User Comment : Account Type : Default Admin User Account Created : Thu Aug 19 23:03:54 2004 Z Last Login Date : Fri Aug 27 15:08:23 2004 Z Pwd Reset Date : Thu Aug 19 23:03:54 2004 Z Pwd Fail Date : Never Login Count : 15 --> Password does not expire --> Normal user account
Excerpt from SAM Hive Regripper Output (2)
Username : Administrator [500] Full Name : User Comment : Built-in account for administering the computer/domain Account Type : Default Admin User Account Created : Thu Aug 19 16:59:24 2004 Z Last Login Date : Never Pwd Reset Date : Thu Aug 19 17:17:29 2004 Z Pwd Fail Date : Never Login Count :0 --> Password does not expire --> Normal user account
Excerpt from SAM Hive Regripper Output (3)
Group Name : Administrators [2] LastWrite : Thu Aug 19 23:03:54 2004 Z Group Comment : Administrators have complete and unrestricted access to the computer/domain Users : S-1-5-21-2000478354-6887898441708537768-1003 S-1-5-21-2000478354-6887898441708537768-500
Lab #2 Part 6: Image Registry Autoruns Extraction
Load image using AccessData Imager Mount image with read/write caching Run autoruns against mounted image
With Image Loaded in FTK Imager, Select Image Mounting
Set Parameters
Run Autoruns Select Analyze Offline System
Enter Parameters for Windows folder & Mr. Evil Profile
Lab #1 Part 5: Registry Hive Extraction
You have the two parts of a Computer Forensics Reference Dataset image in the files 4Dell Latitude CPi(1).E01 and 4Dell Latitude CPi(1).E01 on your lab system. From your Windows Sift Kit VM, open this disk image in FTK Imager, and extract some of the registry hives Examine these files using Regedit, AccessData Registry Viewer, and Regripper
46
Run FTK Imager Add Evidence Item
Image File
Browse to First Image Segment Hit Finish
First Hive to Export: NTUSER.DAT under account: Mr. Evil
Right-click & select Export Files`
Select destination E:\ Hit OK
Select Additional Registry Hives and export the same way
Lab #1 Part 6: Registry Hive Examination with Regedit
Generally more trouble than its worth except on a live system. Even then, lack of date visibility is problematic Regedit is also not read-only To examine non-native hive files, you have to mount them, using load hive under some other key such as HKEY_USERS
Run Regedit
Load Hive
Select Hive File to Load
Type key name to mount hive as
External System hive now visible under local HKEY_USERS
When finished, select hive mount point, and click Unload Hive
Lab #1 Part 7: Registry Examination with AccessData Registry Viewer
Run it Click No to run in demo mode Click Open & Select Hive File
Select Hive File to Examine
System in AccessData Registry Viewer
Lab #1 Part 8: Registry Examination with Yaru
Run Yaru Select Open Hive Browse to Hive File
Yaru deleted key/value recovery example
Current System Name
Current Timezone Information
Last System Shutdown Date/Time
Lab #1 Part 9: Registry Examination with Regripper
Run Regripper Select Hive to Process Provide output filename Select Plugin File (type of registry hive to process) Rip It (Do this for each of the Hive files we exported)
Run Regripper on Exported SAM Hive
Excerpt from SAM Hive Regripper Output (1)
Username : Mr. Evil [1003] Full Name : User Comment : Account Type : Default Admin User Account Created : Thu Aug 19 23:03:54 2004 Z Last Login Date : Fri Aug 27 15:08:23 2004 Z Pwd Reset Date : Thu Aug 19 23:03:54 2004 Z Pwd Fail Date : Never Login Count : 15 --> Password does not expire --> Normal user account
Excerpt from SAM Hive Regripper Output (2)
Username : Administrator [500] Full Name : User Comment : Built-in account for administering the computer/domain Account Type : Default Admin User Account Created : Thu Aug 19 16:59:24 2004 Z Last Login Date : Never Pwd Reset Date : Thu Aug 19 17:17:29 2004 Z Pwd Fail Date : Never Login Count :0 --> Password does not expire --> Normal user account
Excerpt from SAM Hive Regripper Output (3)
Group Name : Administrators [2] LastWrite : Thu Aug 19 23:03:54 2004 Z Group Comment : Administrators have complete and unrestricted access to the computer/domain Users : S-1-5-21-2000478354-6887898441708537768-1003 S-1-5-21-2000478354-6887898441708537768-500
Lab #1 Part 10: Image Registry Autoruns Extraction
Load image using AccessData Imager Mount image with read/write caching Run autoruns against mounted image
With Image Loaded in FTK Imager, Select Image Mounting
Set Parameters
Run Autoruns Select Analyze Offline System
Enter Parameters for Windows folder & Mr. Evil Profile
Questions?
84
S-ar putea să vă placă și
- Cobalt Strike Active Directory ManualsDocument28 paginiCobalt Strike Active Directory ManualsCristian RodriguezÎncă nu există evaluări
- CKDF110-Lab Session #1: Lab Setup: 1. PreliminariesDocument25 paginiCKDF110-Lab Session #1: Lab Setup: 1. PreliminariesMikeÎncă nu există evaluări
- Rhce Rhcsa PaperDocument27 paginiRhce Rhcsa PaperArif Mohammed Rangrezz100% (1)
- 8 Docker Container PlatformDocument9 pagini8 Docker Container PlatformAmarnath SankarÎncă nu există evaluări
- TRLOGDocument44 paginiTRLOGSlendy RgÎncă nu există evaluări
- Cobalt Strike Manual 1658430628Document30 paginiCobalt Strike Manual 1658430628AR HMEÎncă nu există evaluări
- BCSL 063 Solved Assignment 2022 23 UlptmtDocument15 paginiBCSL 063 Solved Assignment 2022 23 UlptmtShubham SrivastavÎncă nu există evaluări
- Don't Have Your Server Admin Query Password Look Here! PDFDocument7 paginiDon't Have Your Server Admin Query Password Look Here! PDFDarkeenÎncă nu există evaluări
- Ethical Hacking With Kali Linux NotesDocument22 paginiEthical Hacking With Kali Linux NotesdhavalÎncă nu există evaluări
- EBS12.2.4 Installation and Upgradation FinalDocument26 paginiEBS12.2.4 Installation and Upgradation FinalIrfan AhmadÎncă nu există evaluări
- WindowsattacksDocument78 paginiWindowsattacksblufakesionÎncă nu există evaluări
- Install OwnCloud on Ubuntu with Apache, MariaDB and Let's Encrypt SSLDocument36 paginiInstall OwnCloud on Ubuntu with Apache, MariaDB and Let's Encrypt SSLSagar PadhyÎncă nu există evaluări
- Step To Clear Common Error MHF Client Side-1Document20 paginiStep To Clear Common Error MHF Client Side-1Arya Stygian EditionÎncă nu există evaluări
- Weblogic Setup GuideDocument131 paginiWeblogic Setup GuideMak Tze KhengÎncă nu există evaluări
- Active Directory Exploitation Cheat SheetDocument14 paginiActive Directory Exploitation Cheat SheetSokoine Hamad DenisÎncă nu există evaluări
- SodapdfDocument30 paginiSodapdffraterxiÎncă nu există evaluări
- Ethical Hacking-1Document142 paginiEthical Hacking-1krishna kumar bhardwajÎncă nu există evaluări
- Networking: Ipconfig Ping FC CHKDSK Net AccountsDocument27 paginiNetworking: Ipconfig Ping FC CHKDSK Net Accountsshivsharma330Încă nu există evaluări
- Cadence Tool Installation and Mounting CommercialDocument21 paginiCadence Tool Installation and Mounting Commercialmartin_titinÎncă nu există evaluări
- Linux QuestionsDocument11 paginiLinux QuestionsMurali TungaÎncă nu există evaluări
- Enabling Web ConsoleDocument2 paginiEnabling Web ConsolepmmanickÎncă nu există evaluări
- Exam EX200 Exam Name Red Hat CertifiedDocument70 paginiExam EX200 Exam Name Red Hat CertifiedahmedwagihÎncă nu există evaluări
- TRLOGDocument10 paginiTRLOGallie343343Încă nu există evaluări
- AdwCleaner (S00)Document2 paginiAdwCleaner (S00)Eduardo PerezÎncă nu există evaluări
- Free VCE and PDF Exam Dumps from PassLeader for Red Hat Certified System Administrator (RHCSA) EX200Document7 paginiFree VCE and PDF Exam Dumps from PassLeader for Red Hat Certified System Administrator (RHCSA) EX200klguuÎncă nu există evaluări
- Backup Logs for Balsharaf GroupDocument16 paginiBackup Logs for Balsharaf GroupKarthikeyan KrishnamoorthyÎncă nu există evaluări
- Lab #11Document13 paginiLab #11Qaxraman SadullaevÎncă nu există evaluări
- Table of ContentsDocument6 paginiTable of ContentsNagendra CÎncă nu există evaluări
- UsbFix ReportDocument3 paginiUsbFix ReportDazdouz MkhalwiÎncă nu există evaluări
- Dorks TodayDocument56 paginiDorks TodayJoao SantosÎncă nu există evaluări
- Cristie TBMR Backup & Restore DemoDocument13 paginiCristie TBMR Backup & Restore DemoJaideep SinghÎncă nu există evaluări
- RKreportDocument2 paginiRKreportLuís Fernando PalazziÎncă nu există evaluări
- Host Name: OS Name: OS Version: OSDocument1.777 paginiHost Name: OS Name: OS Version: OStruonggoodkoolÎncă nu există evaluări
- Rhce Question and AnswerDocument27 paginiRhce Question and AnswerRaj ShuklaÎncă nu există evaluări
- How To Create Newswrap Server (Main Server)Document34 paginiHow To Create Newswrap Server (Main Server)Naveen PandeyÎncă nu există evaluări
- Tuto BactrackDocument1.019 paginiTuto Bactracknouroudine52611Încă nu există evaluări
- Dump Windows Password Hashes Efficiently - Part 1Document9 paginiDump Windows Password Hashes Efficiently - Part 1Prasanna Kumar DasÎncă nu există evaluări
- Make Your Own Bot NetworkDocument18 paginiMake Your Own Bot NetworkexploitoneÎncă nu există evaluări
- R12 Installation on OEL 5Document18 paginiR12 Installation on OEL 5kkpareekÎncă nu există evaluări
- WPI LogDocument5 paginiWPI LogIvan CLÎncă nu există evaluări
- Conti Playbook TranslatedDocument32 paginiConti Playbook Translatedjarot jarotÎncă nu există evaluări
- TroubleshootingDocument20 paginiTroubleshootingTheSaiful 08Încă nu există evaluări
- 0xc0000005 ErrorDocument12 pagini0xc0000005 ErrorTome DimovskiÎncă nu există evaluări
- Rhce Rhcsa PaperDocument25 paginiRhce Rhcsa PaperSopan sonarÎncă nu există evaluări
- A+ With Network Certification: Network Operating System (NOS)Document20 paginiA+ With Network Certification: Network Operating System (NOS)Dinesh RaiÎncă nu există evaluări
- Core Commande CompletDocument7 paginiCore Commande CompletnirvasebÎncă nu există evaluări
- WPI LogDocument5 paginiWPI LogLuis Roberto V. CéspedesÎncă nu există evaluări
- (Resolved) Searchqu ProblemDocument26 pagini(Resolved) Searchqu Problemprabhatm_2Încă nu există evaluări
- Libki Install W CAP1 SettingDocument9 paginiLibki Install W CAP1 Settingtdisidro517Încă nu există evaluări
- WINDOWS XP BOOT TROUBLESHOOTING GUIDEDocument44 paginiWINDOWS XP BOOT TROUBLESHOOTING GUIDETejinder Singh AhirÎncă nu există evaluări
- Technical Hints and TipsDocument14 paginiTechnical Hints and TipsBiswajit DasÎncă nu există evaluări
- KnownIssues ExternalDocument10 paginiKnownIssues ExternalTolulope AbiodunÎncă nu există evaluări
- Jncia Lab GuideDocument10 paginiJncia Lab GuideKhiem Bui100% (1)
- Virtual Box InstallDocument3 paginiVirtual Box Installsunkara2000Încă nu există evaluări
- Lab 2 Configuring Basic Security Controls On A Centos Linux Server Objective of Lab2Document7 paginiLab 2 Configuring Basic Security Controls On A Centos Linux Server Objective of Lab2Hải PhạmÎncă nu există evaluări
- Output LogDocument42 paginiOutput Logrizky d'ramadhaniÎncă nu există evaluări
- Some Tutorials in Computer Networking HackingDe la EverandSome Tutorials in Computer Networking HackingÎncă nu există evaluări
- Common Windows, Linux and Web Server Systems Hacking TechniquesDe la EverandCommon Windows, Linux and Web Server Systems Hacking TechniquesÎncă nu există evaluări
- MCTS 70-680 Exam Questions: Microsoft Windows 7, ConfiguringDe la EverandMCTS 70-680 Exam Questions: Microsoft Windows 7, ConfiguringEvaluare: 3.5 din 5 stele3.5/5 (2)
- Configure AAA Authentication on Cisco RoutersDocument4 paginiConfigure AAA Authentication on Cisco Routersalb3rtlinÎncă nu există evaluări
- PT Activity: Configure Cisco Routers For Syslog, NTP, and SSH Operations - 1 %Document4 paginiPT Activity: Configure Cisco Routers For Syslog, NTP, and SSH Operations - 1 %alb3rtlinÎncă nu există evaluări
- PriDocument33 paginiPrialb3rtlinÎncă nu există evaluări
- ISM 210 Syllabus Winter 2014Document7 paginiISM 210 Syllabus Winter 2014alb3rtlinÎncă nu există evaluări
- CNS 394 - Unit 2: Information Ethics and Codes of ConductDocument24 paginiCNS 394 - Unit 2: Information Ethics and Codes of Conductalb3rtlinÎncă nu există evaluări
- Cns394 Unit8 RegulatoryDocument53 paginiCns394 Unit8 Regulatoryalb3rtlinÎncă nu există evaluări
- Desire2Learn Student InstructionsDocument6 paginiDesire2Learn Student Instructionsalb3rtlinÎncă nu există evaluări
- HW1 Design Critique IDocument2 paginiHW1 Design Critique Ialb3rtlinÎncă nu există evaluări
- 2013 CPA Exam FAQ BrochureDocument8 pagini2013 CPA Exam FAQ Brochurealb3rtlinÎncă nu există evaluări
- Campus Recruiting Timeline: For Accounting ST UdentsDocument8 paginiCampus Recruiting Timeline: For Accounting ST Udentsalb3rtlinÎncă nu există evaluări
- Passport Form2012Document1 paginăPassport Form2012alb3rtlinÎncă nu există evaluări
- ISM210 Midterm Study Guide Winter 2014Document1 paginăISM210 Midterm Study Guide Winter 2014alb3rtlinÎncă nu există evaluări
- Depaul FlowDocument1 paginăDepaul Flowalb3rtlinÎncă nu există evaluări
- Passport Form2012Document1 paginăPassport Form2012alb3rtlinÎncă nu există evaluări
- PCI Consulting Proposal Development 104Document2 paginiPCI Consulting Proposal Development 104alb3rtlinÎncă nu există evaluări
- Unit 6Document40 paginiUnit 6alb3rtlinÎncă nu există evaluări
- 2013 CPA Exam FAQ BrochureDocument8 pagini2013 CPA Exam FAQ Brochurealb3rtlinÎncă nu există evaluări
- Syllabus Acc 101-503, 504Document4 paginiSyllabus Acc 101-503, 504alb3rtlinÎncă nu există evaluări
- 9 Access CTRL Physical Lecture 340Document41 pagini9 Access CTRL Physical Lecture 340alb3rtlinÎncă nu există evaluări
- Stress Test Settings for PrimeNet OptimizationDocument1 paginăStress Test Settings for PrimeNet OptimizationPeniz LetoyÎncă nu există evaluări
- Asdf Class 3Document66 paginiAsdf Class 3alb3rtlinÎncă nu există evaluări
- ISM 210 Syllabus Winter 2014Document7 paginiISM 210 Syllabus Winter 2014alb3rtlinÎncă nu există evaluări
- TDC-478 Class 1Document66 paginiTDC-478 Class 1alb3rtlinÎncă nu există evaluări
- 7 Lecture 340 Online Tracking EncryptionDocument59 pagini7 Lecture 340 Online Tracking Encryptionalb3rtlinÎncă nu există evaluări
- Backtrack Supplement 1Document6 paginiBacktrack Supplement 1alb3rtlinÎncă nu există evaluări
- 2 - TraceifaceDocument4 pagini2 - Traceifacealb3rtlinÎncă nu există evaluări
- Maurice Nicoll The Mark PDFDocument4 paginiMaurice Nicoll The Mark PDFErwin KroonÎncă nu există evaluări
- CNS 320 Week1 LectureDocument63 paginiCNS 320 Week1 Lecturealb3rtlinÎncă nu există evaluări
- CNS 320 Week2 LectureDocument63 paginiCNS 320 Week2 Lecturealb3rtlinÎncă nu există evaluări
- CNS 320 Week9 LectureDocument73 paginiCNS 320 Week9 Lecturealb3rtlinÎncă nu există evaluări
- MortScript ManualDocument83 paginiMortScript ManualCristian WitoszynskiÎncă nu există evaluări
- FSSO InfoDocument15 paginiFSSO InfoHatherst1953Încă nu există evaluări
- Custom ConnectorsDocument20 paginiCustom ConnectorsSaeed NasharÎncă nu există evaluări
- Deploy Outlook Mail Profile Settings Via GPO or Script - HowTo-OutlookDocument5 paginiDeploy Outlook Mail Profile Settings Via GPO or Script - HowTo-OutlookAlexandarÎncă nu există evaluări
- LogDocument55 paginiLogyudoÎncă nu există evaluări
- Changing a systems hostname requires updating SAP, Oracle, hosts file, registry keysDocument2 paginiChanging a systems hostname requires updating SAP, Oracle, hosts file, registry keysKashif KhanÎncă nu există evaluări
- Forensics FJDocument28 paginiForensics FJFaizan Javed (Faizi)Încă nu există evaluări
- Adveon Installation Guide V1.3 and V1.5 - Edgecam - BasicDocument46 paginiAdveon Installation Guide V1.3 and V1.5 - Edgecam - BasictibikomaÎncă nu există evaluări
- How RPC WorksDocument5 paginiHow RPC WorksSaravanan NallusamyÎncă nu există evaluări
- Dyalog APL User GuideDocument314 paginiDyalog APL User GuideHRCÎncă nu există evaluări
- Office 2010 All Editions Keys PacoolioDocument7 paginiOffice 2010 All Editions Keys PacoolioERI WIDYANINGRINIÎncă nu există evaluări
- Frescoplay Courses - DumpDocument32 paginiFrescoplay Courses - DumpSameer KrishnaÎncă nu există evaluări
- Dump: Exam 000-253 - IBM WebSphere Application Server Network Deployment V6.1, Core AdministrationDocument30 paginiDump: Exam 000-253 - IBM WebSphere Application Server Network Deployment V6.1, Core Administrationdanielcgomes100% (2)
- Jet Show Plan Manager HelpDocument8 paginiJet Show Plan Manager HelpgldstarÎncă nu există evaluări
- Managing Extensions in Your Enterprise: Securely Manage Chrome Extensions at ScaleDocument25 paginiManaging Extensions in Your Enterprise: Securely Manage Chrome Extensions at ScaleArvin VangaÎncă nu există evaluări
- 012 A IntroductionDocument112 pagini012 A IntroductionZans SalimaÎncă nu există evaluări
- Getting Started with Devstack: A Guide to Setting Up OpenStack Development EnvironmentDocument5 paginiGetting Started with Devstack: A Guide to Setting Up OpenStack Development EnvironmentPravesh UpadhyayÎncă nu există evaluări
- Veyon Admin Manual en - 4.7.3Document77 paginiVeyon Admin Manual en - 4.7.3maycrayÎncă nu există evaluări
- MSI Unpacker from JSWare: Unpack MSI and MSM filesDocument6 paginiMSI Unpacker from JSWare: Unpack MSI and MSM filesAriel CateroÎncă nu există evaluări
- InstallationManual IRIS KongDocument49 paginiInstallationManual IRIS KongRana Abdul RehmanÎncă nu există evaluări
- Prepare An App For Conversion With The Desktop Bridge: Windows Dev CenterDocument7 paginiPrepare An App For Conversion With The Desktop Bridge: Windows Dev CenterAlejandro Mtz RamosÎncă nu există evaluări
- PC TrickesDocument28 paginiPC TrickesNeeraj SharmaÎncă nu există evaluări
- Microsoft MOC-10982Document7 paginiMicrosoft MOC-10982blarsen_876540493Încă nu există evaluări
- Backup Registry in Windows 10Document5 paginiBackup Registry in Windows 10Pappu KhanÎncă nu există evaluări
- Monitor System Changes with Regshot Registry Comparison ToolDocument13 paginiMonitor System Changes with Regshot Registry Comparison ToolurbanorcÎncă nu există evaluări
- Actual4Test: Actual4test - Actual Test Exam Dumps-Pass For IT ExamsDocument6 paginiActual4Test: Actual4test - Actual Test Exam Dumps-Pass For IT ExamssankarÎncă nu există evaluări
- Fanuc Open Sytem User ManualDocument81 paginiFanuc Open Sytem User ManualsunhuynhÎncă nu există evaluări
- FS2Crew ATR Main OpsDocument73 paginiFS2Crew ATR Main Opsstilllife87Încă nu există evaluări
- OPC Security WP3Document54 paginiOPC Security WP3lakseÎncă nu există evaluări
- Removing The V811SS2 InRoads Group ProductsDocument5 paginiRemoving The V811SS2 InRoads Group Productsjulito81Încă nu există evaluări